Important Update Effective February 1, 2024!
Due to recent changes in Jira and Confluence, we've made the tough decision to discontinue the OpenID Connect (OIDC)/OAuth app and no longer provide new versions for the newest Jira/Confluence releases as of January 31, 2024.
This is due to some necessary components no longer shipping with Jira/Confluence, which would require some extensive rewrites of the OIDC App.
Knowledge Base
Microsoft Power Automate & API Tokens
Unfortunately Microsoft's Jira connector from Power Automate doesn't work with Jira on premises/ self hosted instances anymore.
Neither regular passwords nor API Tokens will work for authentication from the Power Automate suite against your Jira.
This has been confirmed by the Microsoft support in July 2020.
Zapier & API Tokens
If you want to connect Zapier and Jira using API Tokens, make sure that you choose Basic Auth
and enter a valid REST endpoint in Jira, such as https://<your-jira-base-url>/rest/api/2/myself:
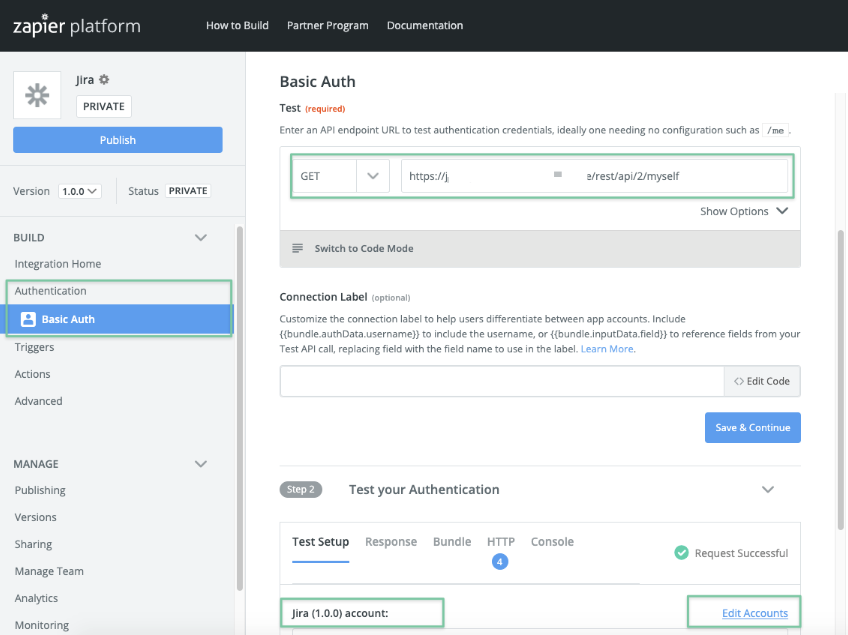
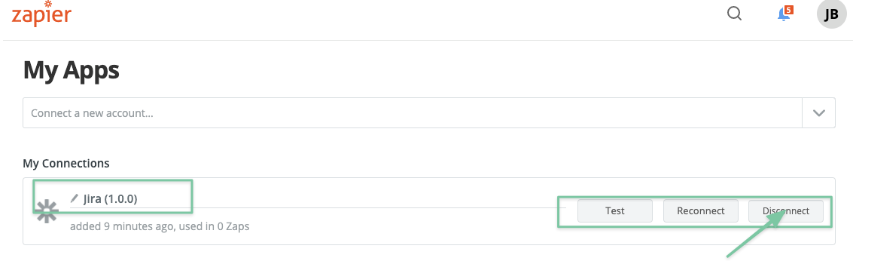
Zapier allows to manage accounts via the Edit Accounts link as depicted in the screenshot above.
By default, the Jira ones are labeled "Jira (1.0.0)".
As you can't change an existing account (i.e. to edit the username and token), you need to disconnect it and create a new one.
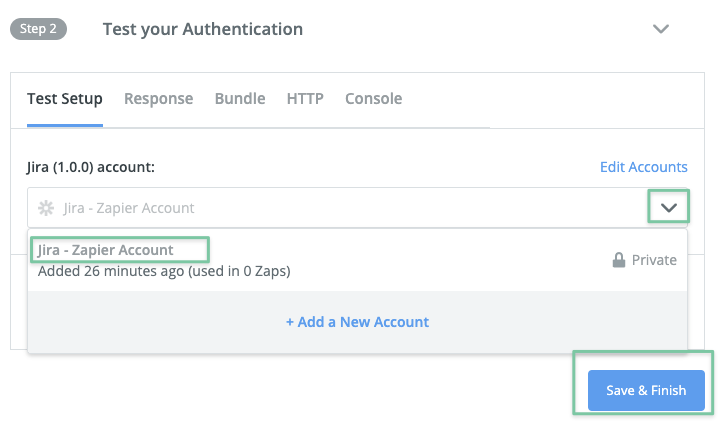
We recommend to provide a meaningful label in that screen, so that you can assign the right account to your Jira/ Zapier integration:
I'm using Bob Swift's CLI for Jira but can't use API Tokens with it
The Bob Swift CLI has a password- and a token parameter for passing credentials.
The token parameter doesn't work, if you are using API Tokens created with our app. Use the password parameter instead.
An example call would look like this:
./acli.sh --server https://your-jira.com --user someuser --password <your-api-token> --action getProjectListYou can also use the short version of the parameters -s, -u and -p to send server name, user name and password/ token.
Please note that the connection test which is part of the new installer for the CLI won't work with API tokens, at least not with Jira 8.14.
You need to skip it and can still use tokens as in the example above.
API Tokens & Captcha Challenge
When a user provides a wrong token or one already expired, the authentication attempt will count towards the failed login count in Jira/ Confluence.
Depending on the settings for "Maximum Authentication Attempts Allowed" in Jira (https://your-jira.com/secure/admin/ViewApplicationProperties.jspa)
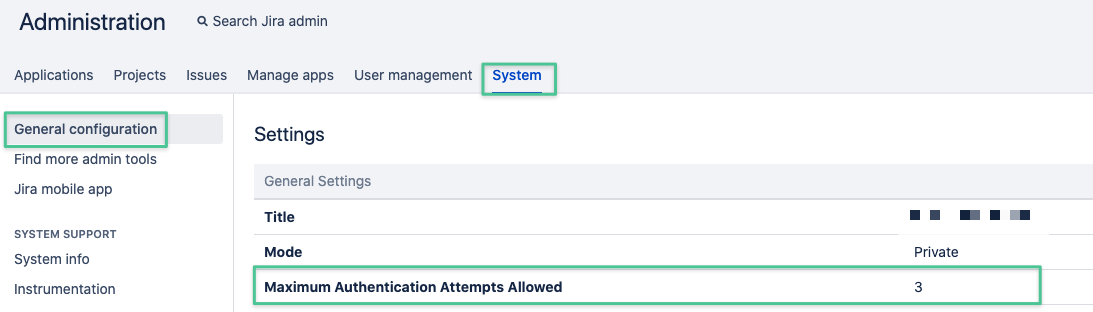
or Confluence (https://your-confluence.com/admin/editsecurityconfig.action)
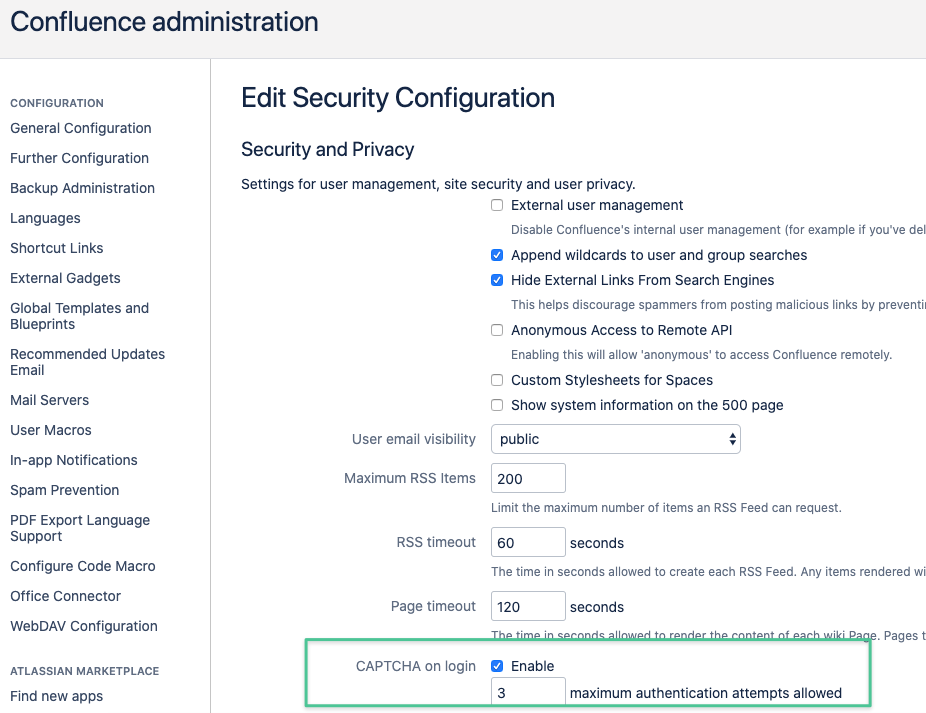
solving a captcha challenge might be required, next time the user logs in to the UI.
Providing a valid token again for authentication on the REST API will reset the failed login counter automatically,
so that solving the capture challenge is not required anymore.
This really only applies for doing that with a valid API token on the REST API.
If the user tries to login with a valid and local password via the UI, he/ she will still see the capture challenge.
The behaviour is the same as with our SAML SSO app, where trying to authenticating with a user and without SSO,
using a local password would also increase the failed login count and create a captcha challenge when trying to login without SSO or REST,
but is reset again, once the user successfully authenticates via SSO.
Summary of behaviour after causing a Captcha Challenge due to using an invalid API Token
- Should the user login to Jira/ Confluence Webinterface via the Resolution SAML SSO app, the failed login counter is reset/ no captcha challenge is displayed anymore
- Should the user login to Jira/ Confluence Webinterface without SSO, he/ she will need to solve the captcha and also need to provide a valid password (API Tokens are REST only)
- Should the user provide another valid token on the REST API again, the failed login counter is also reset/ no captcha challenge is displayed on the Jira/ Confluence Webinterface
