OpenID Connect for Keycloak with Just-in-Time Provisioning
Goal
Configure SAML Single Sign-On for Atlassian Data Center to work with Keycloak, using Just-in-Time provisioning to automatically create and update users during Single Sign On.
Prerequisites
Identity Provider Keycloak
Your Atlassian Data Center or Server application must be accessible via HTTPS. (read more about it in the Atlassian documentation, i.e. for Jira or Confluence)
Step-by-Step Setup Guide
Install the SAML SSO App
In your Atlassian product, open the in-product marketplace as described in the Atlassian documentation.
Search for "resolution saml" and click "Install" for SAML Single Sign On (SSO) by resolution Reichert Network Solutions GmbH.
After the installation is complete, click Manage Apps/Addons.
Configure SAML SSO
For the next steps, please go to Manage apps (or addons), choose SAML SSO and click Configure.
First Steps - Wizard
After you clicked "Configure", the Wizard will be triggered. If not, or if you want to add another Identity Prover (IdP) to your existing configuration, click on "+ Add IdP". This guide assumes, that there is no IdP configured.
The Wizard greets you with information, click on "Add new IdP" to proceed.
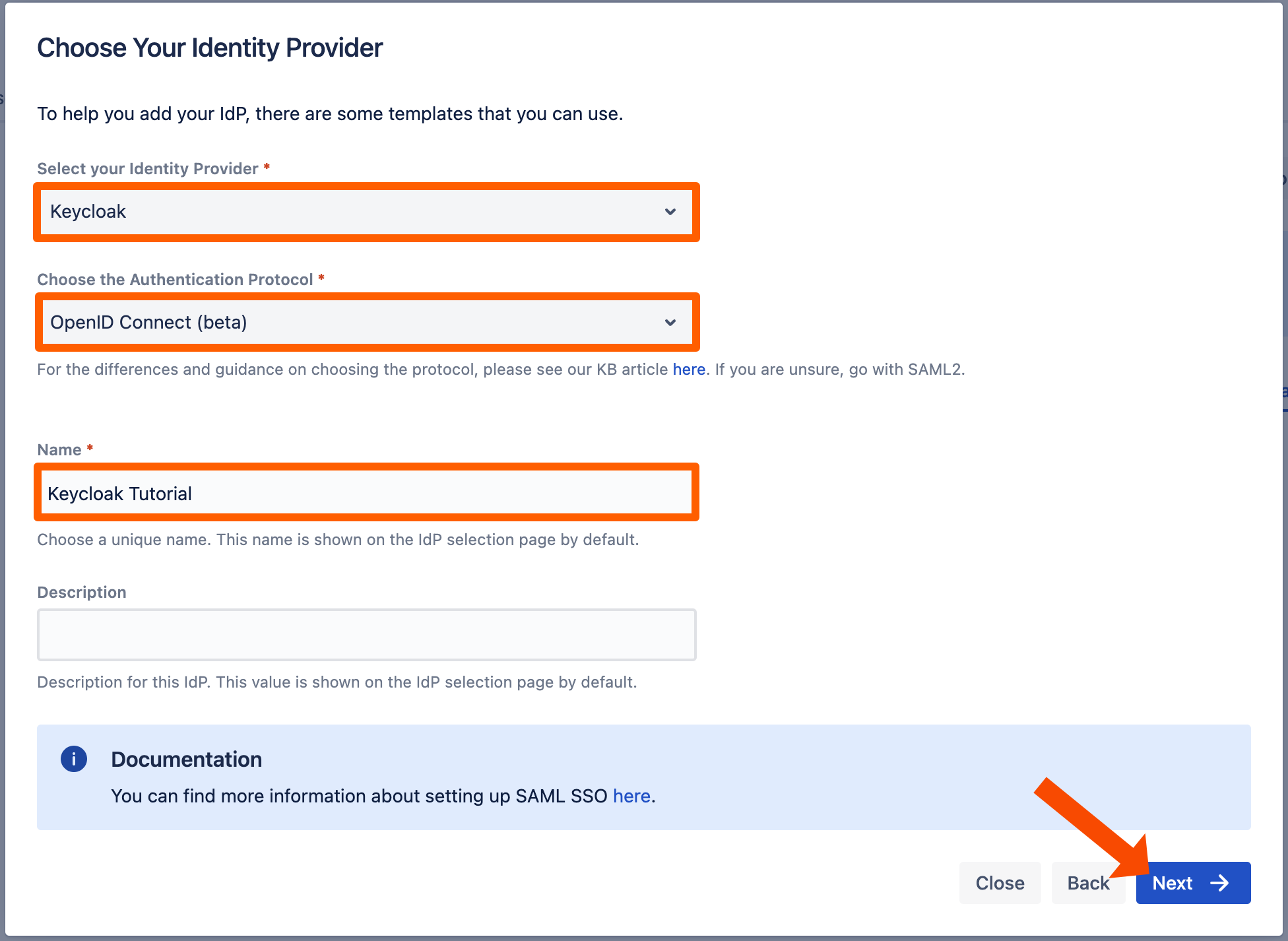
Select Keycloak for your identity provider and select OpenID Connect for the authentication protocol. Enter a unique name and click Next to continue.
Copy the callback url to your favourite text editor. 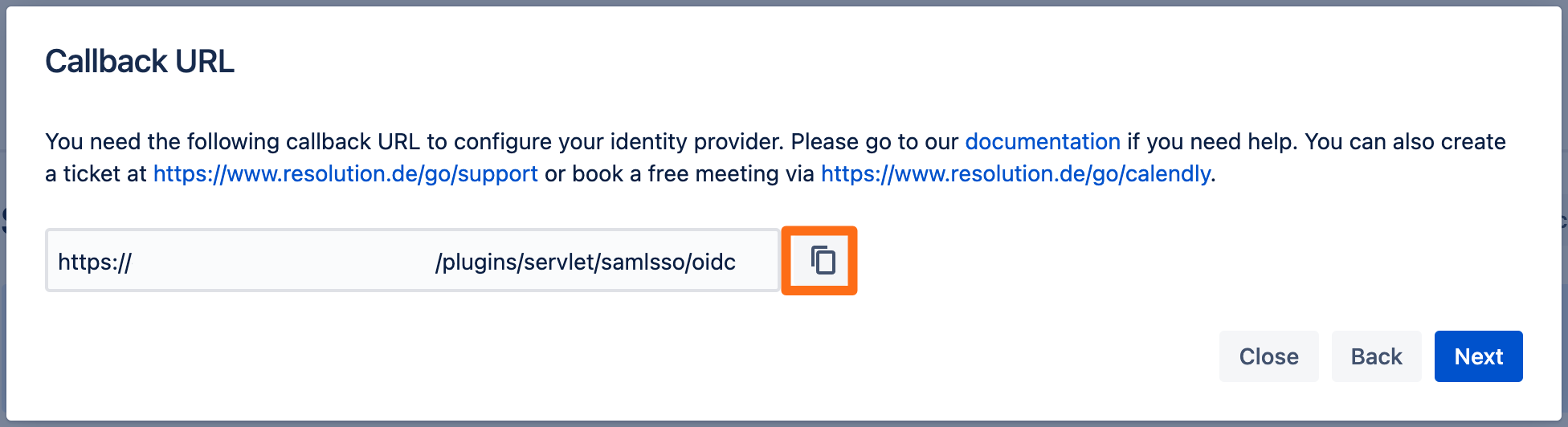
Go to your Keycloak server and choose your realm. Then go to Clients and click Create.
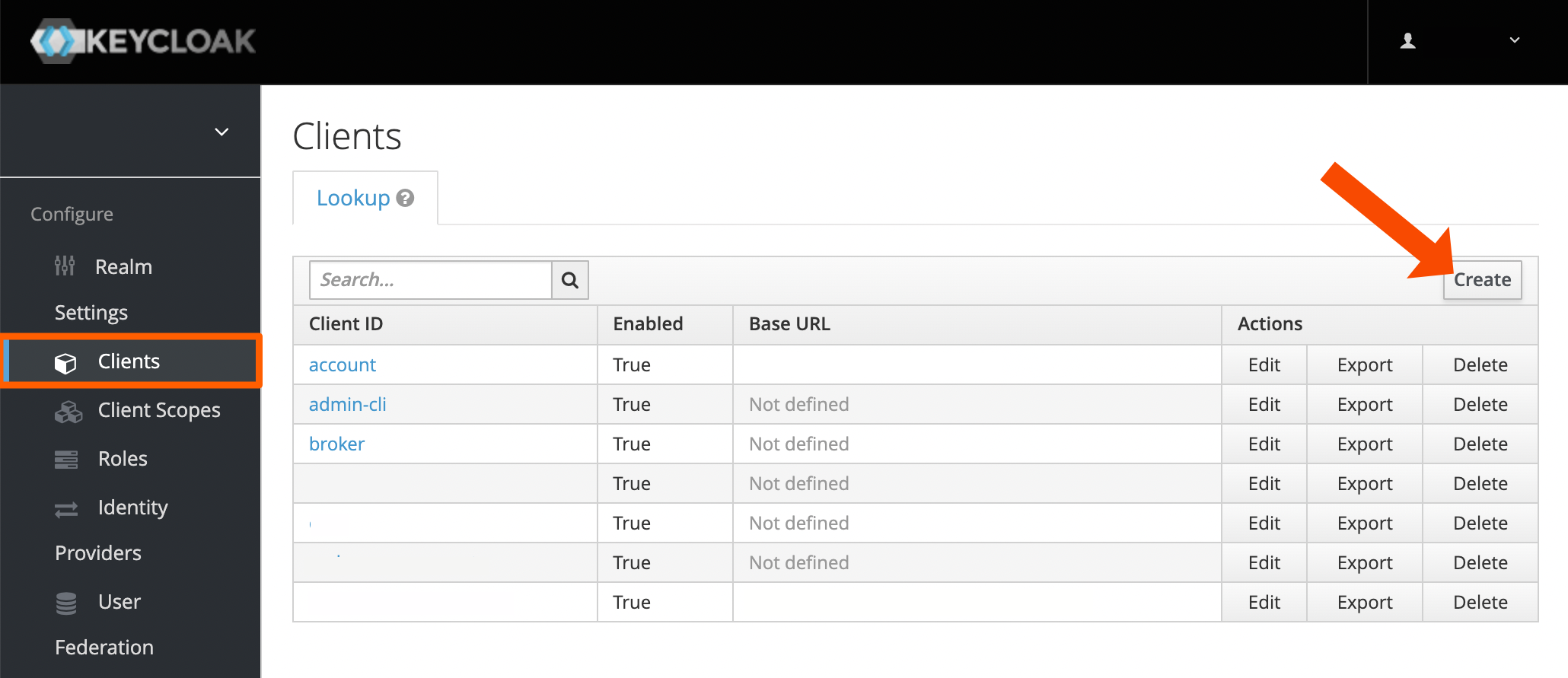
Enter a Client ID. That must be unique. Click Save to continue.
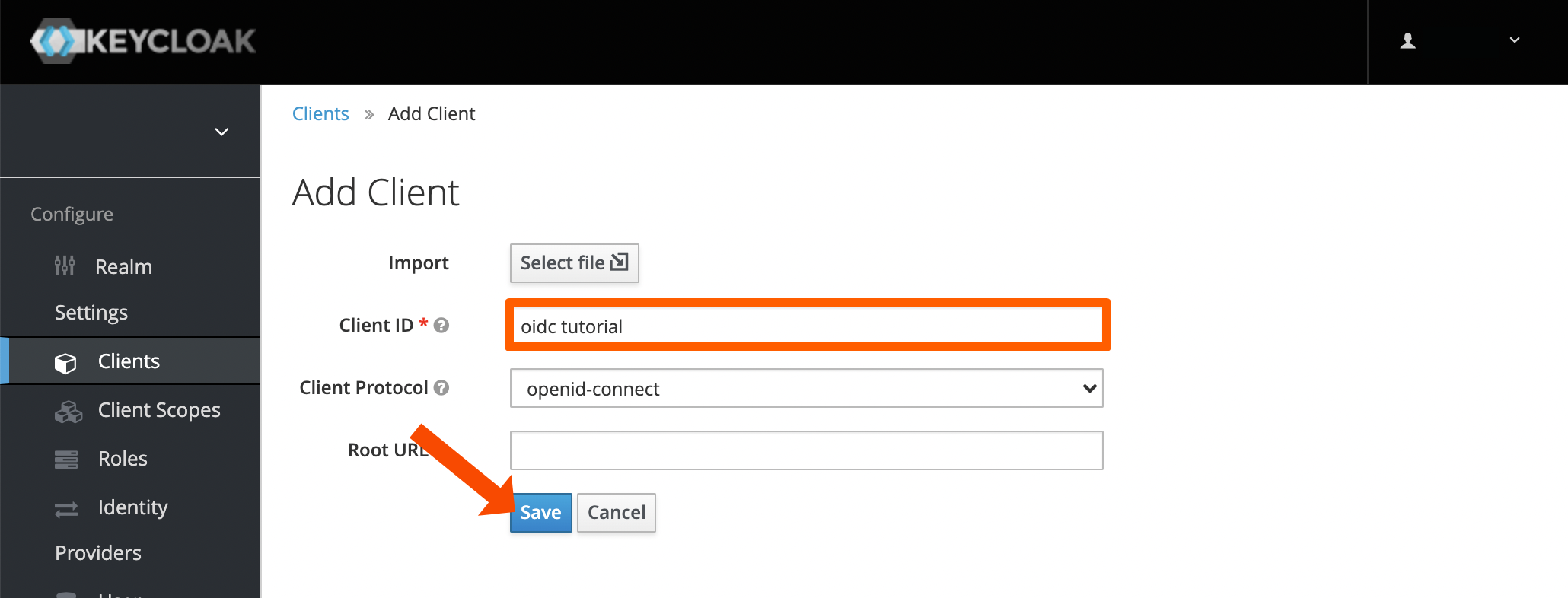
Next, scroll down and choose confidential for the Access Type. For the Valid Redirect URIs enter the callback URL from before.
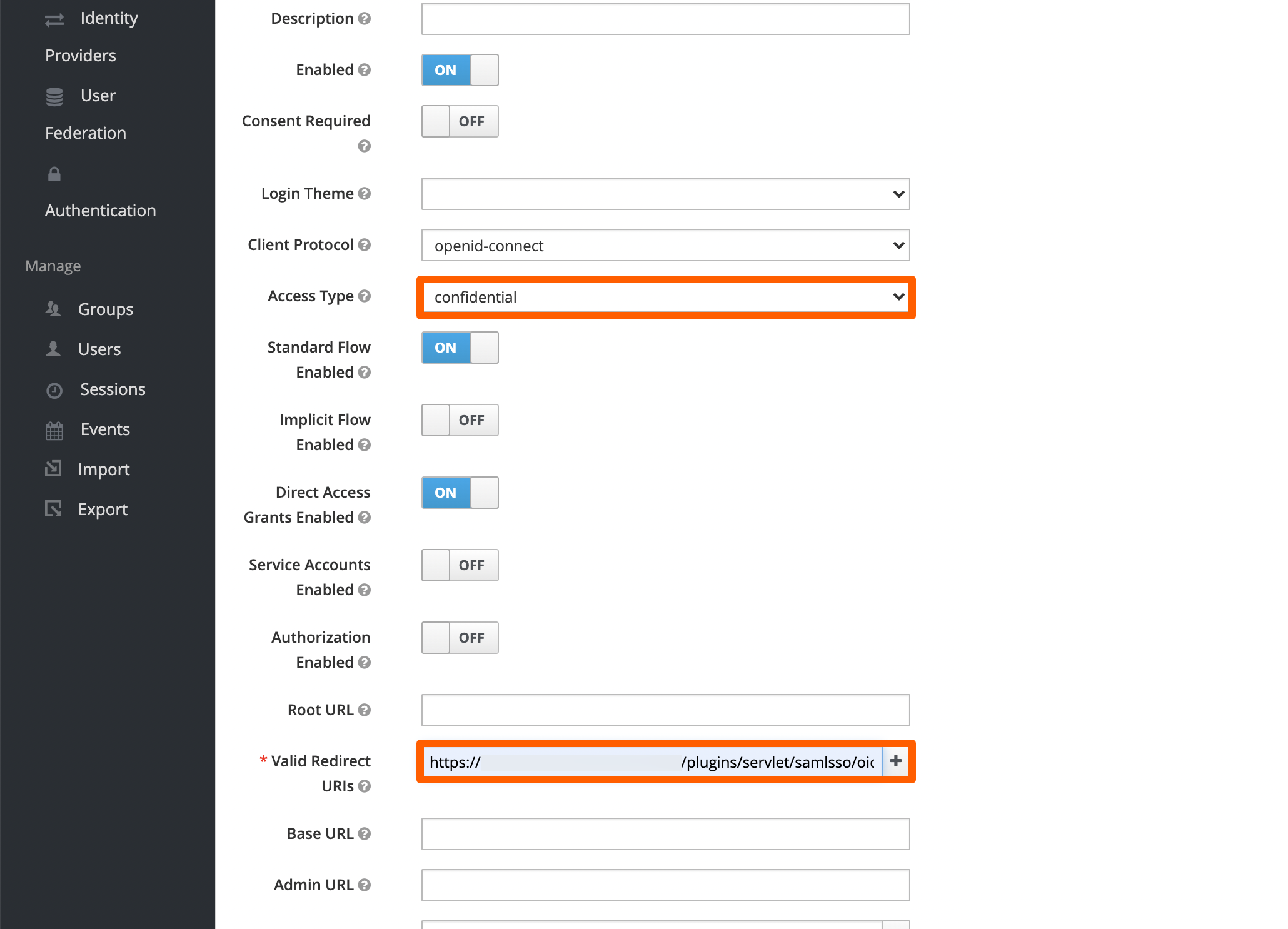
Next, click Save and reload the page. Without reloading, the options for the next step is not displayed!
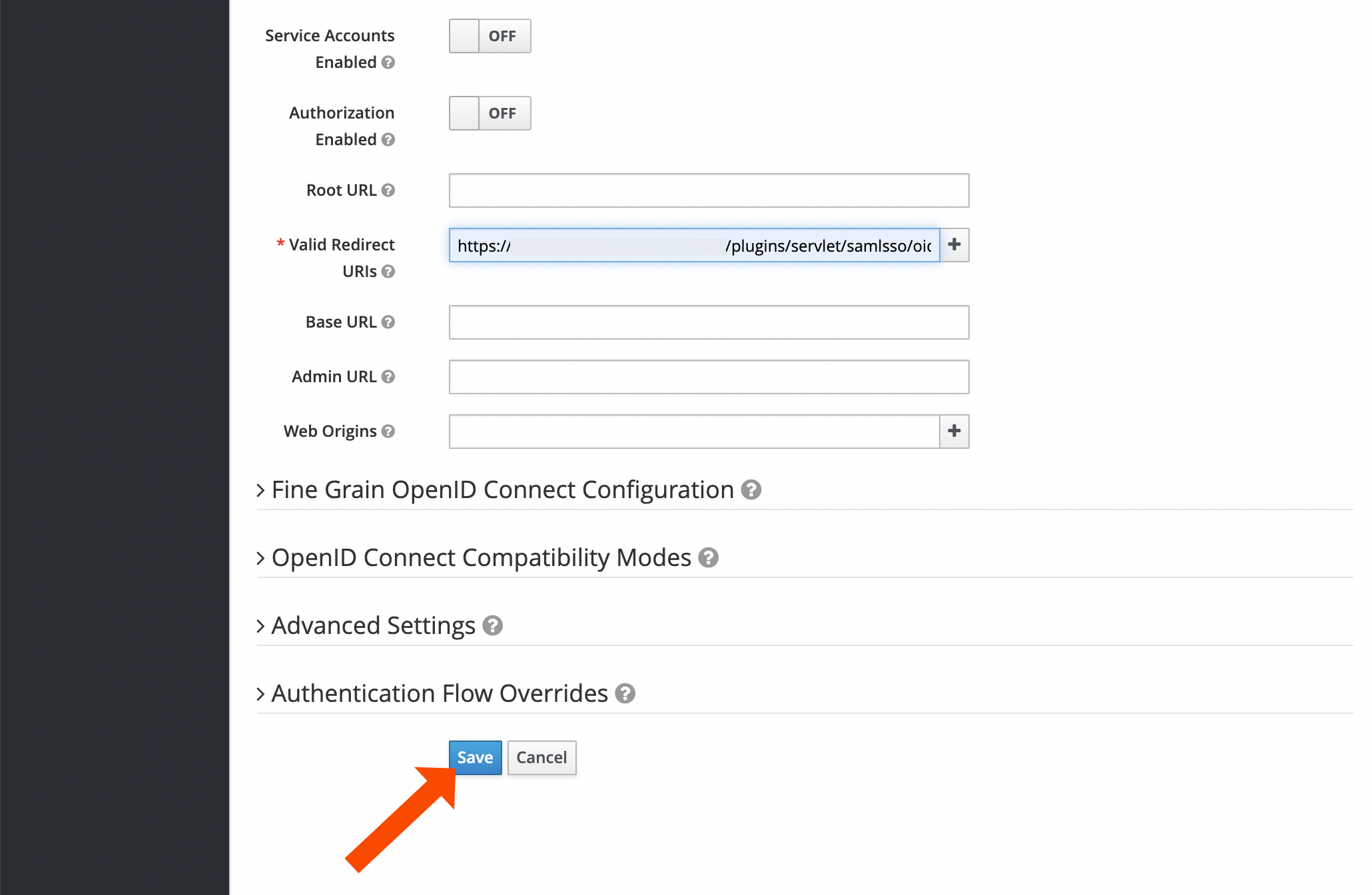
After reloading the page, go to the Credentials tab. Without reloading, the tab is not displayed!
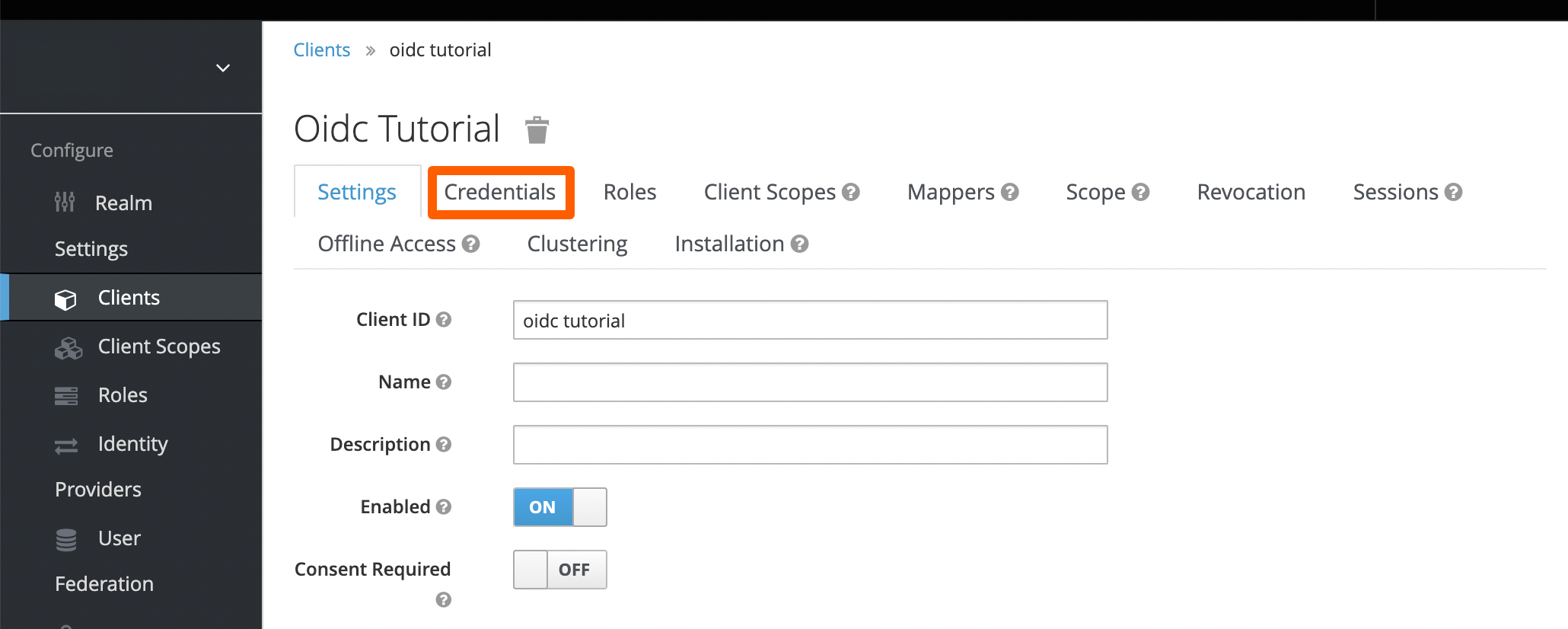
Copy the secret to your favorite text editor, we will need it soon.
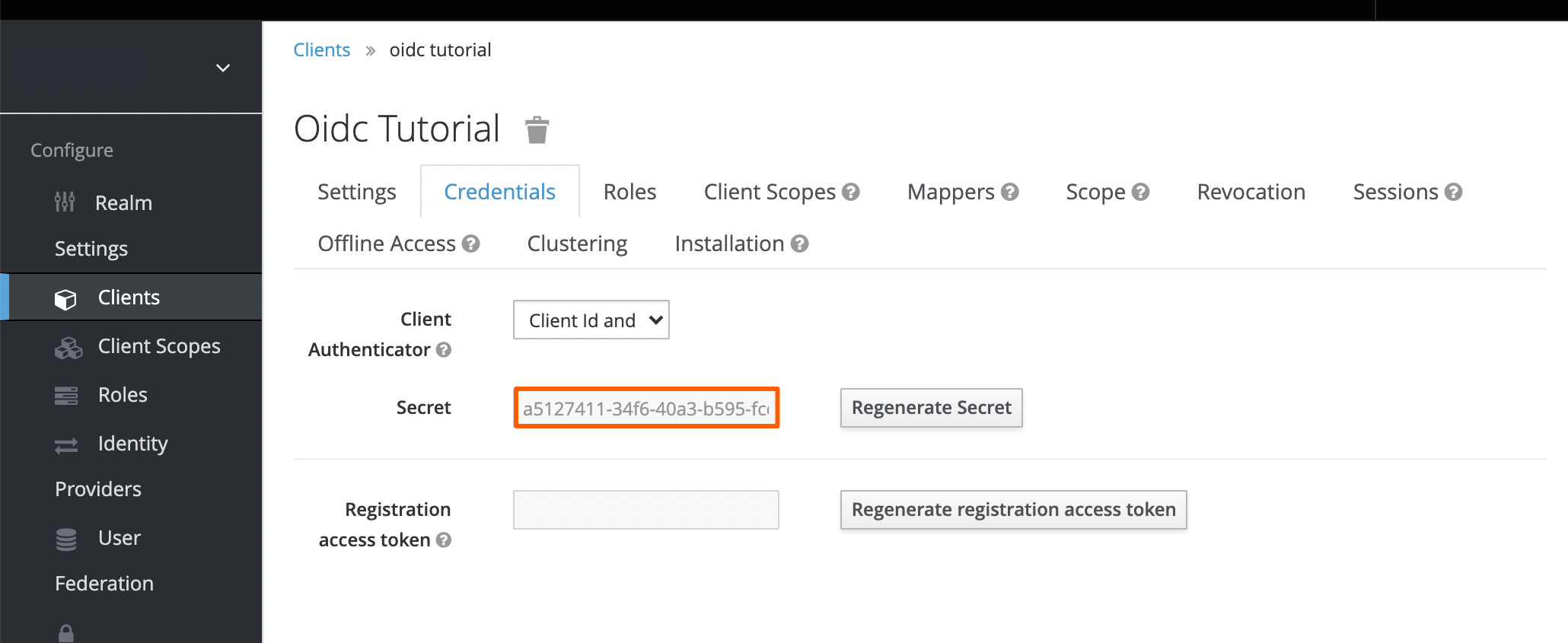
Enter your Keycloak Base Url and Keycloak Realm, next click Generate Metadata Url.
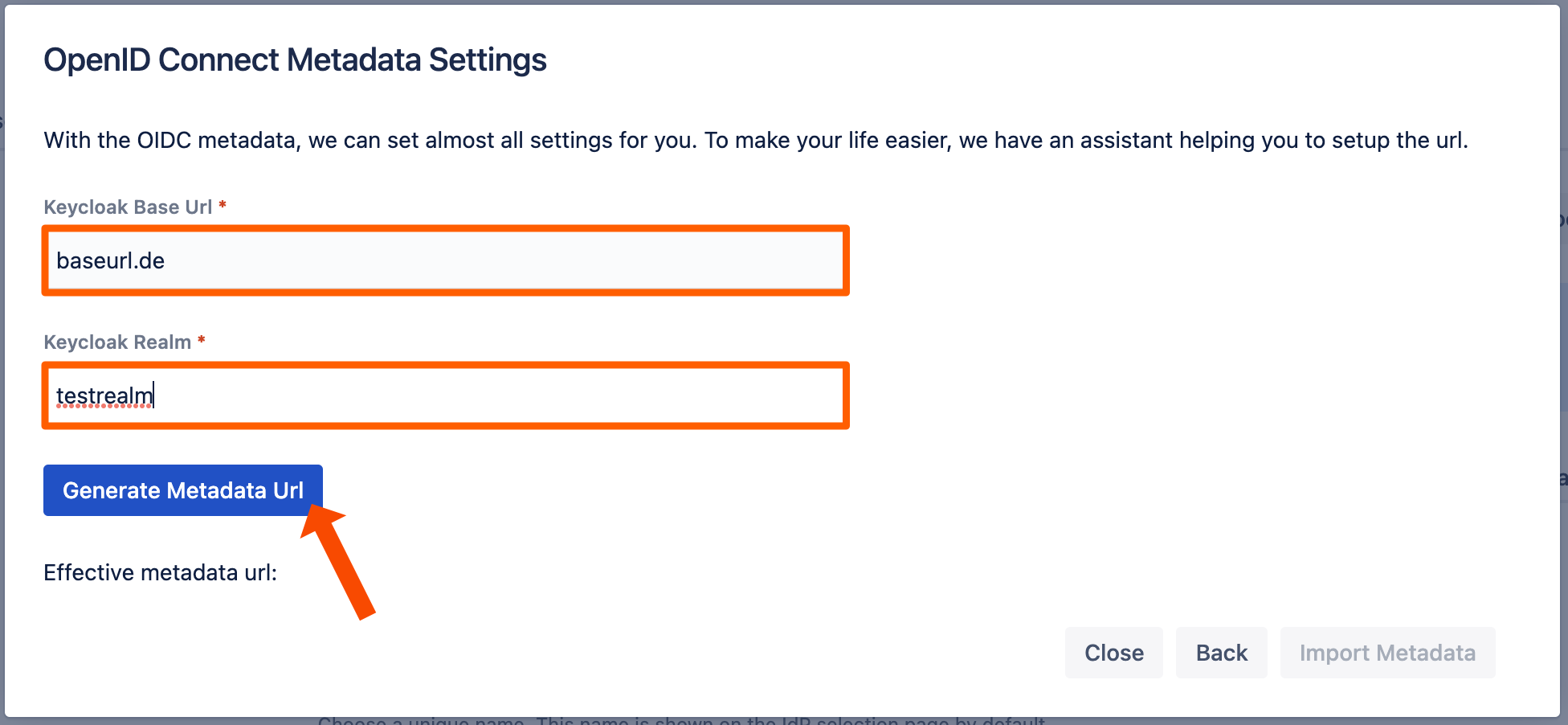
Click Import Metadata.
You will see this message if the import was successful.
To finish the wizard, click Save and Close.

To Configure Just-In-Time provisioning, go to UserSync.
Click Create Connector and choose Just-In-Time.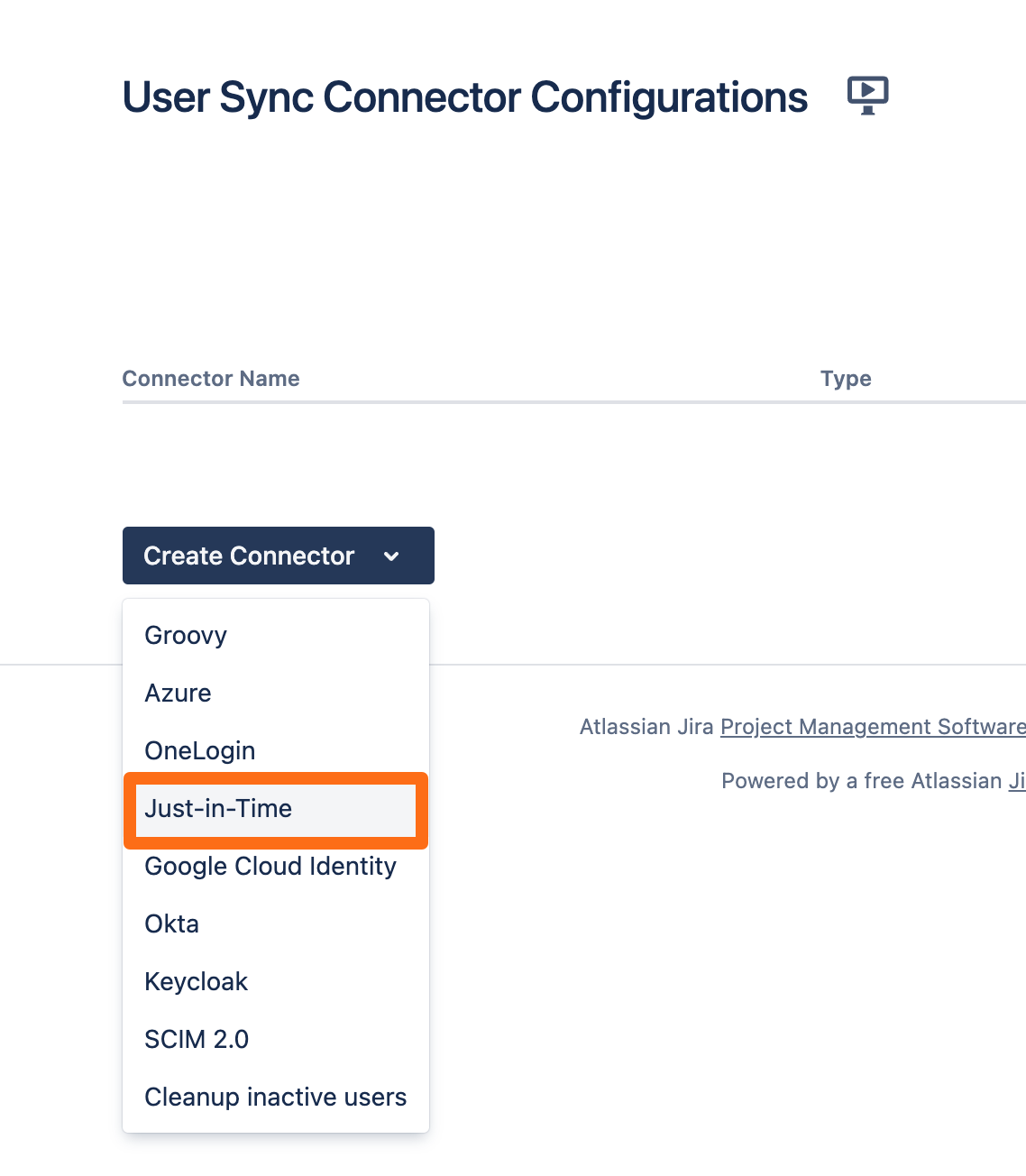
On the next screen, you must either choose an existing directory or click the Create new empty directory... button.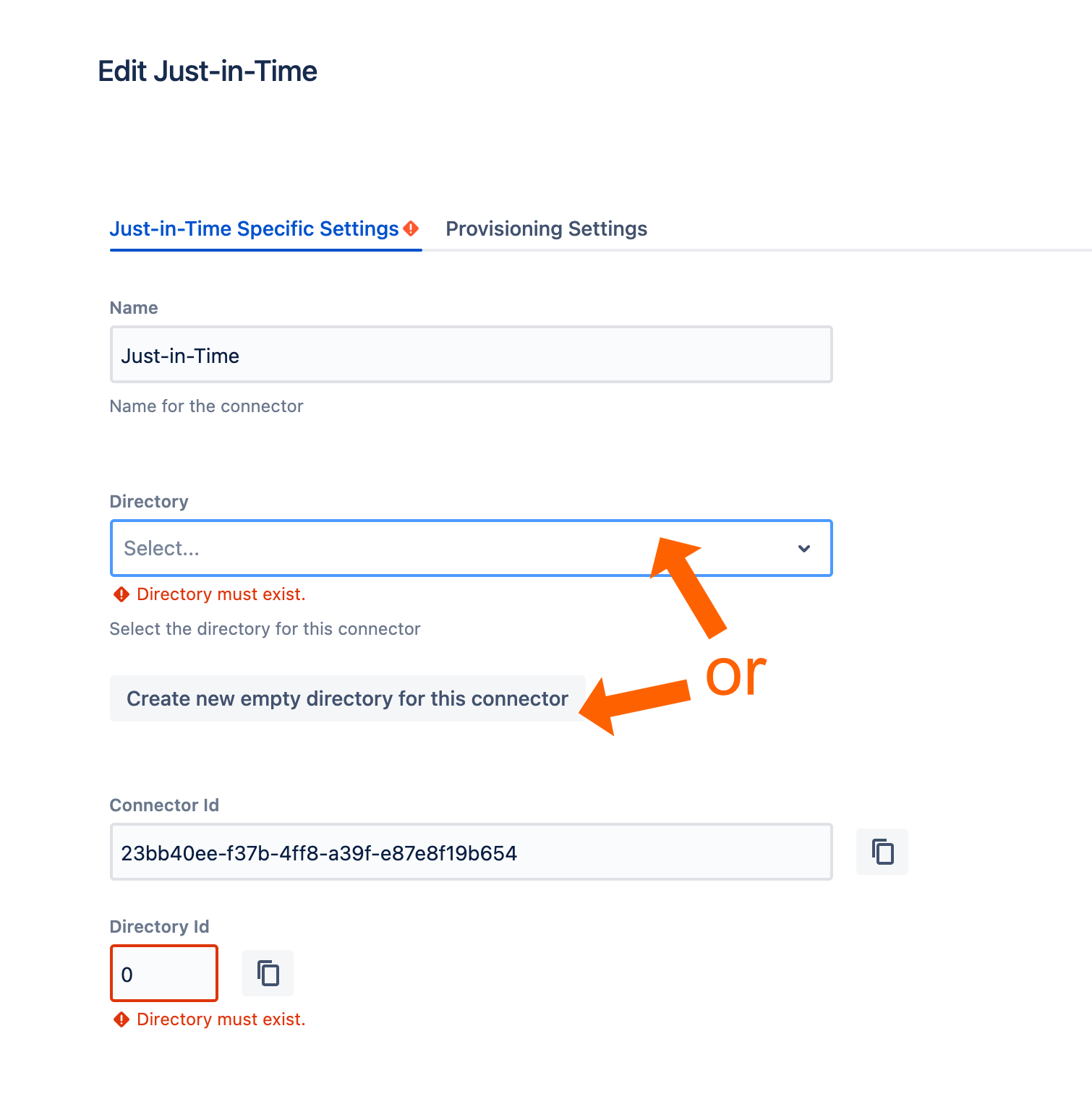
Next, go to the Provisioning Settings. In order for our app to create new users, you must map the Username, Full Name and Email. Additionally, you may also want to assign users automatically on creation to groups. You can use Always Assign Users to Certain Groups for this.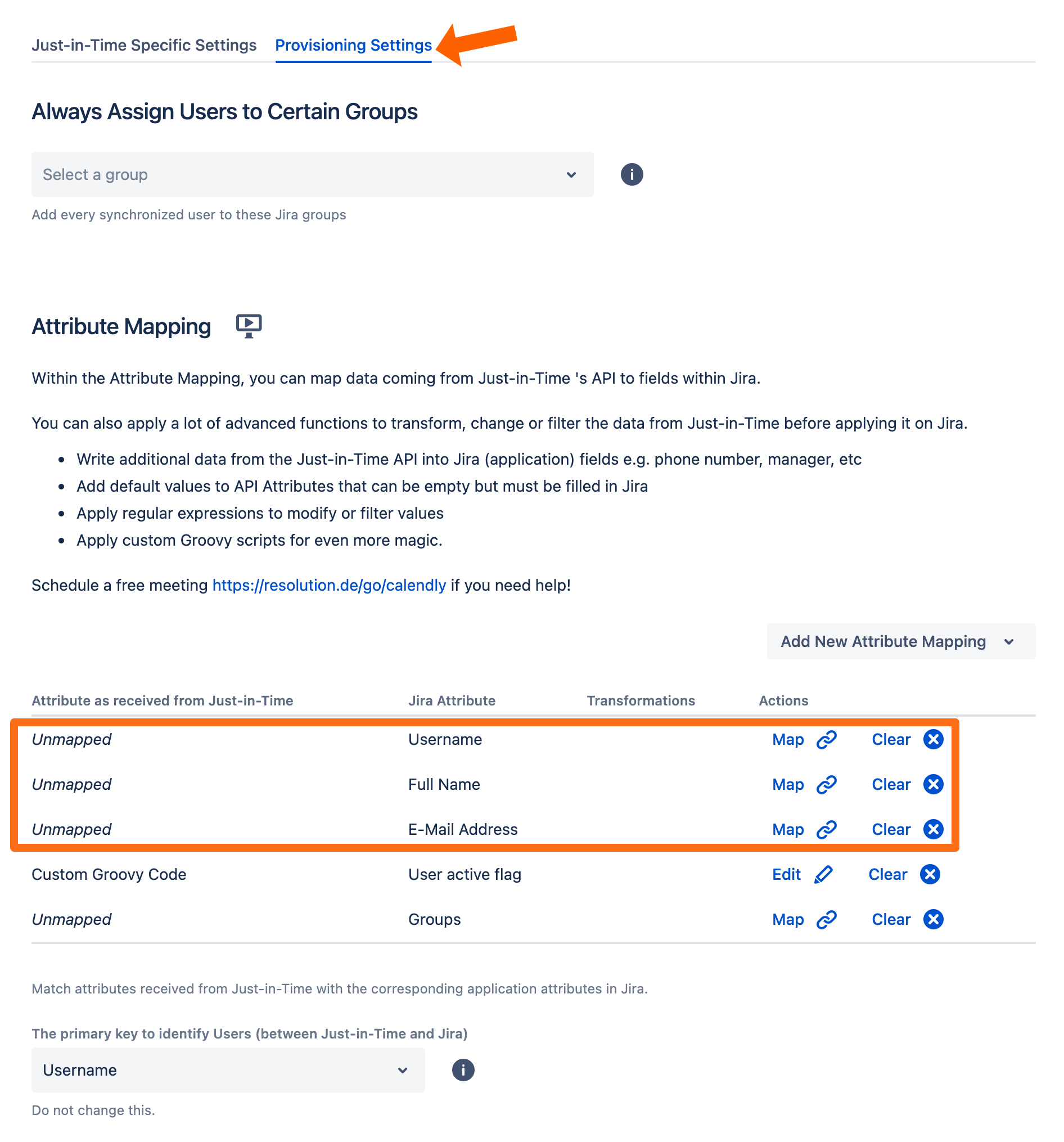
For Keycloak, you need the following mappings. Please note that mapping for the Full Name works a little differently. Thus, we will show how to map the fullname and the username
Attribute | Value |
|---|---|
Username | |
Full Name | {given_name} {family_name} |
E-Mail Address |
Keycloak does not send the Full Name in one field. It sends the given name and the family name in two attributes that we need to combine.
For the Full Name row, click Map.
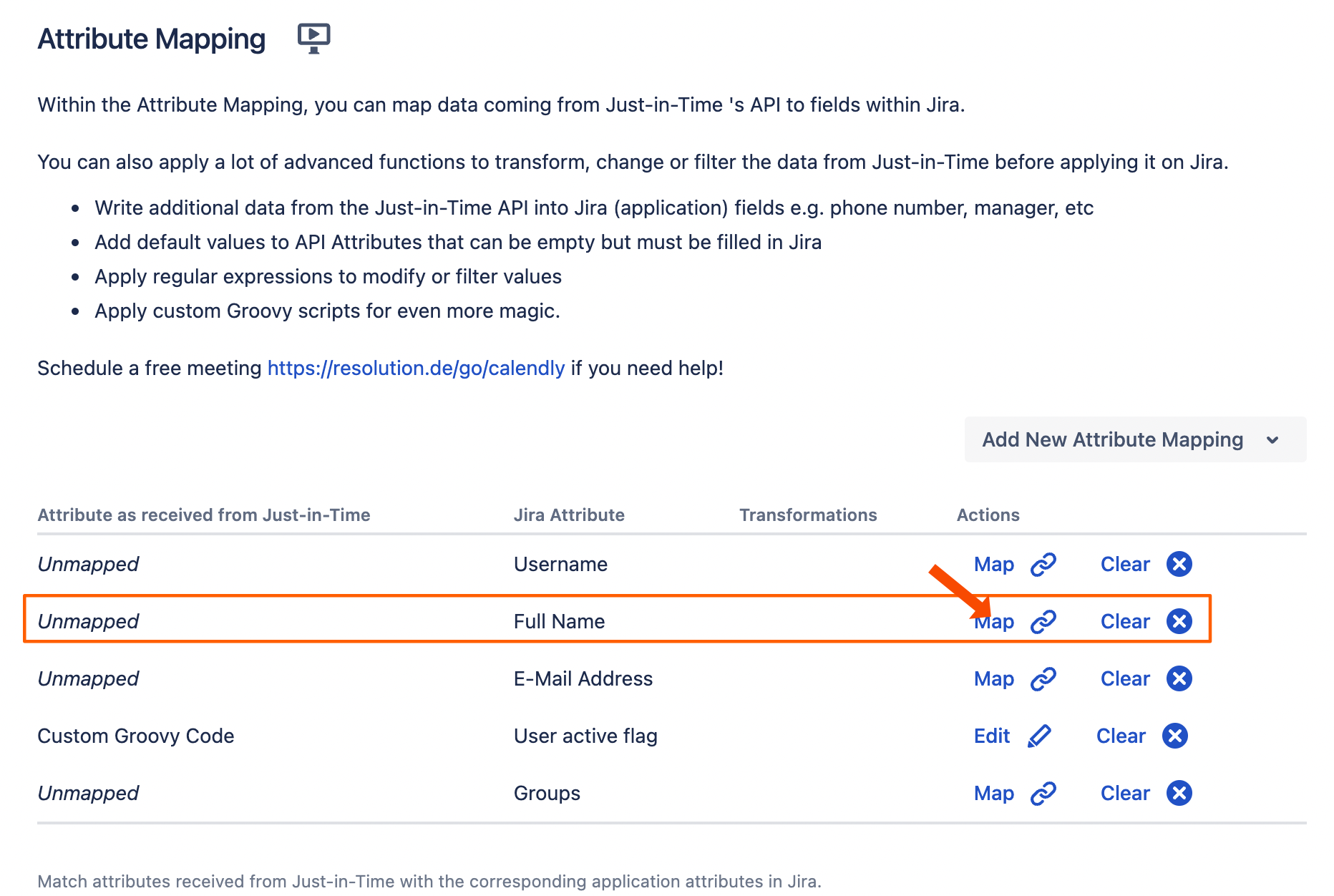
For the Source Type, choose Combine multiple attributes... .
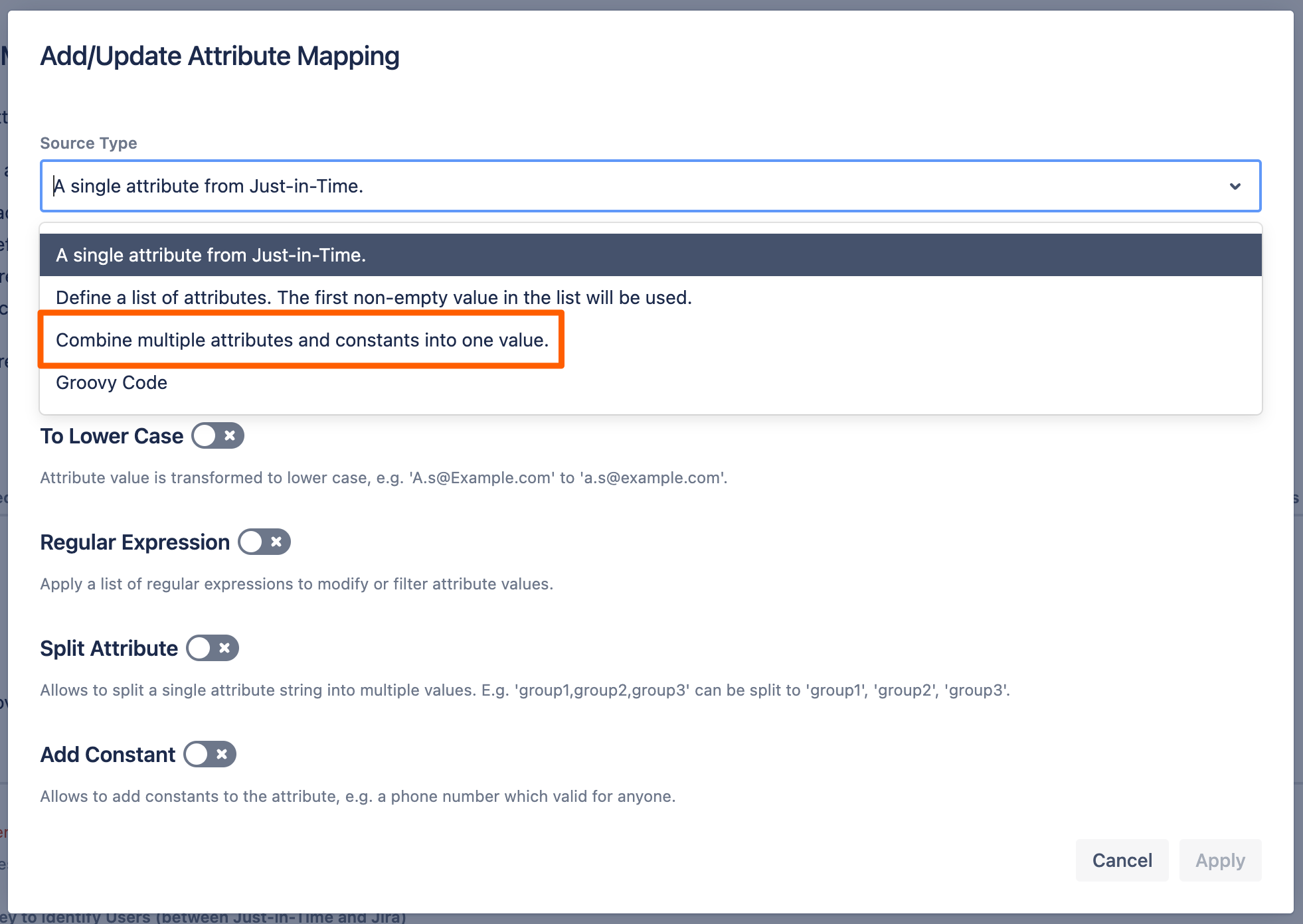
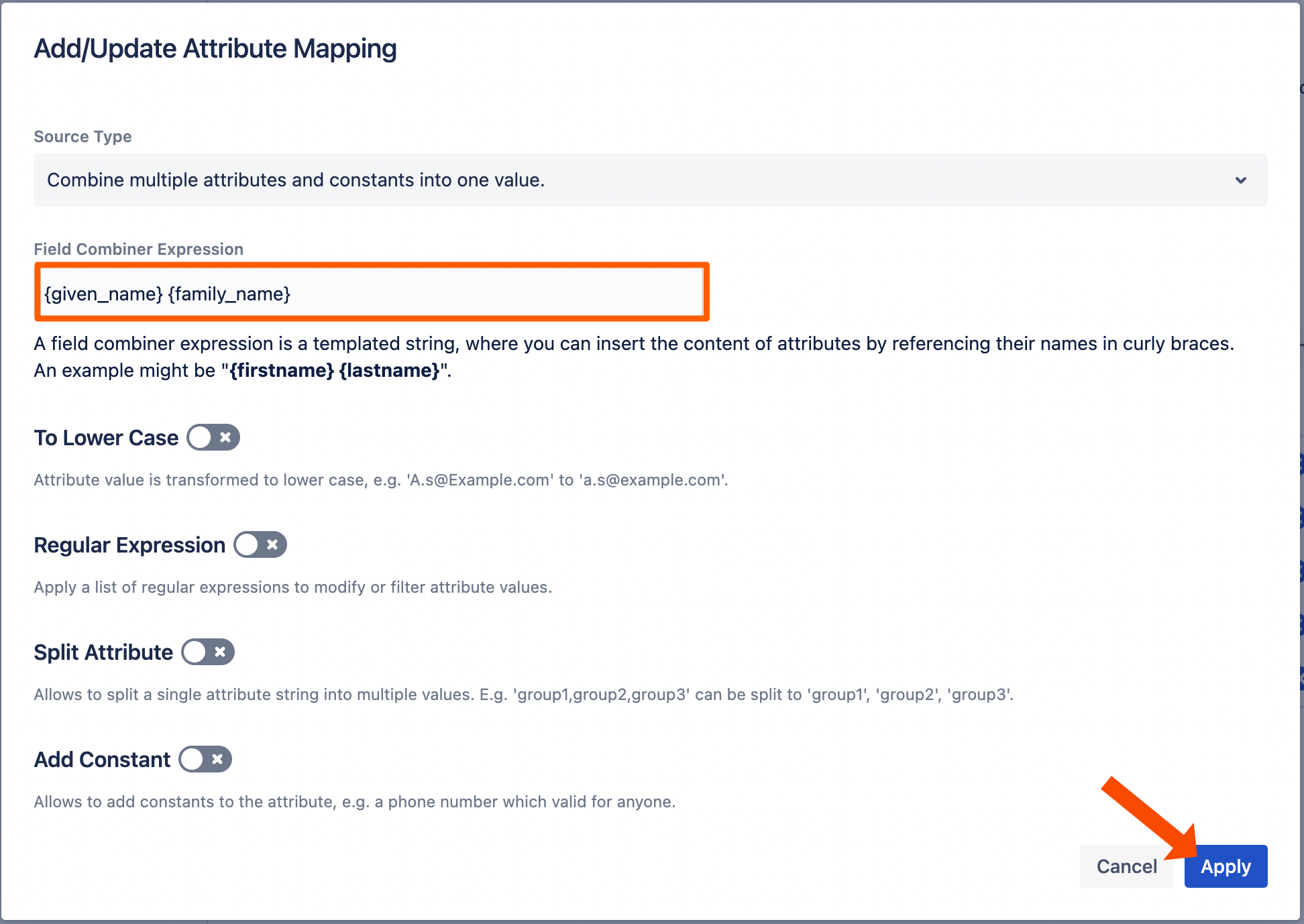
For the Field Combiner Expression enter {given_name} {family_name} . Click Apply to finish the mapping.
For the Username and Email row, click Map and enter the attributes from the table above. If you need to transform the value, you can do this here. Click Apply to finish.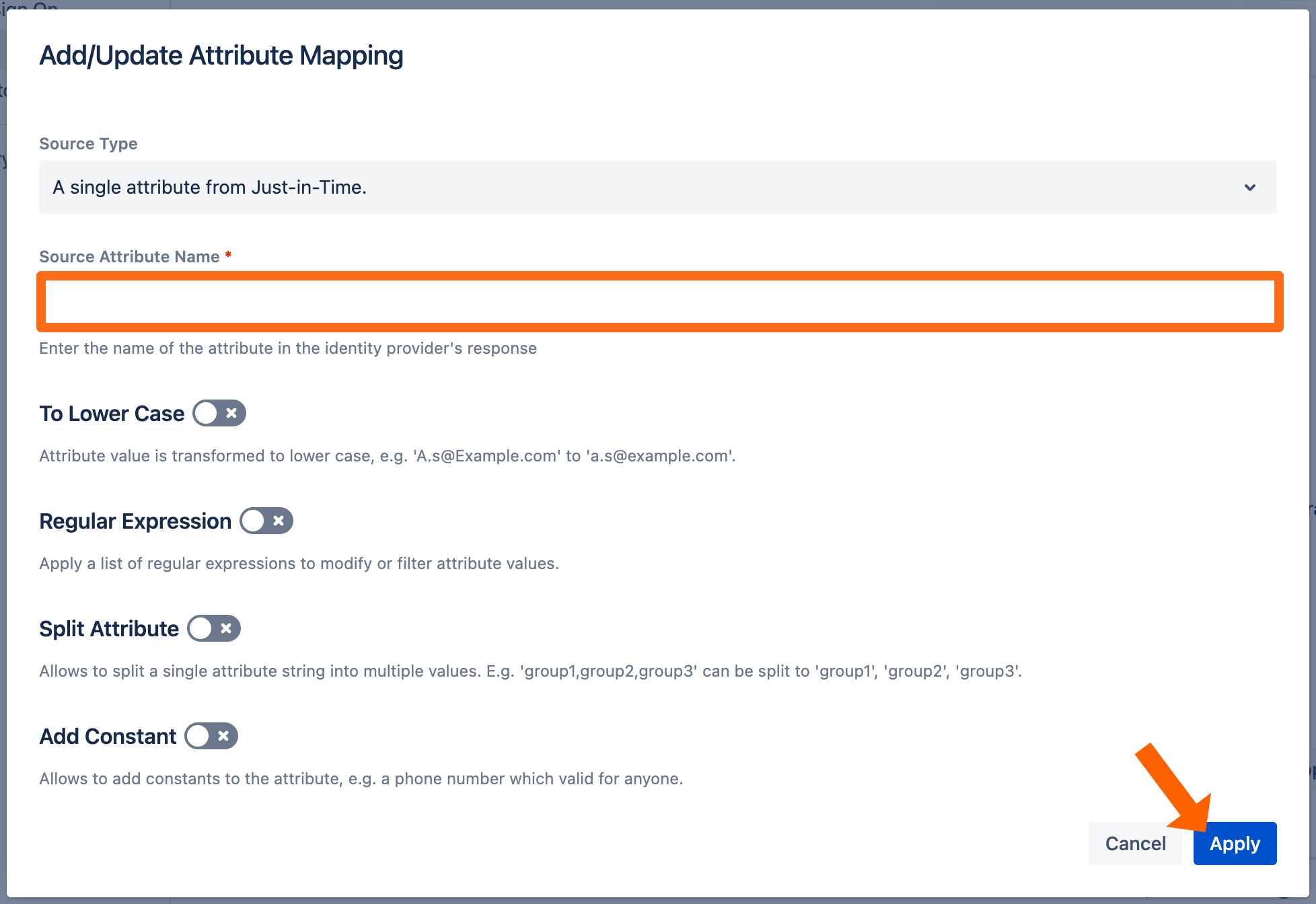
After mapping all necessary attributes, your view should look like this:
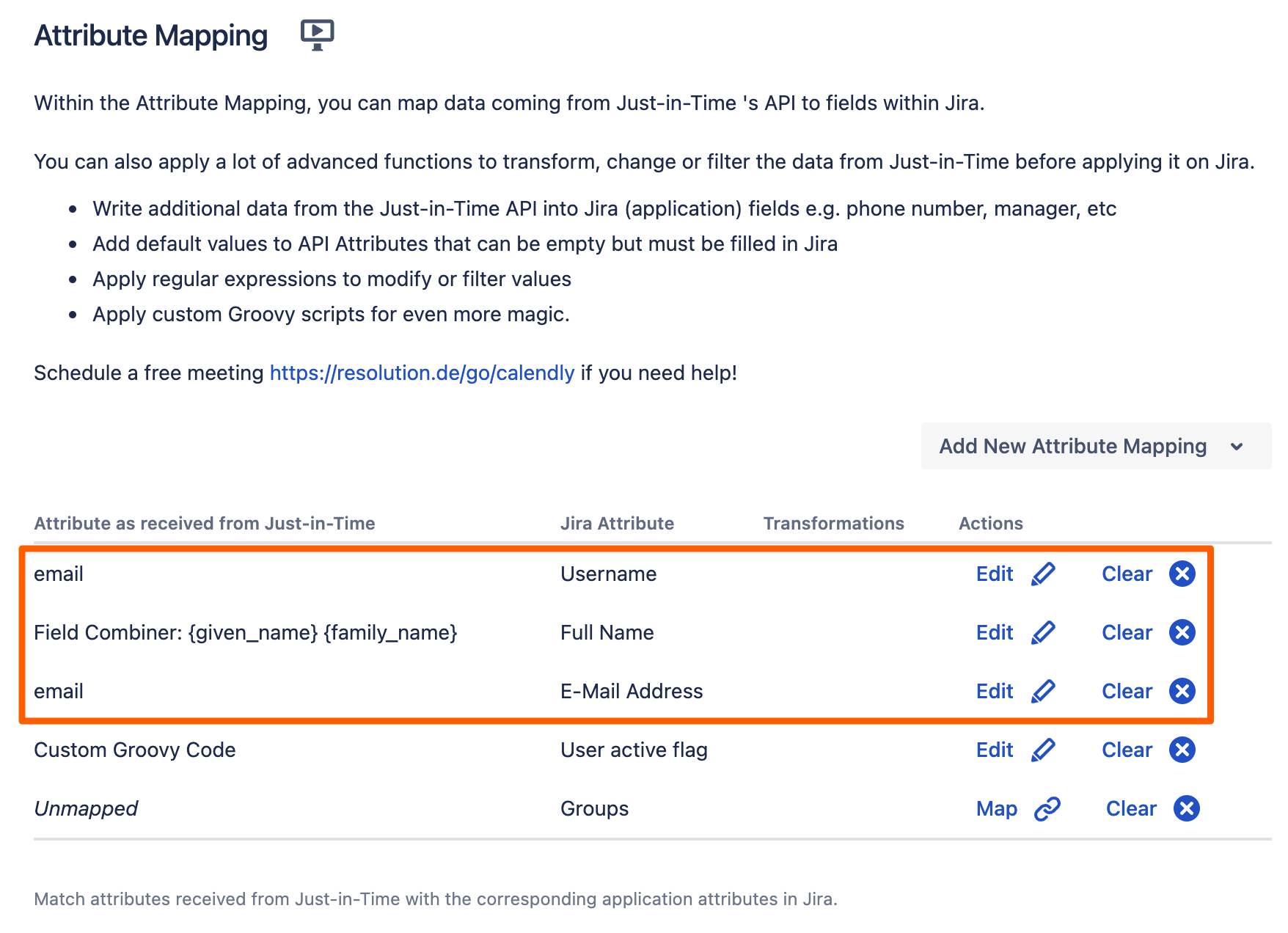
Click Save and Return to finish the configuration.
Next, we need to assign this connector in the OpenID Connect configuration. Go back to the SAML SSO configuration.
Scroll down to the User Creation and Update section. Choose Update with UserSync for the User Update Method.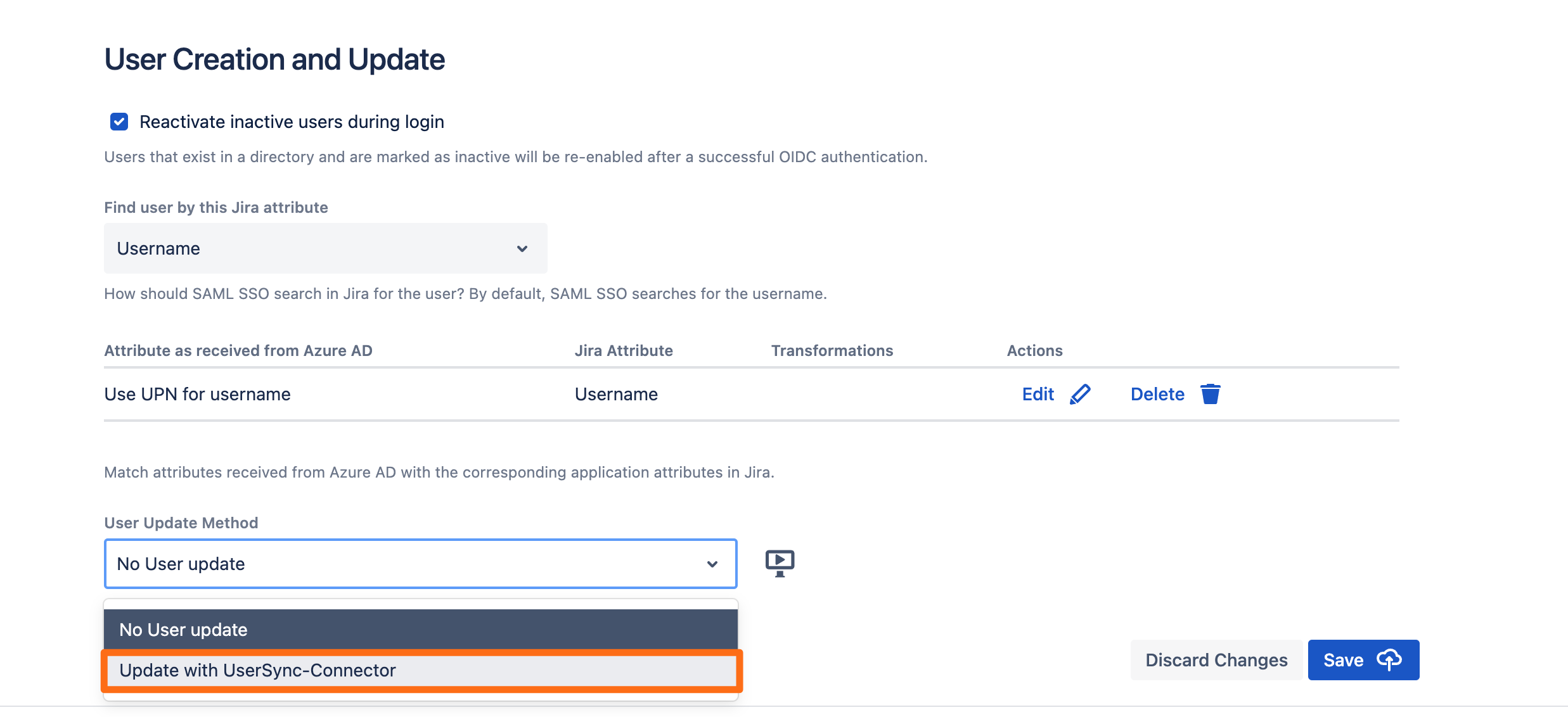
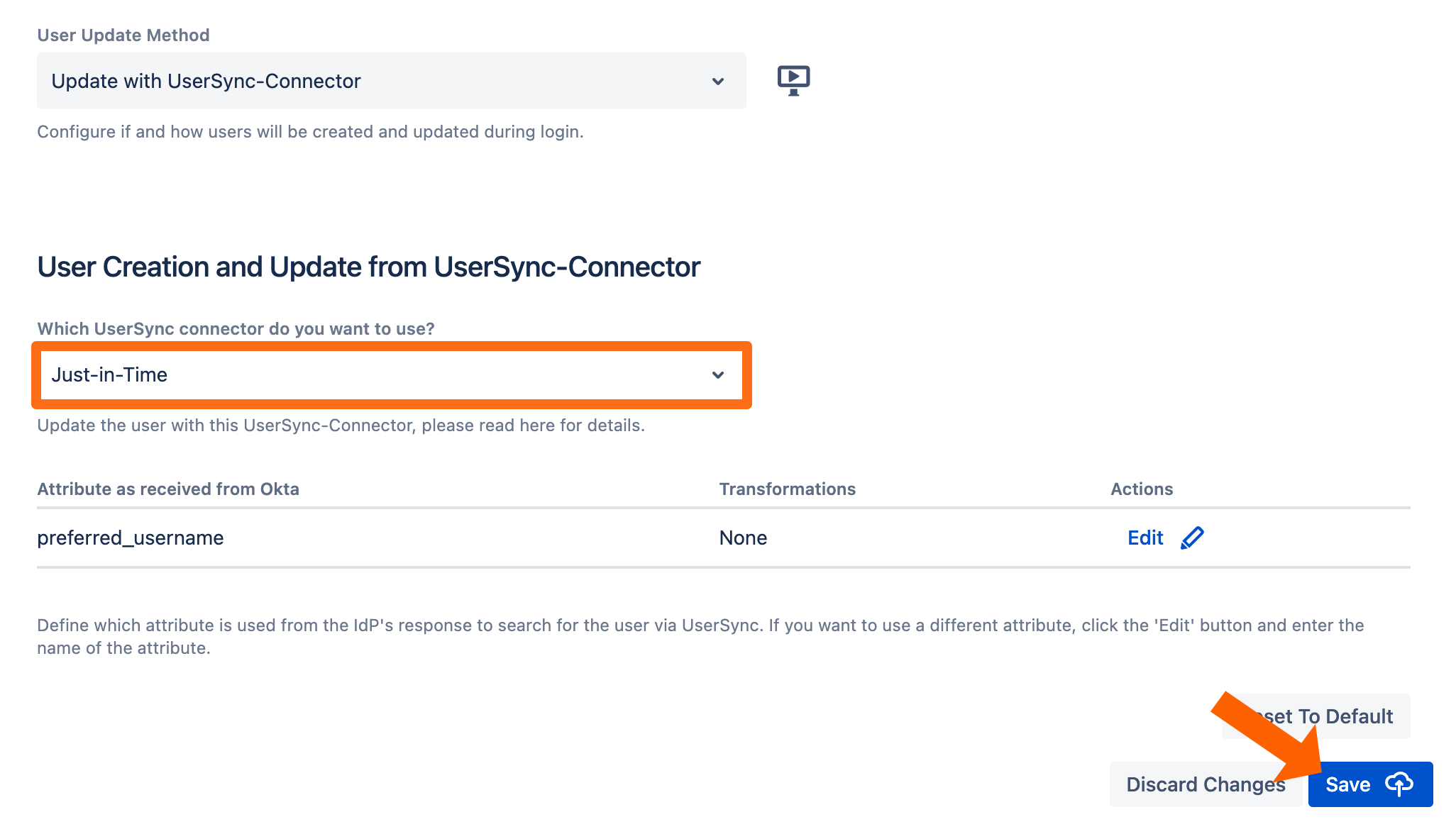
Now, select the Just-In-Time connector that was created before and click Save to finish the configuration.
Testing SSO
To test you configuration, go to the System & Support section of the app and scroll down to the Tracker List.
Click New Tracker. If you have more than one identity provider configured, you must choose which configuration should be used for the log in test.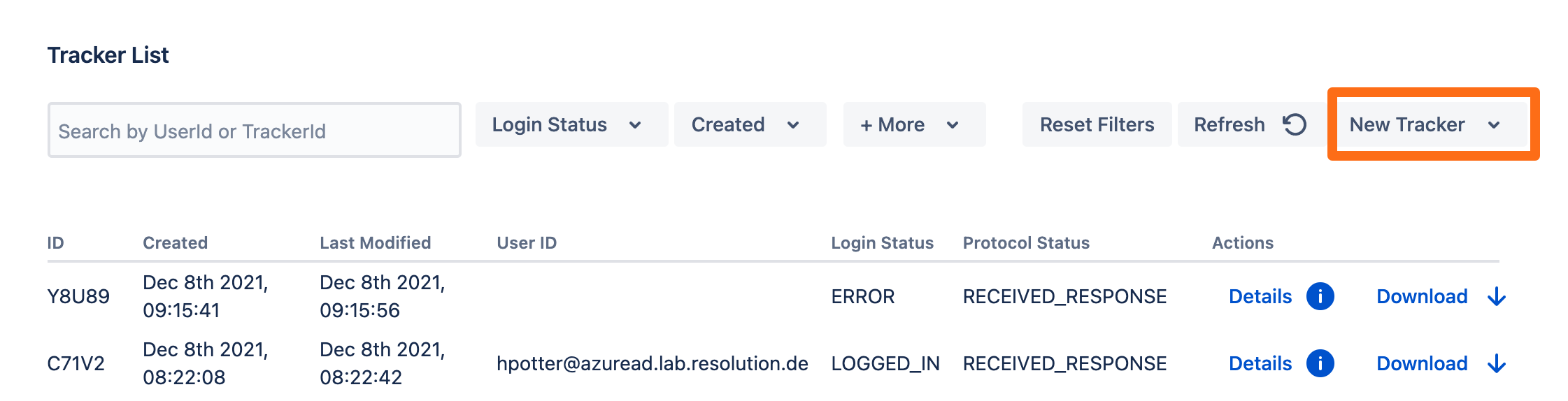
Copy the test url and open the link an incognito web browser. If something goes wrong during the test, you can easily create a support ticket that includes this tracker by click Contact Support. Additionally, you can contact us by going to https://www.resolution.de/go/support or booking a free meeting via https://www.resolution.de/go/calendly.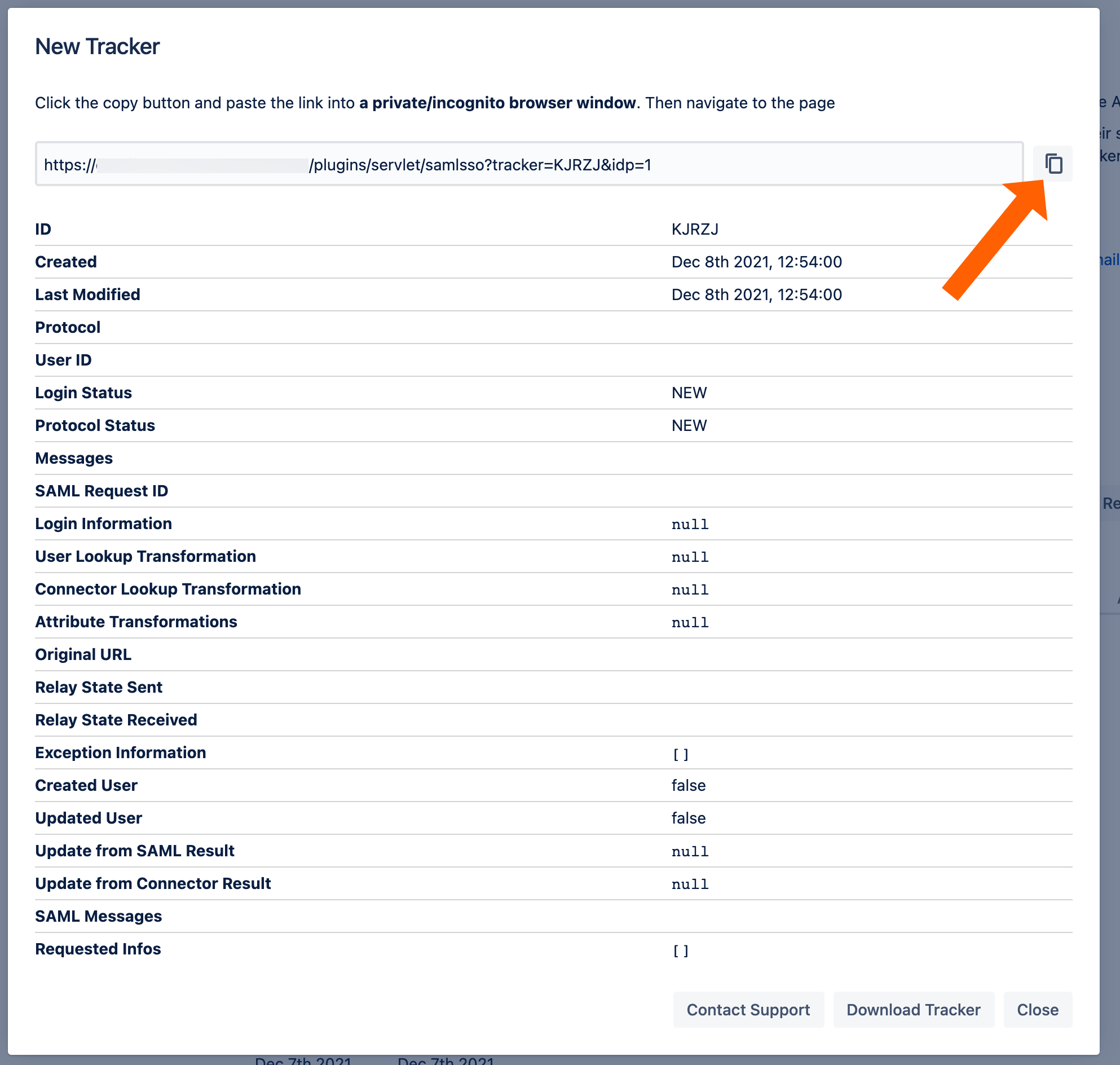
Redirect to SSO
After a successful test, the next step is to configure the redirection. With the redirection setting, the app can automatically redirect users to log in via OpenID Connect.
Go change this setting, go to Redirection from the middle panel.
By checking Enable SSO Redirect, users will get redirected to the configured SSO provider for login. If you are running JSM, you find a second option below.
Click Save to finish the configuration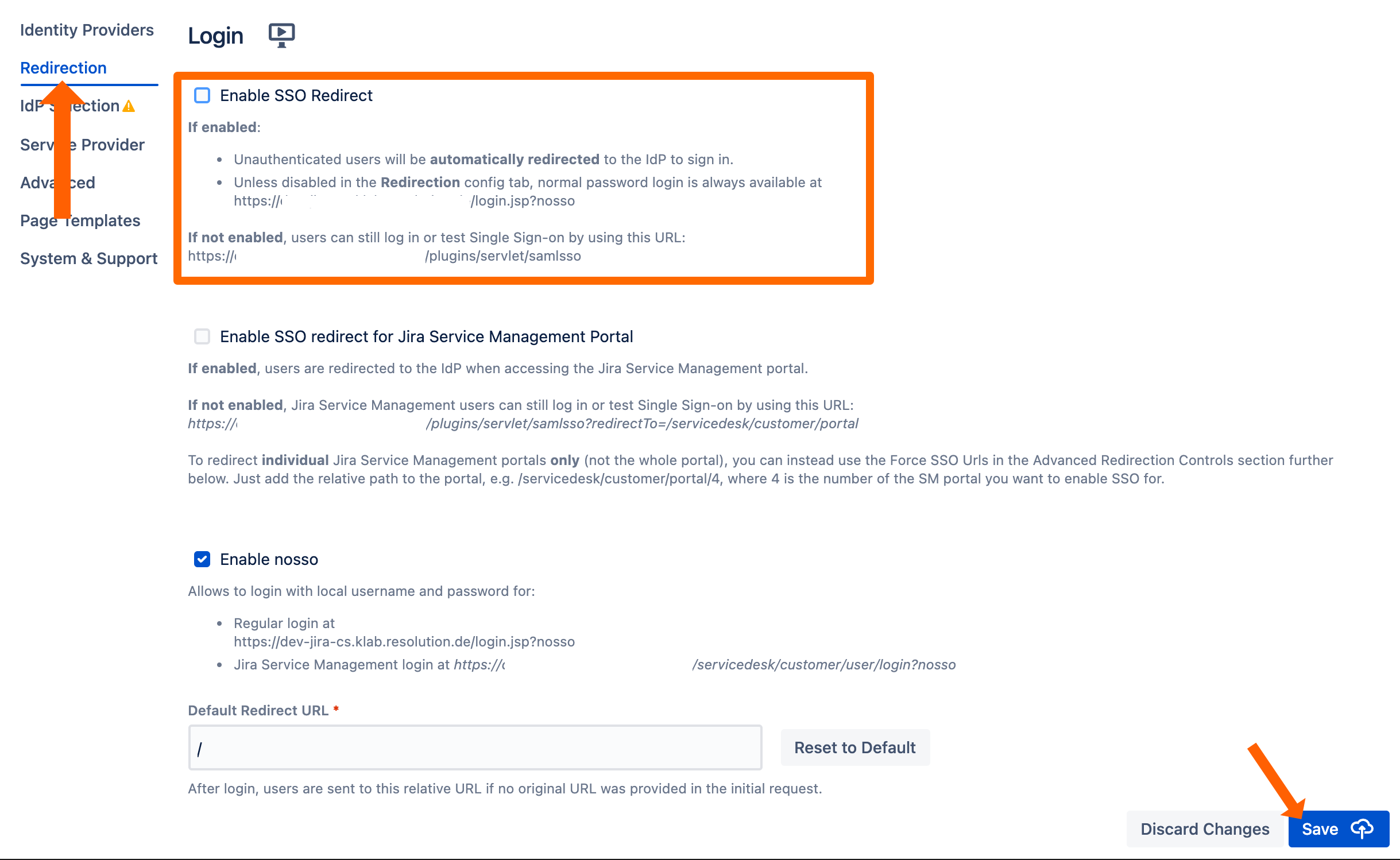
If Enable SSO Redirect is enabled, you can login to your Atlassian application manually by browsing to the URL that fits your Atlassian Data Center application as listed below.
Use this URL, if you need to login a local user unknown to Keycloak or if there are any issues with Single Sign On.
Jira: https://<baseurl>/login.jsp?nosso
Confluence: https://<baseurl>/login.action?nosso
Bitbucket: https://<baseurl>/login?nosso
Bamboo 5: https://<baseurl>/userlogin!default.action?nosso
Bamboo 6: https://<baseurl>/userlogin!doDefault.action?nosso
