Test IdP
The SAML Test IdP can be used for testing and troubleshooting. It allows creating and sending SAML responses.
This Software is provided as is, with no kind of warranty.
It's intended for testing purposes only in the implementation phase of your SAML SSO app for Atlassian Data Center & Server. We strongly recommend not to use it in production environments.
Usage
Java 8 runtime is required. Download the jar-file and start it from the command line using
- java -jar samlTestIdP-2.3.1.jar
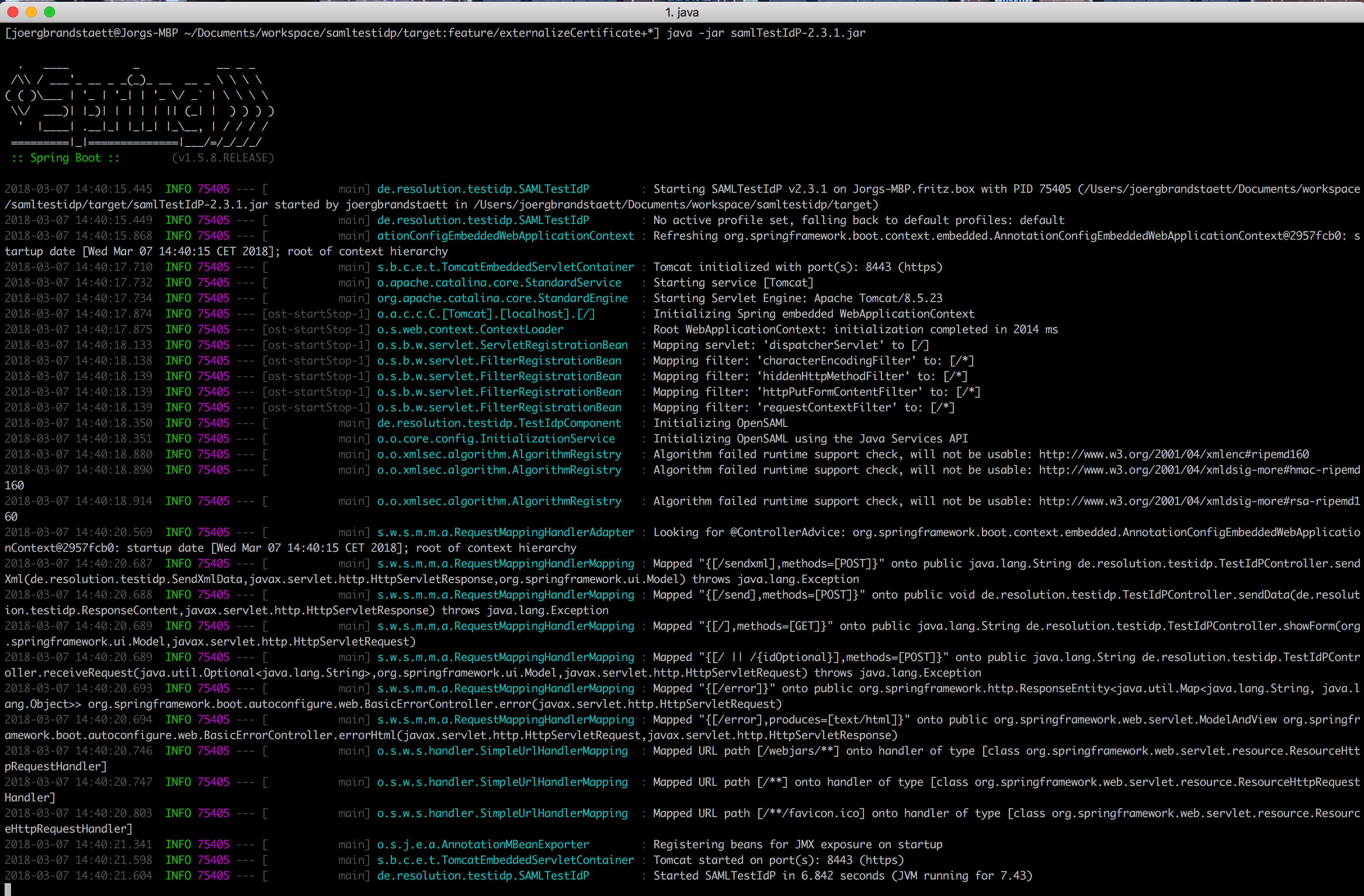
The output should look like this:
Modify and resend an existing SAML-response
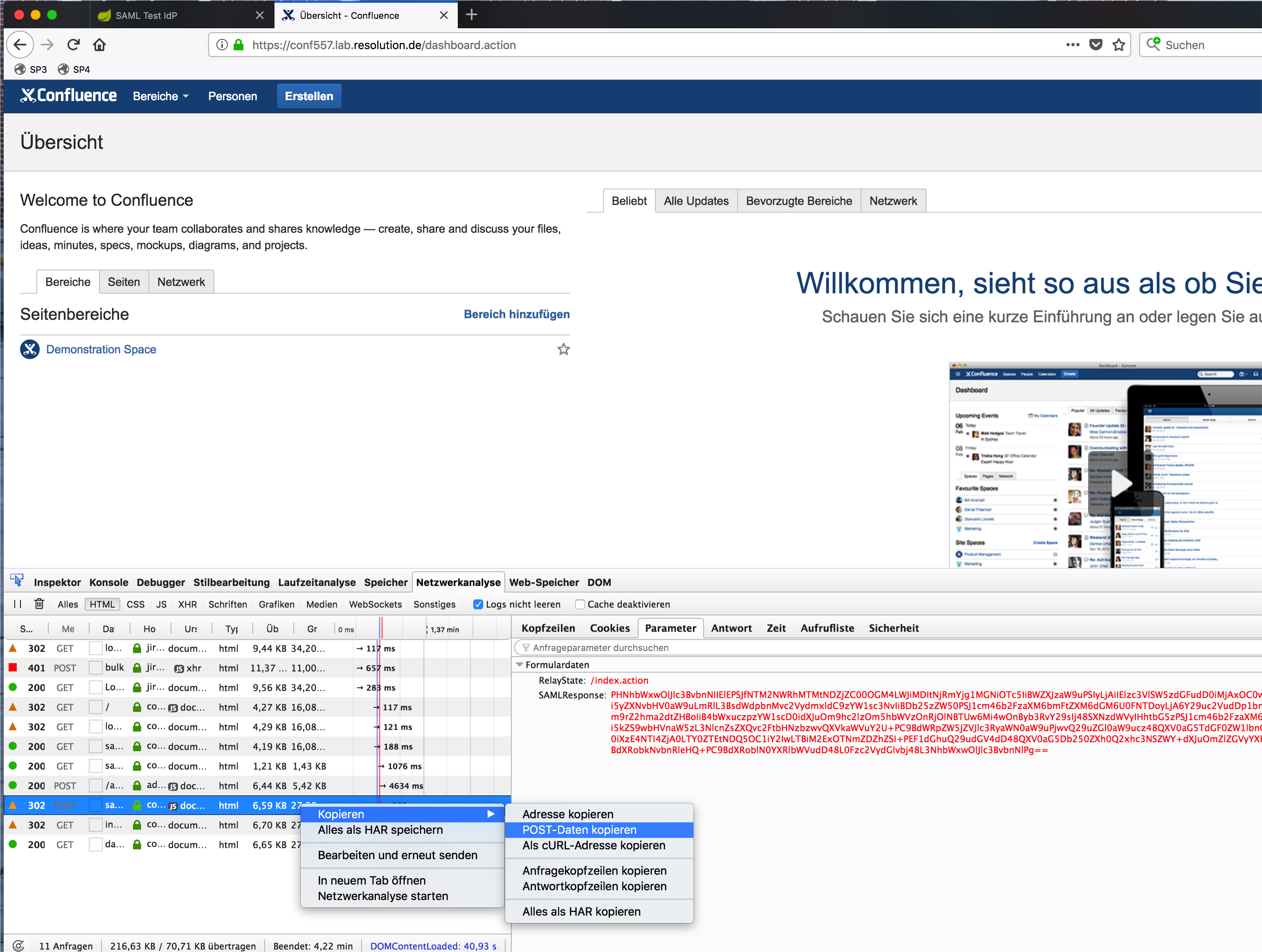
One way to get a valid SAML-Response is to enable the Browsers Developer console during a SAML login and copy the POST data to from the POST-request to /plugins/servlet/samlsso after authenticating at the IdP:
The Test IdP application starts a Web Server on port 8443, so you should see this when browsing https://localhost:8443/:
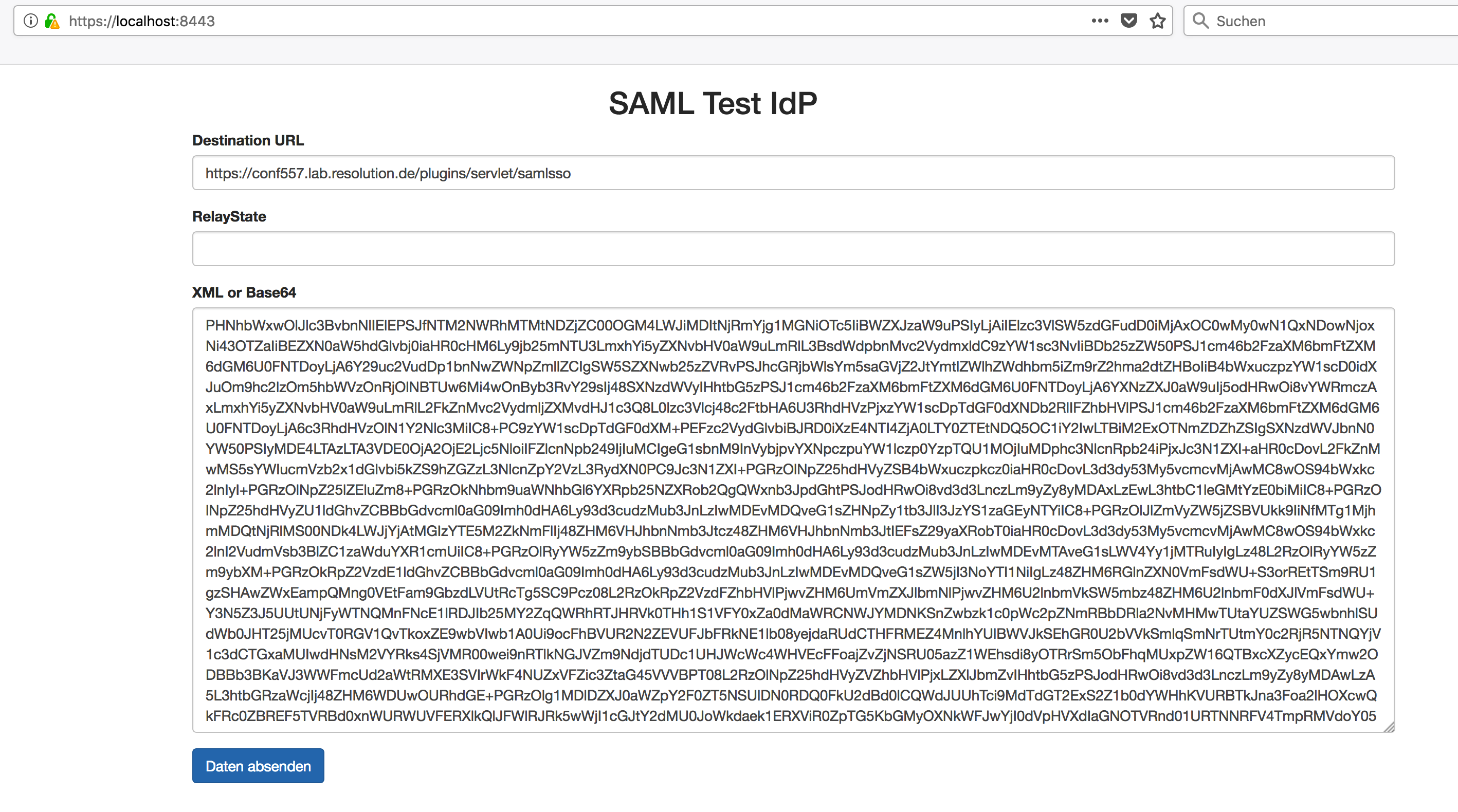
Enter the copied POST-request and remove any other parameter and the SAMLResponse= so that there is the Base64-encoded message only.
Enter the SAMLSSO-url of the system you want to test (e.g. https://jira.test/plugins/servlet/samlsso) in the Destination URL field.
After submitting the form, the Base64 is decoded into XML and the form is shown again:
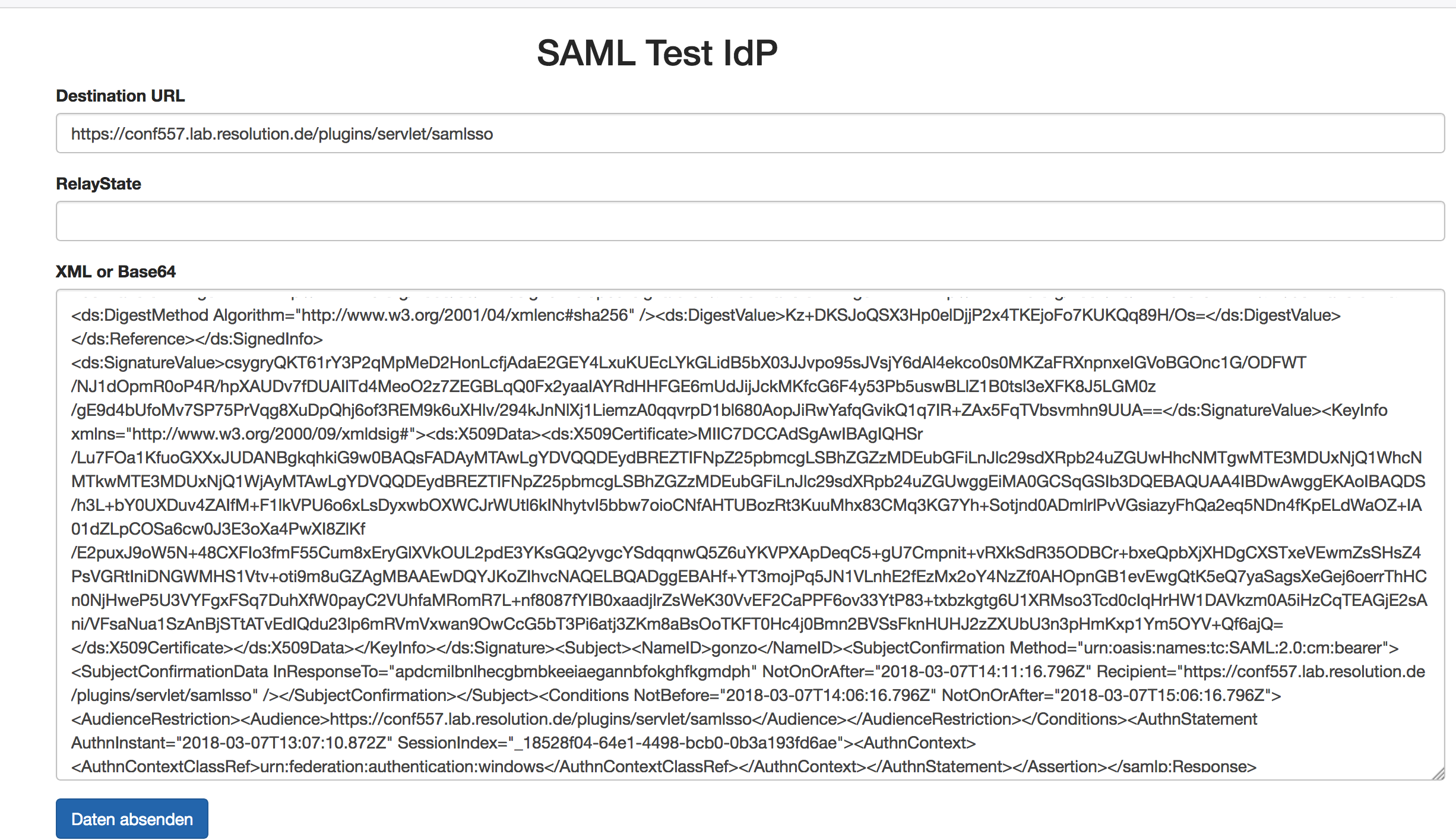
Now, you can modify the XML and send it.
Reusing a SAML-Response should result in an error message stating that the ID has already been used or that the Response is no longer valid. For testing purposes (DO NOT DO THIS ON PRODUCTION SYSTEMS), you can disable these checks in the Addon's configuration in the tab Service Provider:
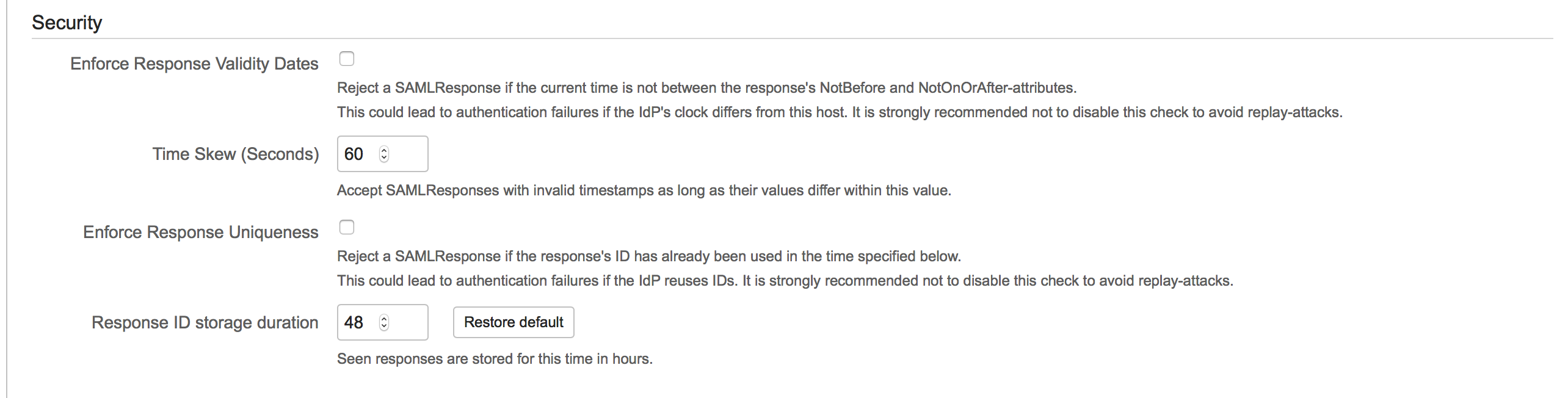
Modifying the XML should result in an error message stating that the signature could not be verified.
To test wether your system is affected by (6.15.x) 2018-03-01 Values in SAML Response can be shortened, find the <NameID>-attribute and insert a comment within the value, e.g. <NameID>ad<!---->min</NameId>. If the system is affected, it will parse the userid as "min" and show an error message that "min" does not exist.
Set it up as IdP
This IdP can be configured in the SAML addon configuration:
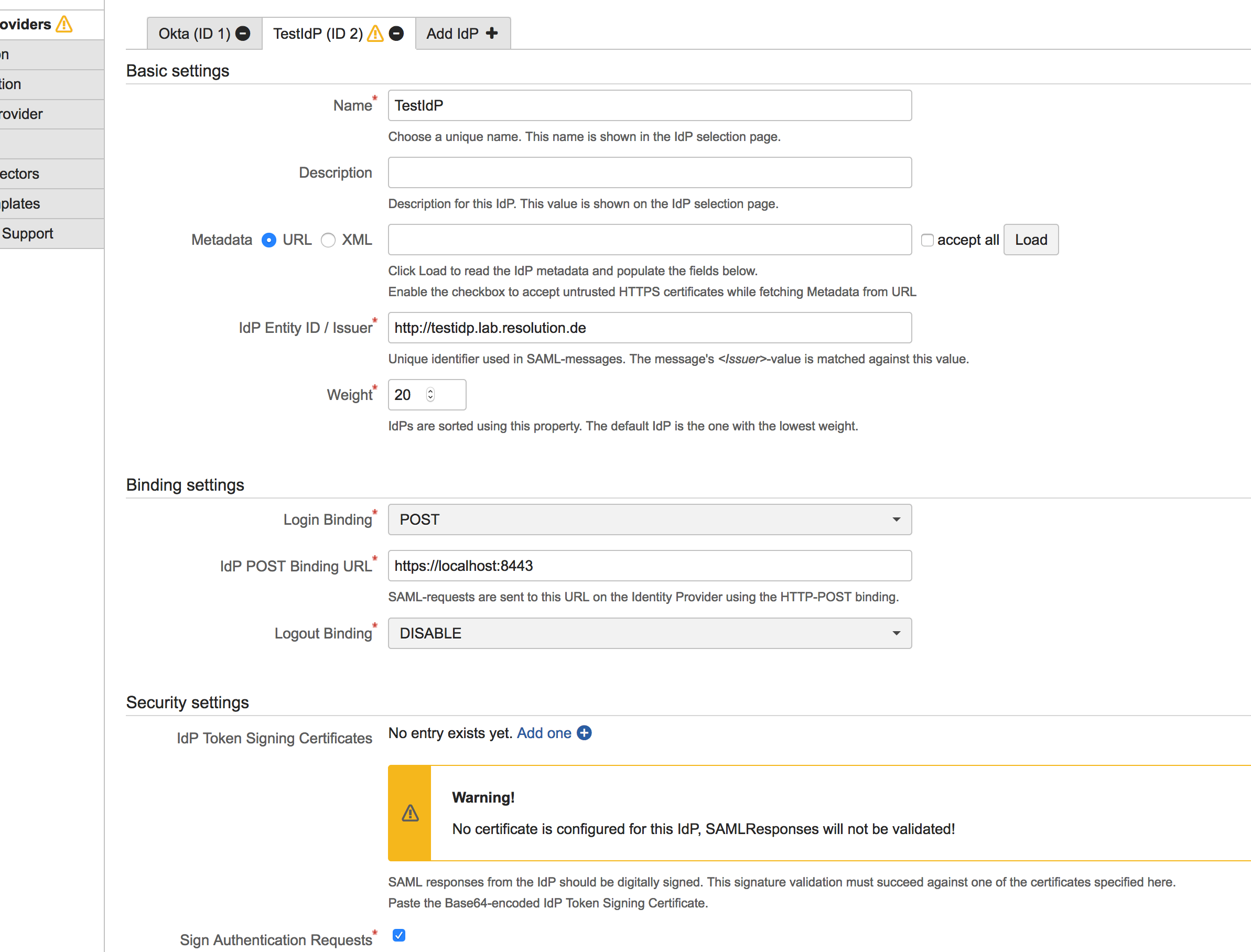
Set the IdP Entity ID to http://testidp.lab.resolution.de and the IdP POST binding URL to https://localhost:8443
Currently the TestIdP does not support response signing, so there is no certificate to configure
If you trigger SSO using this IdP, you will see this form:
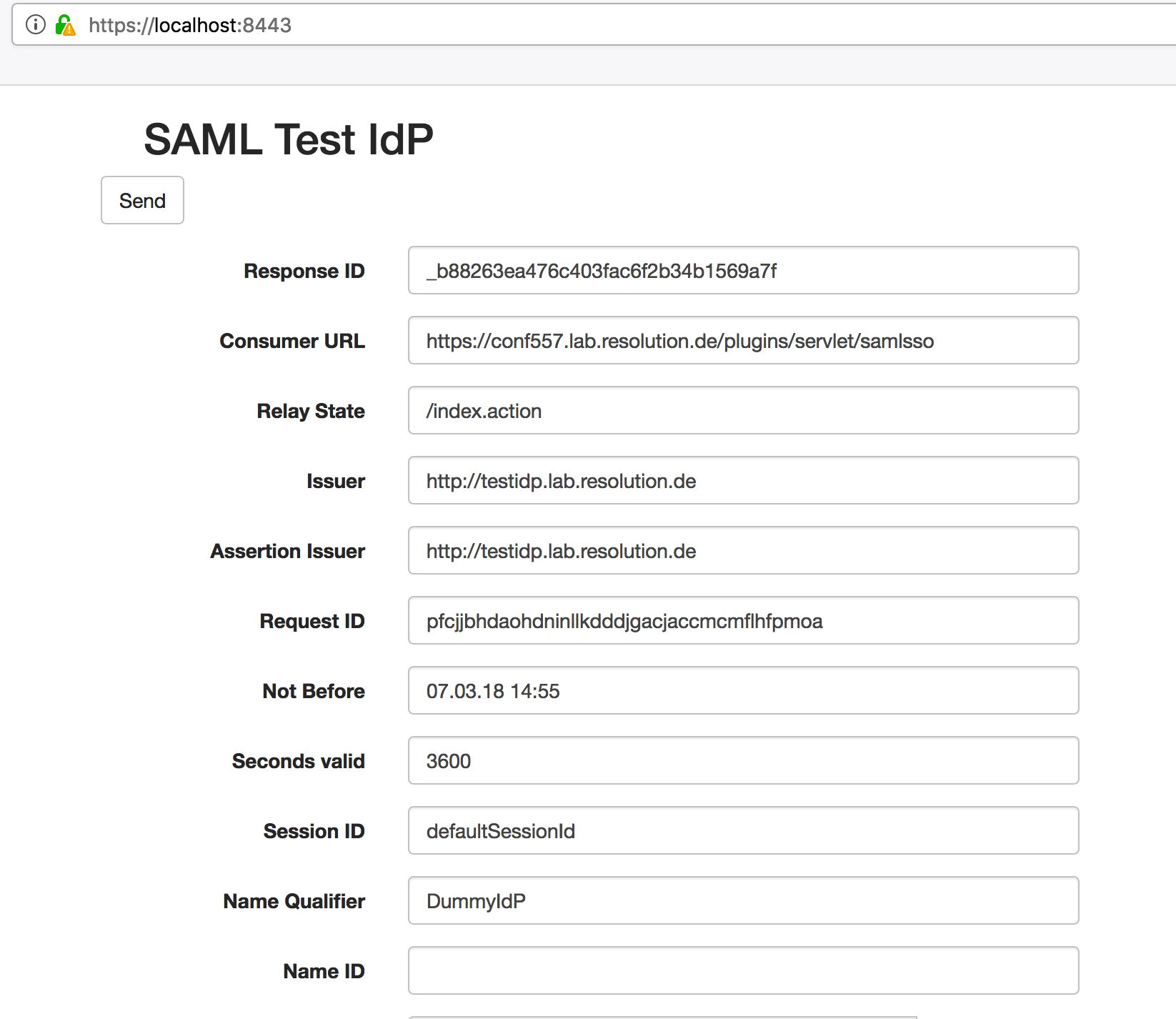
Specify the information to send and click the send button on the bottom of the page.
