2020-07-09 - SQL injection Vulnerability
Summary | Authenticated Users with "Create Token on Behalf" permissions can gain full access to the Jira/Confluence database. |
|---|---|
Advisory Release Date | 7/9/2020 - Interim Version |
Affected Product | |
Affected versions | 1.3.0, 1.3.1 & 1.4.0 |
Fixed versions | Versions 1.2.3 and below are not affected by this issue 1.4.x releases the first fixed version → 1.4.1 and above are not vulnerable. |
CVSS Score | CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H/E:F/RL:O/RC:C |
Summary
This advisory discloses a critical severity security vulnerability affecting our API Token Authentication Products in the versions from 1.3.0 - 1.4.0.
An authenticated user with the Permissions to create tokens on behalf of other users can gain full access to the Jira/Confluence Database.
Please upgrade your Installations to 1.4.1 or newer to fix this vulnerability.
Details
Today (7/9/2020) we received a submission via our Bugcrowd Bung bounty program, of this critical security vulnerability.
We will disclose the exact steps to reproduce/exploit this vulnerability by 7/23/20206 a.m CET - to leave our customers some time to put mitigations/fixes in place.
The vulnerability allows an authenticated User, who has the permission in our plugin to create tokens on behalf of other users, to gain full access to the host products (jira/confluence) database.
Generally, the "Create Token on Behalf" permission is only given to administrators or not used at all - this often serves as natural mitigation of the Issue.
A fixed version 1.4.1 & 1.3.2 has been available in the Marketplace since 7/9/202011 a.m CET (5 hours after the original bug crowd submission).
What You Need to Do
Upgrade
Upgrade your installation to version 1.4.1 or newer. If you are currently on 1.3.0 or 1.3.1 you can also choose to upgrade to 1.3.2 which has been released to contain this fix.
Other Mitigations / Workarounds
If you cannot upgrade our plugin right now - here are two more possible mitigations/workarounds
Remove the "Create token on behalf" permission from all Users.
Confluence/Jira Administration → API Token Authentication → Go to the "Permissions" Tab.
At the Section "Create Token On Behalf Permission", remove all Groups from the Setting "Groups with create token on behalf permission".
It should look like this afterward:
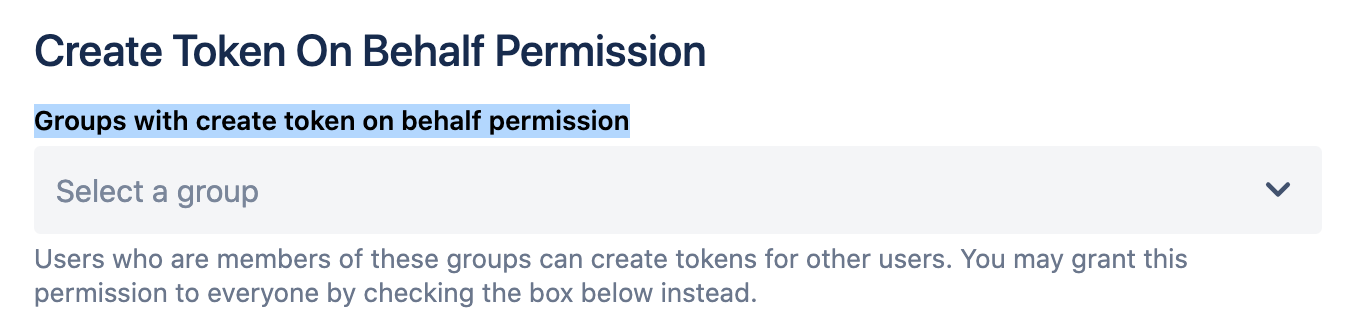
→ Save the config.
Accept the Risk
Based on your deployment, you could also choose to accept the Risk without any changes. Generally, Permission to create tokens on behalf of other users is only given to highly privileged groups like Administrators.
Administrators often already have or can gain (by installing an addon) full DB access already, so that they don't need to rely on this vulnerability to do this.
Support
If you have questions or concerns regarding this advisory, please raise a support request via our Support Portal.
