Google Cloud Identity with Manual Provisioning
Goal
After completing this setup guide, you will have setup Google Cloud Identity with Manual Provisioning and your Atlassian product for the SAML SSO app. Additionally, you will test SSO and enable the SSO redirection.
Prerequisites
To use the SAML SSO app with GSuite, you need the following:
A GSuite subscription
A (trial) subscription for the SAML SSO app
Admin access to your Atlassian product
Users are already available in Jira and GSuite.
Video Guide
Step-by-Step Setup Guide
Configure GSuite for the SAML SSO App
Go to http://admin.google.com and click on "Apps", then "Web and mobile apps".
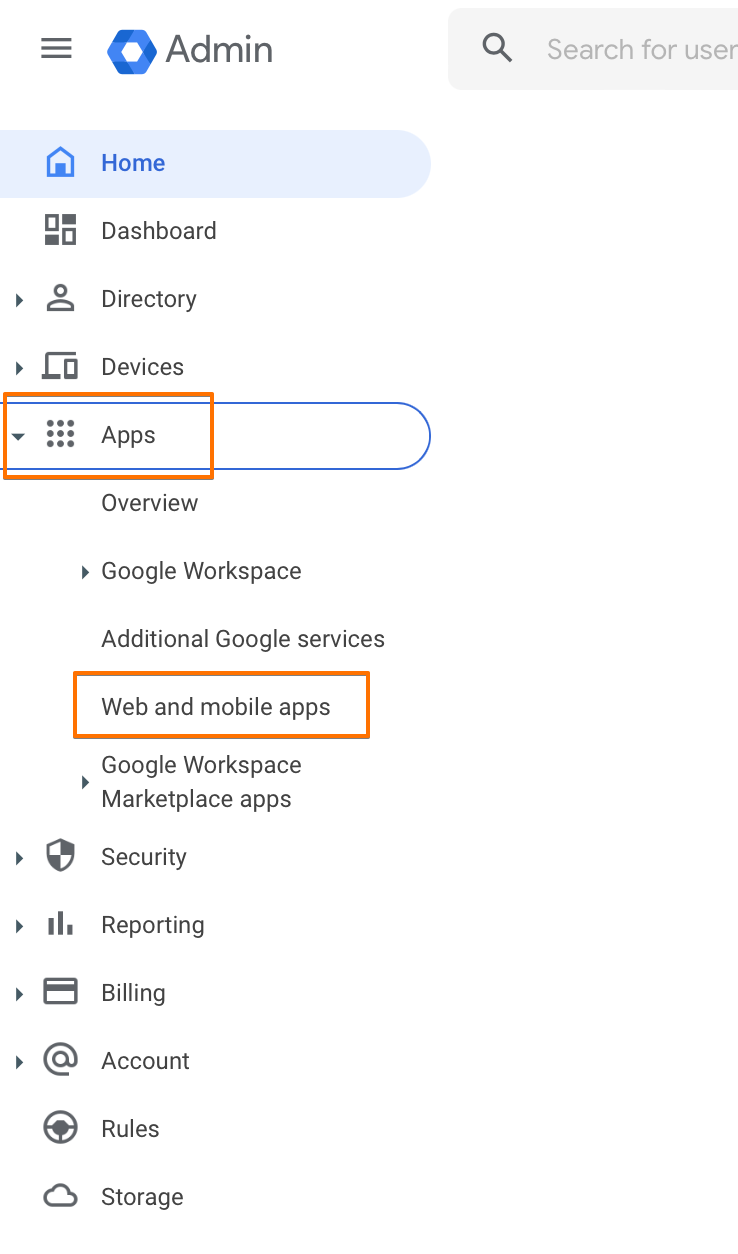
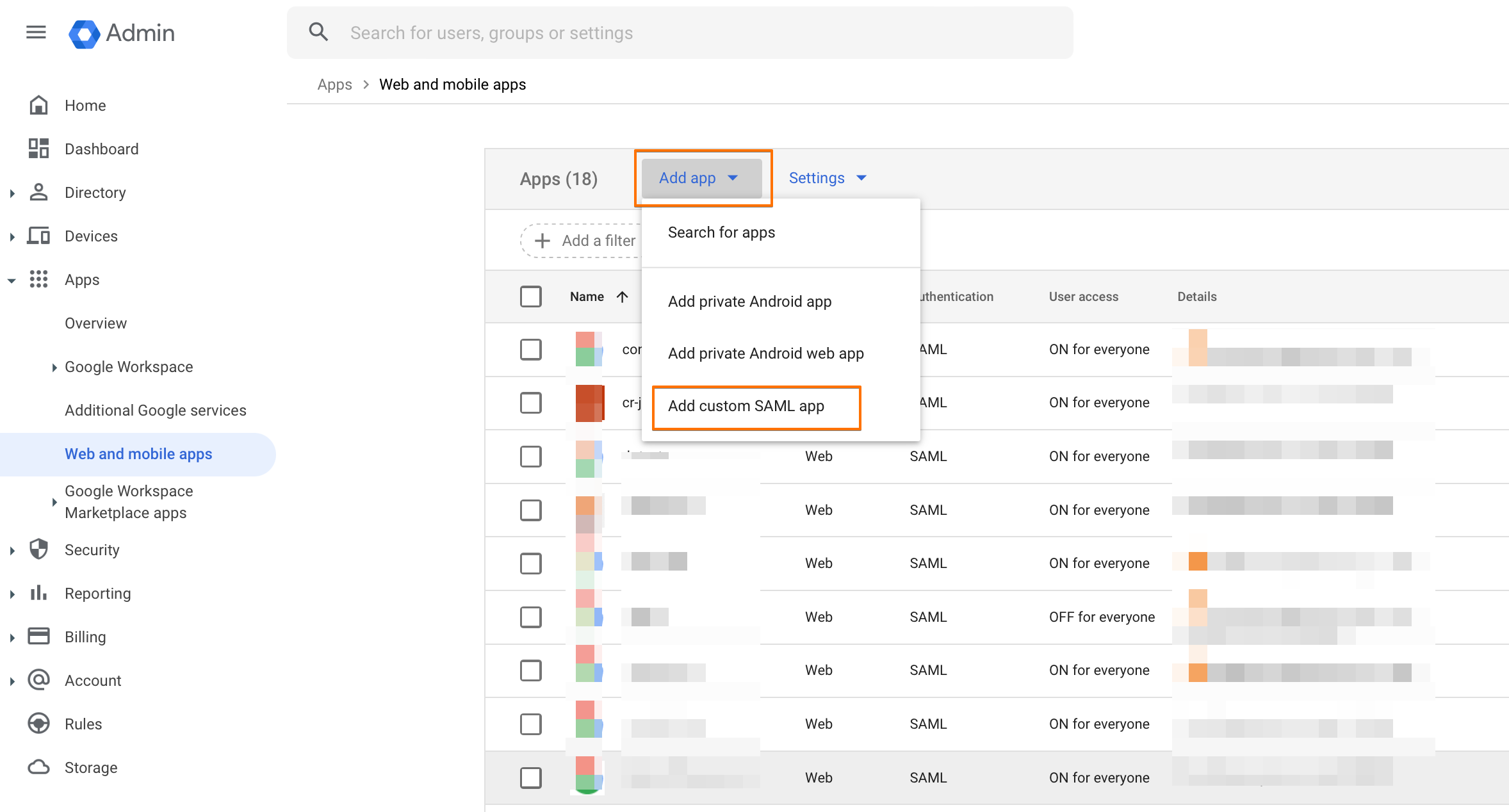
Afterwards, click on "Add app", then "Add custom SAML app".
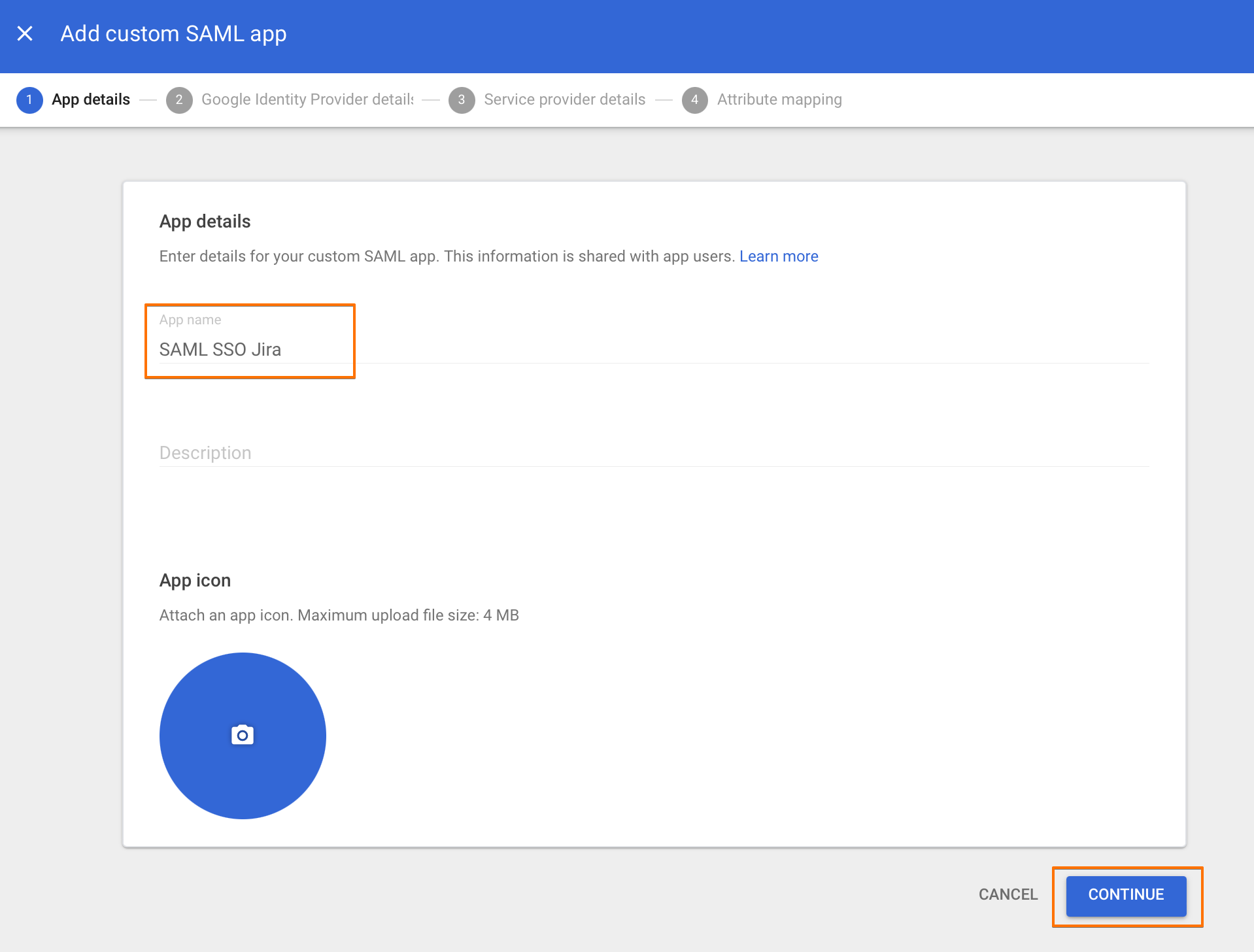
In the next window, give the application a name, and click on "CONTINUE".
Next, click "DOWNLOAD METADATA" and save the file to your computer, and click "CONTINUE".
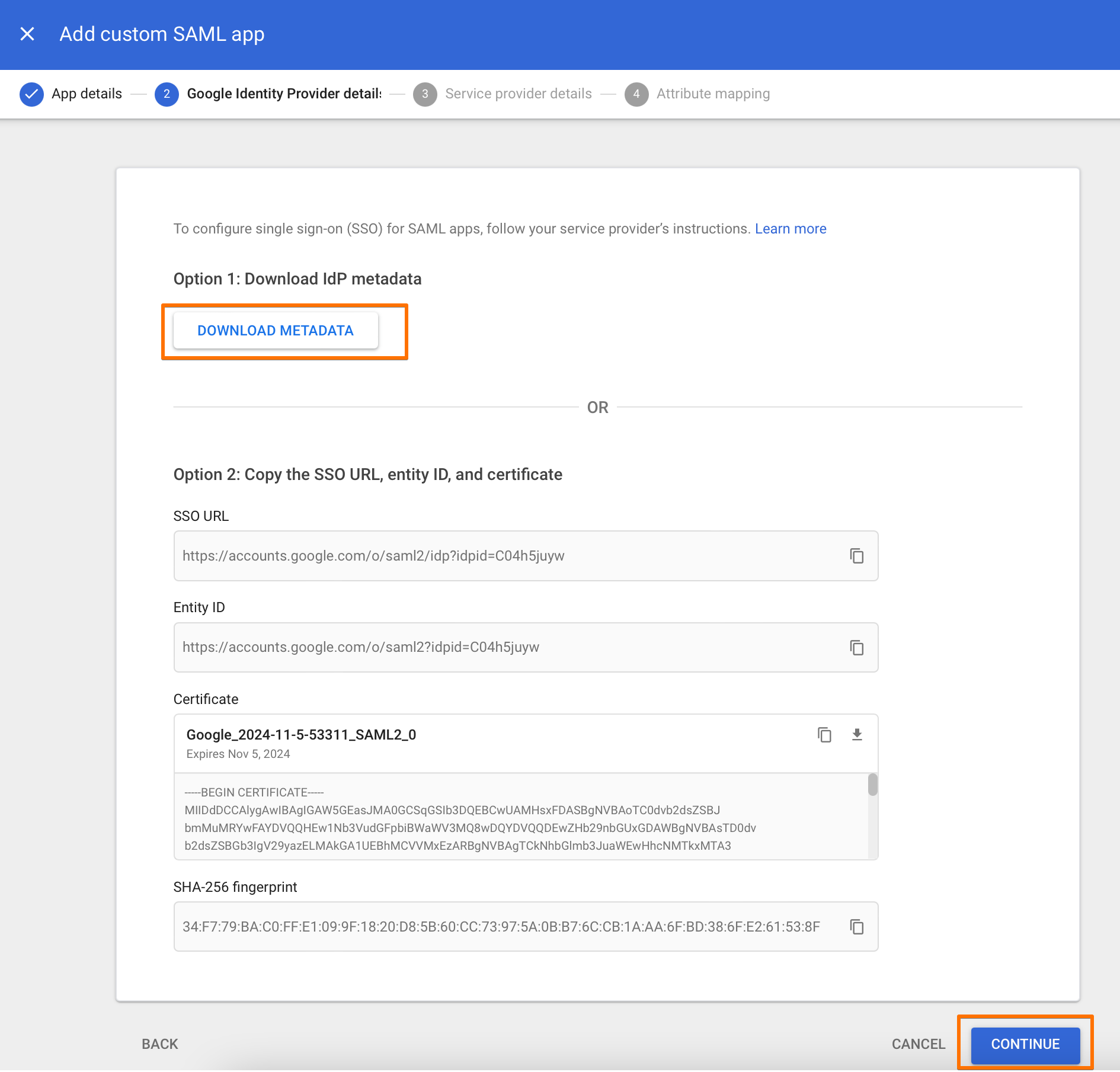
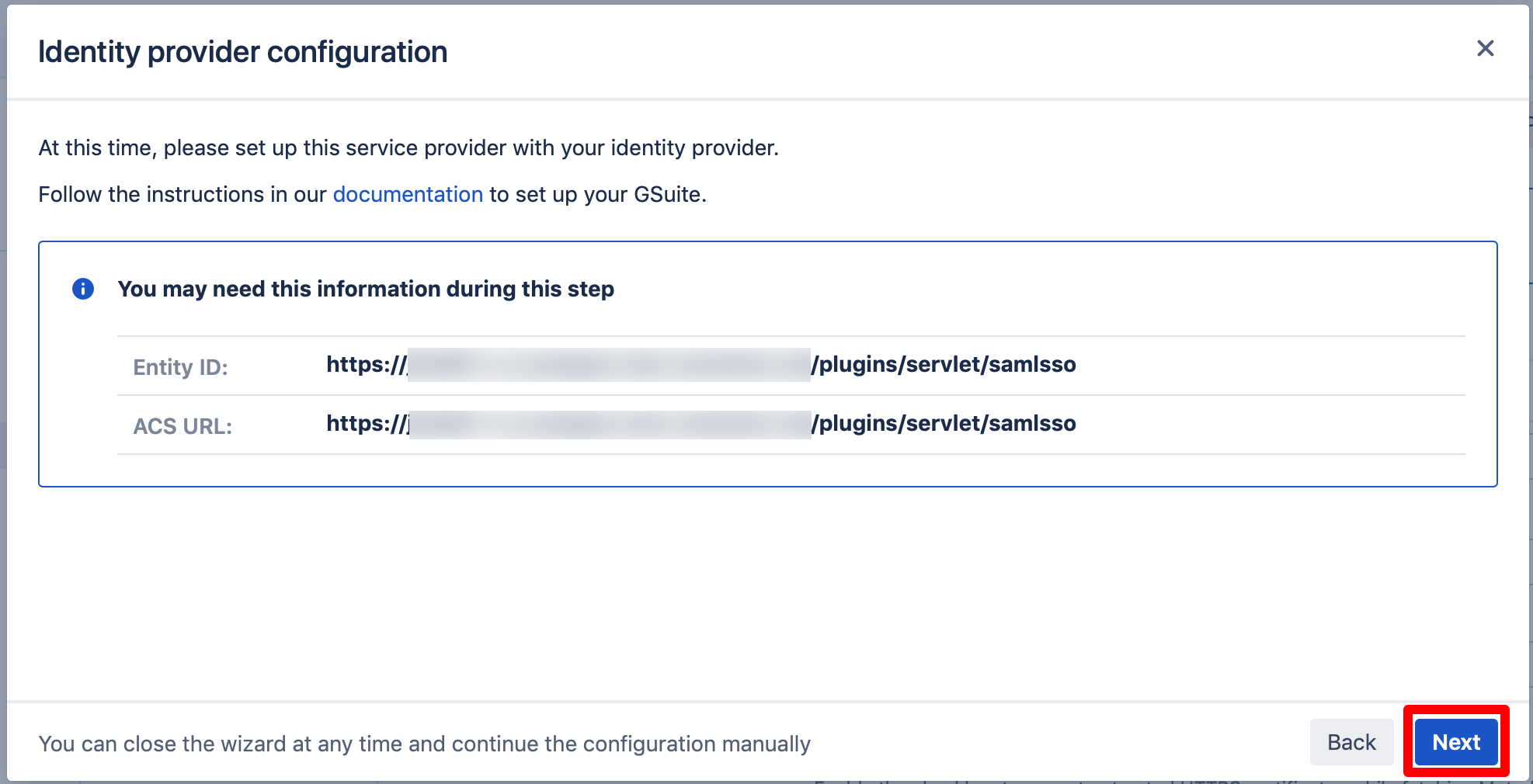
Next, for "ACS URL" and "Entity ID" enter "https://<base-url>/plugins/servlet/samlsso" (without quotes) and substitute "<baseURL>" with the URL to your Atlassian product.
For "Name ID", make sure that "Name ID Format" is set to "UNSPECIFIED" and that "Name ID" is set to "Basic Information > Primary email".
Click "CONTINUE" to proceed.
Click "Finish".
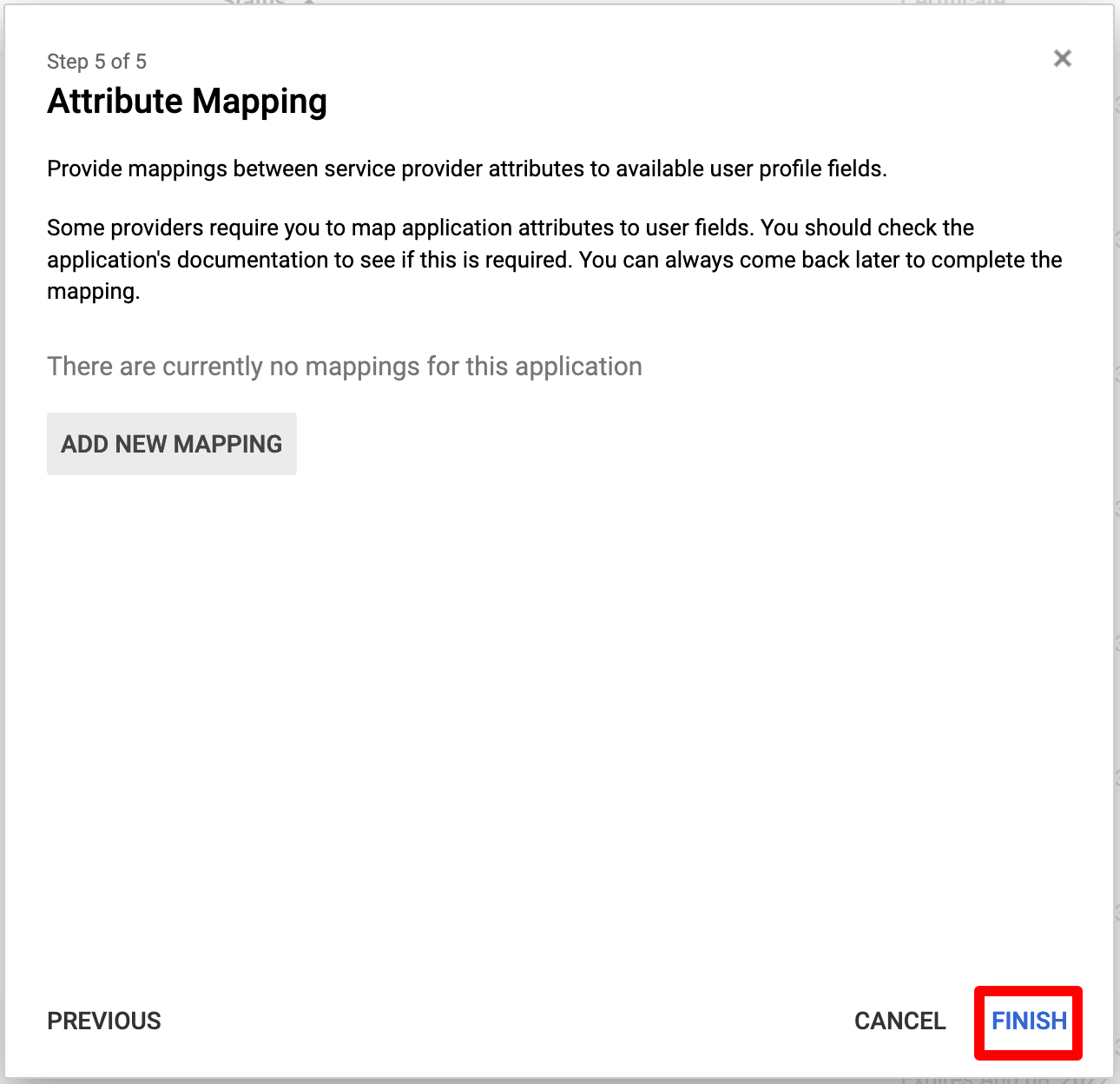
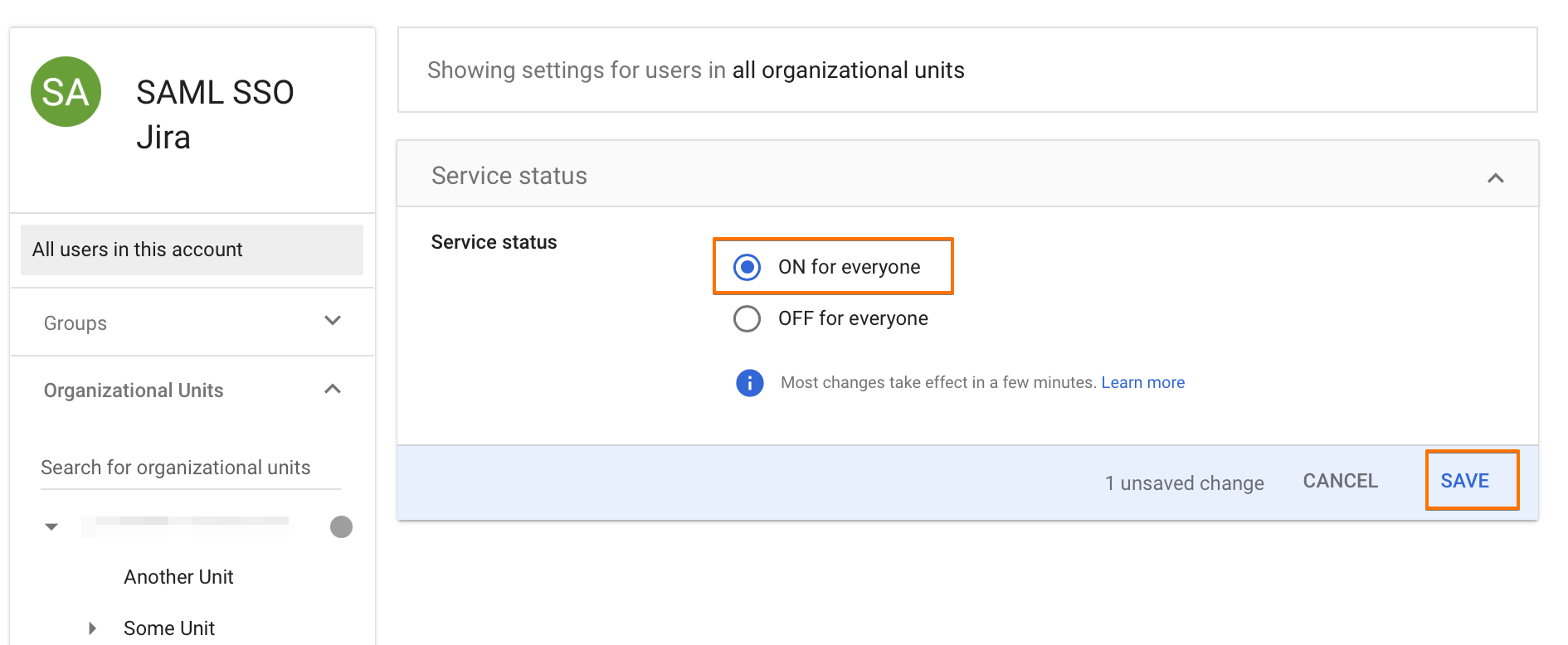
After setting up the app, it is turned OFF. To activate it, click on "OFF for everyone".
Check "ON for everyone" and click "SAVE".
Configure Jira for the SAML SSO App
Install the SAML SSO App
In your Atlassian product, open the in-product marketplace as described in the Atlassian documentation.
Search for "resolution saml" and click "Install" for SAML Single Sign On (SSO) by resolution Reichert Network Solutions GmbH.
After the installation is complete, click on Manage, then choose Configure.
Now, you are on the Add-on / app configuration page and the first step of the setup wizard will appear.
Configure the SAML SSO App
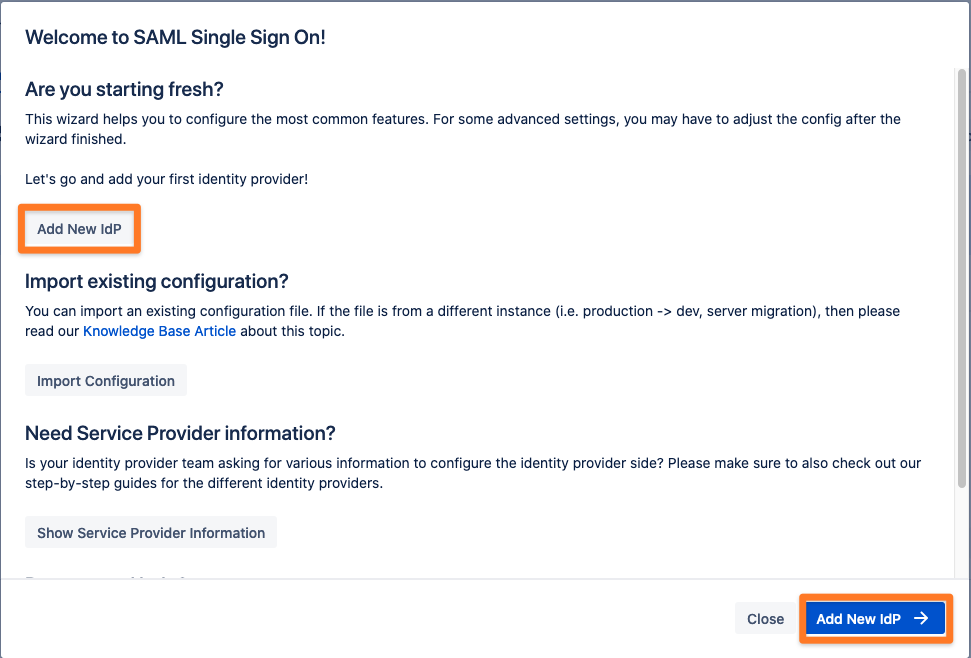
After you clicked "Configure", the Wizard will be triggered. If not, or if you want to add another Identity Provider (IdP) to your existing configuration, click on "Add new IdP +". This guide assumes, that you there is no IdP configured.
The Wizard greets you with information, click on "Add New IdP" to proceed.
Choose Google Cloud identity (G Suite) for the Identity Provider. Keep the Authentication Protocol set to SAML2. You must also provide a (unique) name.
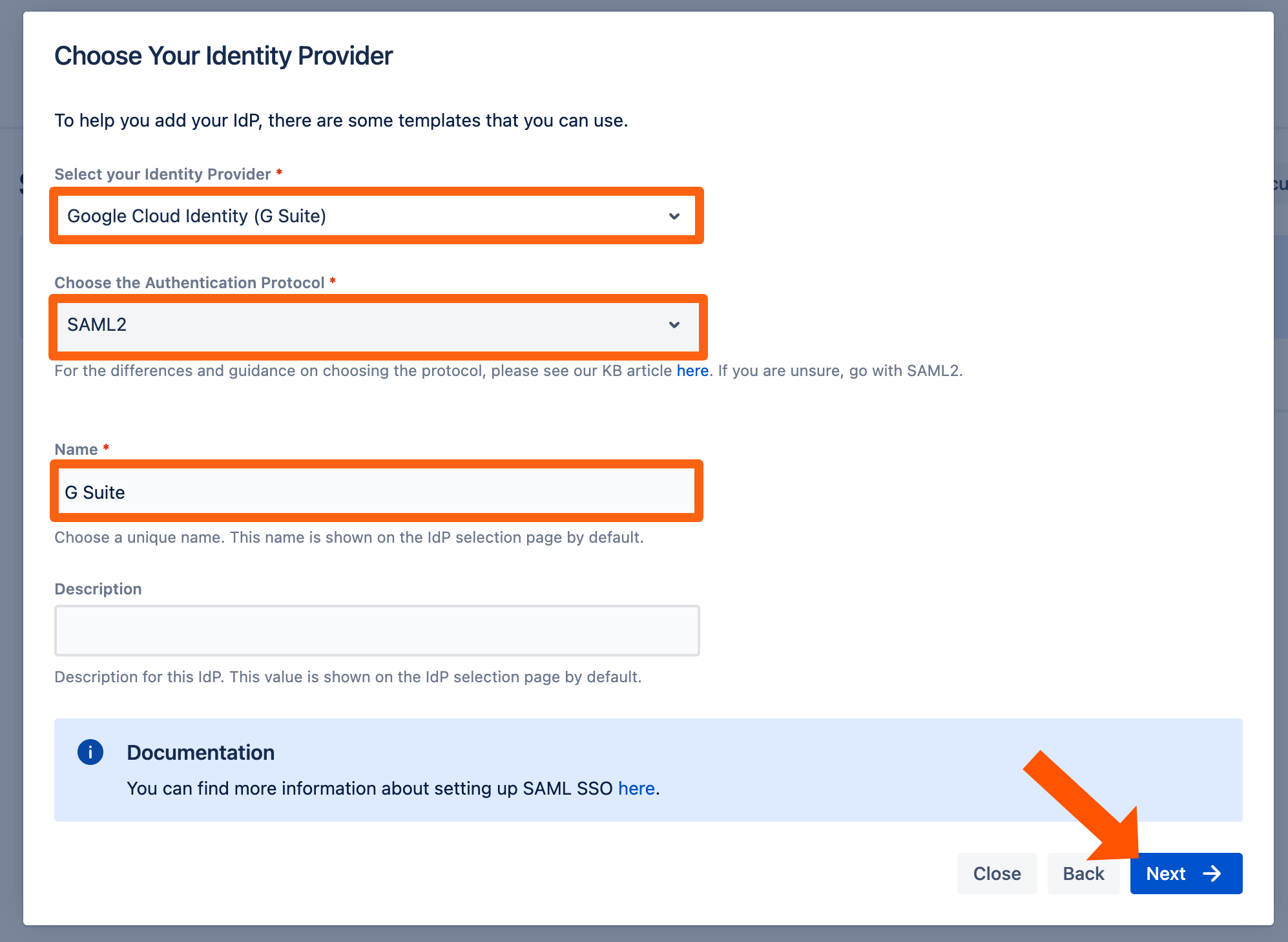
Click "Next".
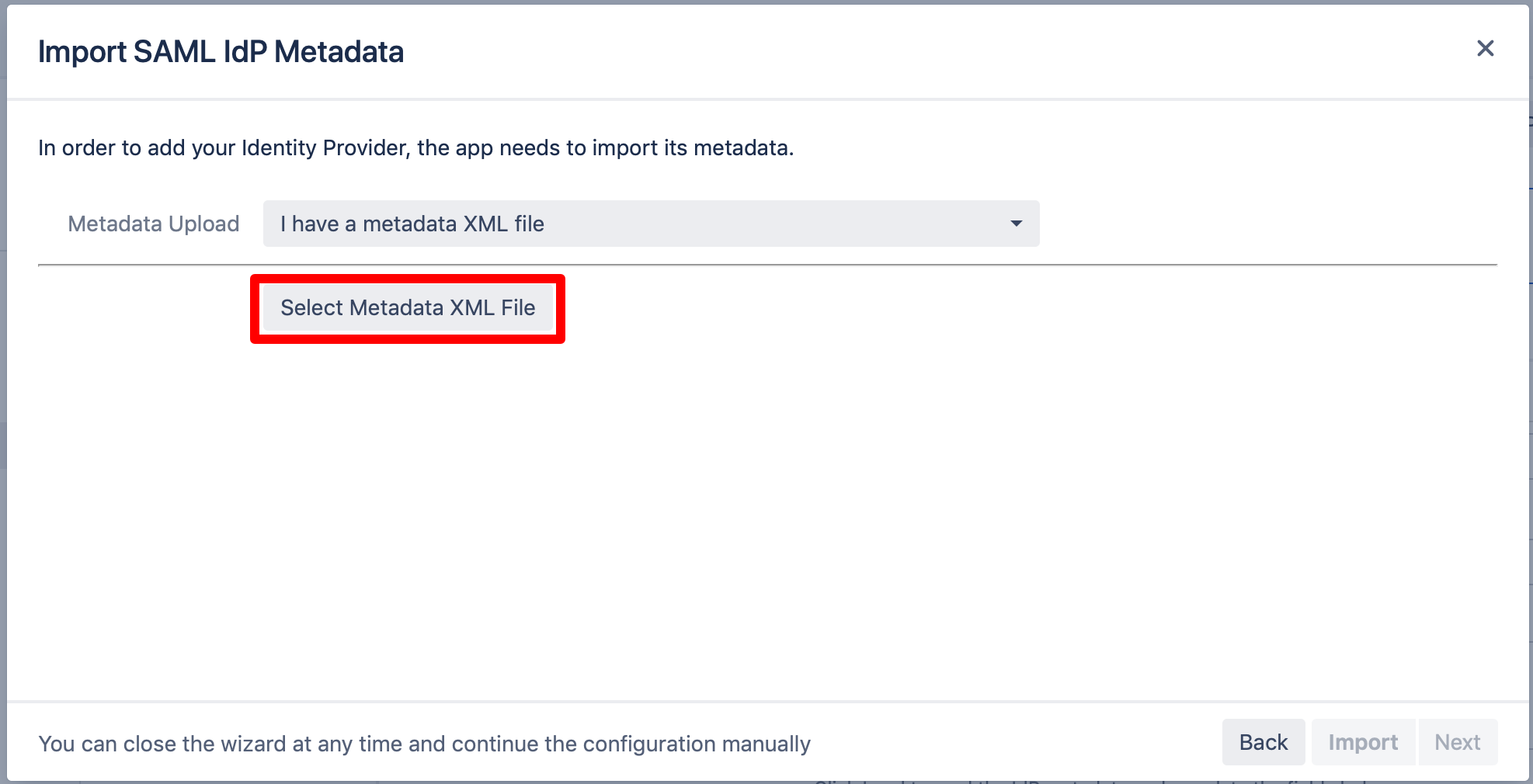
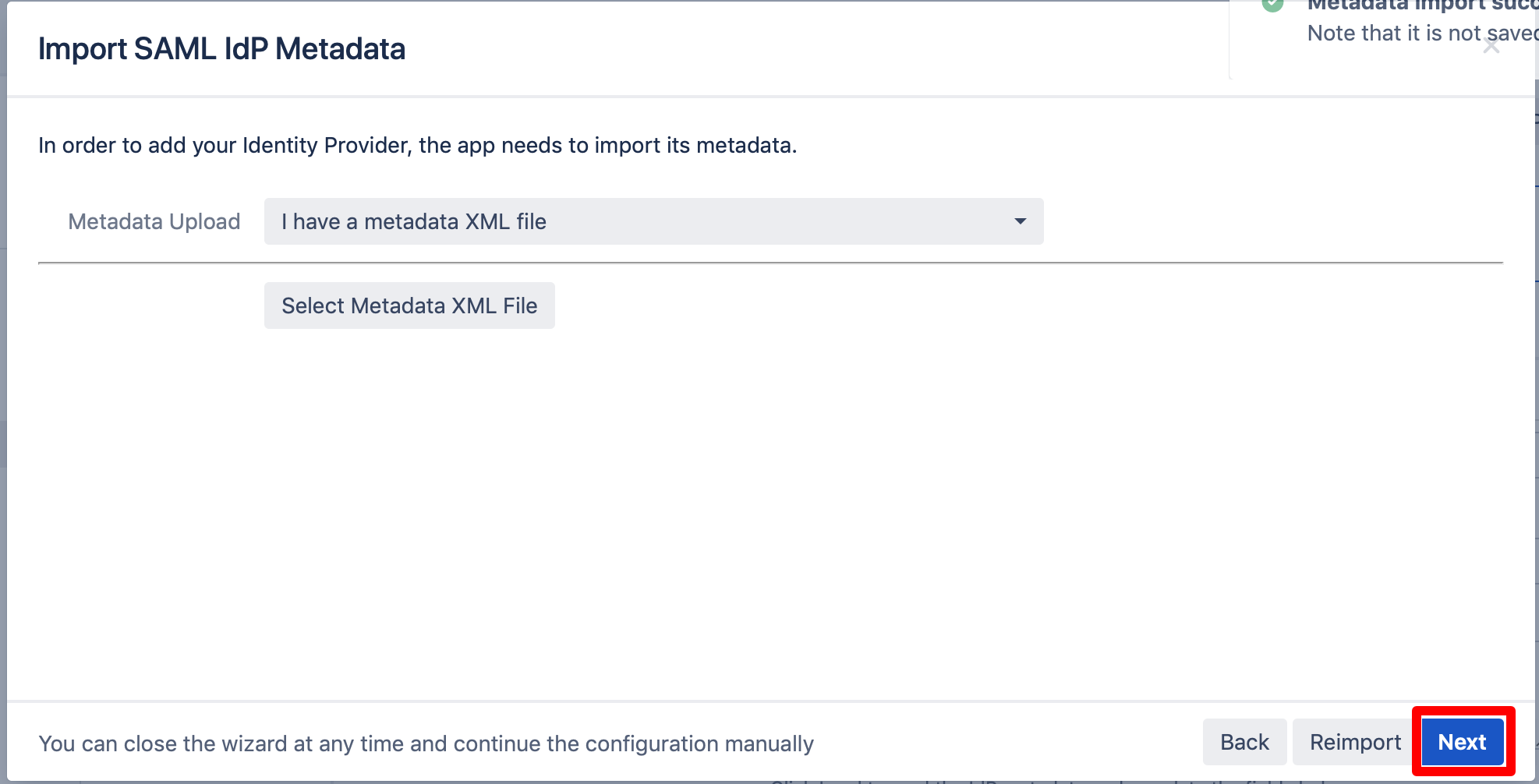
Click on "Select Metadata XML File".
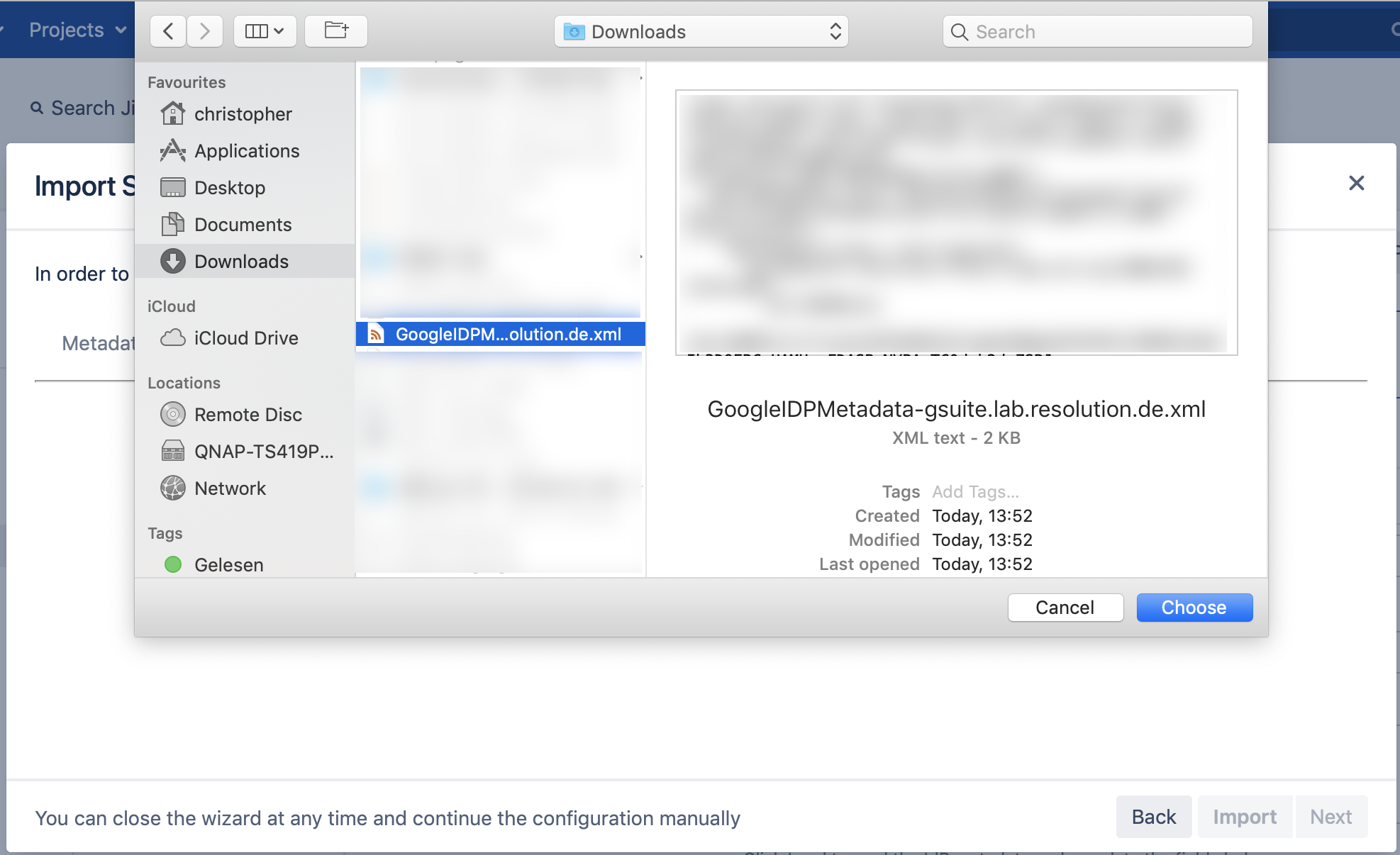
Select the file you have downloaded before and click "Choose".
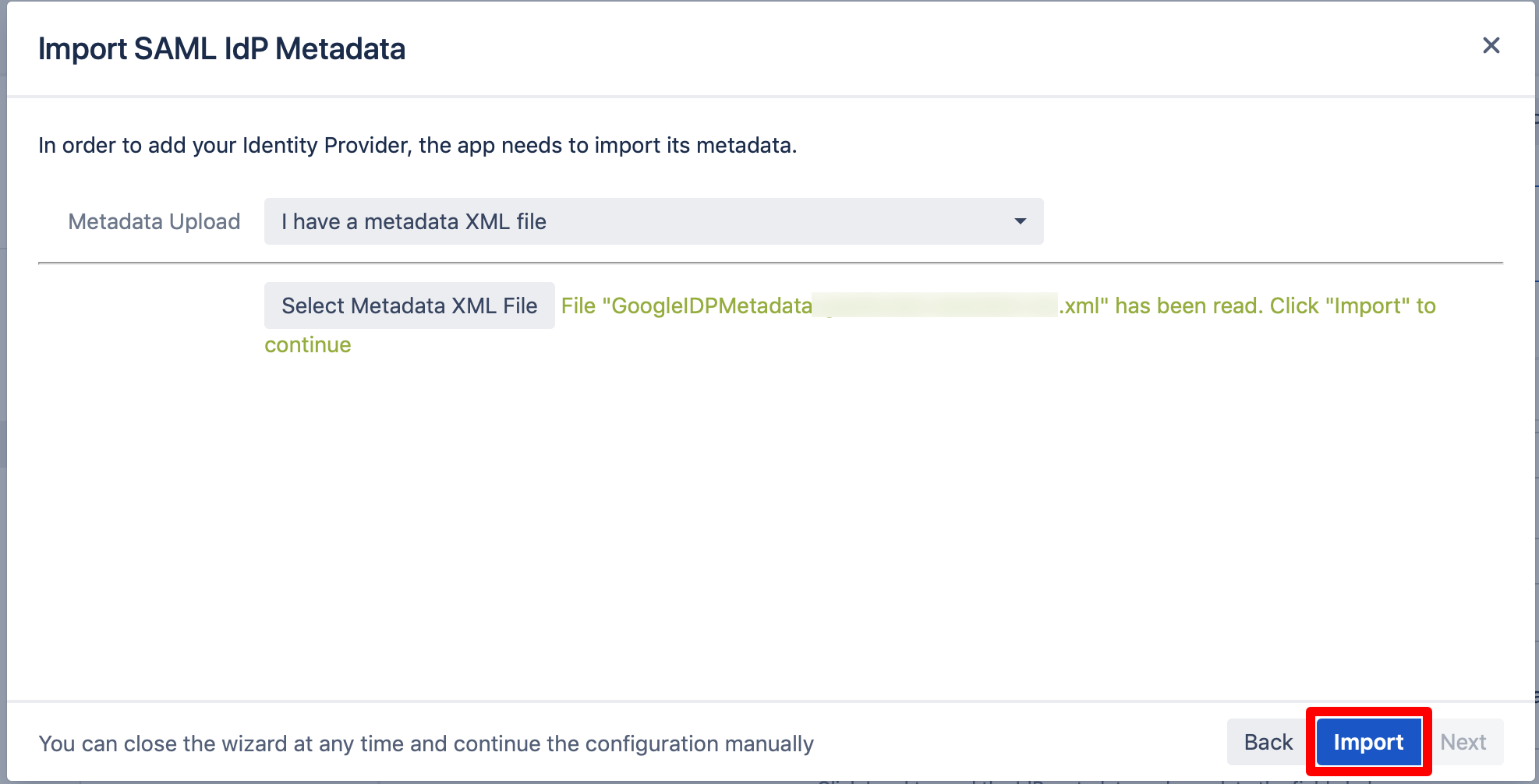
Click on "Import".
Click "Next" to continue.
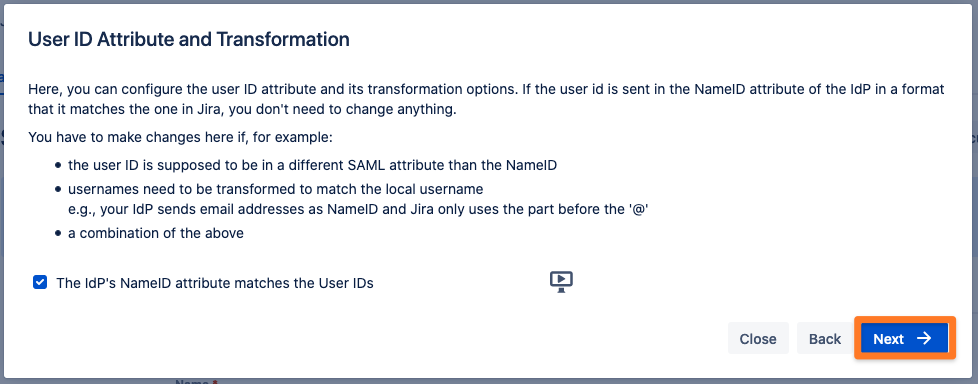
If you configured your Atlassian product and your Identity Provider in a common way, you do not need to change anything here. In that case, just click "Next".
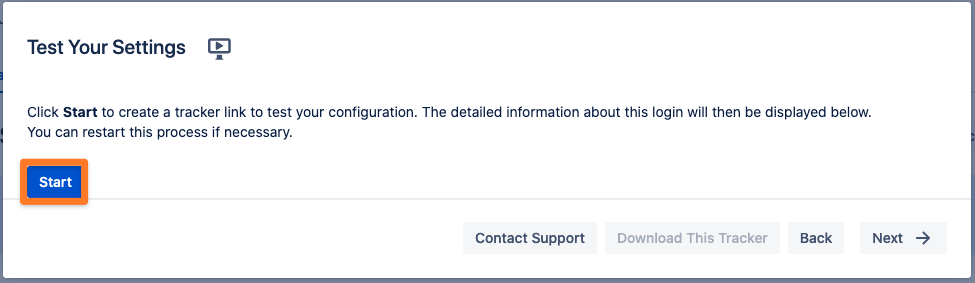
Testing SSO
The wizard also allows to test the Single Sign On. Just follow the steps to test if the login works as expected.
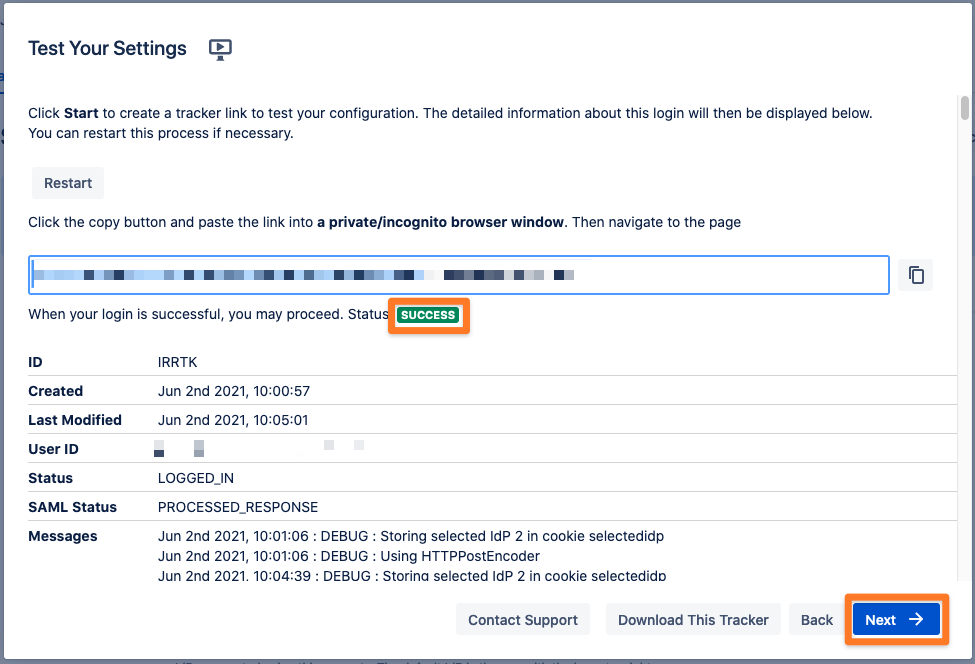
Click on "Start test" to proceed.
Copy the orange marked link and open a new incognito/private tab or a different web browser. Then, paste the link and navigate to it.
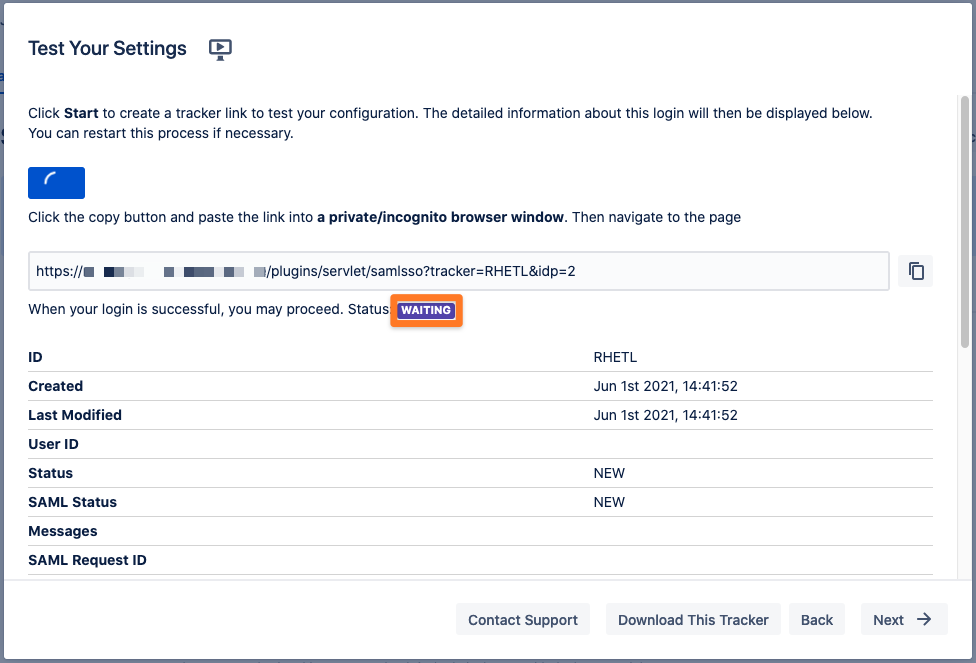
You will be now redirected to GSuite's login page. Please log-in with you username and password.
If everything worked fine, you will log in into your Atlassian product. In the other tab/browser in which you were configuring the SAML SSO plugin, you can see also the "SUCCESS" status, if everything worked as expected. Click Next to proceed.
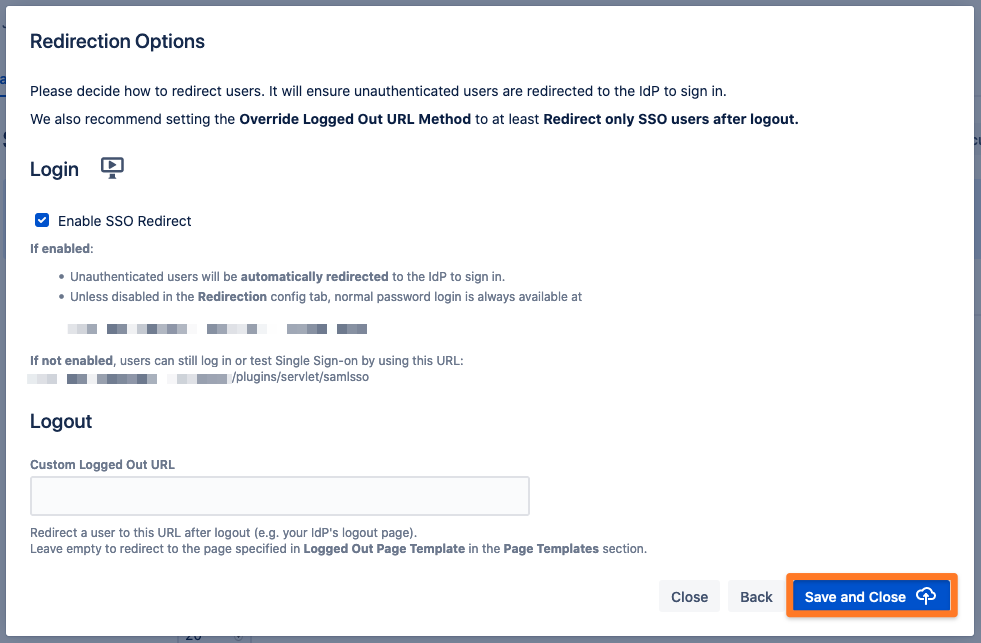
SSO Redirection
As a last step, you can set the Enable SSO Redirect option. If set, all users will be redirected to Single Sign On, thus they will be logged in via the IdP. Click on Save & Close to finish the configuration.