Error: XMLCipher::decryptElement unable to resolve a decryption key
Problem
Login via SSO with Okta fails, and you get an error in the tracker, with a message "Something bad happened: null".
Diagnosis
In the log file, there are similar errors to the below:
- 2024-10-23 13:36:07,302+0000 http-nio-8080-exec-19 url: /plugins/servlet/samlsso ERROR anonymous 816x1141x1 16e6we 77.11.179.58,10.2.88.105 /plugins/servlet/samlsso [o.a.x.security.encryption.XMLCipher] XMLCipher::decryptElement unable to resolve a decryption key
- 2024-10-23 13:36:07,303+0000 http-nio-8080-exec-19 url: /plugins/servlet/samlsso WARN anonymous 816x1141x1 16e6we 77.11.179.58,10.2.88.105 /plugins/servlet/samlsso [c.o.saml2.util.Util] Error executing decryption: encryption.nokey
- org.apache.xml.security.encryption.XMLEncryptionException: encryption.nokey
- at org.apache.xml.security.encryption.XMLCipher.decryptToByteArray(XMLCipher.java:1757)
- at org.apache.xml.security.encryption.XMLCipher.decryptElement(XMLCipher.java:1673)
- .
- .
- 2024-10-23 13:36:07,305+0000 http-nio-8080-exec-19 url: /plugins/servlet/samlsso WARN anonymous 816x1141x1 16e6we 77.11.179.58,10.2.88.105 /plugins/servlet/samlsso [c.r.a.s.tracker.activeobjects.AuthenticationTrackerActiveObjectsProxy] Adding ExceptionInfo for this Exception to HN6Q1EHYJ32VJGB:
- com.resolution.samlwrapper.api.exception.MessageReadingException: Something bad happened: null
- at com.resolution.samlwrapper.osj.SAMLResponseReader.readAndValidateSamlResponse(SAMLResponseReader.java:120)
- at com.resolution.samlwrapper.osj.SAMLResponseReader.validateSAMLResponseAndReadLoginInformation(SAMLResponseReader.java:52)
- at com.resolution.samlwrapper.osj.SAMLWrapperImpl.handleSAMLResponse(SAMLWrapperImpl.java:622)
- at com.resolution.samlwrapper.osj.SAMLWrapperImpl.handleSAMLMessage(SAMLWrapperImpl.java:592)
- at com.resolution.atlasplugins.samlsso.servlet.SamlSsoServlet.processRequest(SamlSsoServlet.java:170)
- at com.resolution.atlasplugins.samlsso.servlet.BasicServlet.doPost(BasicServlet.java:100)
- .
- .
- Caused by: java.lang.NullPointerException
- at com.onelogin.saml2.authn.SamlResponse.decryptAssertion(SamlResponse.java:1319)
- at com.onelogin.saml2.authn.SamlResponse.loadXml(SamlResponse.java:221)
- at com.onelogin.saml2.authn.SamlResponse.loadXmlFromBase64(SamlResponse.java:187)
- at com.onelogin.saml2.authn.SamlResponse.<init>(SamlResponse.java:122)
- at com.resolution.samlwrapper.osj.SAMLResponseReader.readAndValidateSamlResponse(SAMLResponseReader.java:93)
- ... 335 more
Solution
The above indicates that the Assertion Encryption in Okta has been enabled but doesn't have the correct certificate from the SAML SSO plugin (the service provider).
To fix that:
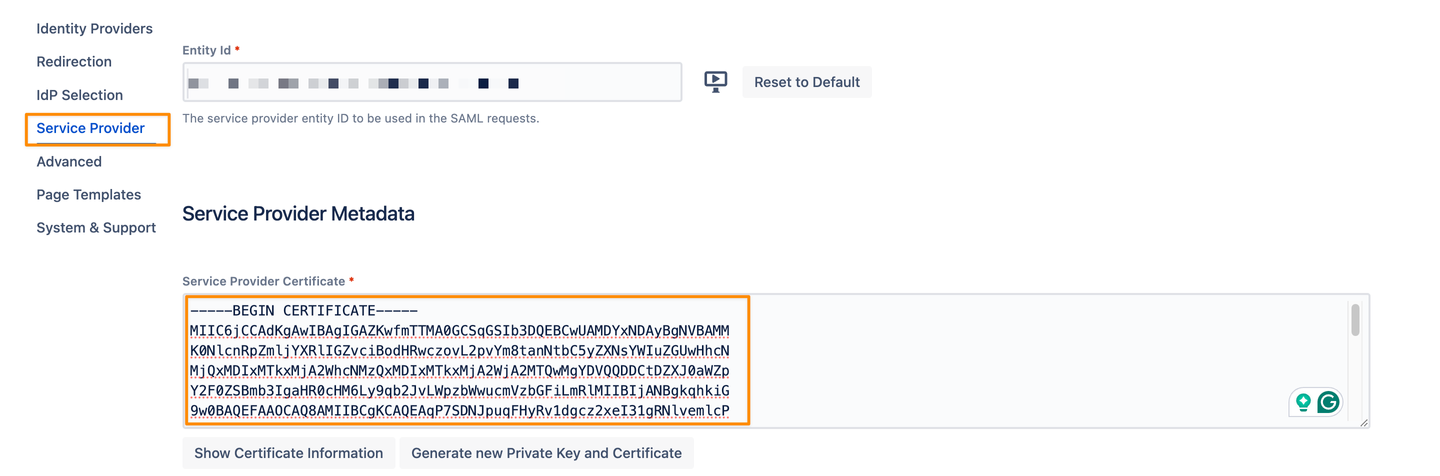
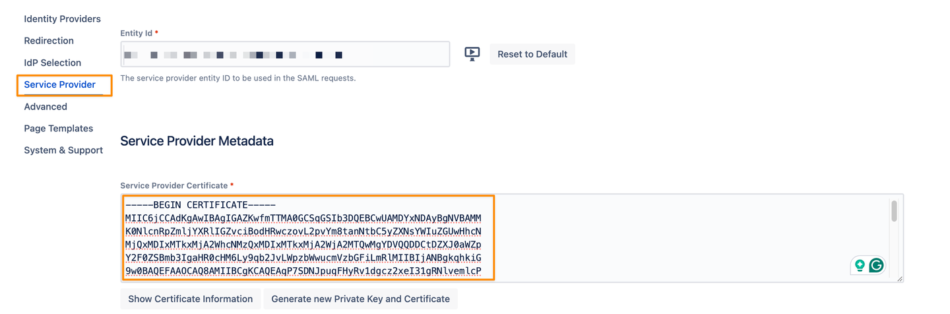
In the SAML Single Sign On Configuration page, in the Service Provider tab, copy the Service Provider Certificate
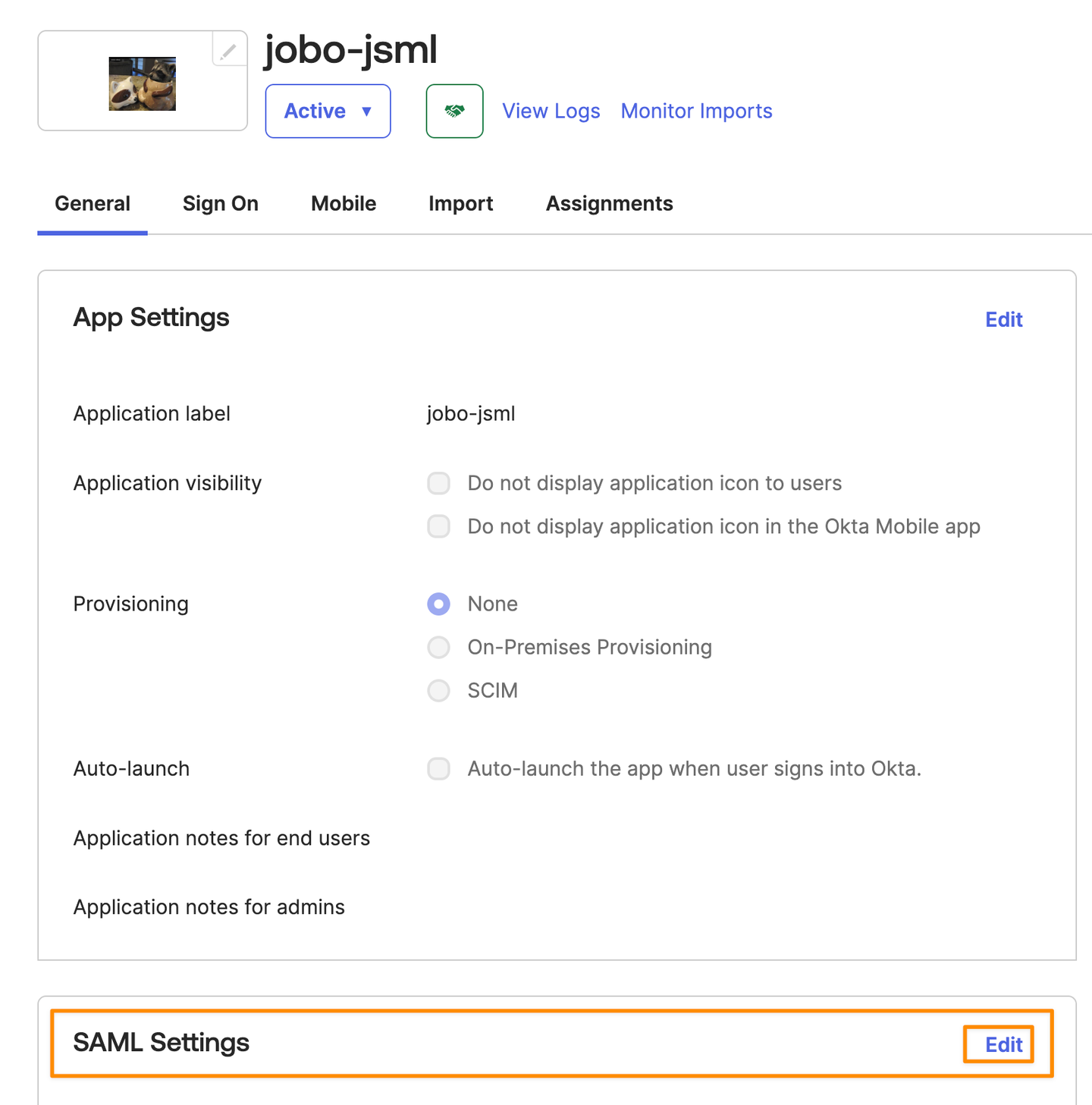
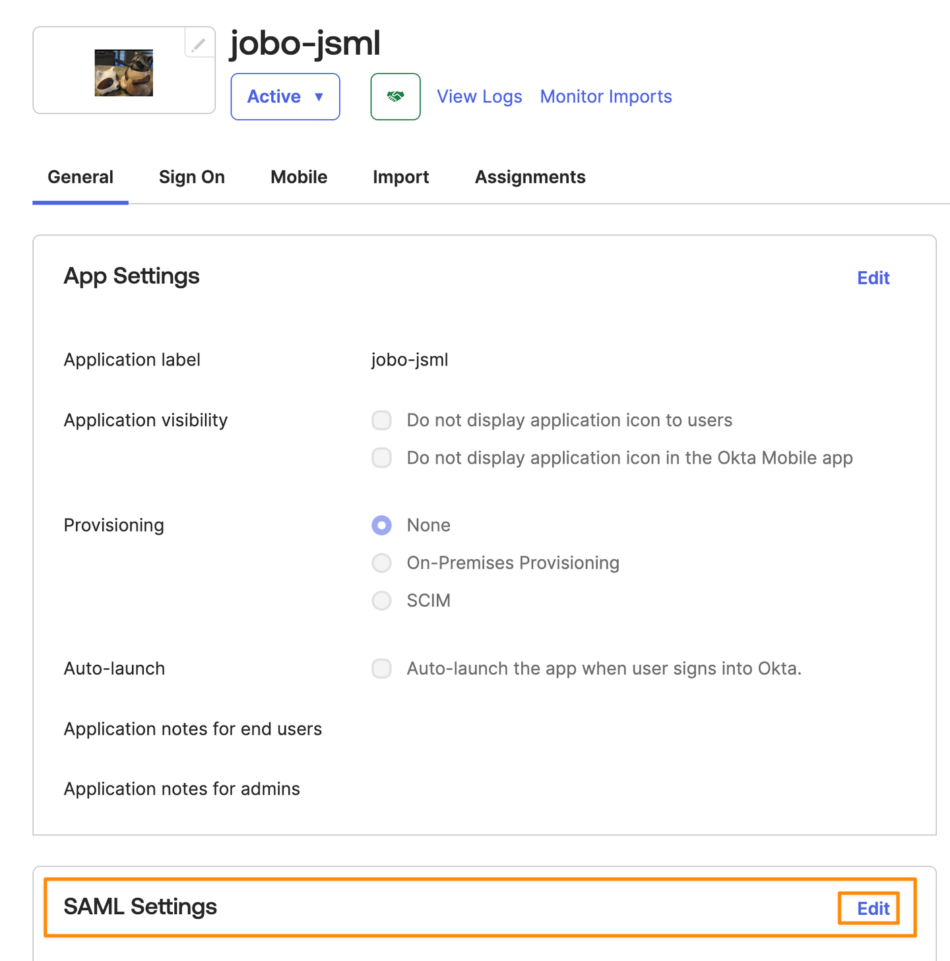
In Okta and under SAML Settings, click Edit
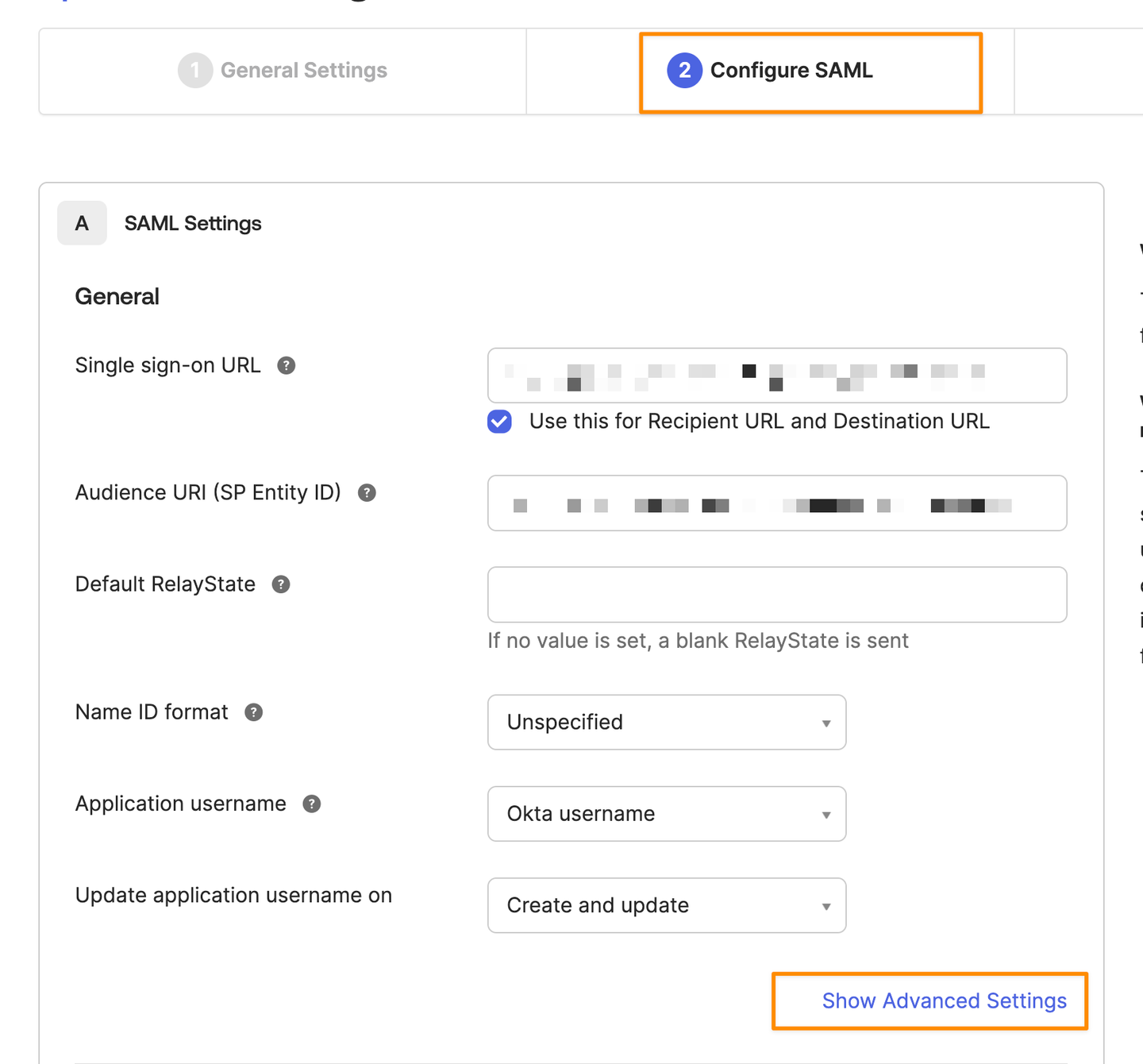
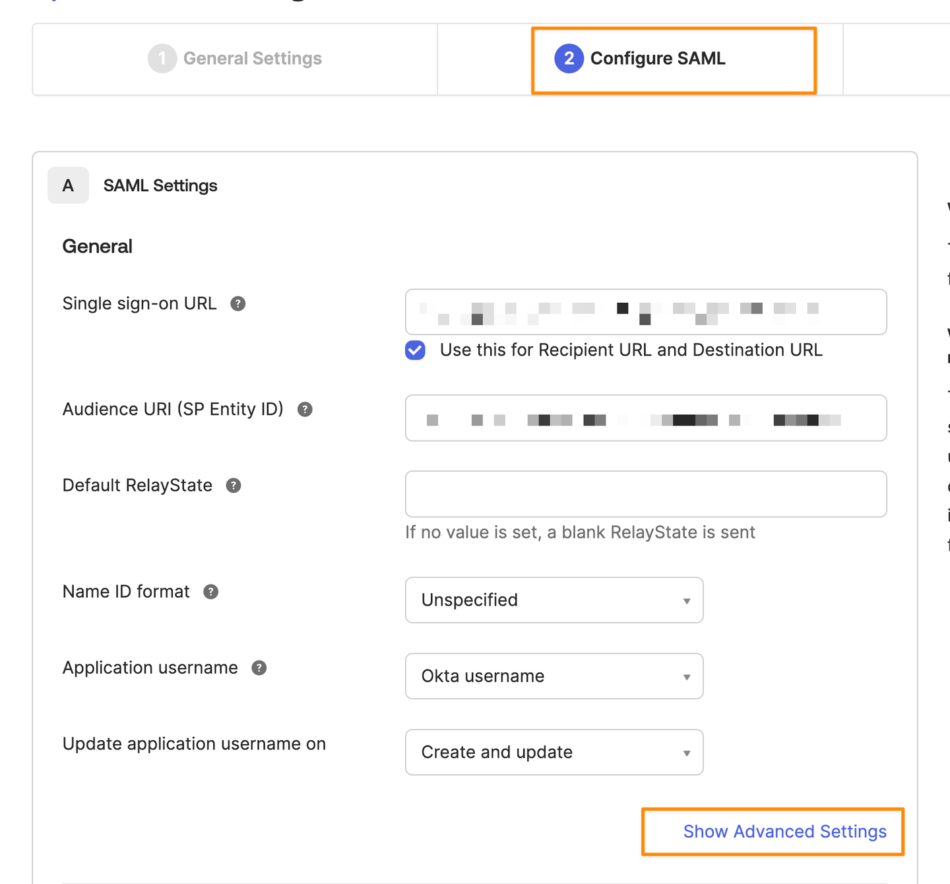
Navigate to step 2 (Configure SAML) and click on “Show Advanced Settings”
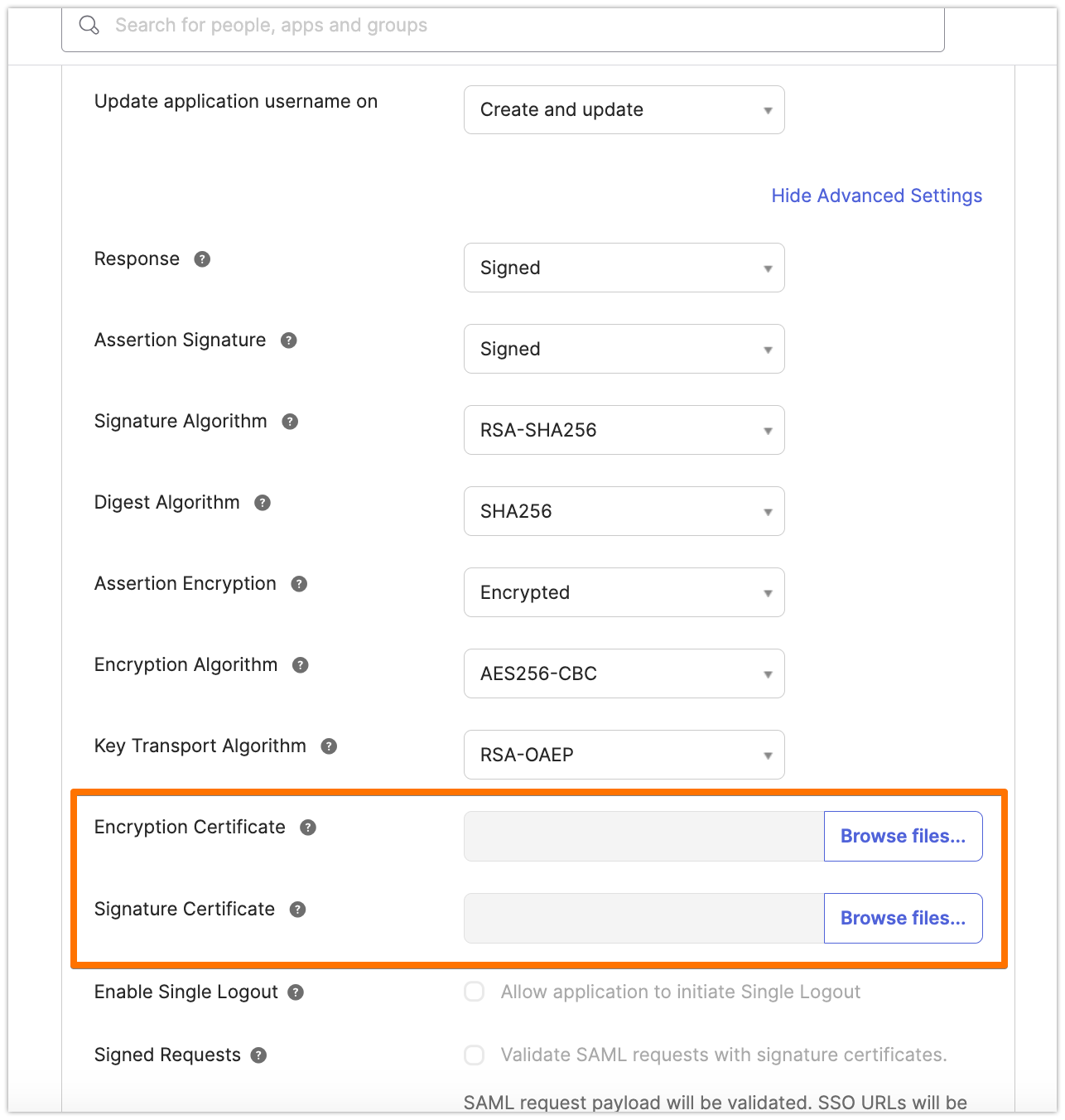
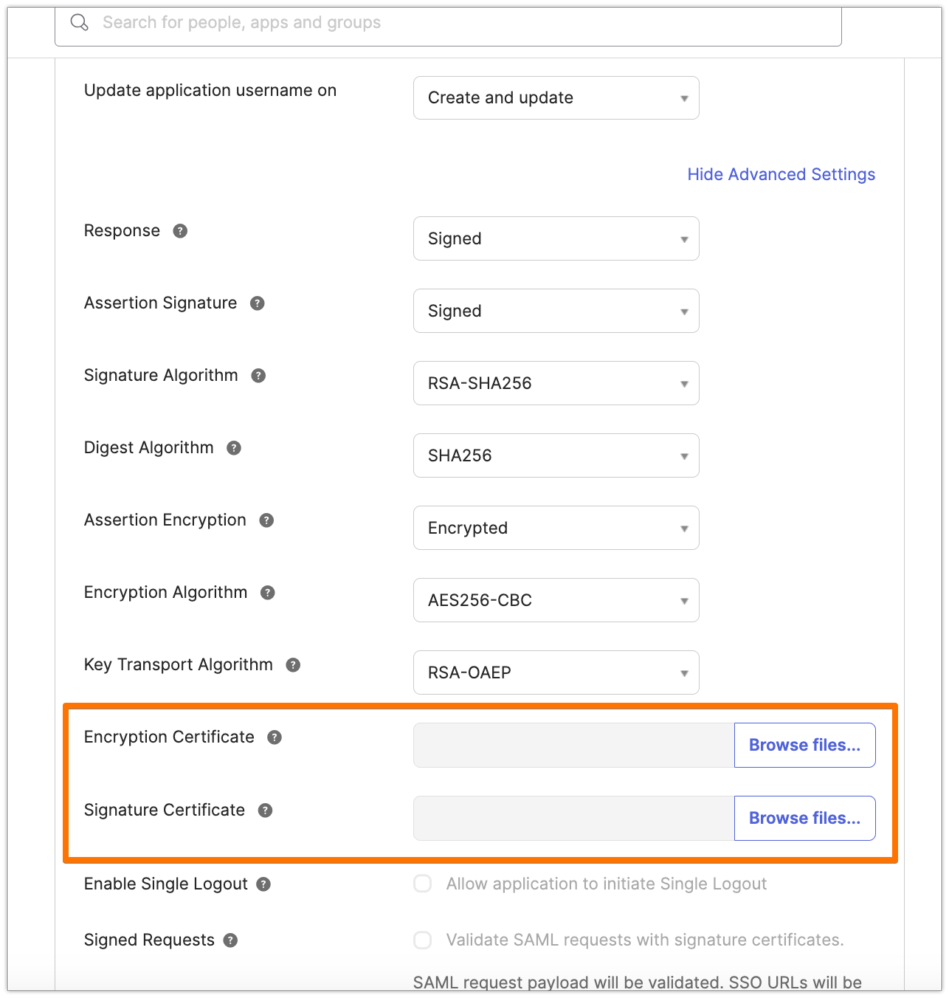
Upload the new certificate to be used both as Encryption and Signature certificate
Save the settings