Performing Bulk Operations
This guide covers the essential knowledge for performing bulk operations in User Management & License Optimizer, focusing on how each operation works and what you need to know to use them effectively.
Note: Before performing bulk operations, a manual sync is recommended to ensure you're working with the most current user data. Recent changes made by other administrators in admin.atlassian.com, SCIM updates from your identity provider, or group membership modifications may not yet be reflected in User Management & License Optimizer. A manual sync ensures accurate results and prevents operations on outdated information. See the Sync Functionality page for detailed instructions on when and how to sync.
Remove App Access
Remove users' access to specific Atlassian applications while maintaining their accounts and non-product group memberships.
How It Works
The Remove App Access operation:
Removes users from application-specific access groups automatically
Immediately revokes access to selected applications
Preserves user accounts, data, and non-product groups
Updates billing automatically at the next cycle
Allows selective removal (specific apps) or complete removal (all apps)
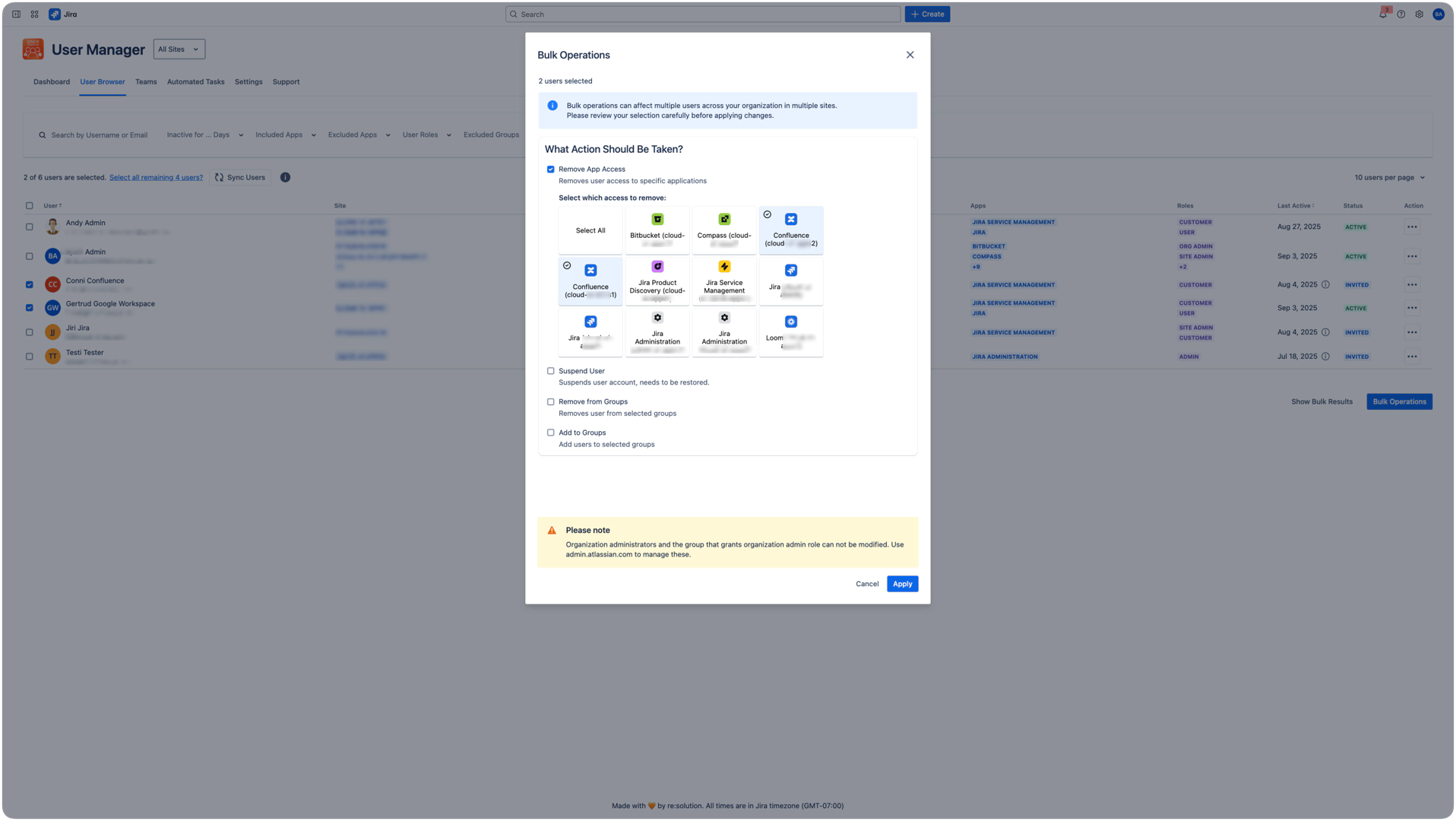
Configuration Options
Option A: Specific Applications
Select "Removes user access to specific applications"
App tiles appear showing available applications
Click on app tiles to select them (blue checkmark appears)
Each tile shows the app icon, name, and site it belongs to
Option B: All Applications
Select "Select All" option
Removes access from every application across all sites
Use with caution - this is complete access removal
Impact and Effects
Immediate Effects:
Users lose access within seconds to minutes
Cannot log into removed applications
Receive "access denied" messages when attempting access
Automatically removed from app-specific access groups
Billing and License Impact:
License count decreases immediately in your organization
Billing adjustments occur at the next billing cycle
Cost savings visible in organization admin dashboard
Data Preservation:
All user-created content remains intact (issues, pages, comments)
Content attribution preserved
Historical data and audit logs maintained
Multi-Site Behavior
When working with multiple sites:
Each app tile shows which site it belongs to
Users may have the same product on multiple sites
Can remove from specific sites while maintaining others
Site-specific groups are handled automatically
Example: Remove production access but maintain staging
Select only production site applications:
Jira Software (Production)Leave staging applications unchecked:
Jira Software (Staging)Result: Users retain staging access while losing production access
Suspend User
Temporarily suspend user accounts from accessing any Atlassian services while preserving all account data and settings.
How It Works
Suspension is a comprehensive security action that:
Disables account access entirely across all Atlassian services
Affects all sites and applications immediately
Preserves account data, settings, and group memberships
Requires administrative reactivation to restore access
Cannot be applied to Organization Administrators (automatic protection)
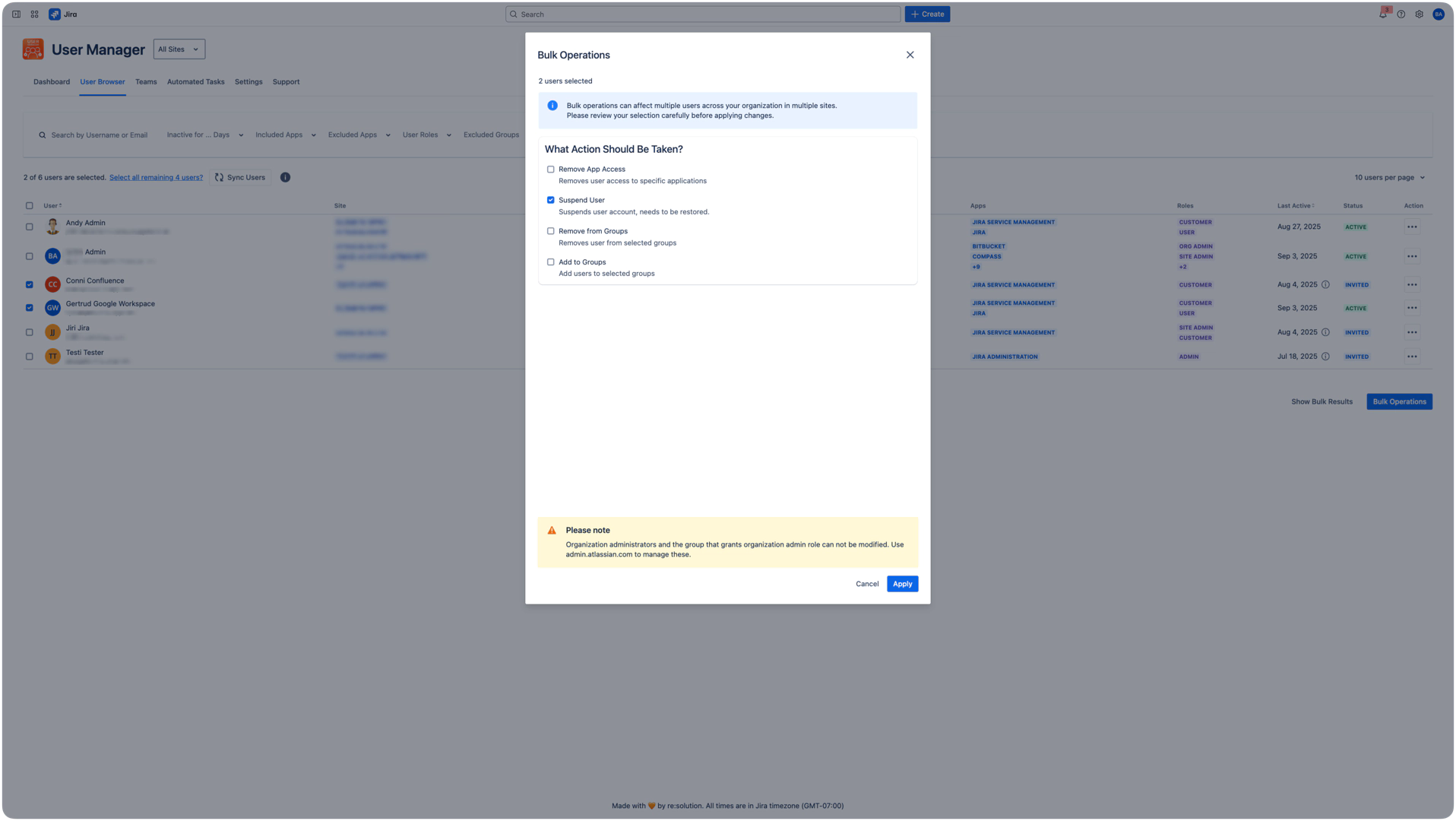
Suspension Process
Select users in the User Browser
Open Bulk Operations modal
Check "Suspend User" checkbox
Review warnings about reactivation requirements
Note admin exclusion warning (org admins automatically protected)
Click Apply to execute
Post-Suspension Effects
Users appear as "Suspended" in User Browser
Cannot authenticate to any Atlassian service
API tokens and OAuth tokens are invalidated
Active sessions terminated across all sites
Group memberships preserved for future reactivation
Suspension vs. App Access Removal
Aspect | Suspend User | Remove App Access |
|---|---|---|
Scope | All Atlassian services | Selected applications only |
Account Status | Suspended | Active |
Group Memberships | All preserved | Product groups removed |
Reactivation | Required via admin interface | Grant access via groups |
Use Case | Security/Leave situations | License optimization |
Security Features
Automatic Admin Protection:
Organization administrators cannot be suspended
Prevents accidental administrative lockouts
Cannot be overridden
Protected users identified in operation results
Immediate Security Effects:
Active sessions terminate across all sites immediately
API access revoked - all tokens invalidated
OAuth connections severed
Multi-factor authentication settings preserved for reactivation
Reactivation Requirements
Current Process (Bulk reactivation not yet available):
Navigate to admin.atlassian.com
Go to Directory > Users
Find and select the suspended user
Click reactivation option and confirm
User regains all previous access and group memberships
Group Management
Add or remove multiple users from groups to manage permissions, access, and organizational structure.
Understanding Group Types
Product Access Groups:
Format:
{product}-users-{sitename}Examples:
jira-software-users-main,confluence-users-documentationControl application access
Automatically managed during app access operations
Custom Groups:
Created by administrators for organizational needs
Examples:
engineering-team,external-contractors,project-alpha-teamUsed for project access, departments, or role-based permissions
Full administrative control over membership
System Groups:
Reserved groups with special functions
Examples:
site-admins,system-administratorsConnected to administrative privileges
Exercise caution when modifying
Add to Groups
Process
In Bulk Operations modal, check "Add to Groups"
Use dropdown to search for and select groups
Select multiple groups as needed
Review selections and apply
Key Considerations
Check existing memberships to avoid redundancy
Understand what permissions each group grants
Review license implications of group membership
Consider interactions between different groups
Remove from Groups
Process
In Bulk Operations modal, check "Remove from Groups"
Search for and select groups to remove users from
Select multiple groups if needed
Verify selections and apply
Critical Considerations
Permission Dependencies:
Some groups may be prerequisites for others
Removal might affect access to multiple systems
Administrative groups have cascading effects
High-Risk Groups:
Administrative and privileged access groups
Single sign-on or authentication groups
MFA enforcement and security groups
Multi-Site Group Behavior
Site-Scoped Groups:
Associated with specific sites
Examples:
jira-software-users-production,site-admins-documentationGrant access to applications on specific sites only
Organization-Wide Groups:
Span across all sites
Examples:
engineering-team,senior-developersUsed for global policies and cross-site collaboration
Combining Operations
Execution Order
Operations execute sequentially in the order you select checkboxes.
First selected checkbox executes first
Subsequent checkboxes follow in selection order
System processes each operation completely before starting the next
Changing Order
To modify execution sequence:
Deselect all checkboxes to reset
Re-select checkboxes in desired order
New sequence will be applied
Strategic Sequencing
Clean Transition (Moving users between teams):
First: Add to new groups (grants new access)
Then: Remove from old groups (removes old access)
Result: No access gaps during transition
Security Reduction (Reducing privileges):
First: Remove from privileged groups (reduces risk immediately)
Then: Add to restricted groups (applies limitations)
Result: Immediate security improvement
Results and Monitoring
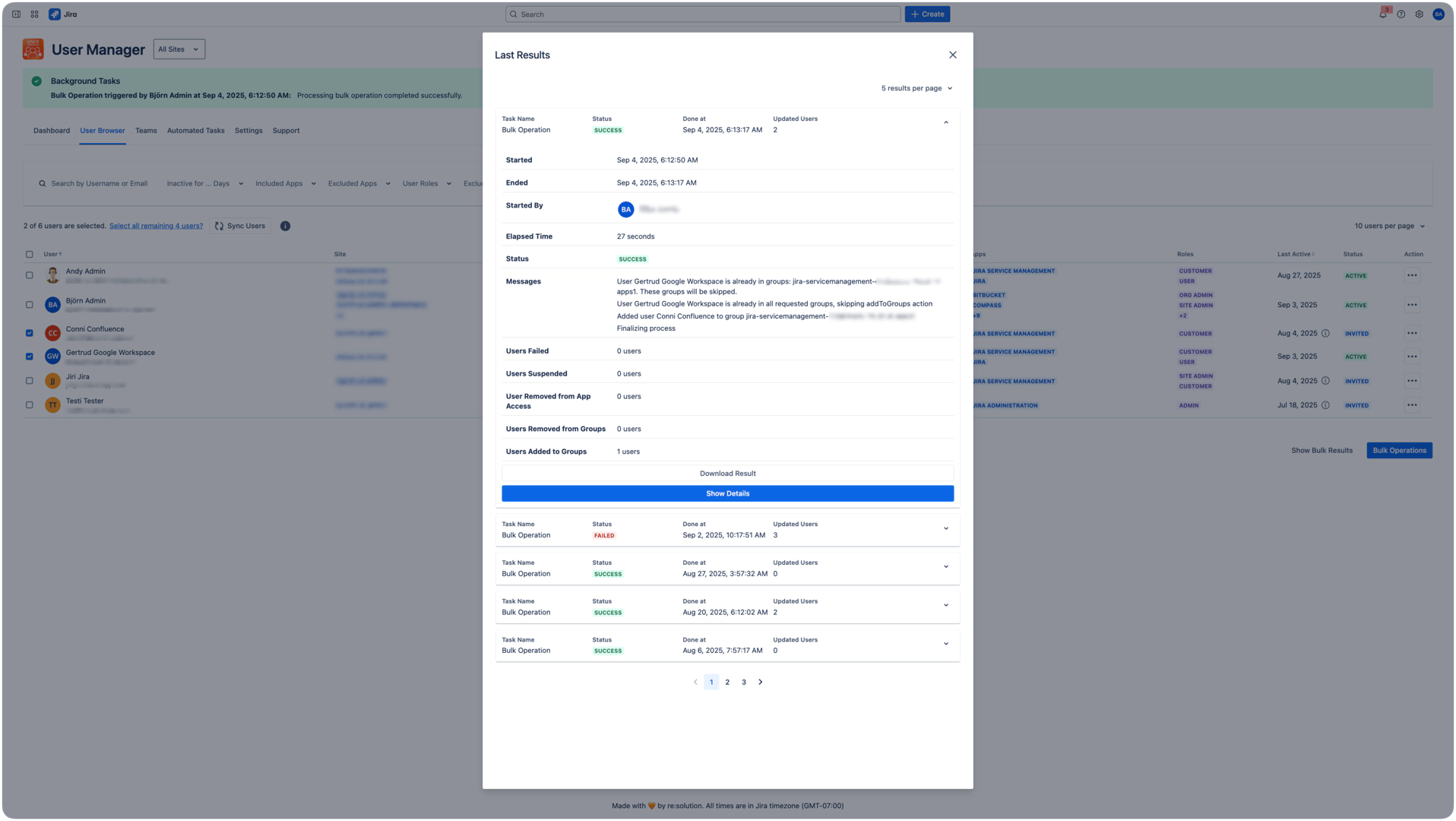
Accessing Results
After operation completion:
Click "Show Bulk Results" button
View summary table with recent operations
Click individual operations for detailed results
Download detailed logs if needed
Understanding Results
Summary Information:
Status: SUCCESS, FAILED, or PARTIAL
Updated Users: Count of users affected
Started By: Administrator who executed
Detailed Results Analysis
User Processing Statistics:
Users Failed: Count where operation couldn't be completed
Users Deactivated: Successfully suspended user count
Users Removed from App Access: Count by application
Users Removed from Groups: Group removal count
Users Added to Groups: Group addition count
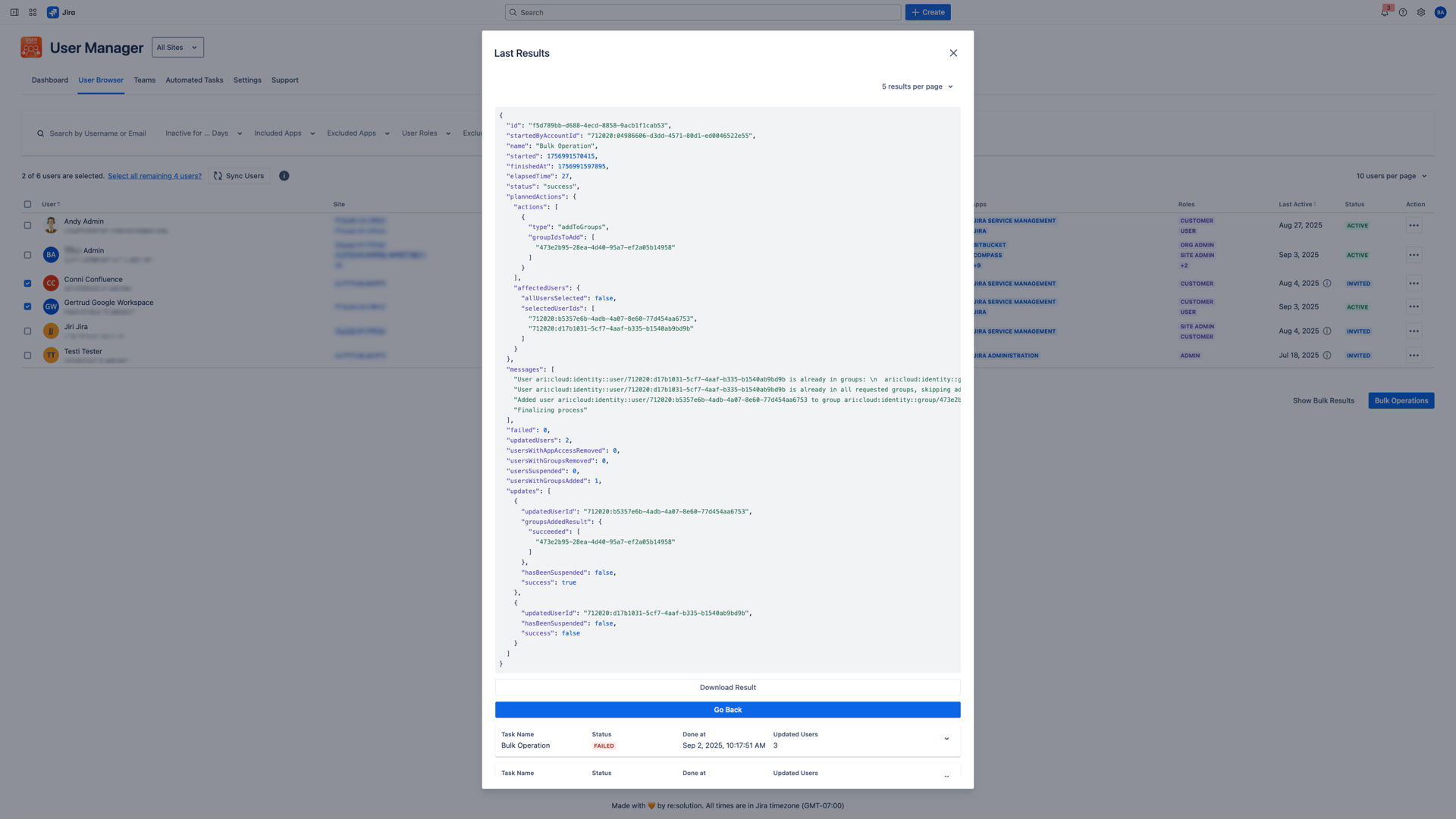
Show Details:
JSON-formatted complete operation log
Individual user processing results
Specific error messages for failures
API response codes and timing data
Granular success/failure breakdown
Multi-Site Results
Results provide site-specific information:
- Example:
- Operation: Remove App Access
- Total Users: 50
- Results by Site:
- - Production: 50 successful
- - Staging: 48 successful, 2 failed
- - Documentation: 50 successful
Security Protections
Administrator Protection
Organization administrators automatically excluded from all operations
Prevents accidental administrative lockouts
Cannot be overridden through any interface
Protected users identified in operation results
Audit Trail
All bulk operations create permanent records:
Complete operation details with timestamps
Individual user processing results
Administrator attribution and IP tracking
Available for compliance and audit purposes
Important Limitations
Manual Sync Dependency
Bulk operations work on data in User Management & License Optimizer database
Recent changes in admin.atlassian.com may not be reflected
Manual sync recommended before operations for accuracy
SCIM and Identity Provider Considerations
SCIM-managed groups cannot be modified manually
Identity provider may reverse manual changes
Coordinate with identity management team for SCIM environments
Organization Admin Restrictions
Org admins cannot be suspended or have access removed
Automatic protection prevents administrative lockouts
Plan alternative approaches for org admin management
Related Topics
User Browser - Learn how to search, filter, and select users for bulk operations
Automated Tasks - Set up recurring bulk operations on a schedule
Sync Functionality - Understand when and how to sync data before bulk operations
Organizations and Sites - Multi-site concepts and management
Groups & Access Control - Understanding Atlassian group types and permissions
Settings - Configure organization settings and access controls
Best Practises & Troubleshooting - Best practises, scenarios, and general troubleshooting guidance
