SAML SSO Toolbox
The SAML SSO Toolbox includes additional features for the SAML SSO add-ons (JIRA, Confluence, Bitbucket, Bamboo and Fisheye/Crucible) and can be used for free. It replaces the old Clearssoconfig plugin, which can remove the SAML Single Sign-On configurations from the database. As a new feature, your user's local passwords can be cleared now.
Use this tool only in cooperation with our customer support.
Installation
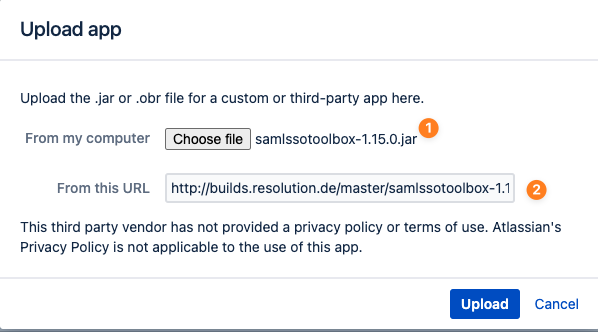
You can either download the SAML SSO Toolbox and upload the file from your browser (1) or use the URL (http://builds.resolution.de/master/samlssotoolbox-1.17.1.jar) (2), provided your Atlassian instance can access it.
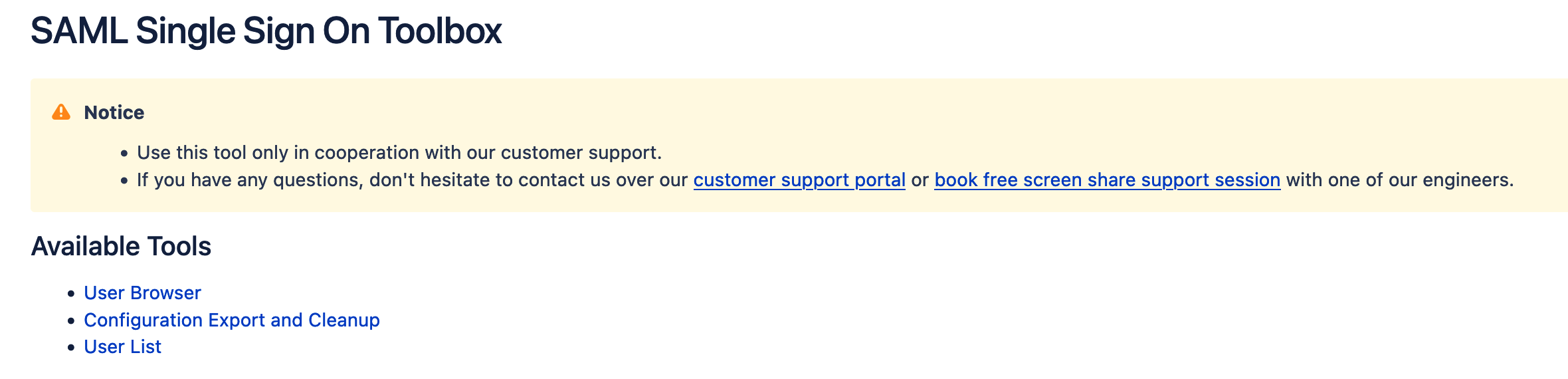
Usage
Open the installed Plugin in the Plugin Manager and select Configure or open the URL "https://<application-baseurl>/plugins/servlet/samlsso/toolbox" directly.
On the main page, you can select between the included tools:
Manipulating users
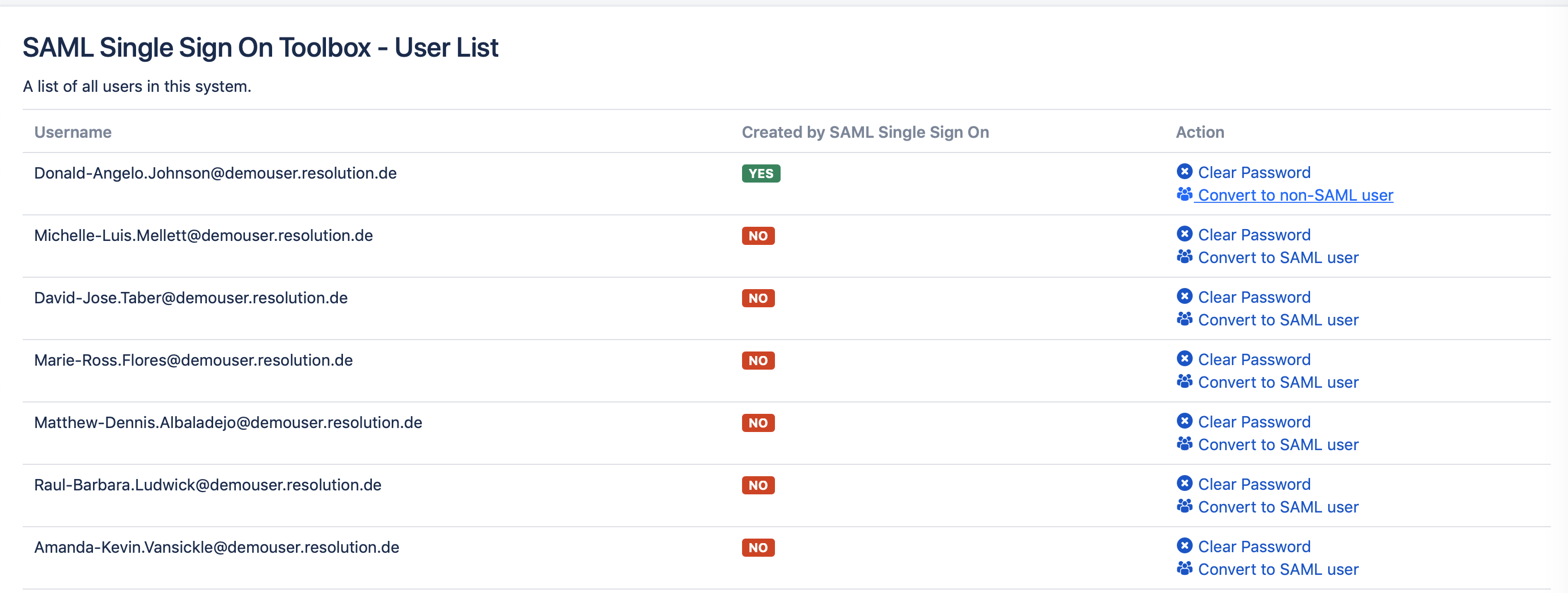
The SAML SSO User List shows all your users from your internal directories (sorted alphabetically) and indicates which users are created by the SAML SSO add-on. Furthermore, under Actions, it is possible to:
Clear the Password of your users (not possible for administrators), which sets the user password to a special value, resulting in the user not being able to log in with a password. This ensures that your users can only use the Single Sign-On for authentication. Administrators can easily reset the “cleared” user password in the application user configurations.
Convert a non-SAML user to a SAML user and vice versa. This adds or removes the same flag that is added when a user is created via the Just In Time user provisioning.
It's also password to set users passwords via the REST API of the SAML SSO Toolbox:
After installing it, for setting users' passwords, please use the following REST command:
- curl -X "PUT" "https://<base_url>/rest/samlsso-toolbox/1.0/users/<username>?directoryId=<directoryId>" \ -H 'Content-Type: application/json; charset=utf-8' \ -u '<sysadmin>:<password>' \ -d $'{ "ATTR_PASSWORD": "<new_password>" }'
You would need to substitute the following in the above command:
<base_url>: with your Confluence base URL
<username>: with the username of the user for whom you'd like to set a password
<directoryId>: with the directory ID of the UserSync Azure directory ID, which you can when you go to the User Directories page, click on the "Directory Configuration Summary" link at the bottom of the page, look up for the Azure directory and retrieve its Directory ID
<sysadmin>: with your admin username
<password>: with your admin password
<new_password>: with the new password that you want to set for the user
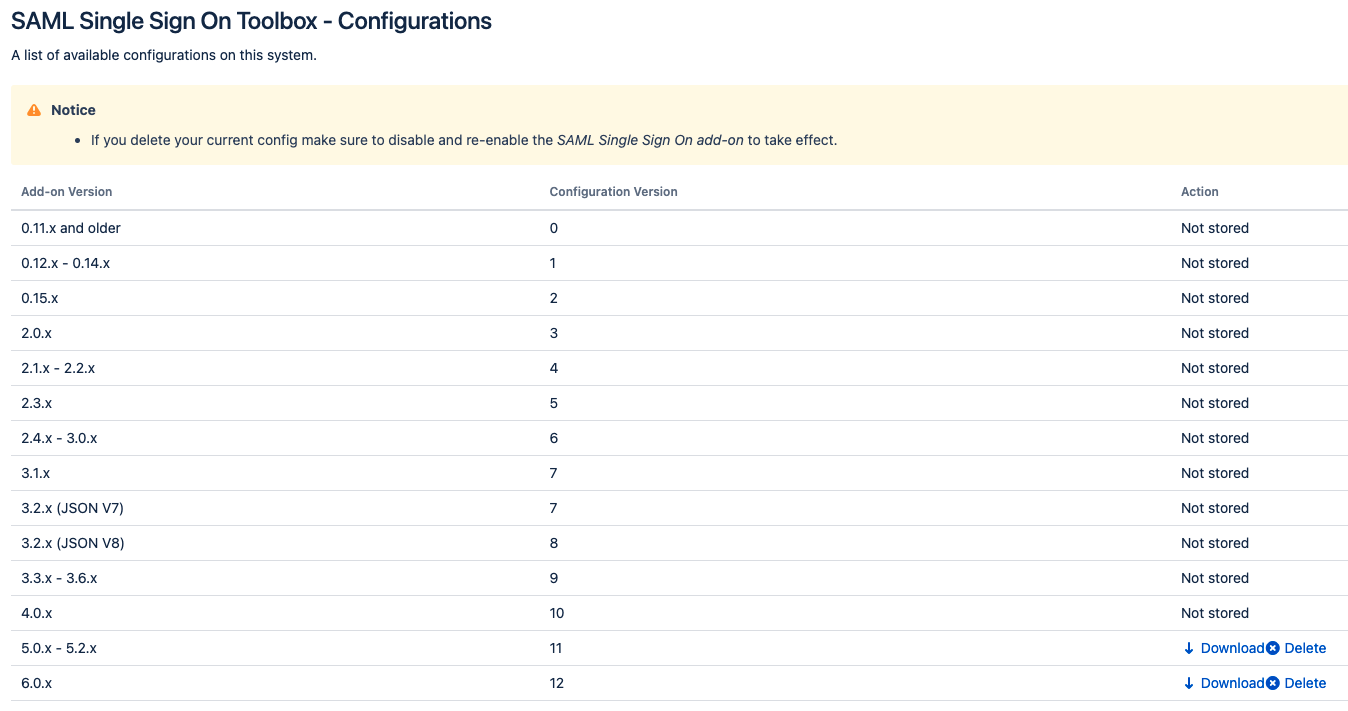
SAML SSO Configurations Export and Cleanup
Please make sure to disable and reenabled the SAML Single Sign-On app using the Plugin Manager after manipulating the saved configurations.
This feature shows all installed SAML SSO configurations as versions in a list. If a version is available, the configurations can be downloaded (Download XML) or removed (Delete).
Reimport downloaded configurations
Currently, it's not directly possible to import a configuration that was downloaded with the help of the SAML SSO Toolbox into the main SAML Single Sign On app. If you want to do that you need to slightly modify the downloaded configuration to make the import possible. Use this template and replace the content from the download file at the marked position:
- <?xml version="1.0" encoding="UTF-8" standalone="yes"?>
- <supportInfo>
- // enter the downloaded content here (<configurationData>...</configurationData>)
- <ssoPluginInfo/>
- </supportInfo>
User Browser
Usage
Click the User Browser link in the SAMLSSO Toolbox to access the User Browser.
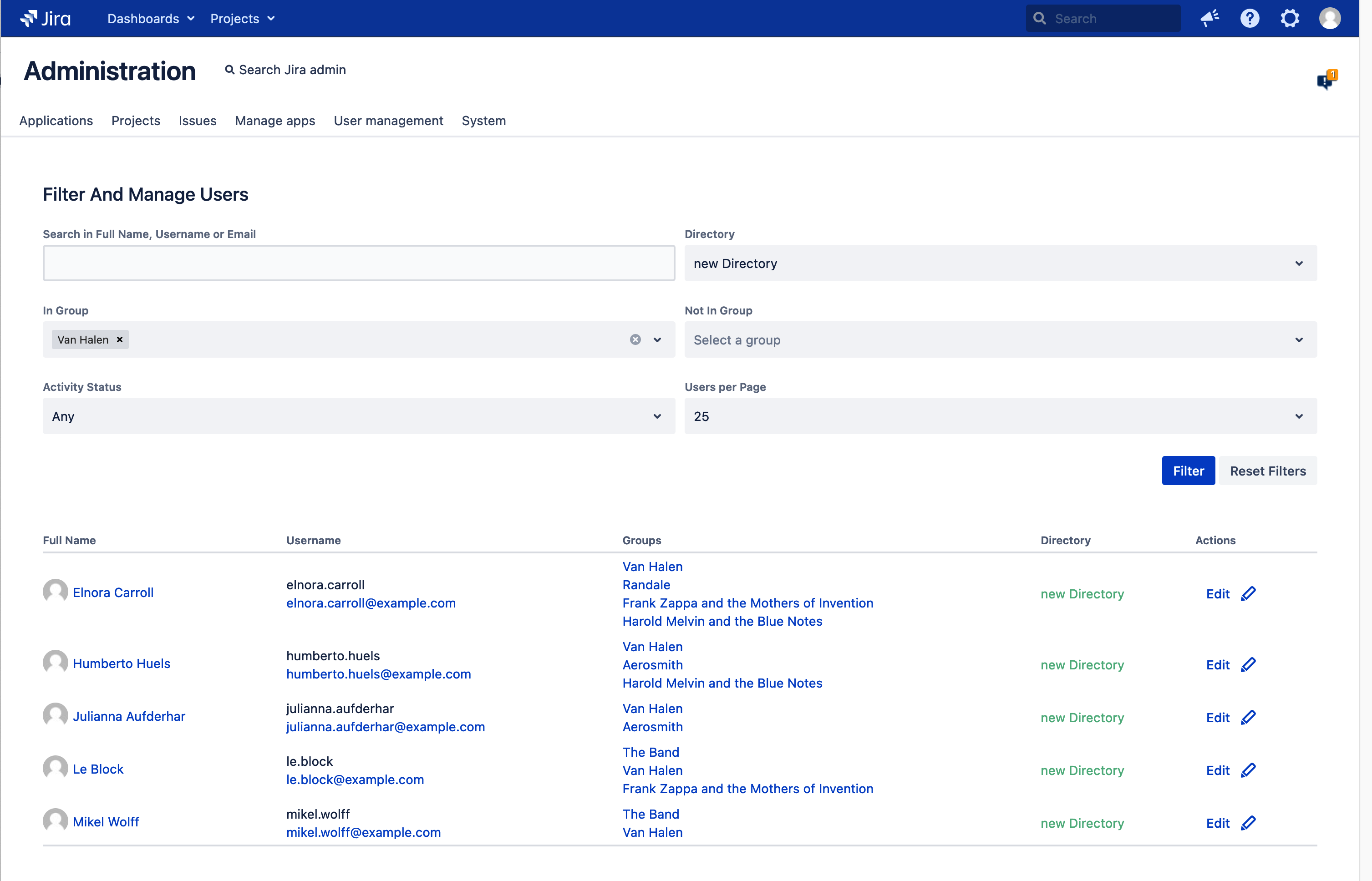
The user list can be filtered with the fields above.
Edit Users
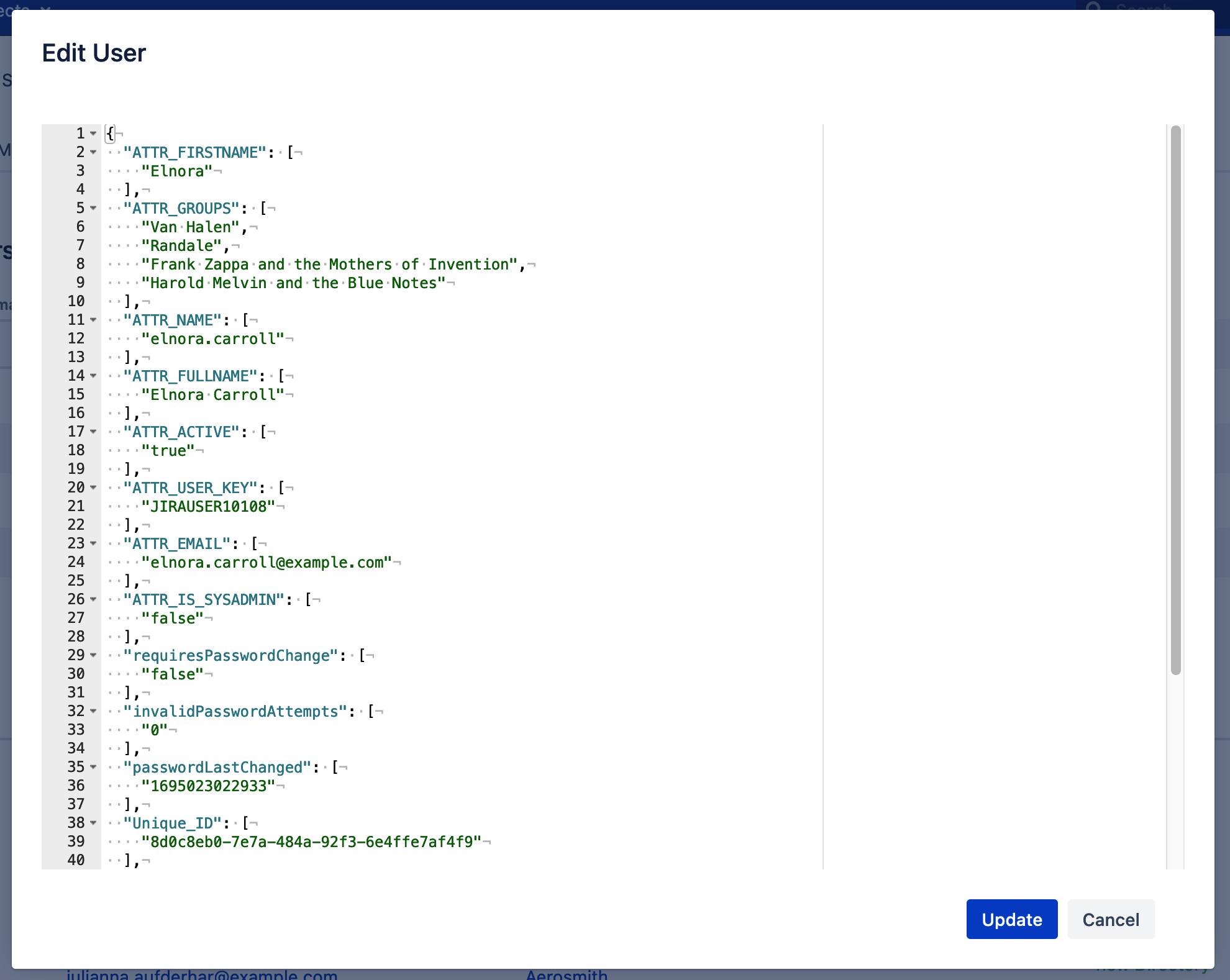
Click the Edit-link next to a user for editing.

This opens a dialog where the user's attributes can be changed.
All attributes consist of a key and a value-list. Most value lists contain only on entry.
Attributes not listed here are stored as Crowd-Attribute at the user if they don't start with one of the prefixes below.
Key | Description |
|---|---|
ATTR_ACTIVE | Is the user active or deactivated |
ATTR_USER_KEY | The user key. This attribute is read only, updates are ignored. |
ATTR_NAME | The username |
ATTR_FIRSTNAME | First name |
ATTR_LASTNAME | Last name |
ATTR_FULLNAME | Fullname - if not set, first name and last name is shown. |
ATTR_EMAIL | The Email Address |
ATTR_IS_SYSADMIN | True if the user has sysadmin privileges. This attribute is readonly, updates are ignored. |
ATTR_IS_ADMIN | True if the user has admin privileges. This attribute is readonly, updates are ignored |
ATTR_ID | Unique id within the directory. Not to be confused with the user key which is unique across all directories |
ATLAS_USER_TIMESTAMP | This timestamp is updated on every user update |
Attribute prefixes
JIRA.PROP.* | Jira User Properties |
JIRA.EPROP.* | Jira Entity Properties |
CONFLUENCE.UD.* | Confluence User Details |
CONFLUENCE.CP.* | Confluence Content Properties |
COMMUNARDO_UP.* | Communardo User Profile attributes |
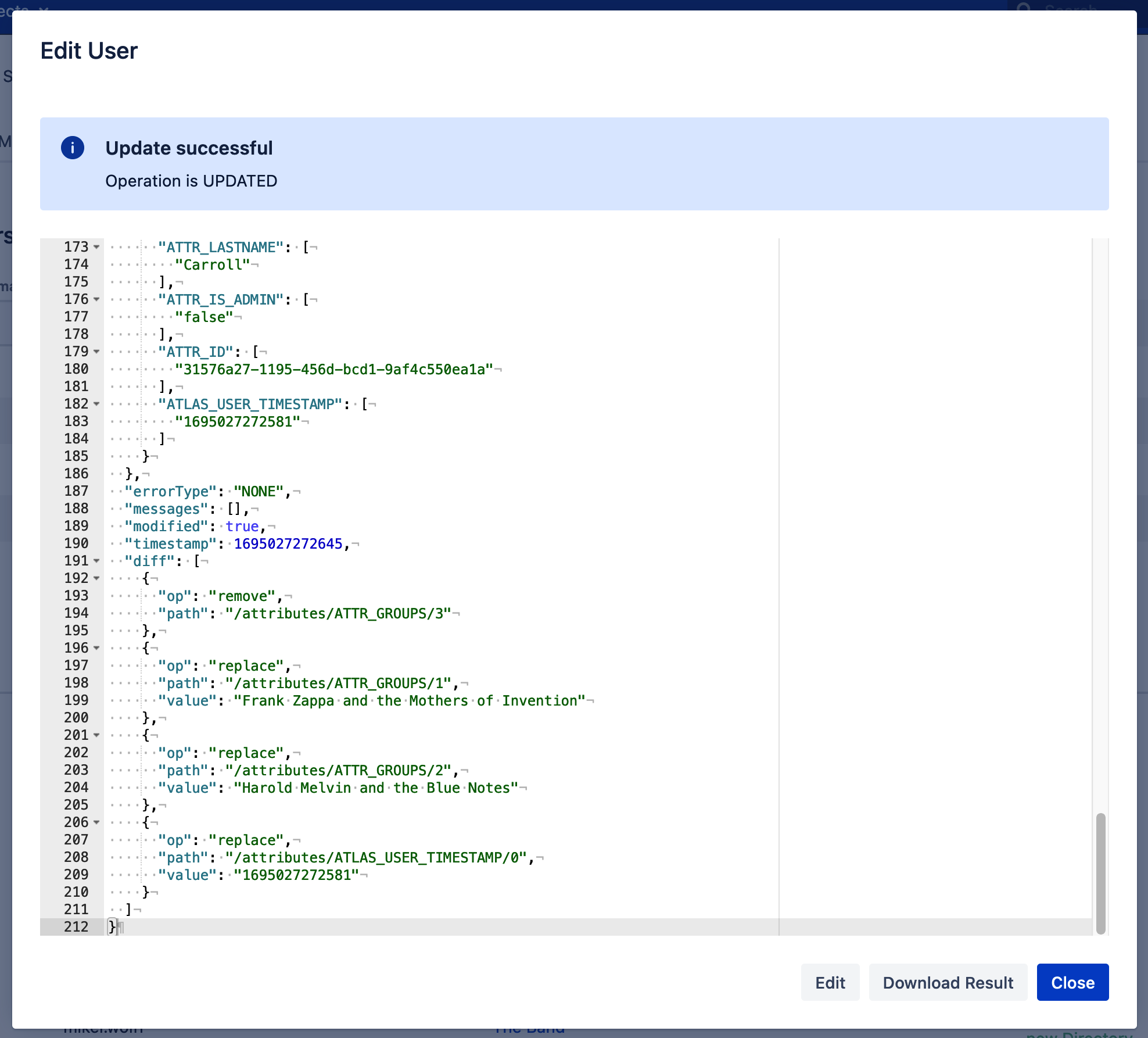
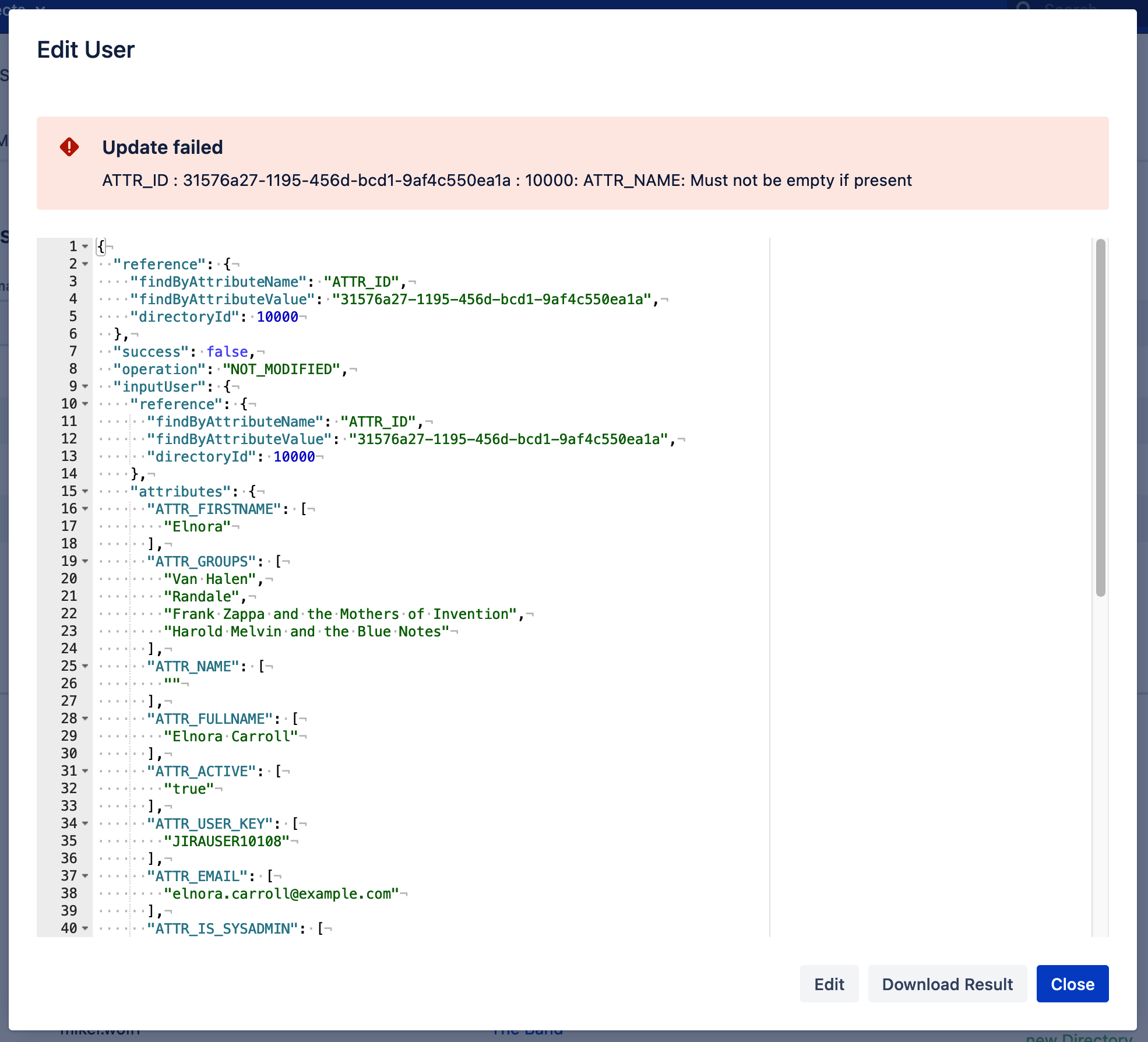
Click Update to save the changes. This changes the view to the result. In case of a failure, the error message is shown in the red box on top.
The SAML SSO Toolbox includes additional features for the SAML SSO add-ons (JIRA, Confluence, Bitbucket, Bamboo and Fisheye/Crucible) and can be used for free. It replaces the old Clearssoconfig plugin, which can remove the SAML Single Sign-On configurations from the database. As a new feature, your user's local passwords can be cleared now.
Use this tool only in cooperation with our customer support.
Installation
Download the samlssotoolbox-1.15.2.jar file here: http://builds.resolution.de/master/samlssotoolbox-1.15.2.jar and upload it using the Plugin Manager.
You can either upload the file from your browser (1) or use the URL above (2), provided your Atlassian instance can access it.

Usage
Open the installed Plugin in the Plugin Manager and select Configure or open the URL "https://<application-baseurl>/plugins/servlet/samlsso/toolbox" directly.
On the main page, you can select between the included tools:

Manipulating users
The SAML SSO User List shows all your users from your internal directories (sorted alphabetically) and indicates which users are created by the SAML SSO add-on. Furthermore, under Actions, it is possible to:
Clear the Password of your users (not possible for administrators), which sets the user password to a special value, resulting in the user not being able to log in with a password. This ensures that your users can only use the Single Sign-On for authentication. Administrators can easily reset the “cleared” user password in the application user configurations.
Convert a non-SAML user to a SAML user and vice versa. This adds or removes the same flag that is added when a user is created via the Just In Time user provisioning.

It's also password to set users passwords via the REST API of the SAML SSO Toolbox:
After installing it, for setting users' passwords, please use the following REST command:
- curl -X "PUT" "https://<base_url>/rest/samlsso-toolbox/1.0/users/<username>?directoryId=<directoryId>" \ -H 'Content-Type: application/json; charset=utf-8' \ -u '<sysadmin>:<password>' \ -d $'{ "ATTR_PASSWORD": "<new_password>" }'
You would need to substitute the following in the above command:
<base_url>: with your Confluence base URL
<username>: with the username of the user for whom you'd like to set a password
<directoryId>: with the directory ID of the UserSync Azure directory ID, which you can when you go to the User Directories page, click on the "Directory Configuration Summary" link at the bottom of the page, look up for the Azure directory and retrieve its Directory ID
<sysadmin>: with your admin username
<password>: with your admin password
<new_password>: with the new password that you want to set for the user
SAML SSO Configurations Export and Cleanup
Please make sure to disable and reenabled the SAML Single Sign-On app using the Plugin Manager after manipulating the saved configurations.
This feature shows all installed SAML SSO configurations as versions in a list. If a version is available, the configurations can be downloaded (Download XML) or removed (Delete).

Reimport downloaded configurations
Currently, it's not directly possible to import a configuration that was downloaded with the help of the SAML SSO Toolbox into the main SAML Single Sign On app. If you want to do that you need to slightly modify the downloaded configuration to make the import possible. Use this template and replace the content from the download file at the marked position:
- <?xml version="1.0" encoding="UTF-8" standalone="yes"?>
- <supportInfo>
- // enter the downloaded content here (<configurationData>...</configurationData>)
- <ssoPluginInfo/>
- </supportInfo>
User Browser
Usage
Click the User Browser link in the SAMLSSO Toolbox to access the User Browser.

The user list can be filtered with the fields above.
Edit Users
Click the Edit-link next to a user for editing.

This opens a dialog where the user's attributes can be changed.
All attributes consist of a key and a value-list. Most value lists contain only on entry.
Attributes not listed here are stored as Crowd-Attribute at the user if they don't start with one of the prefixes below.
Key | Description |
|---|---|
ATTR_ACTIVE | Is the user active or deactivated |
ATTR_USER_KEY | The user key. This attribute is read only, updates are ignored. |
ATTR_NAME | The username |
ATTR_FIRSTNAME | First name |
ATTR_LASTNAME | Last name |
ATTR_FULLNAME | Fullname - if not set, first name and last name is shown. |
ATTR_EMAIL | The Email Address |
ATTR_IS_SYSADMIN | True if the user has sysadmin privileges. This attribute is readonly, updates are ignored. |
ATTR_IS_ADMIN | True if the user has admin privileges. This attribute is readonly, updates are ignored |
ATTR_ID | Unique id within the directory. Not to be confused with the user key which is unique across all directories |
ATLAS_USER_TIMESTAMP | This timestamp is updated on every user update |
Attribute prefixes
JIRA.PROP.* | Jira User Properties |
JIRA.EPROP.* | Jira Entity Properties |
CONFLUENCE.UD.* | Confluence User Details |
CONFLUENCE.CP.* | Confluence Content Properties |
COMMUNARDO_UP.* | Communardo User Profile attributes |

Click Update to save the changes. This changes the view to the result. In case of a failure, the error message is shown in the red box on top.


