Just-in-Time Connector
The Just-in-Time connector in User & Group Sync creates and updates users after a successful authentication into the Atlassian product based.
The connector uses the attributes in the SAML response received from the identity provider
It's similar to the Just-in-Time provisioning method included in the SAML SSO as a user update method.
The User & Group Sync connector includes additional features, particularly regarding group management, that are included below.
Available since SAML Single Sign On 5.2.0 / User & Group Sync 2.2.0.
Prerequisites
SAML Single Sign On >5.2.0 is installed.
Instructions
User Sync Settings
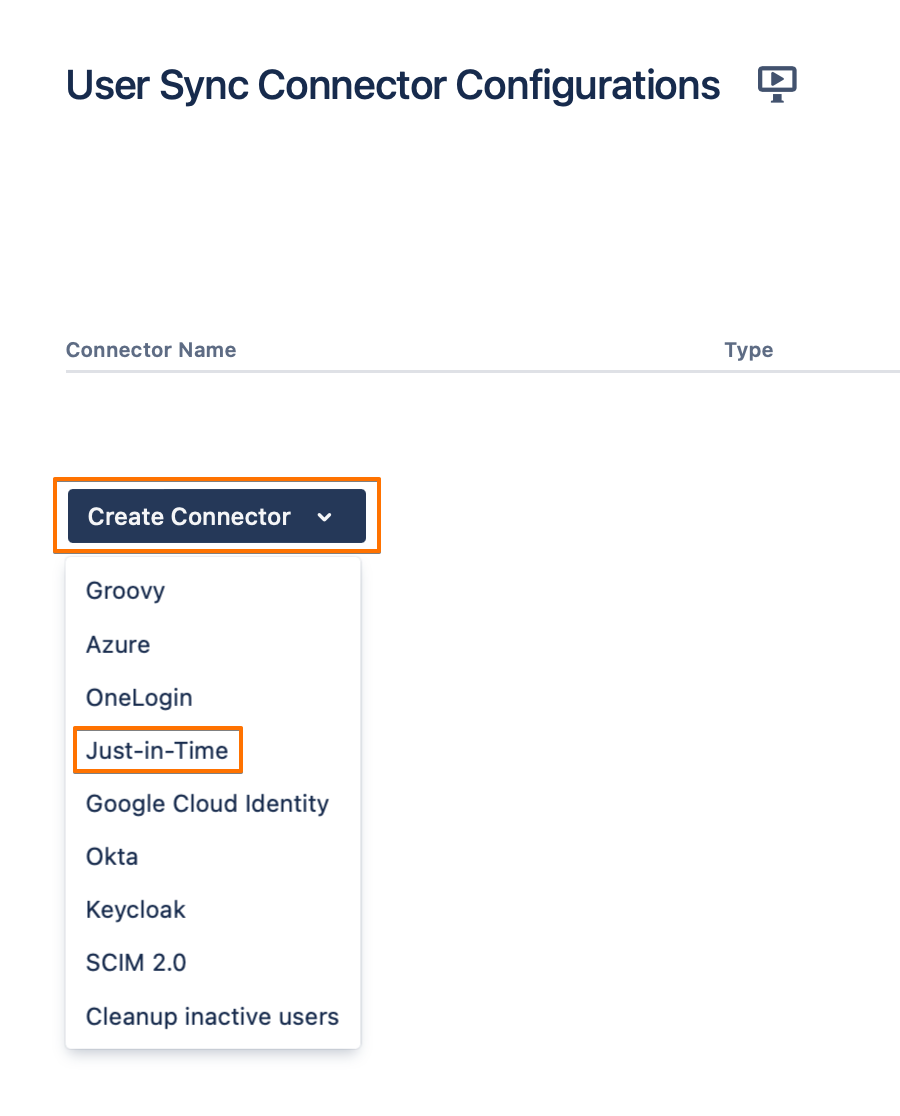
Navigate to the User Sync page.
Click on the Create Connector dropdown list, and choose Just-in-Time.
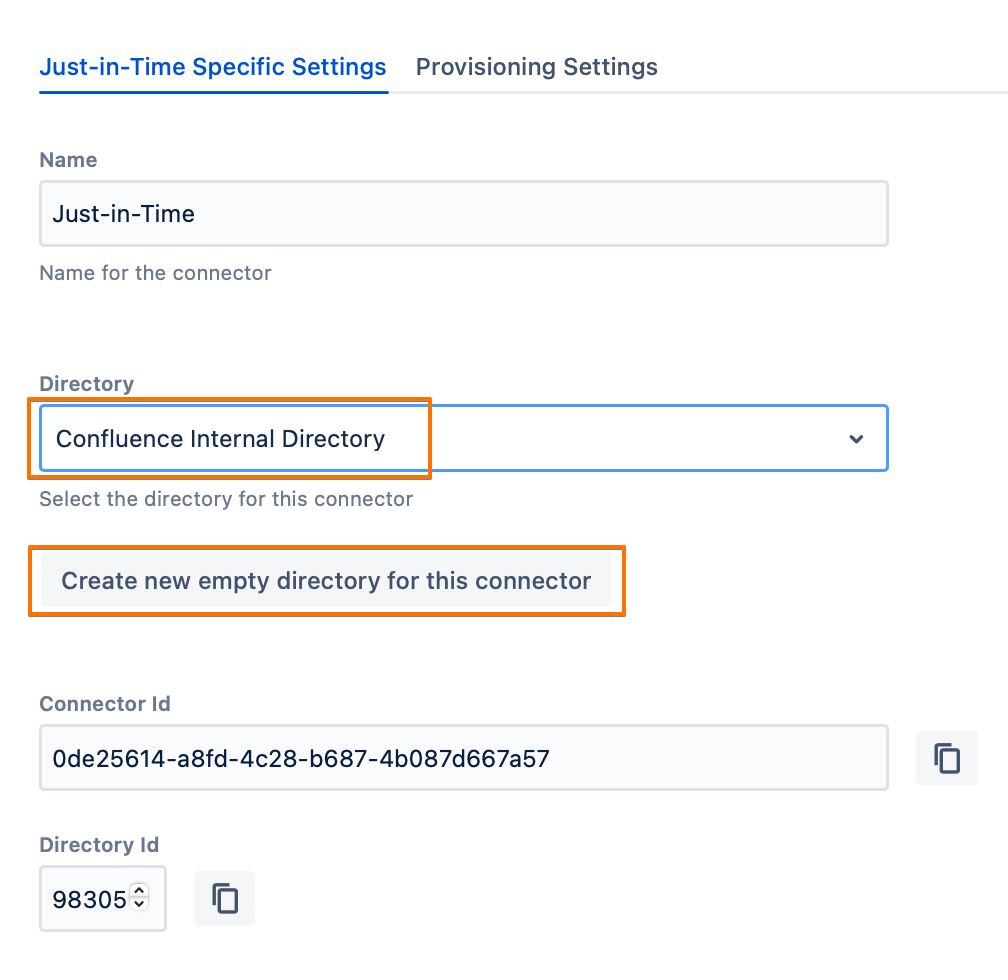
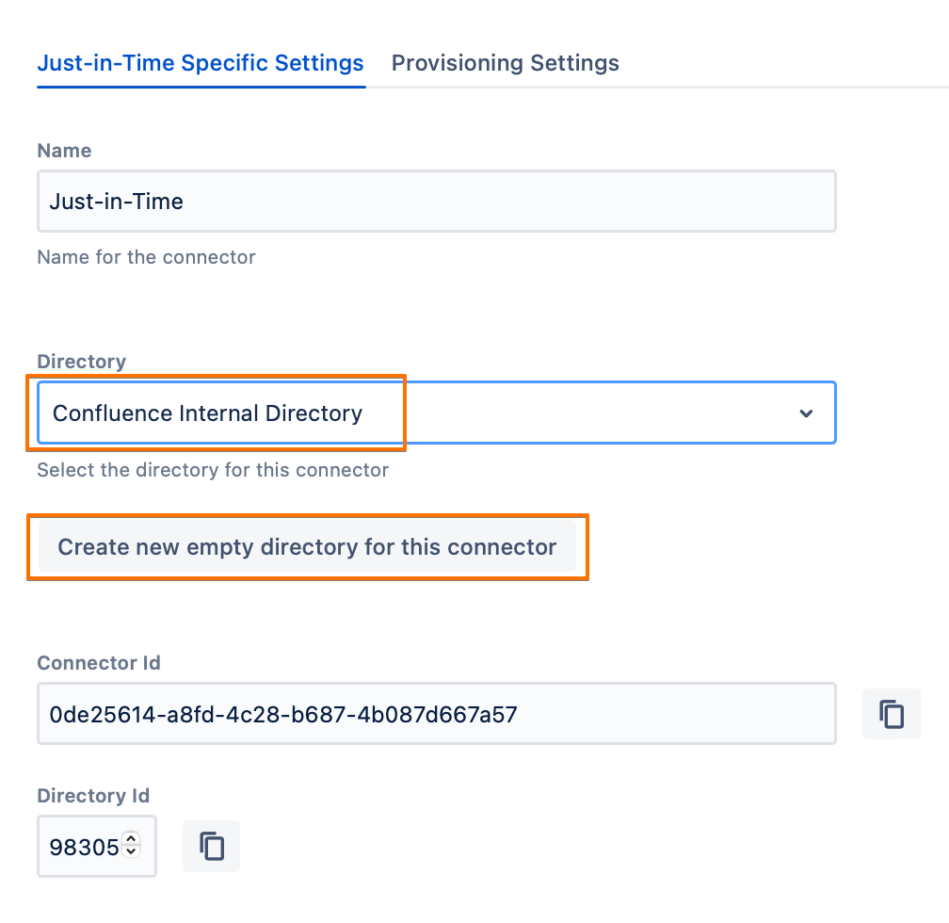
Under the Just-in-Time Specific Settings tab, choose the directory for the user. This can be achieved by either:
selecting an existing directory from the Directory dropdown list,
or creating a new empty directory by clicking on the Create new empty directory for this connector button.
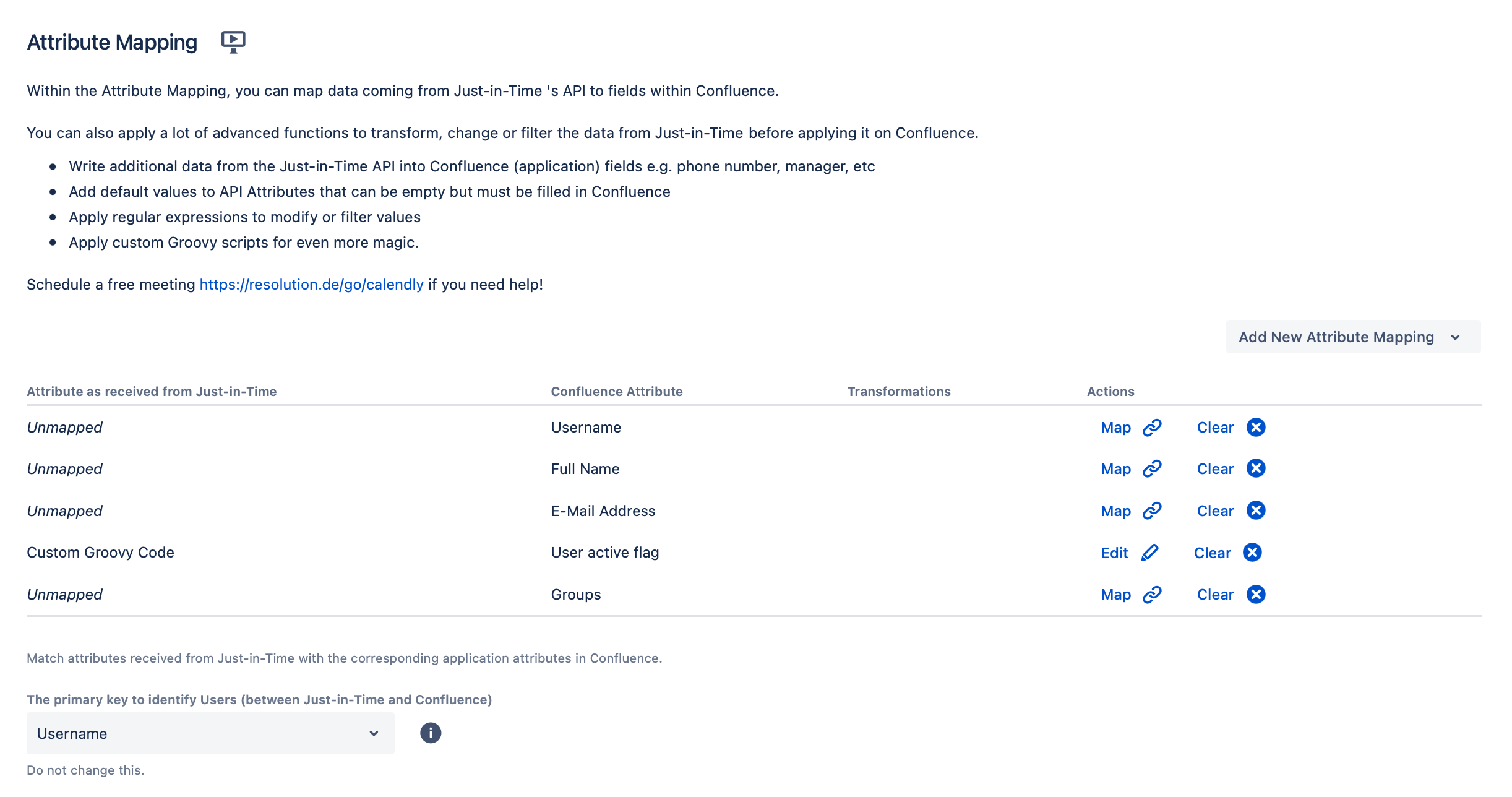
Under the Provisioning Settings tab, navigate to the Attribute Mapping section. Here's where attributes in the Atlassian application must be mapped to the corresponding attributes names from the SAML response.
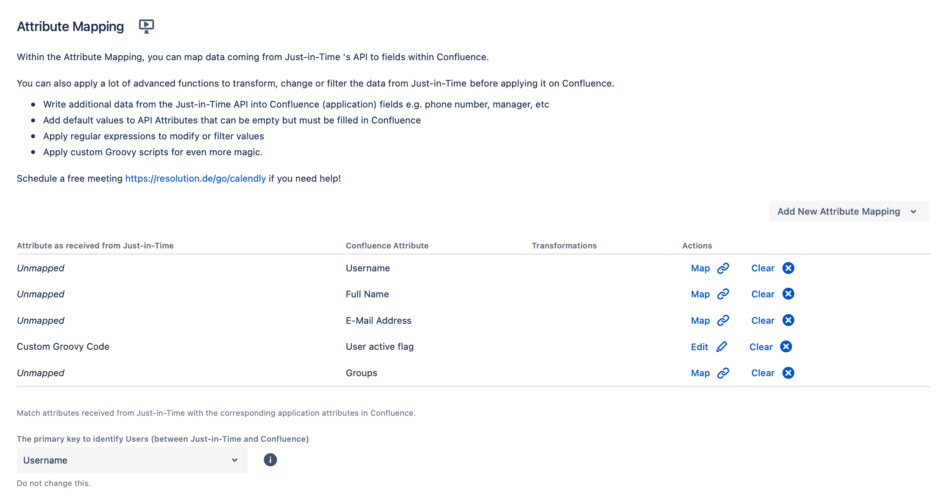
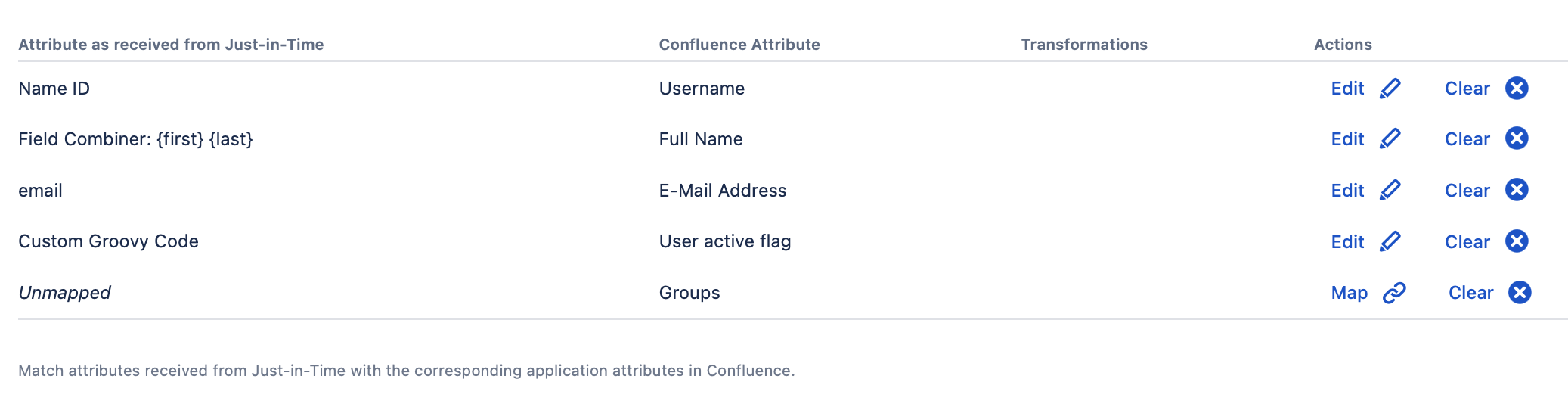
How many attributes to be mapped and what value exactly to be used depends entirely on specific use cases and requirements. Below is an example of mappings, without handling groups.
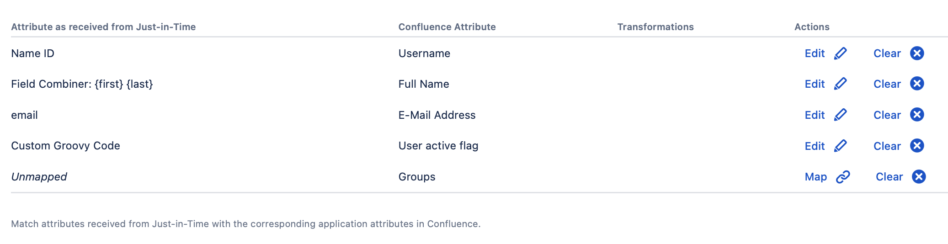
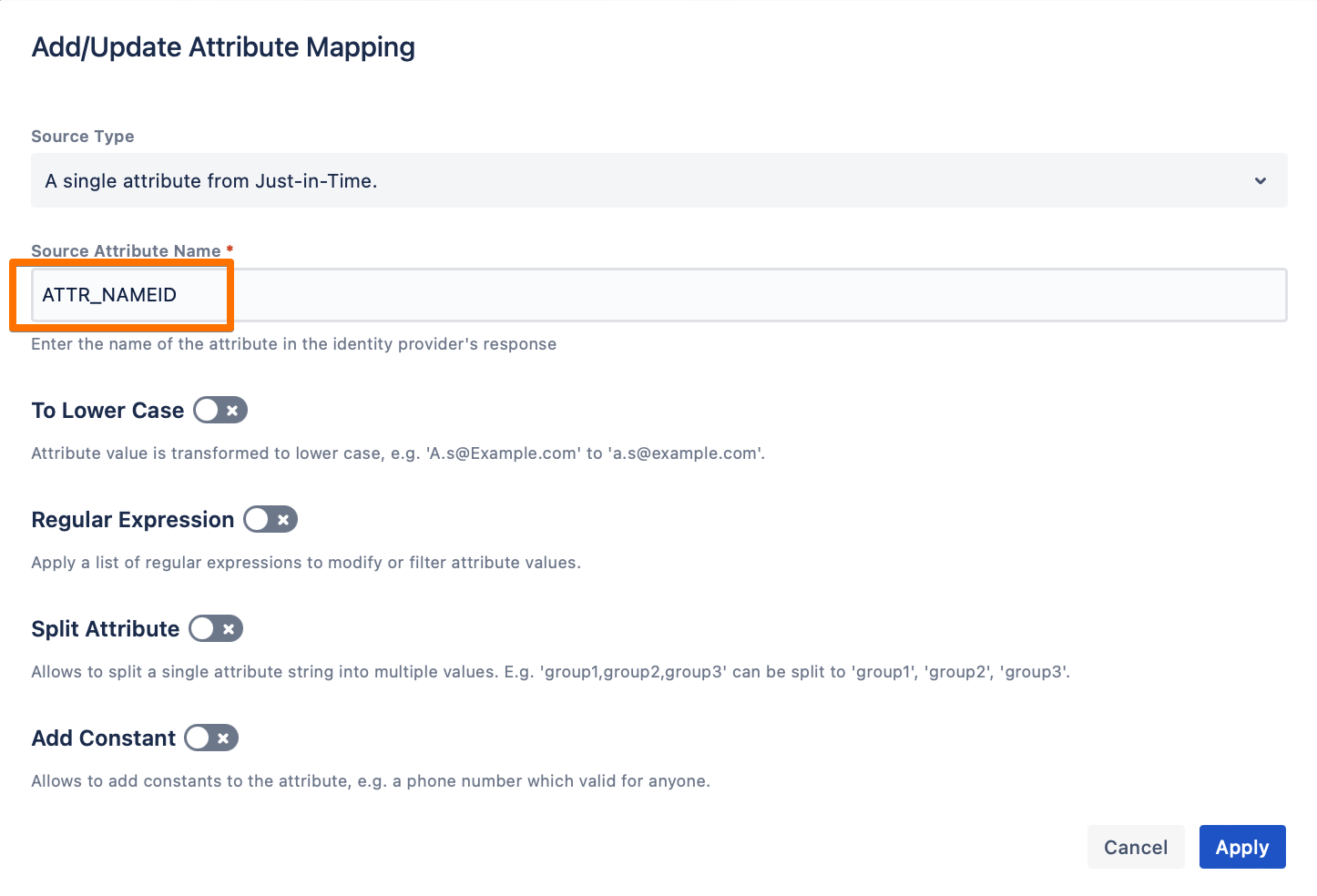
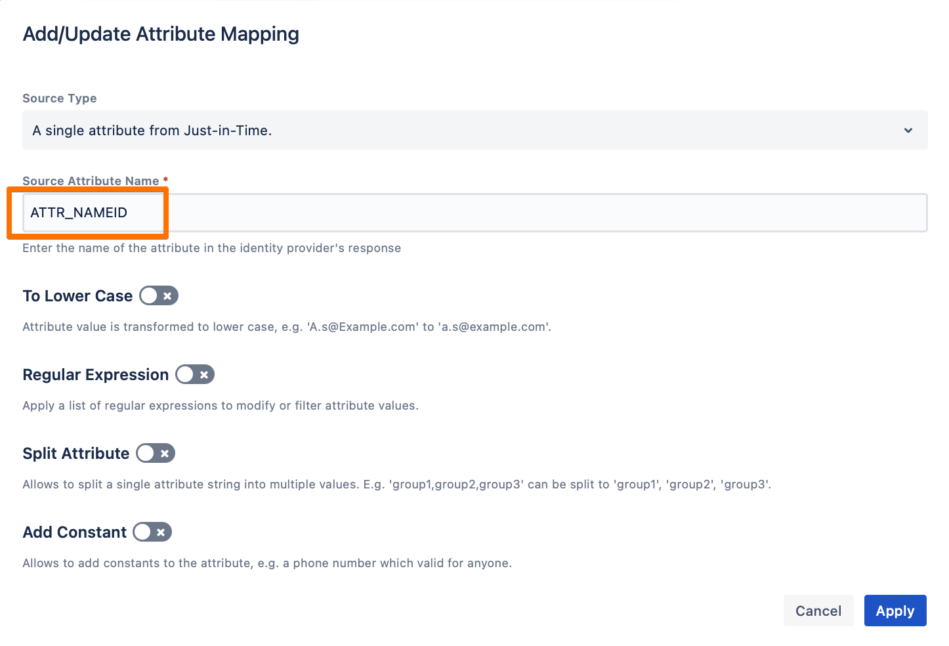
If you’d like to use the nameID attribute that is usually sent by the IdP in the SAML response, use the ATTR_NAMEID attribute mapping. Don't be confused with the display name "Name ID" when you save - this is how the ATTR_NAMEID looks in the UI.
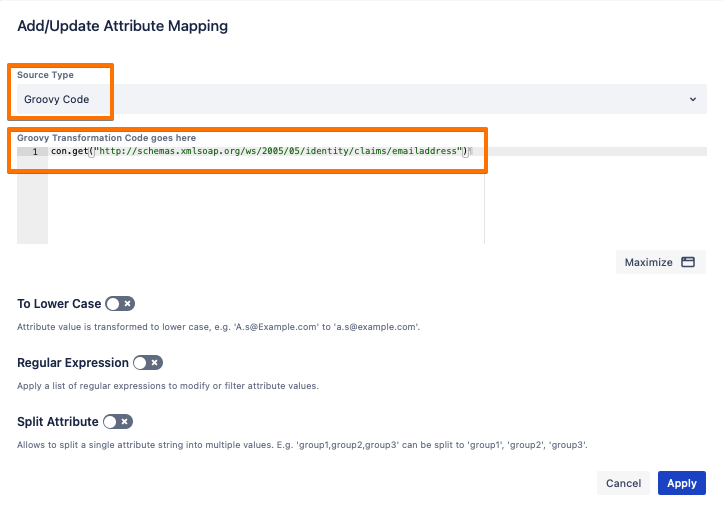
Some IdPs, like AD FS, send the attribute names as URL format, e.g.,
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress. In that case, while mapping the attribute, switch the Source Type from A single attribute from Just-in-Time to Groovy Code, and refer to the IdP SAML attribute like this:- con.get("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress")
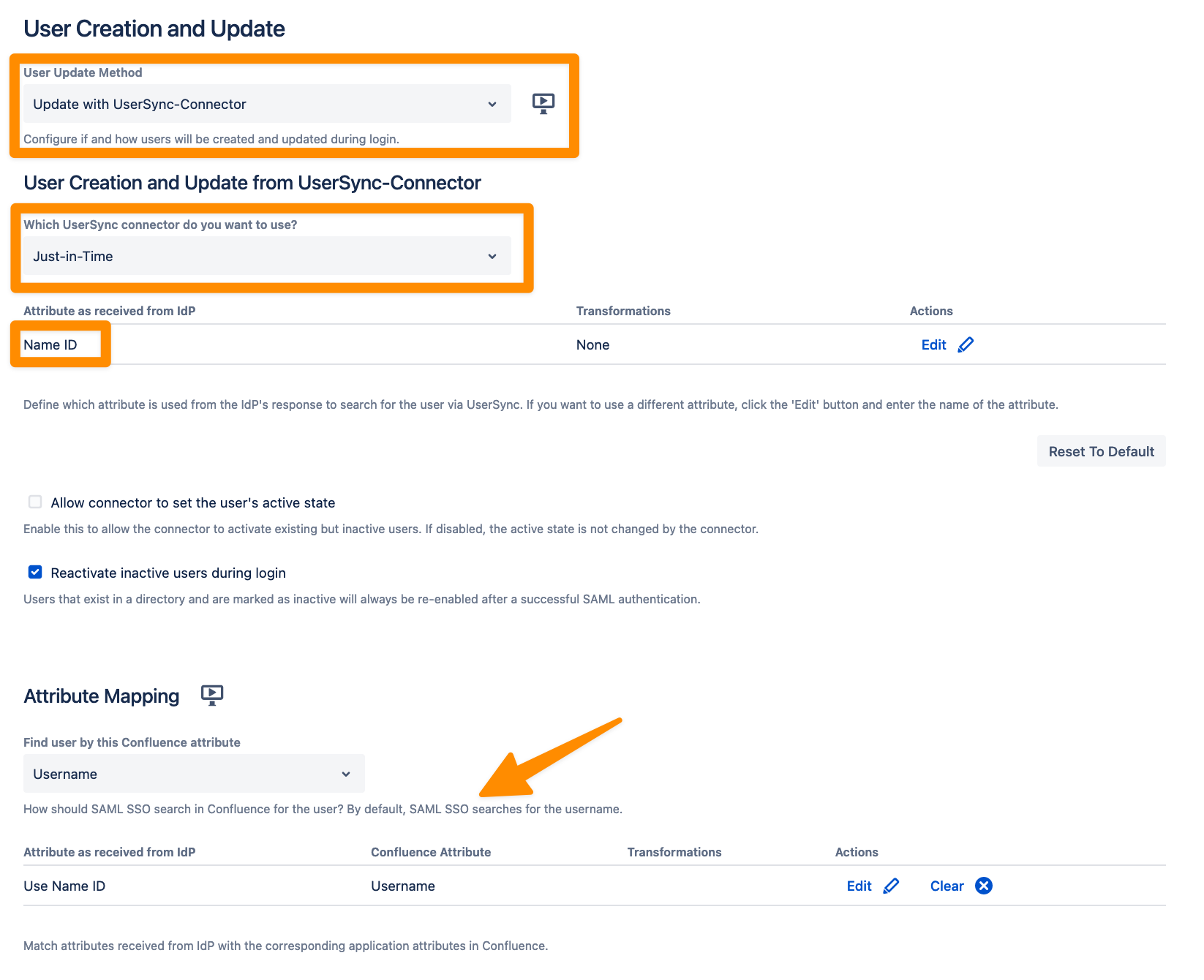
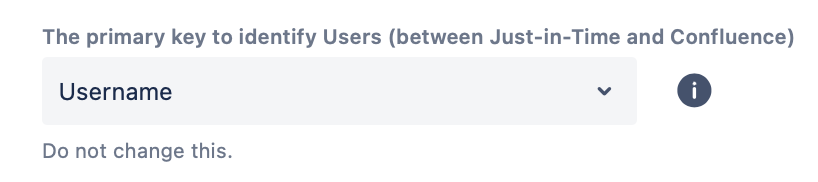
Choose the primary key for UserSync to identify the users with. By default, it’s set to Username.
You can now click on the Save or the Save and Return button to save your settings.
SAML SSO Settings
Navigate to the SAML Single Sign On configuration page.
Under the Identity Providers tab, scroll down to the User Creation and Update section, and select “Update with UserSync-Connector” as a User Update Method.
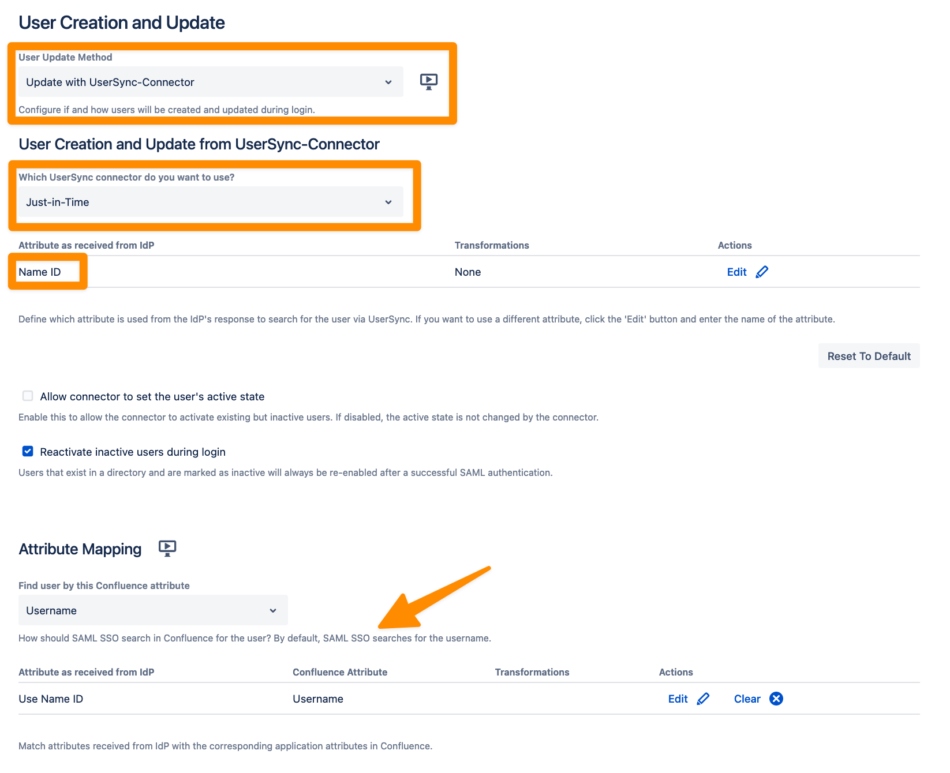
N.B. The attribute in the Attribute as received form IdP section should match the attribute from the Attribute Mapping table.
Click on the Save button to save your configurations.
Group Filtering and Management
Use Cases
Reflect the group assignment based on the group attribute in the SAML response, but also keep selected local groups
The following combination of settings only allows to manage group memberships from the IdP:
The Update from SAML-Attributes (Just-in-Time Provisioning) option in the SAML Single Sign On configuration is being used,
The Remove from Groups option is enabled

In other words, since the group assignment will be done based on what's being returned by the IdP in the SAML response in the group attributes, manual groups additions or removals will be overridden during SSO.
If you also need to retain some local groups, it's recommended to switch over to the JIT connector with User Sync.
Setup
Configure the JIT connector as per the above instructions in this article.
Under the Provisioning Settings tab, scroll down to the Never Remove Users From These Groups, and add the groups names that you would like to retain.
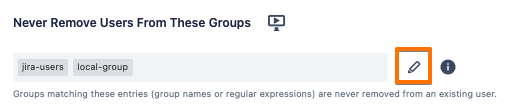
Save the connector settings.
Assign groups only if they already exist in the Atlassian product
Based on the above use case, if you don't want to create new groups that the IdP returns in the SAML response that don't already exist in the Atlassian product, this could also be achieved via the JIT connector. This is equivalent to the SAML Single Sign On configuration option Create groups if they do not exist. 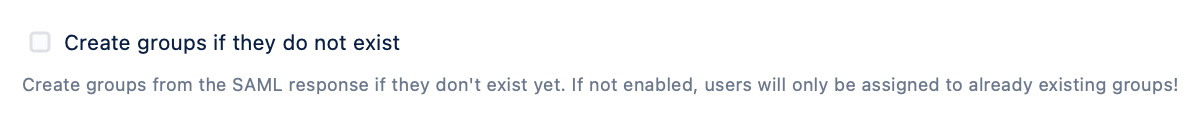
If you are using the JIT connector, then below is how to implement that.
Configure the JIT connector as per the above instructions in this article.
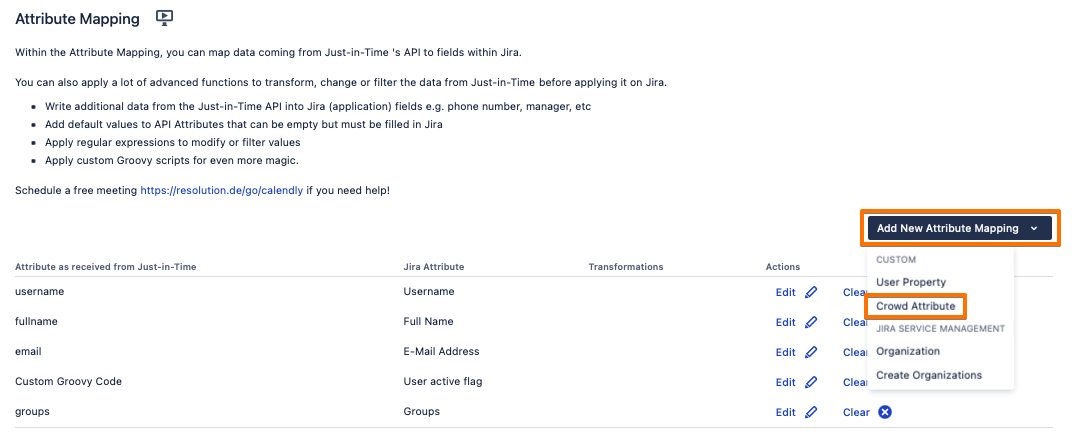
Under the Provisioning Settings tab, scroll down to the Attribute Mapping section, click on the Add New Attribute Mapping button, and choose Crowd Attribute.
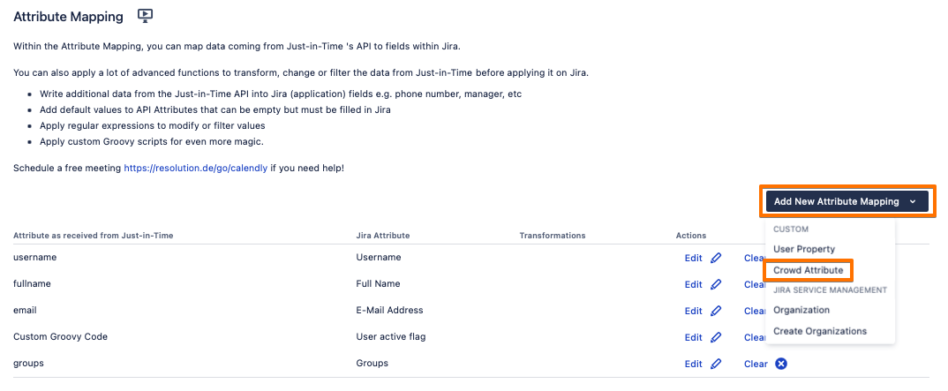
Enter
ATTR_IS_CREATE_GROUPSas a Crowd Attribute Name, and click on Next.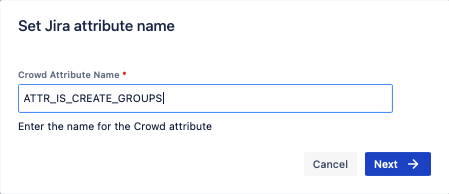
Change the Source Type to Groovy Code, write
falsein the Code field, then click on Apply.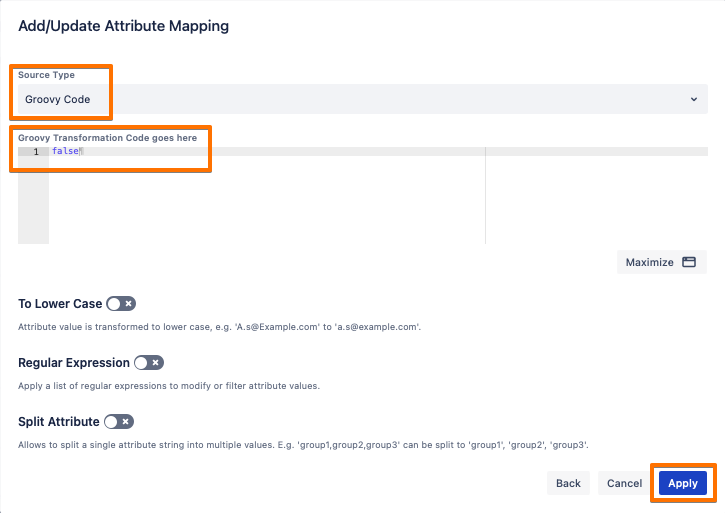
Save the connector settings.
Manage ALL groups (including administrator groups) totally from the IdP side
As you could read in the SAML Single Sign On configuration, the Remove from Groups option doesn't apply to groups that give administrative permissions. That was intended to protect admin revocations by mistake which might lead to losing admin access to the instance.
However, if you really need that to be applied to administrators, then you can implement the JIT connector setup, since it doesn't have the above restriction.