Setup SAML SSO with Azure AD (JIRA) - 0.14.5 NEW
This setup guide describes how to setup JIRA SAML Single Sign On (SSO) with Azure AD, applicable for SAML plugin from version 0.14.5 JIRA .
Prerequisites
JIRA must be accessible via HTTPS
See https://confluence.atlassian.com/jira064/running-jira-over-ssl-or-https-720411727.html for instructions. This is necessary because Azure AD accepts only HTTPS-URLs for SAML endpoints.
Installation Procedure
Step 1: Install the plugin | Step 2: Setup the Azure AD (Substep A-D) | |
|---|---|---|
Step 4: Test | Step 5: Enable login redirection |
Step 1: Install the plugin
Install the plugin from the Atlassian Marketplace.
Click Add-ons under JIRA Administration on the top right corner of your JIRA interface. Then, you will be taken to Atlassian Marketplace. Search for SAML SSO and click on Free Trial to install.
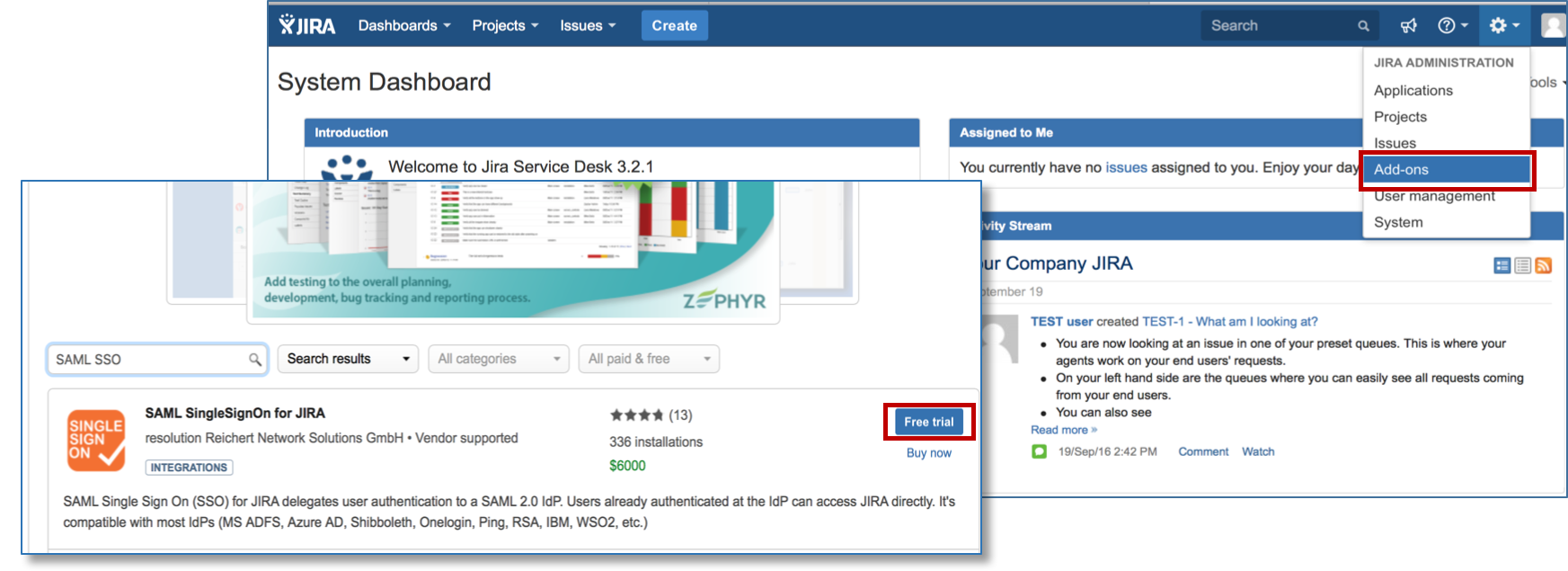
After installation succeeded, click on Manage, then choose Configure. Now, you are on the plugin configuration page.
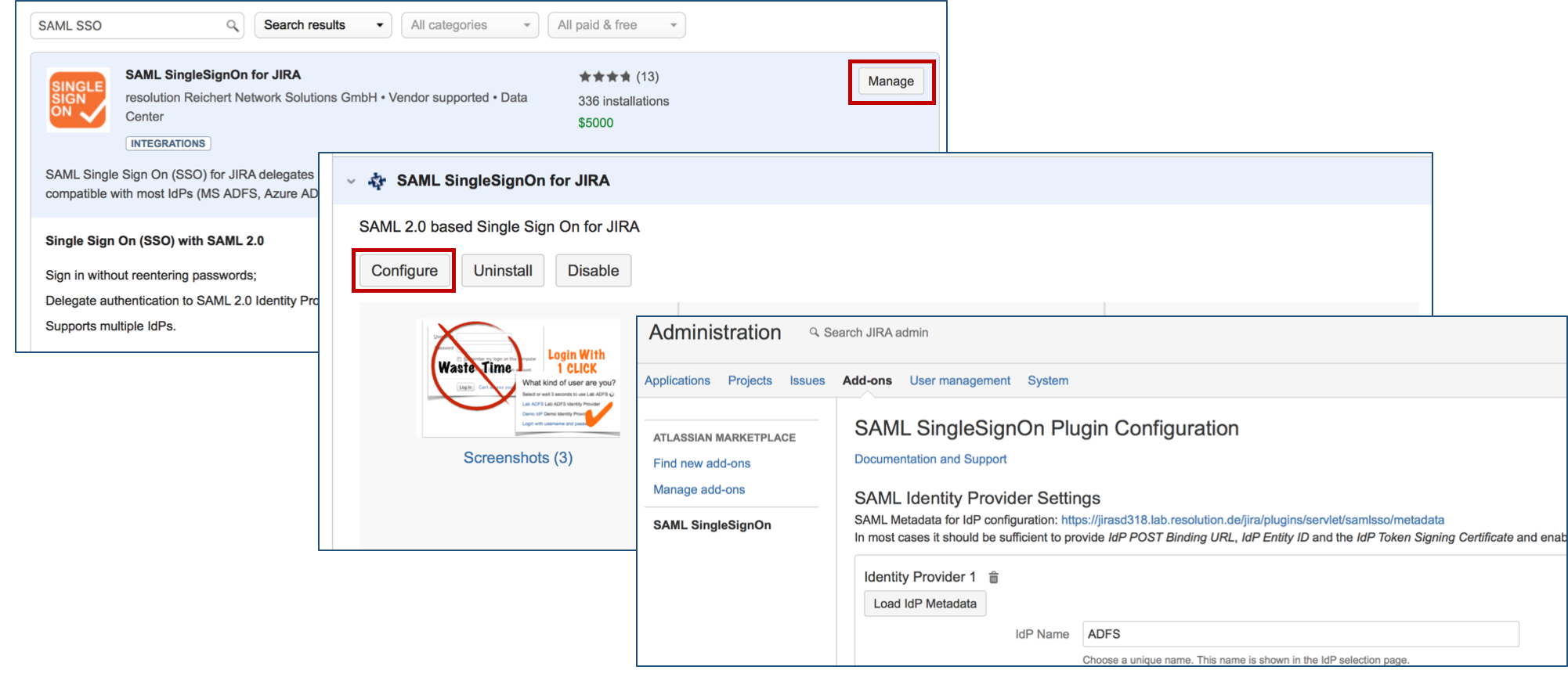
Step 2: Setup the Azure AD
Step 2 will be completed in Azure AD.
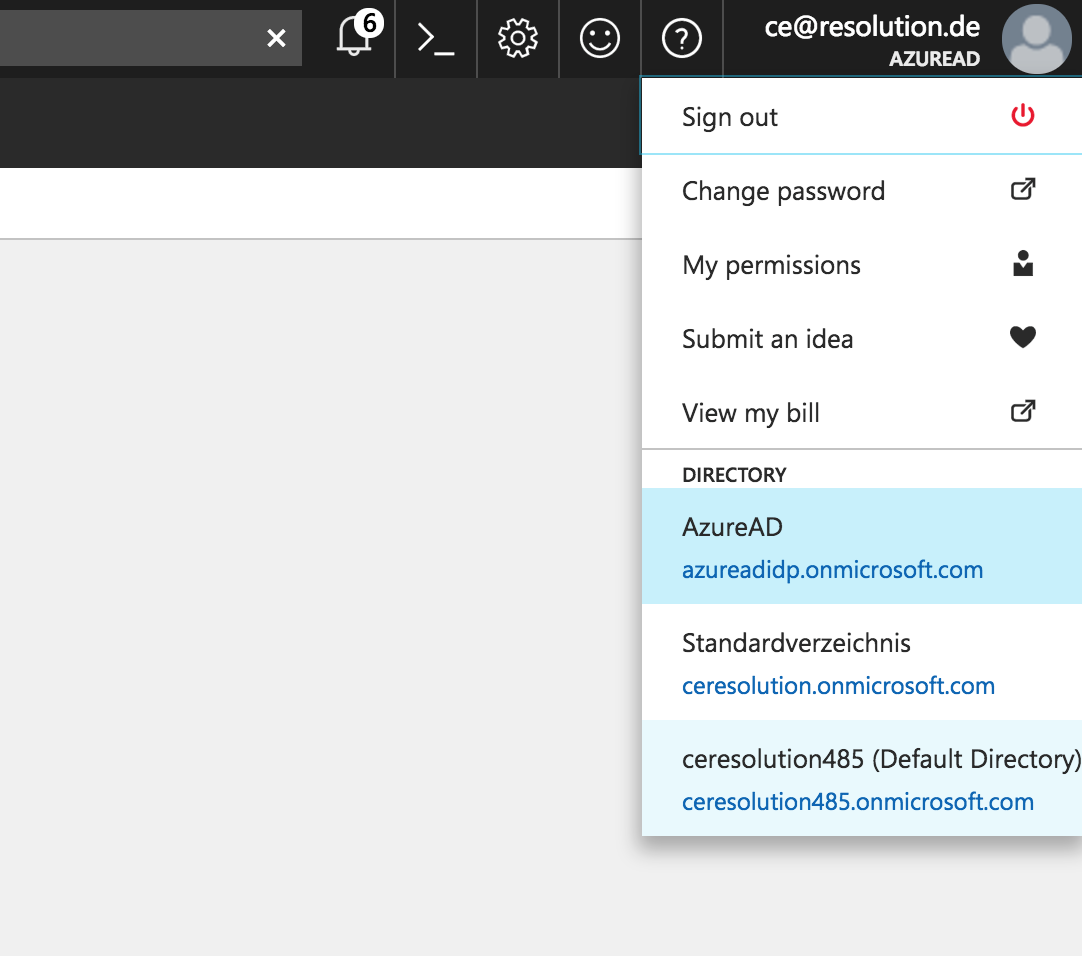
Select your Profile on the top right corner and select the directory that you want to use with SAML Single Sign On.
Select Azure Active Directory on the left navigation panel.
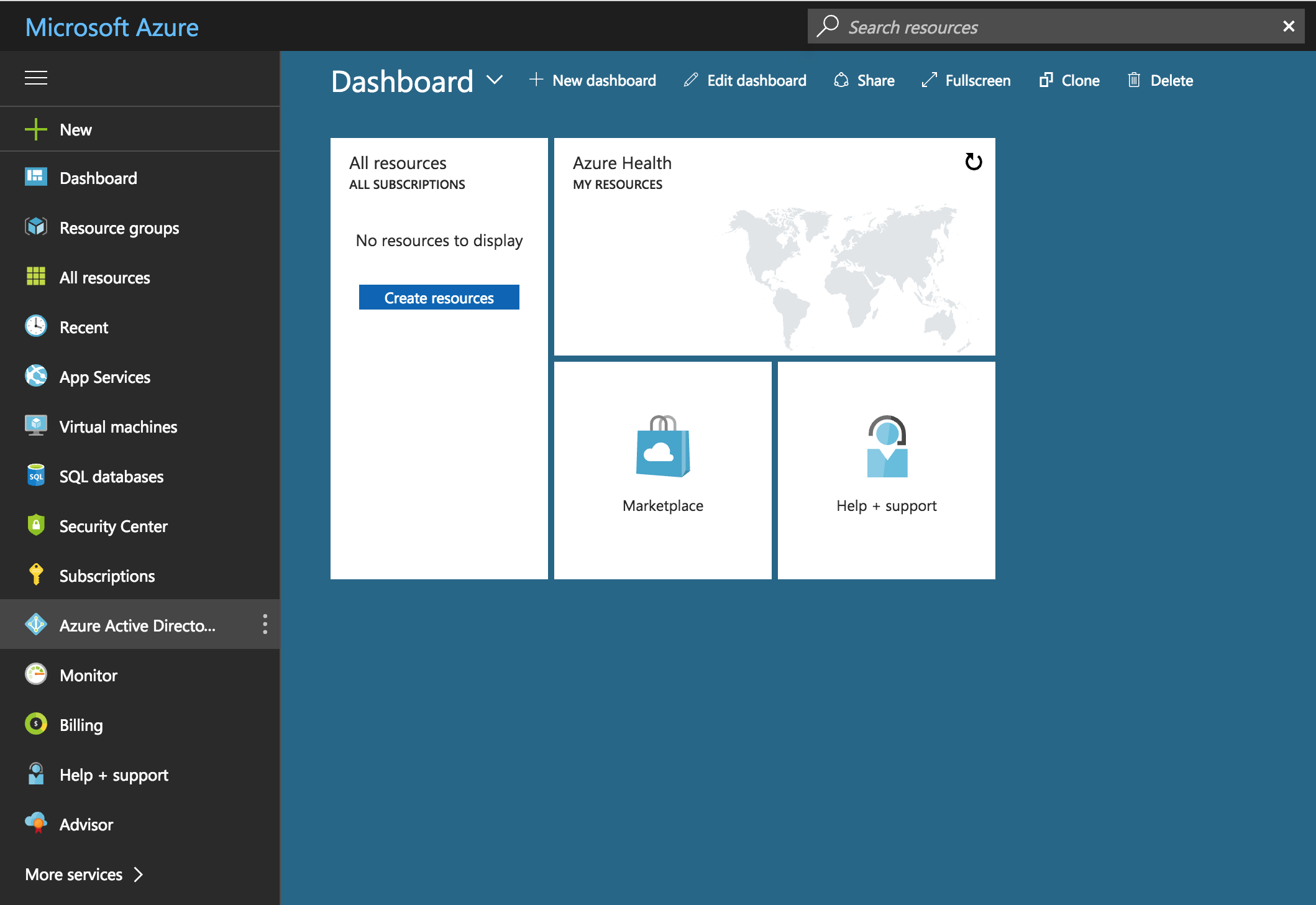
Under Manage select Enterprise applications.
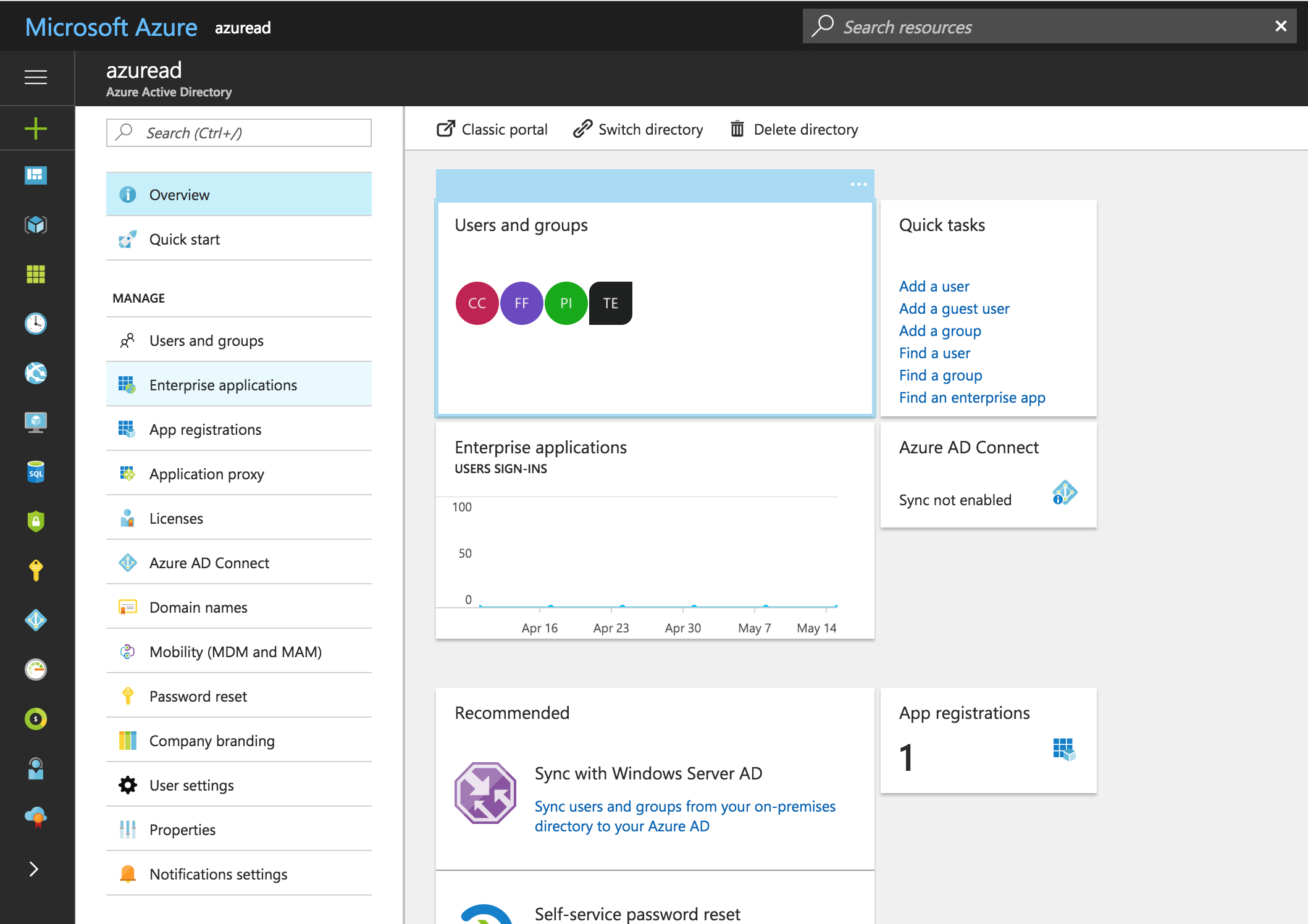
Select + New application.
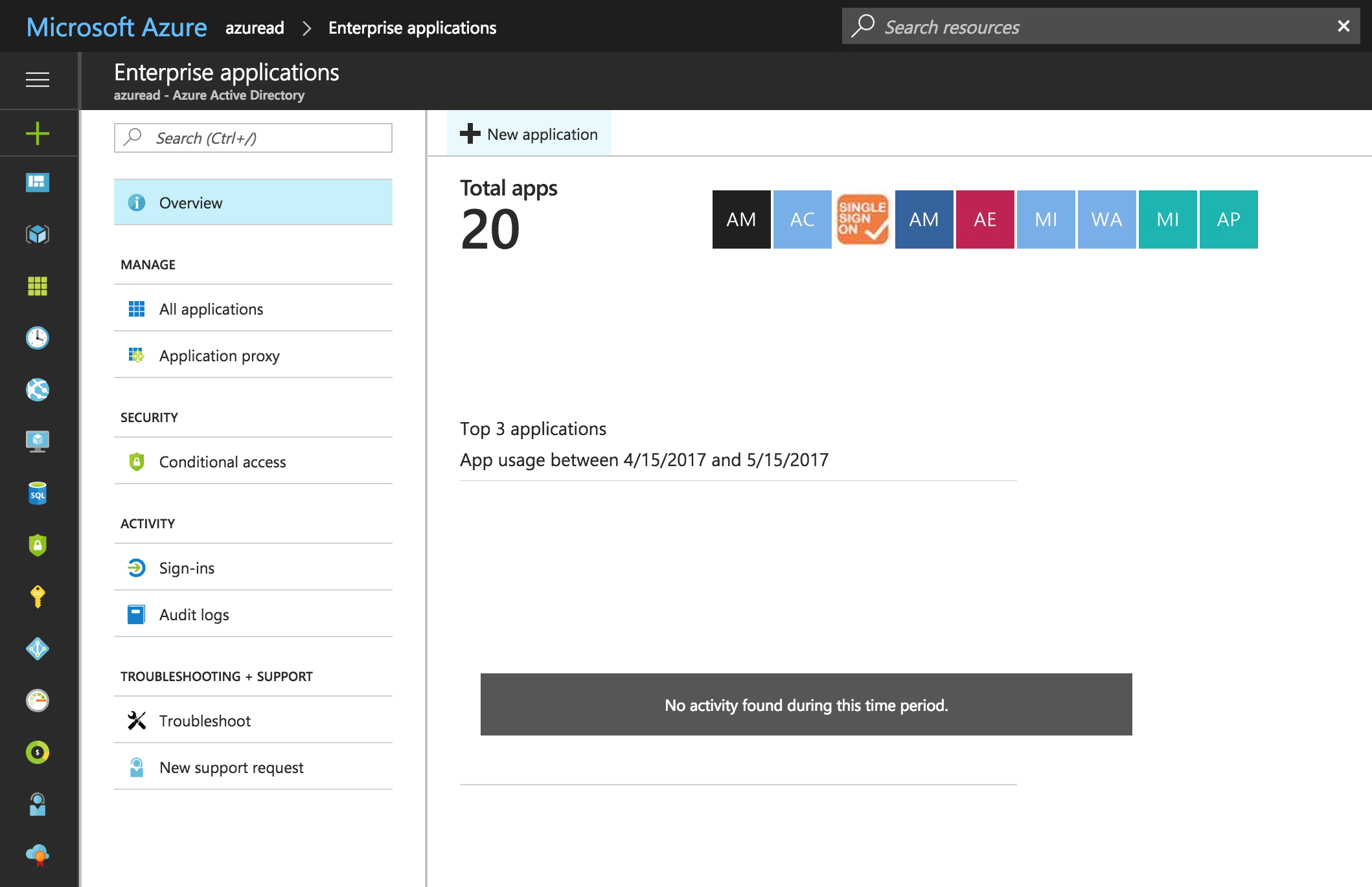
Under Categories select ALL.
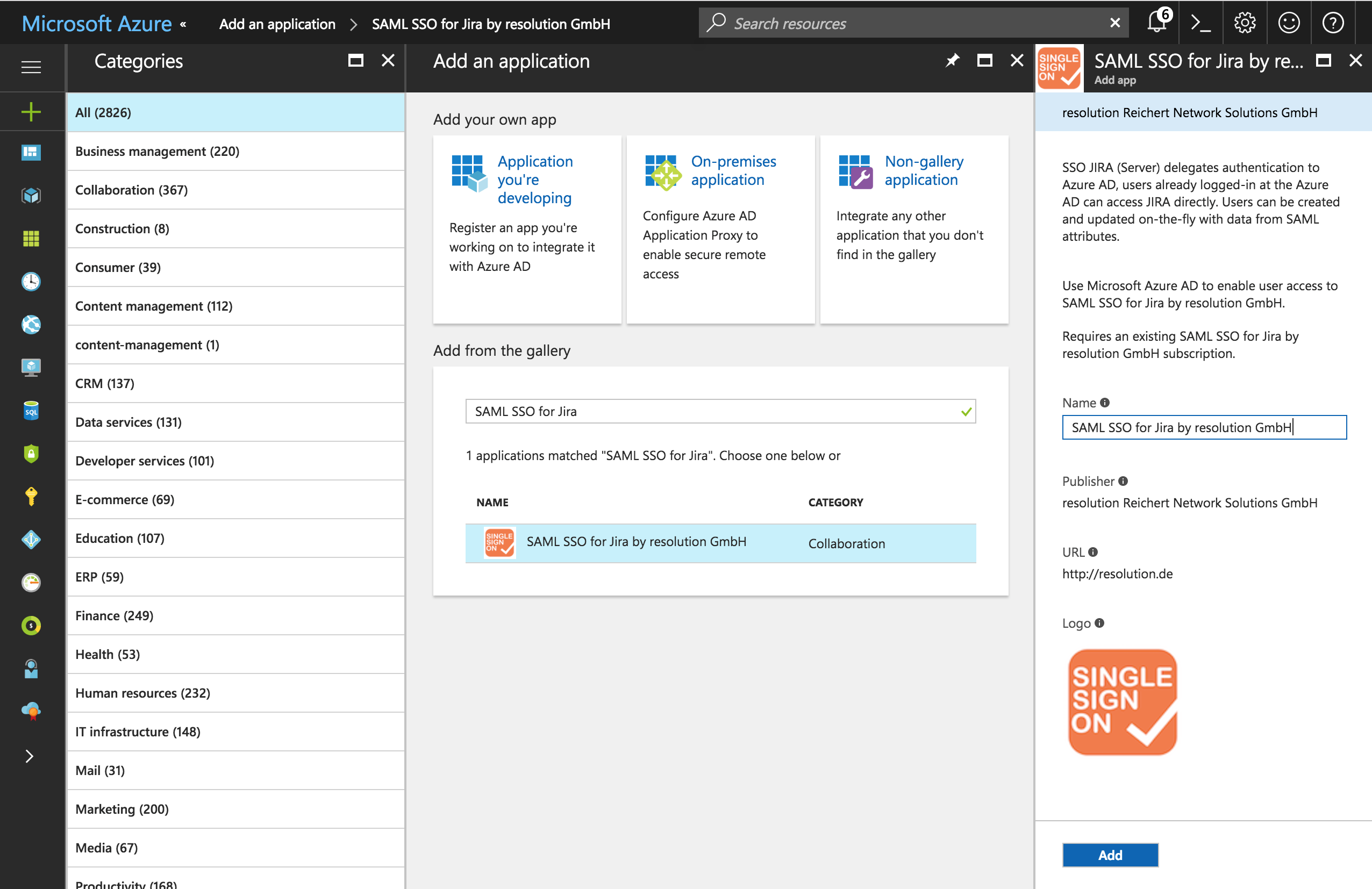
In the Add from gallery section search for SAML SSO for Jira.
Select the result SAML SSO for JIRA by resolution GmbH.
Choose a Name for the new application and click on Add.
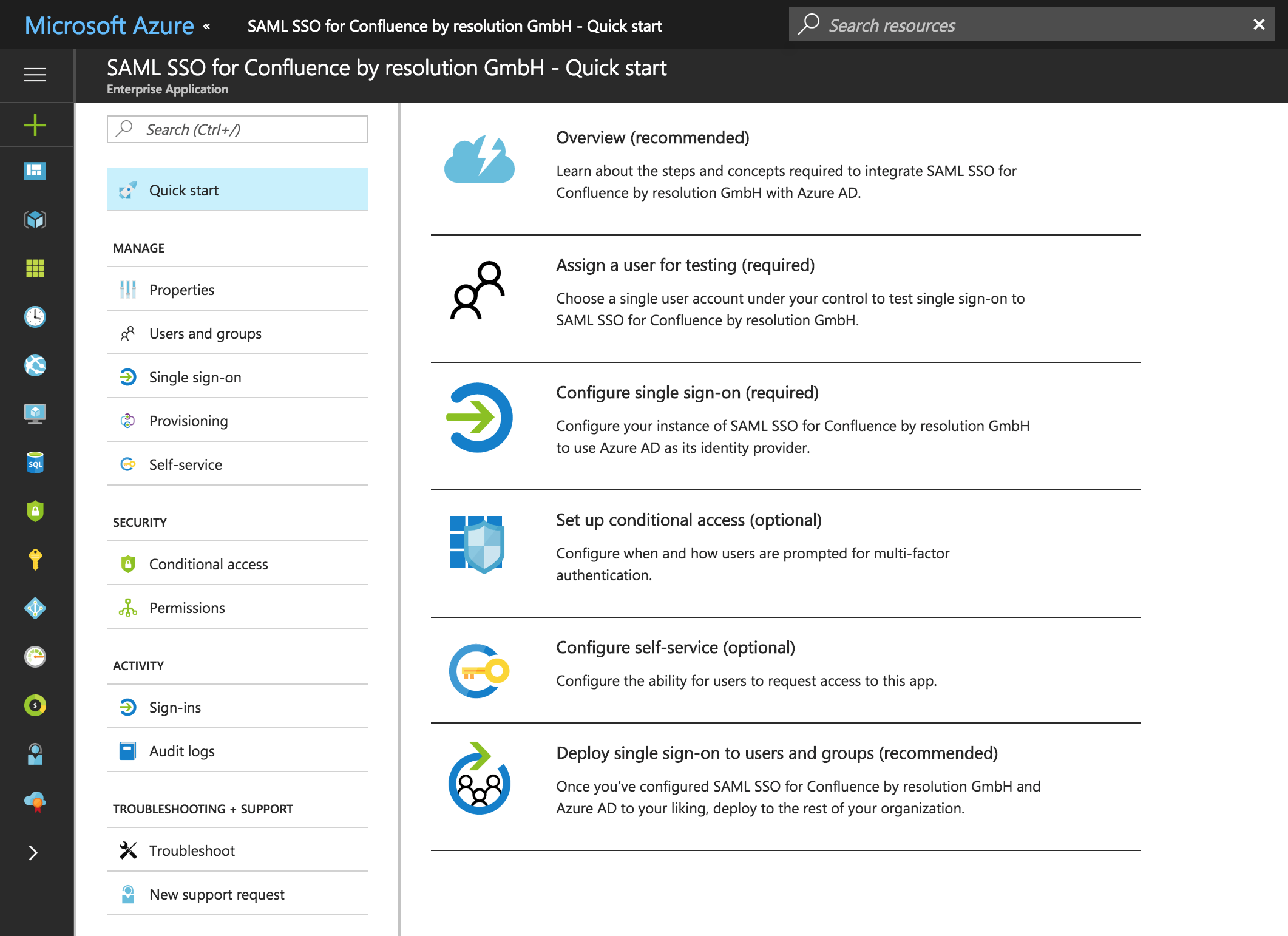
The next window opens automatically after adding the new application. The other way would be through Azure Active Directory → Enterprise applications → All applications → SAML SSO for Jira by resolution GmbH
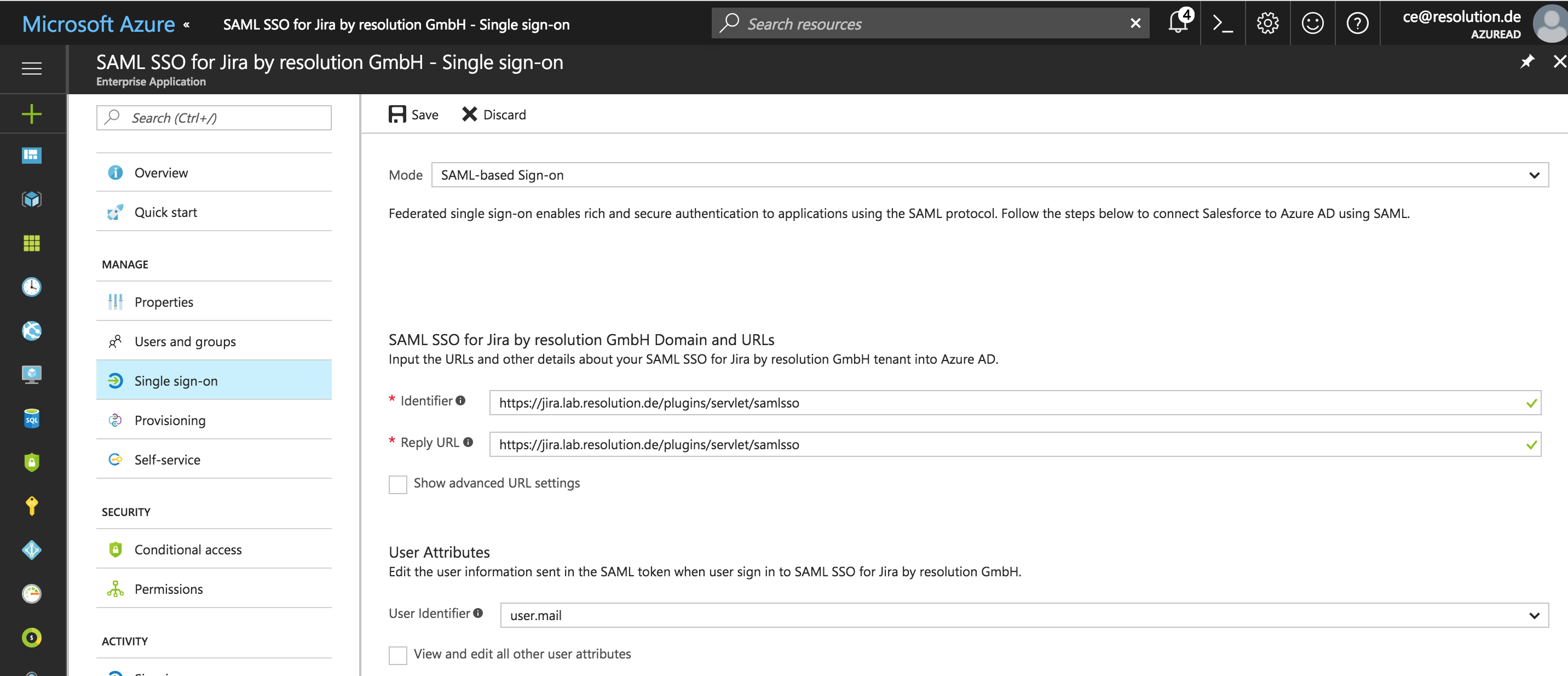
On the left Navigation Panel under MANAGE select Single Sign On or in the Quick Start selection choose Configure single sign-on (required).
Change Mode to SAML-based Sign-on.
As Identifier and Reply URL use "https://<jirabaseurl>/plugins/servlet/samlsso".
For User Attributes -> User Identifier select user.mail.
In the same window further down..
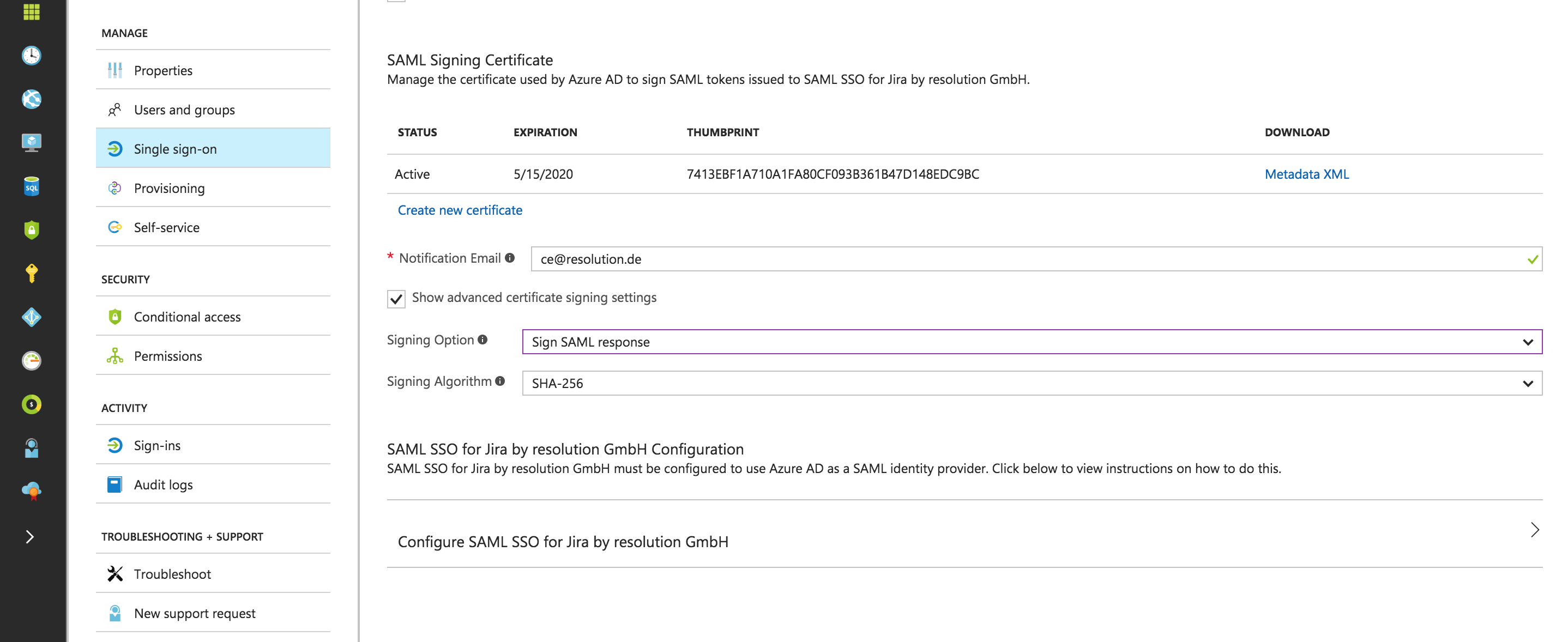
Select the Show advanced certificate signing settings so two new options are displayed.
For Signing Option select Sign SAML response.
For Signing Algorithm leave it with SHA-256.
Save the configurations with click Save (see screenshot above).
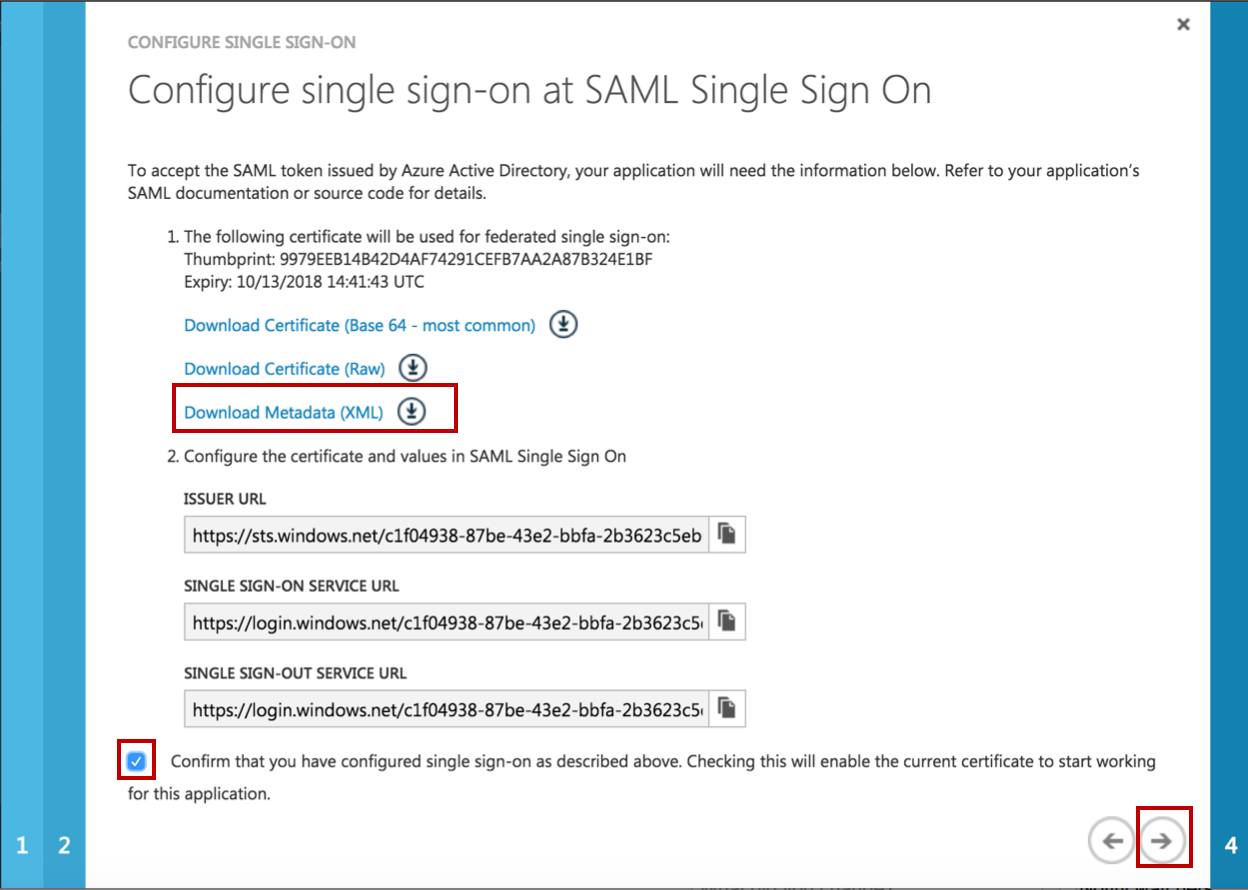
Now use the Metadata XML link (on the SAML Signing Certificate) to download the Azure AD metadata xml file. This file is required for the SAML plugin configurations in STEP X.
On the left Navigation Panel click on Quick Start (see screenshot above).
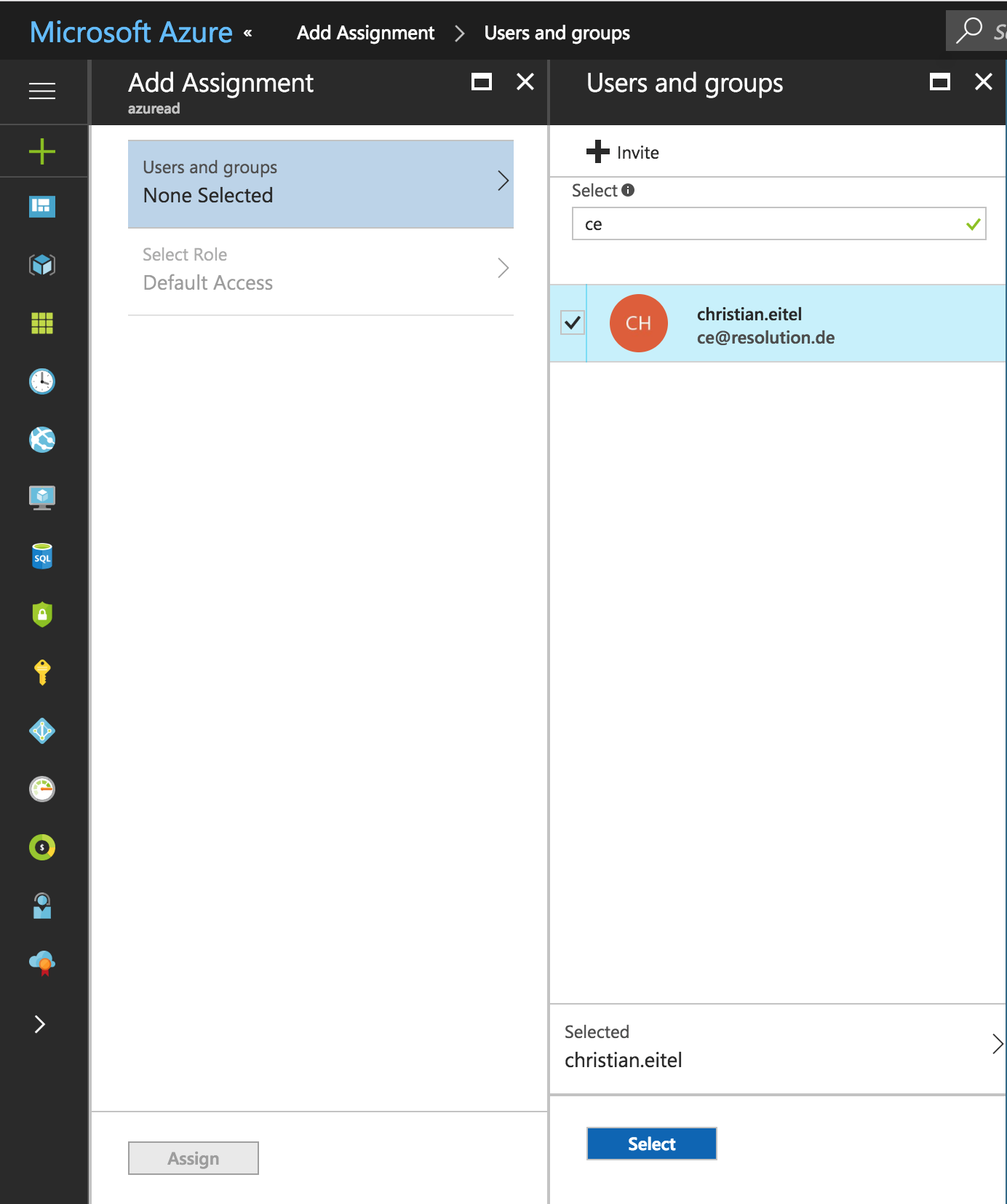
On the left Navigation Panel under MANAGE select User and groups or in the Quick Start select Assign a user for testing (required).
Substep A : Select your directory and start application dialog
Go to https://manage.windowsazure.com and login with your credentials.
Select Active Directory on the left navigation panel, and select the directory that you want to use with SAML Single Sign On.
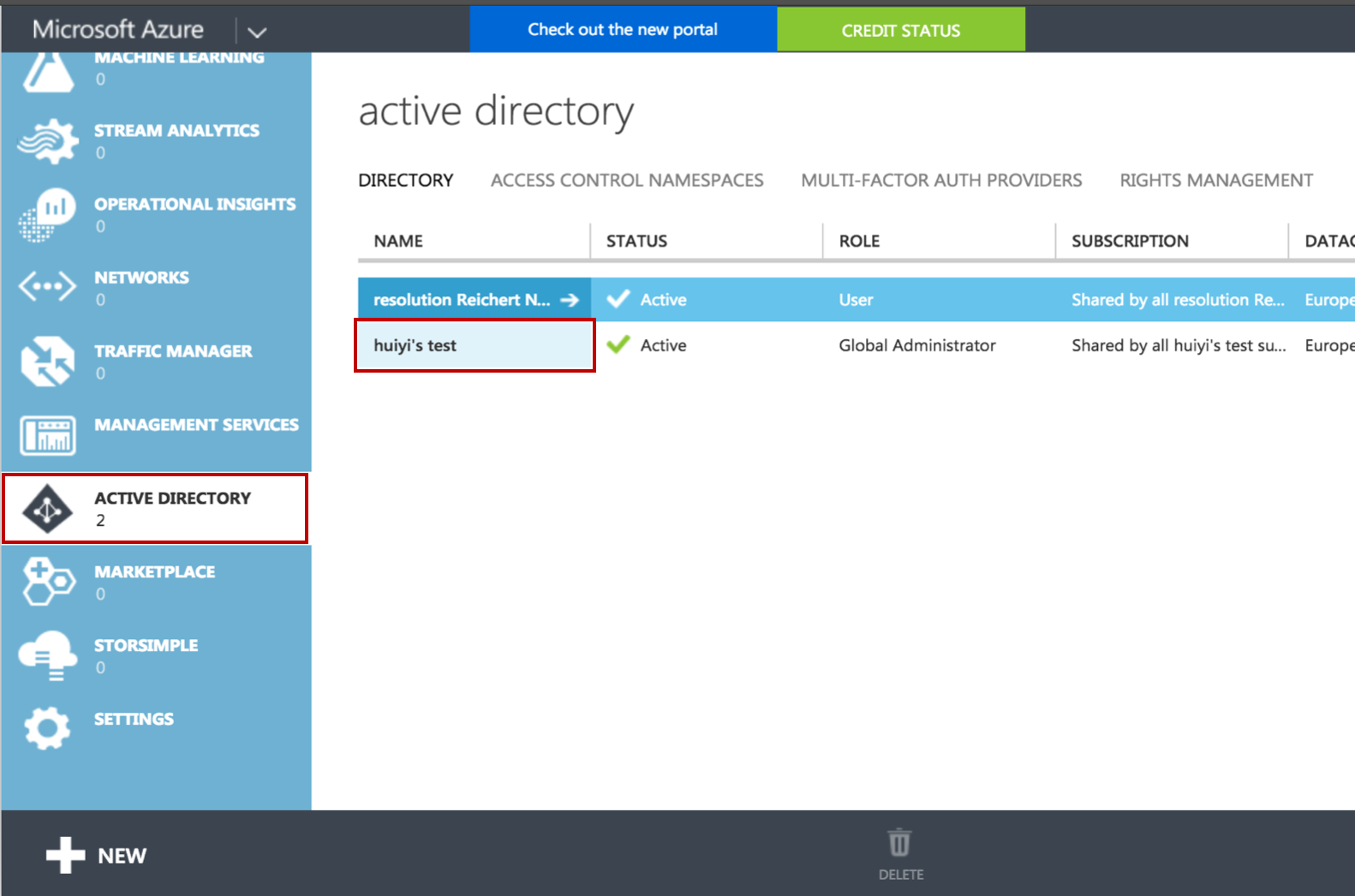
Click on APPLICATIONS, then click on ADD to start a new application dialogue
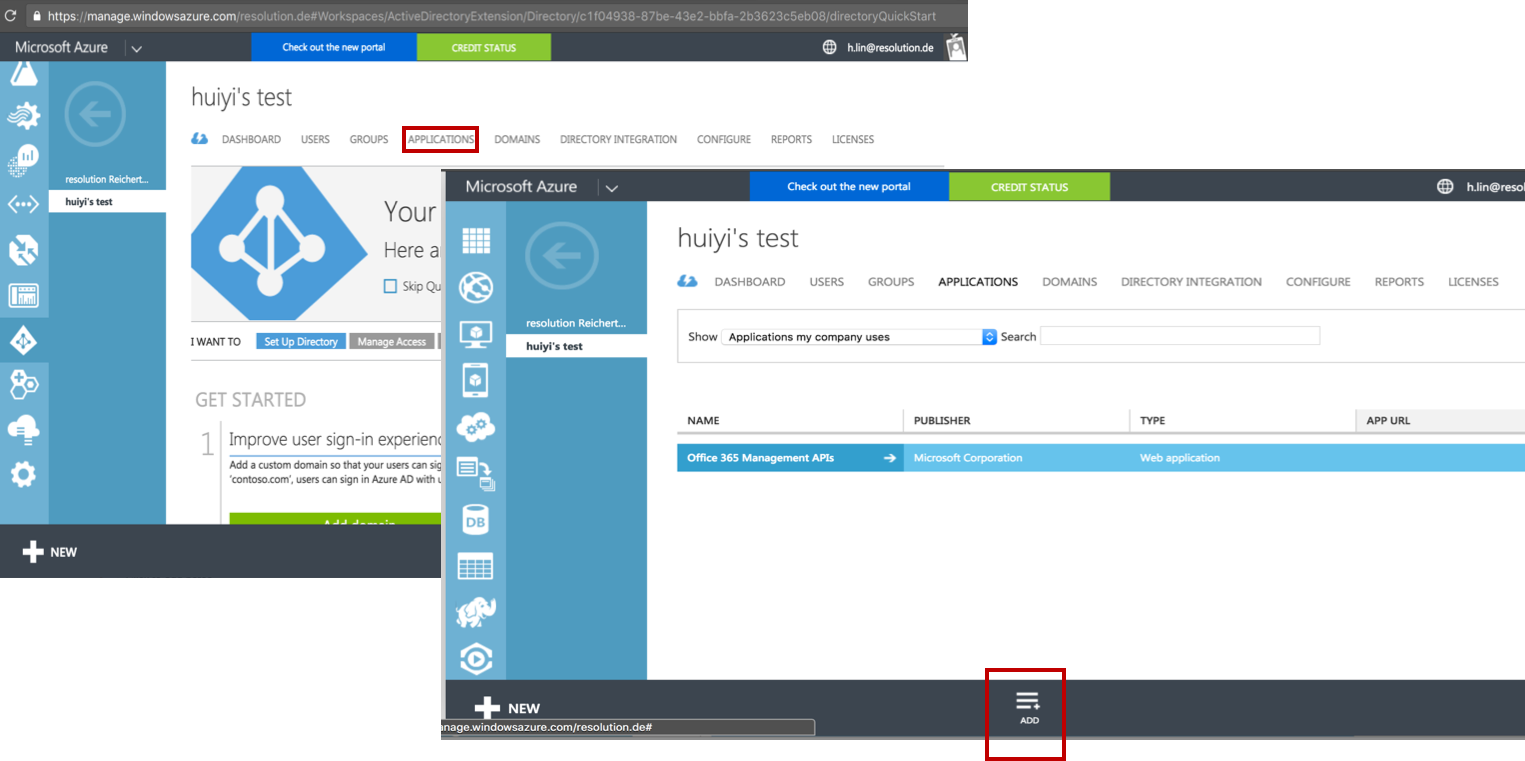
Substep B: Add a new application
Click on Add an application from the gallery.
Select Custom on the left navigation panel, and click Add an unlisted application my organization is using.
Then, fill in a name of your choice, e.g.. SAML Single Sign On in the NAME field.
Click on the Finish button at the bottom to add the application to your directory.
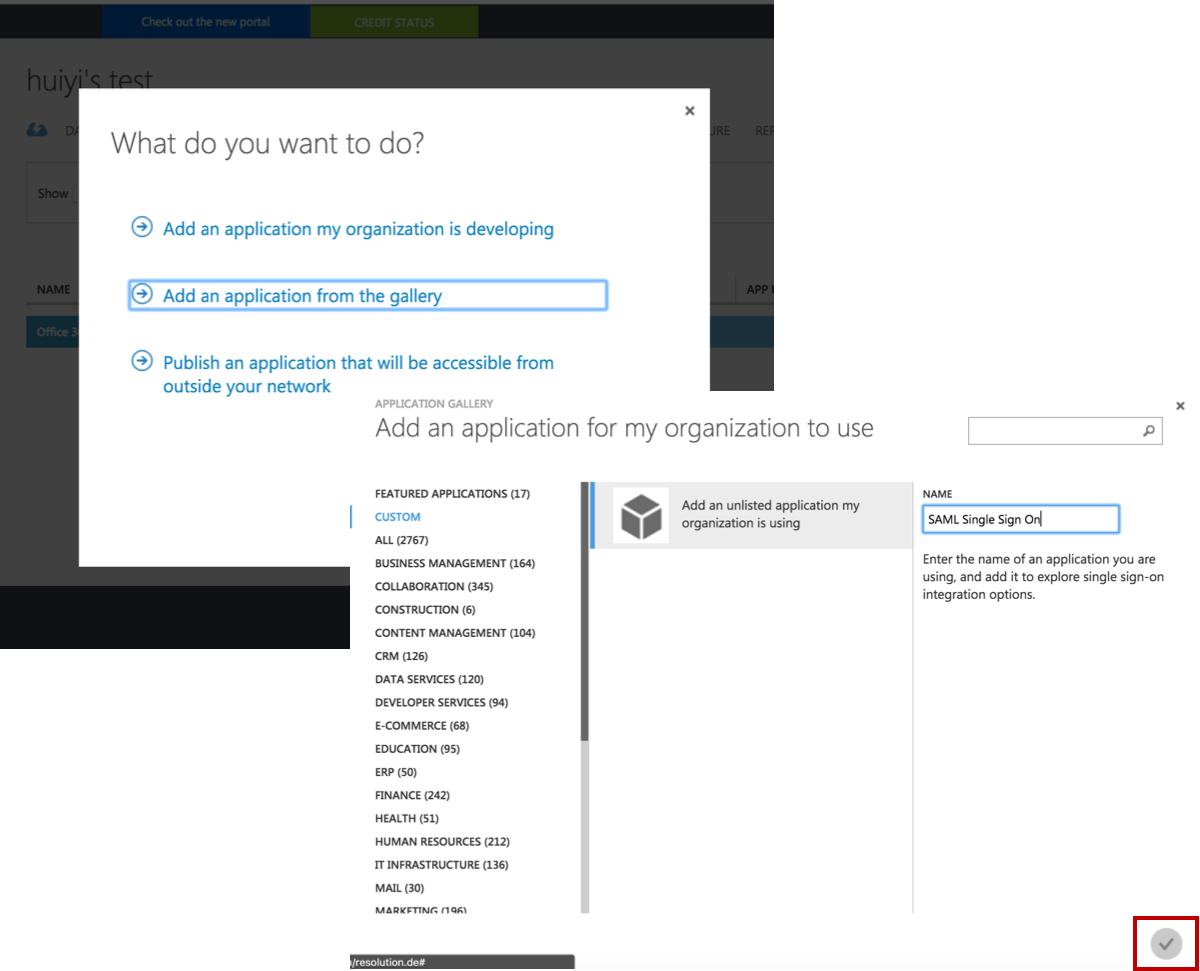
Substep C: Configure the new application
Click on Configure Single Sign On. In the Pop-up window choose select Microsoft Azure AD Single Sign-On, then click on Next.
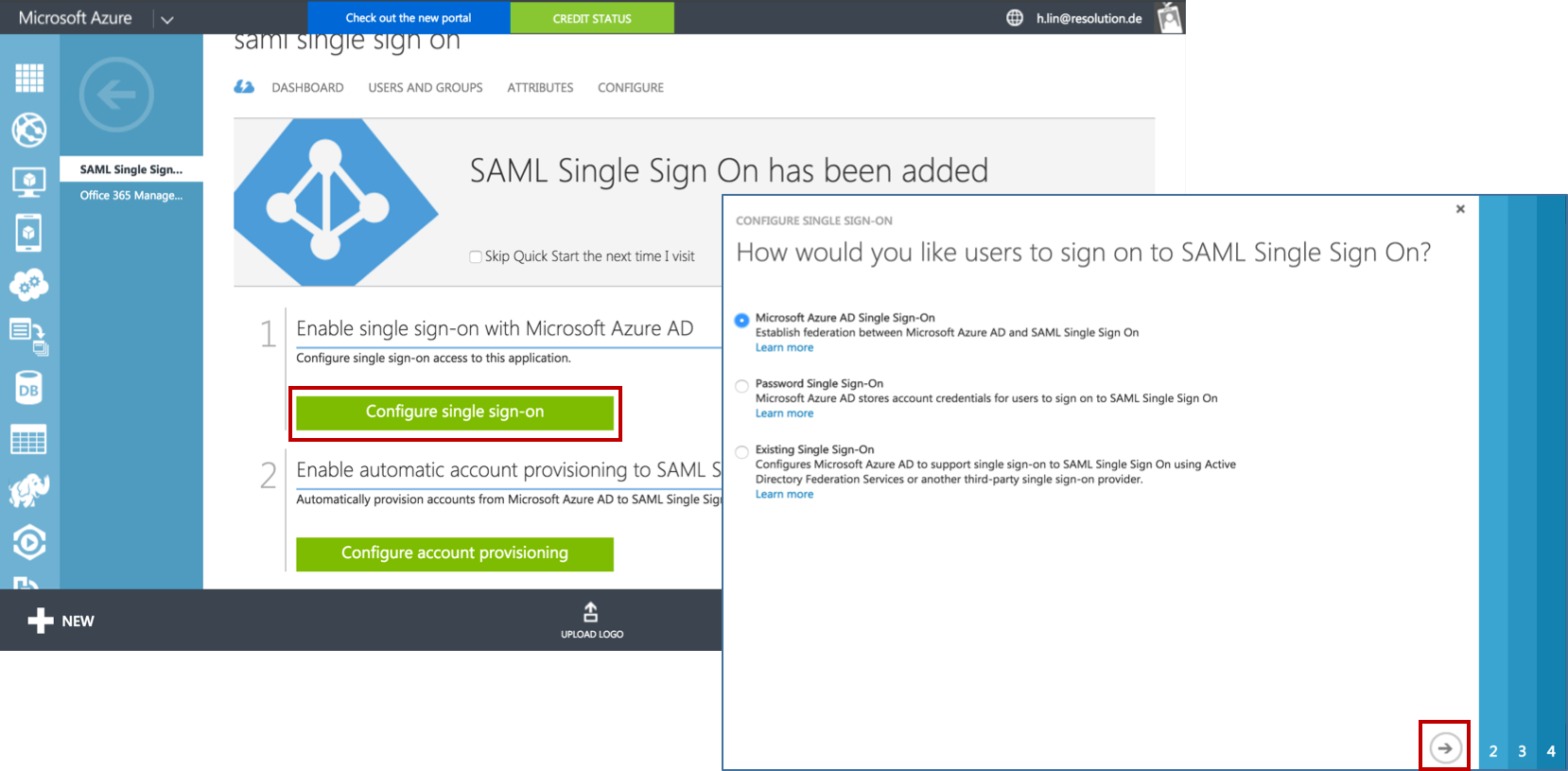
In the IDENTIFIER and REPLY URL fields please fill in your JIRA SAML Single Sign On URL :
https://<your-JIRA>/plugins/servlet/samlsso. (e.g. https://JIRA318.lab.resolution.de/plugins/servlet/samlsso)Click Next.
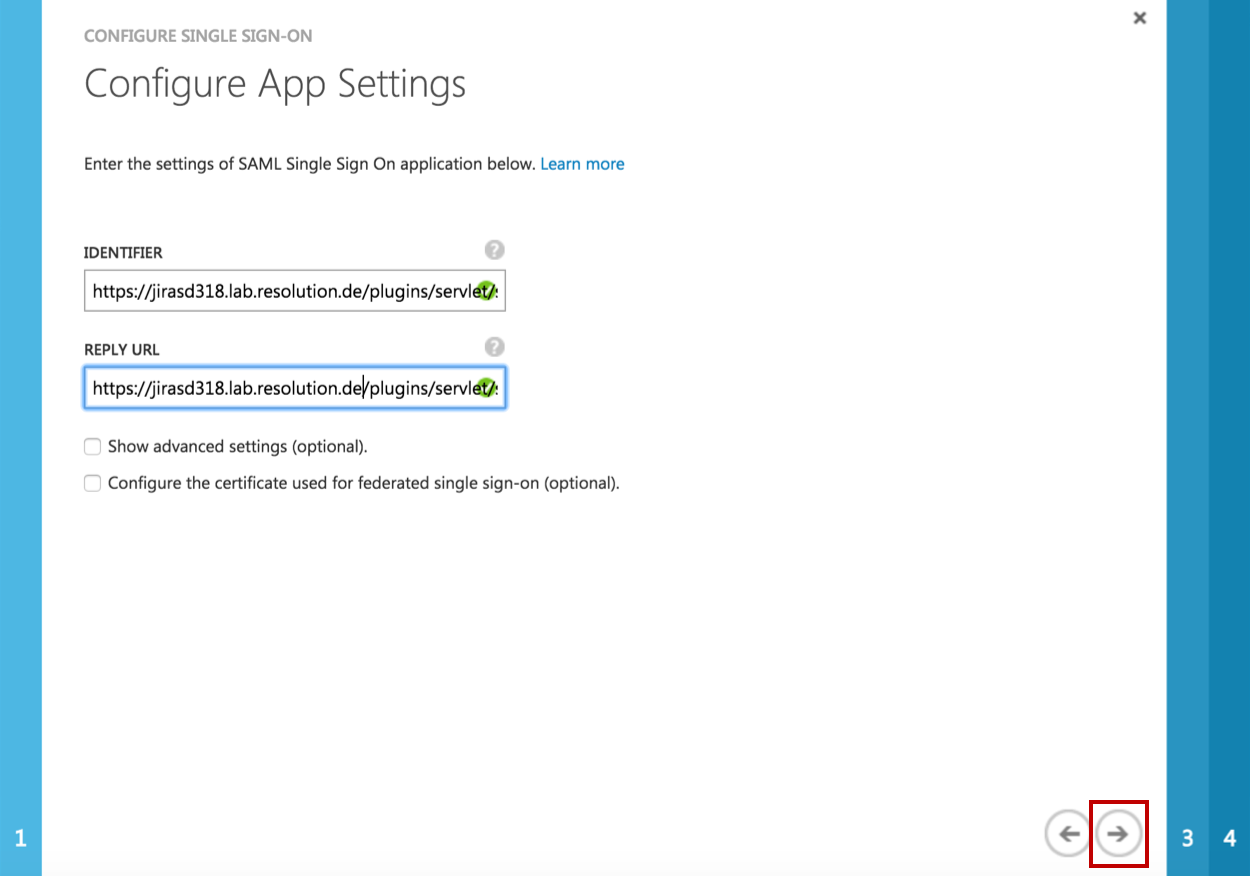
Click on Download Metadata (XML) to download the FederationMetadata.xml. We will configure the SAML Single Sign On with the Metadata from Azure AD in Step F.
Check the Checkbox Confirm that you have configured... .
Click on Next.
Fill in a NOTIFICATION E-MAIL for which you want to get notifications for this application.
Click Finish to complete the application configuration. Then you come back to the overview page of SAML Single Sign On and continue with Substep D to grant user access.
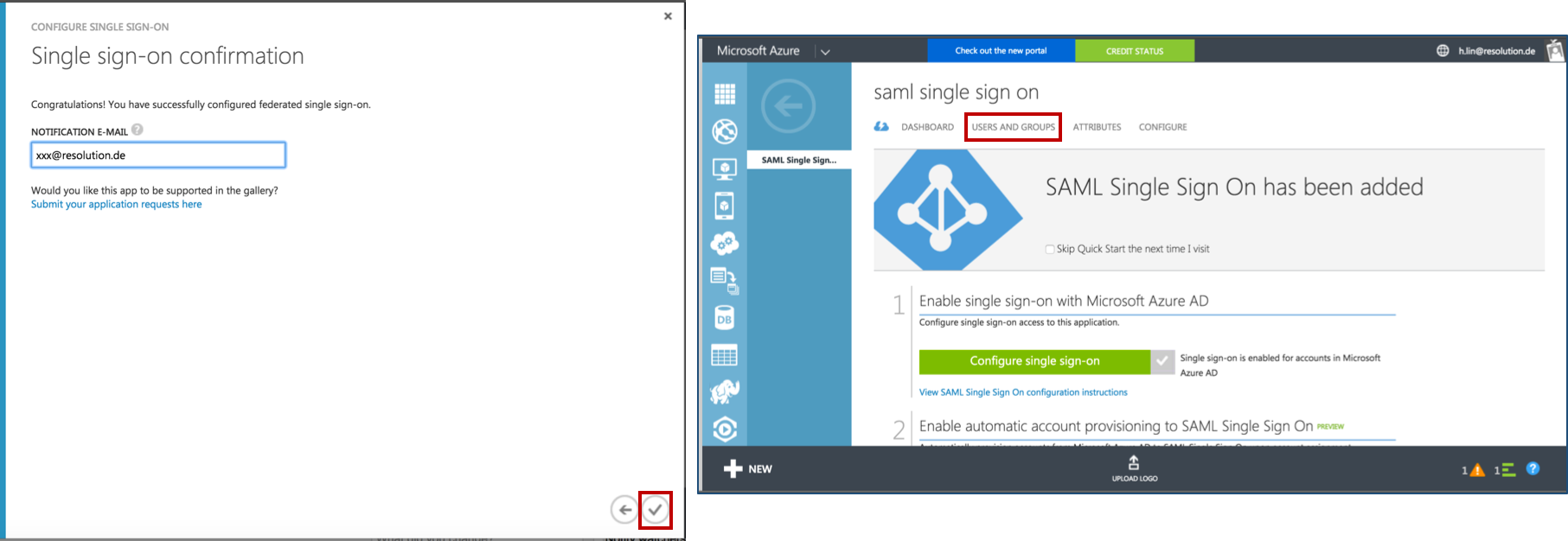
Substep D: Grant access to users
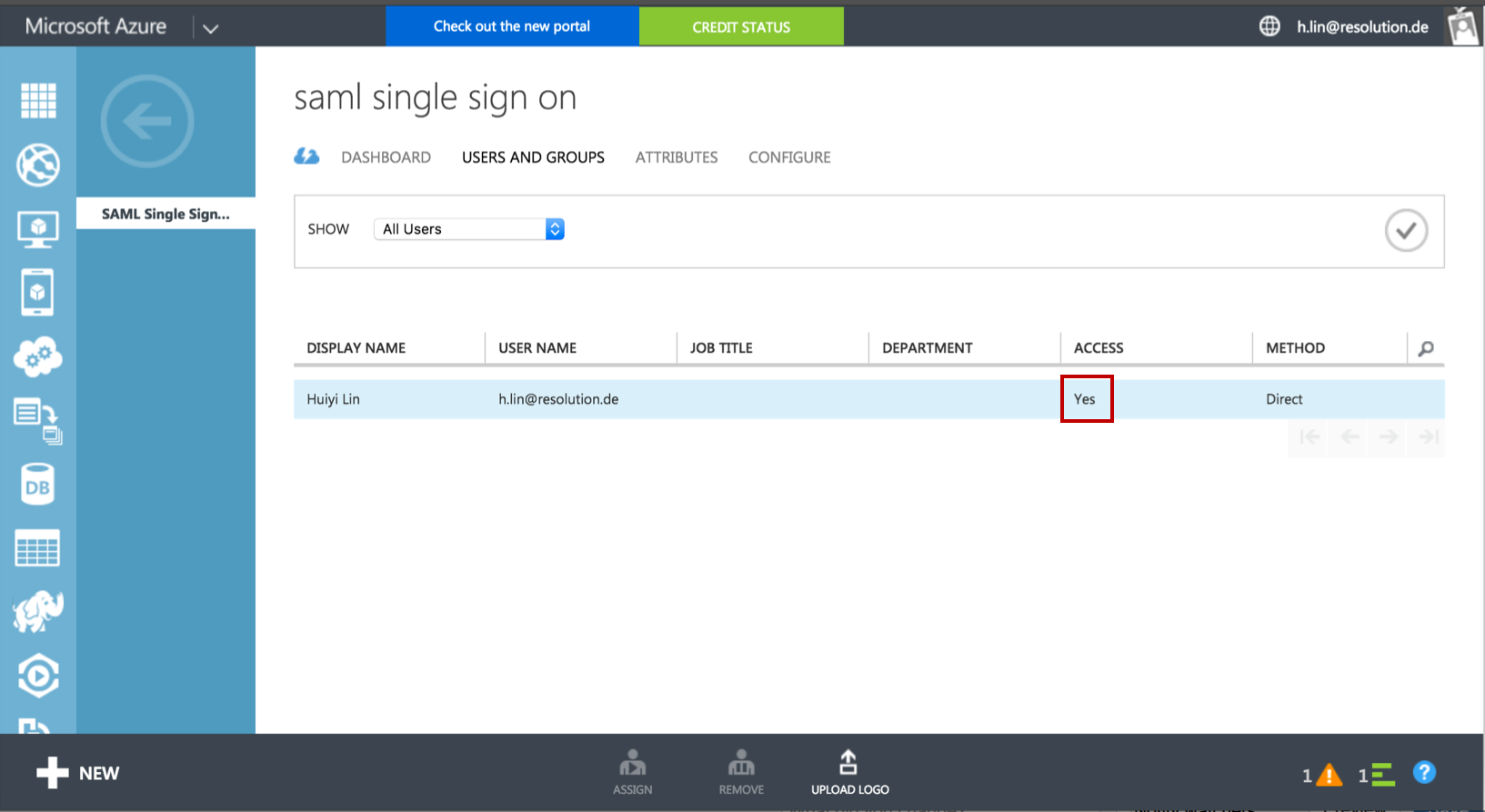
Click on USERS AND GROUPS and select All Users in the SHOW drop down field. Then click on the tick on the right side to show all users.
Select the user which you want to grant access for this application, and click on ASSIGN at the bottom.
Then, click on YES at the bottom of the black pop-up window to confirm to enable access for selected users.
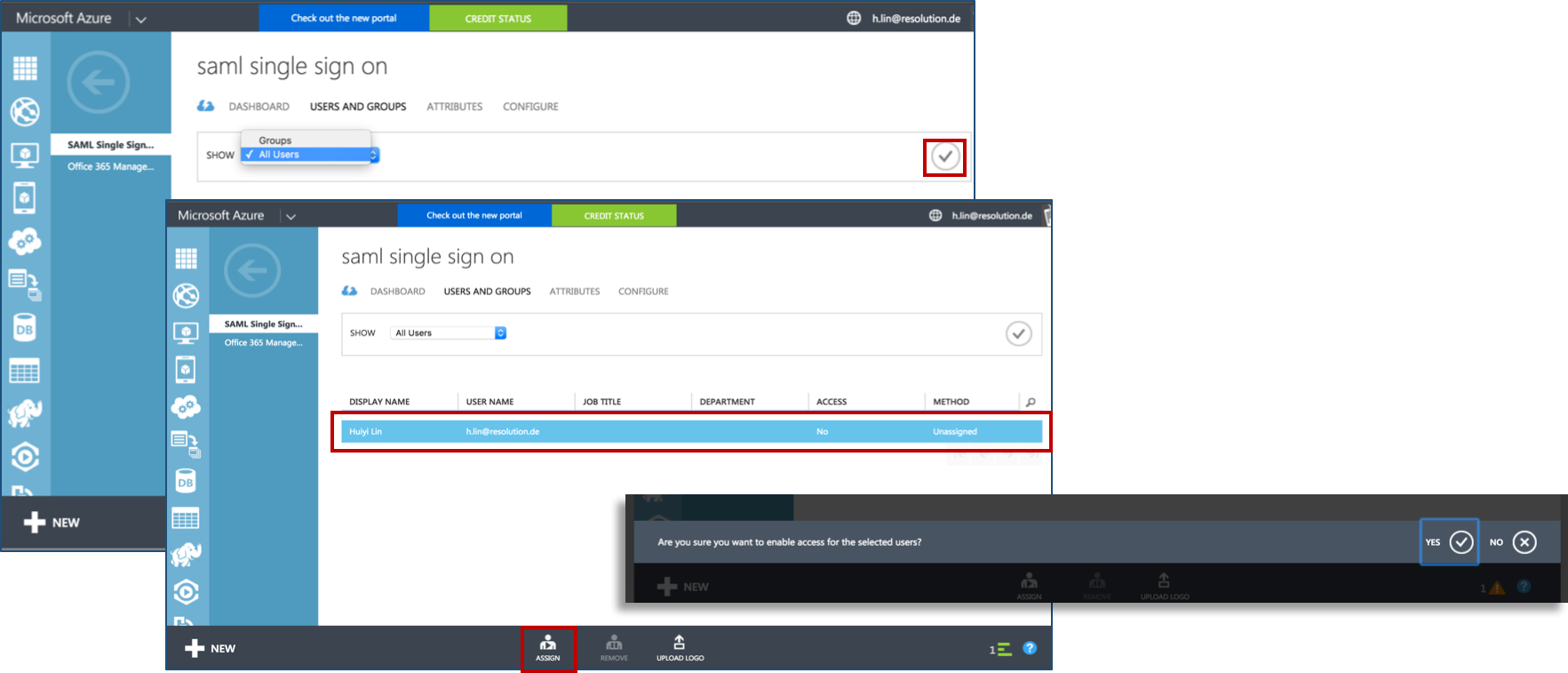
Finally, review “Access” status to see if the user has been successfully granted access to application now.
Step 3: Configure the Plugin
To continue Step 3, please go back to the plugin configuration page opened in Step1.
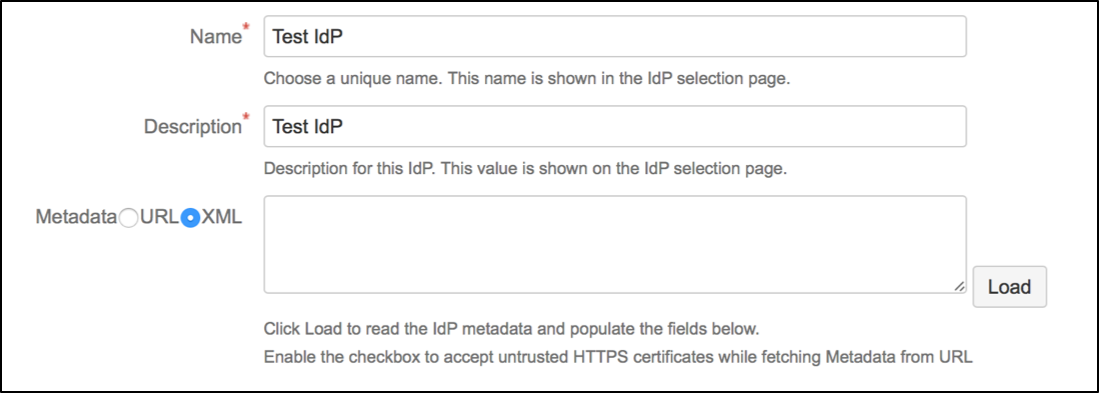
Substep A: Load Azure AD Metadata
The recommended way to setup the Azure AD on the SAML Single Sign On is to import the Azure AD Metadata .
Select load from XML and paste in the content from the FederationMetadata.xml (downloaded in Step2 Substep C) into the field below.
Click on Load to load the Azure AD configurations into the plugin.
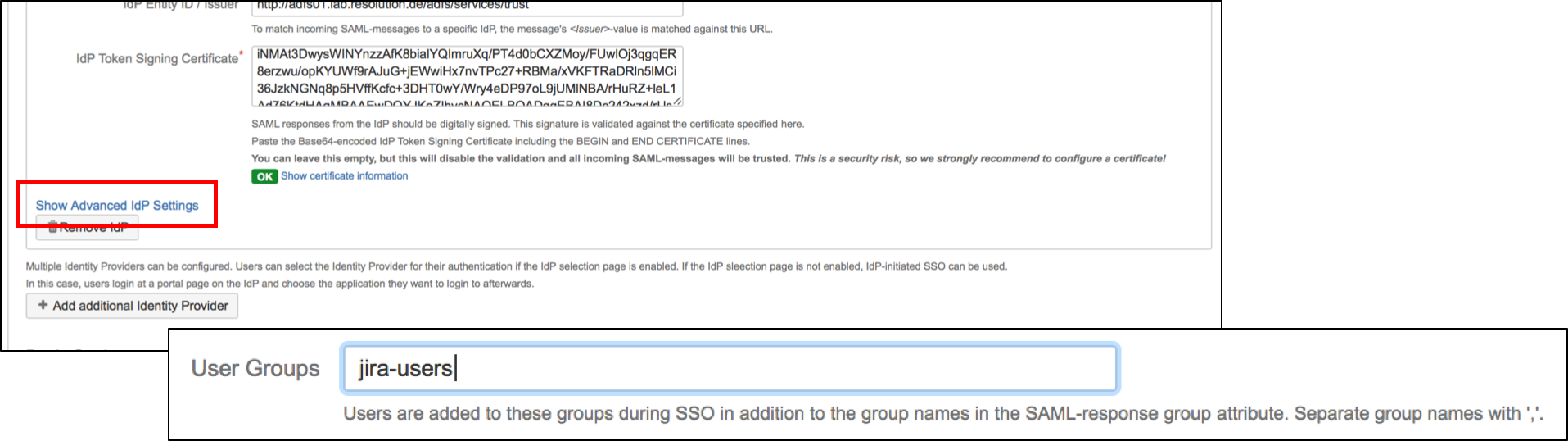
Substep B: Configure general JIRA groups in Advance IdP Settings
If a user logs in using SAML, he will be added to the groups specified in the User Groups section. This applies to all users. The user is assigned to these groups in addition to the groups in the SAML-response's attribute.
The standard group in JIRA 6 is called jira-users.
The standard group in JIRA 7 is depending on which JIRA Version you are using:
JIRA Version | Standard group |
|---|---|
JIRA Core | jira-core-users |
JIRA Software | jira-software-users |
JIRA Service Desk | jira-servicedesk-users |
Click on show Advanced IdP Settings, find User Group in the drop down menu.
Click Save settings to store the configuration
Step 4: Test
In a separate browser, open the URL
https://<your-JIRA>/plugins/servlet/samlsso.You should be authenticated by your Azure AD and redirected to the JIRA Dashboard.
Step 5: Enable login redirection
After testing, you can enable the login page redirection to finally activate the plugin. After checking the Enable SSO Redirect checkbox and clicking Save settings, requests to the JIRA login page should be redirected to the Azure AD.

If Enable SSO Redirect is enabled, you can login to JIRA manually by browsing https://<your-JIRA>/login.jsp?nosso. Use this URL if you need to login a local user unknown to the Azure AD or if there are any issues with Single Sign On.
You might also find following documentation helpful:
