User Creation and Update with UserSync-Connector
Please contact our Support if you have questions about this functionality.
Introduction
Our SAML Single Sign On apps for Atlassian Data Center can also use User Sync to automatically create and update users on the first Single Sign On login, or update them on all subsequent logins. For the creation or update process, the user information is taken from the attribute mapping configured in the User Sync plugin and a Sync Single User Update is triggered, fetching data from the Identity Provider. User Sync is already bundled with our SSO app.
Optional
The update method Update with UserSync-Connector and apply SAML attributes combines information received via User Sync (first) and enriches/ adds/ overwrites it with information from the SAML response (second).
There is usually no need to do that unless there is some data that is only available in the SAML response but not via the API of the identity provider we are using for User Sync.
Prerequisites
You need a User Sync Connector that is already configured and working (successful sync for the users who should log in).
SAML Provisioning Configurations
Update with UserSync-Connector
Go to the configuration page of our SAML SSO app and switch to its Identity Providers tab
Scroll down to the section User Creation and Update
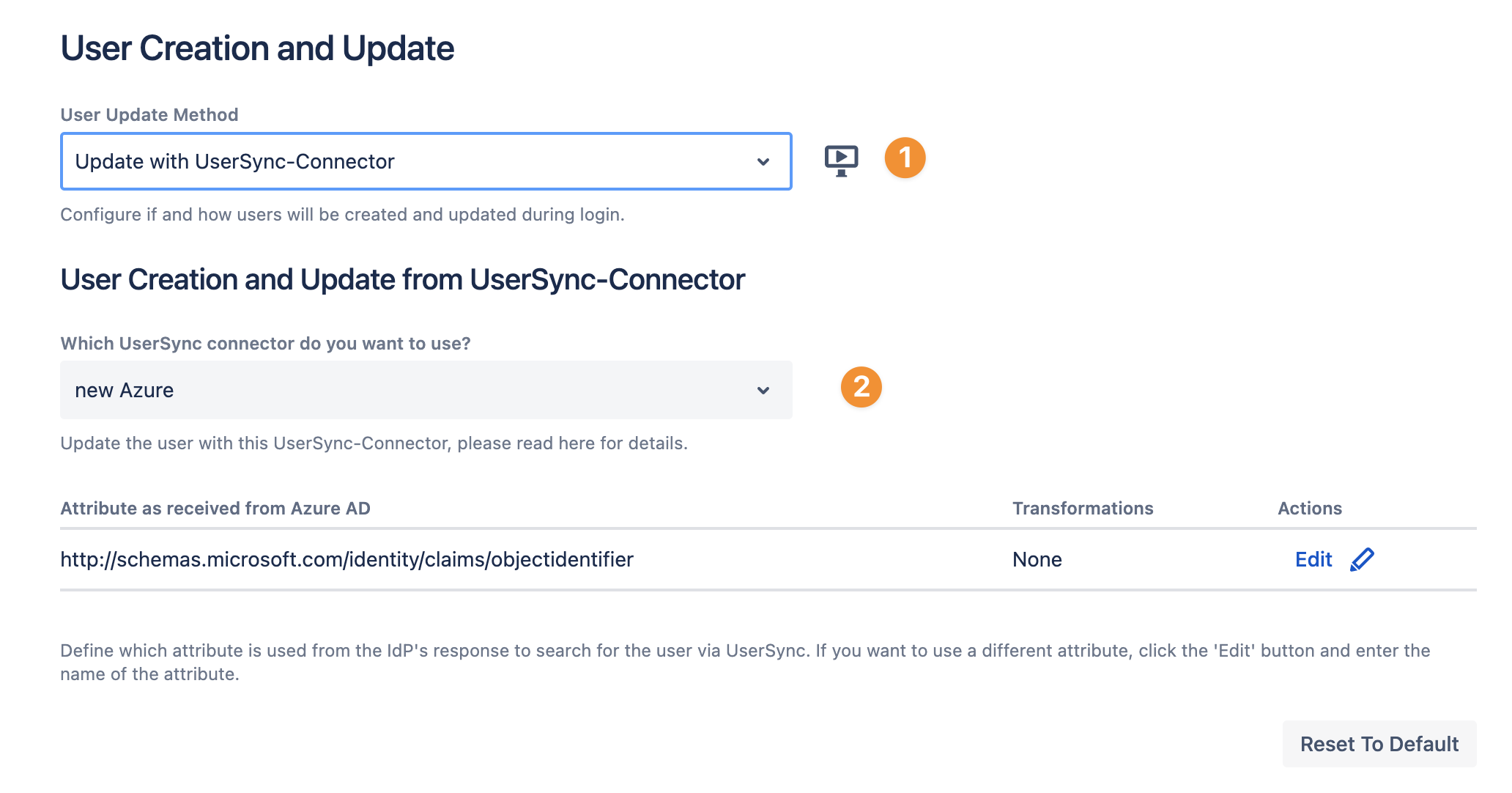
As User Update Method, use Update with UserSync-Connector
Select the User Sync connector you want to use to update the user
If needed, you can change the attribute which is used from the IdP's response to search for the user via User Sync.
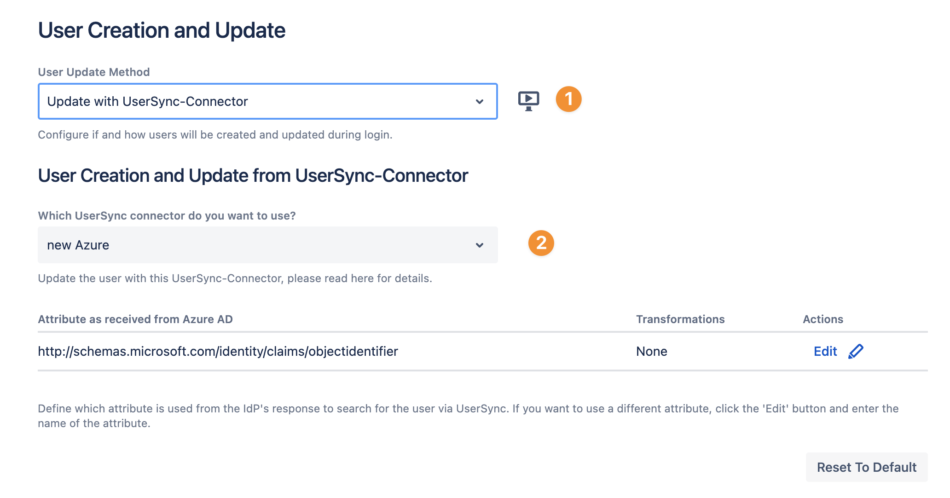
Next to the User Update Method and User Sync connector, you can configure two options
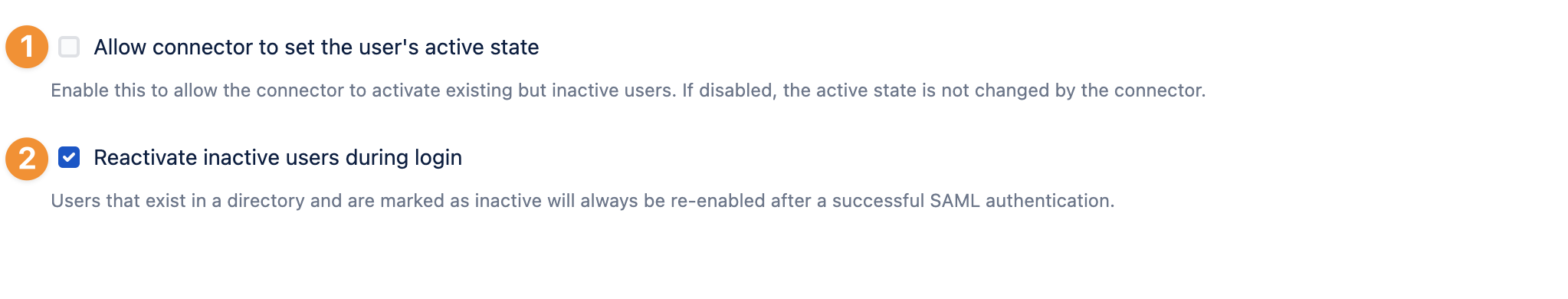
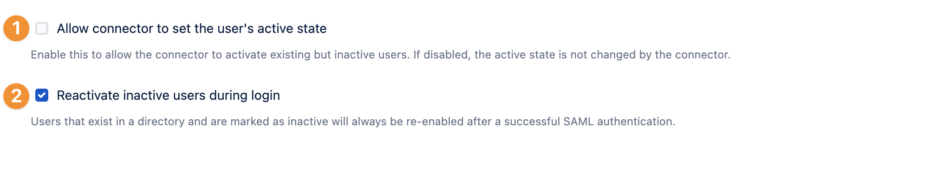
Allow connector to set the user's active state
If users were returned (removed and added again) to the required group (on the IdP side), User Sync is not activating users again when they return to the required group. Toggle this option to change the active state by the User Sync Connector.
The option to Reactivate inactive users during login will re-enable users (after a successful SAML authentication) if they exist in a directory and are marked as inactive.
 options_us_usercreationandupdate
options_us_usercreationandupdate
Save the configurations
Perform a Single Sign On and check if the user is correctly created/ updated
Update with UserSync-Connector and apply SAML attributes
Go to the configuration page of our SAML SSO app and switch to its Identity Providers tab
Scroll down to the section User Creation and Update
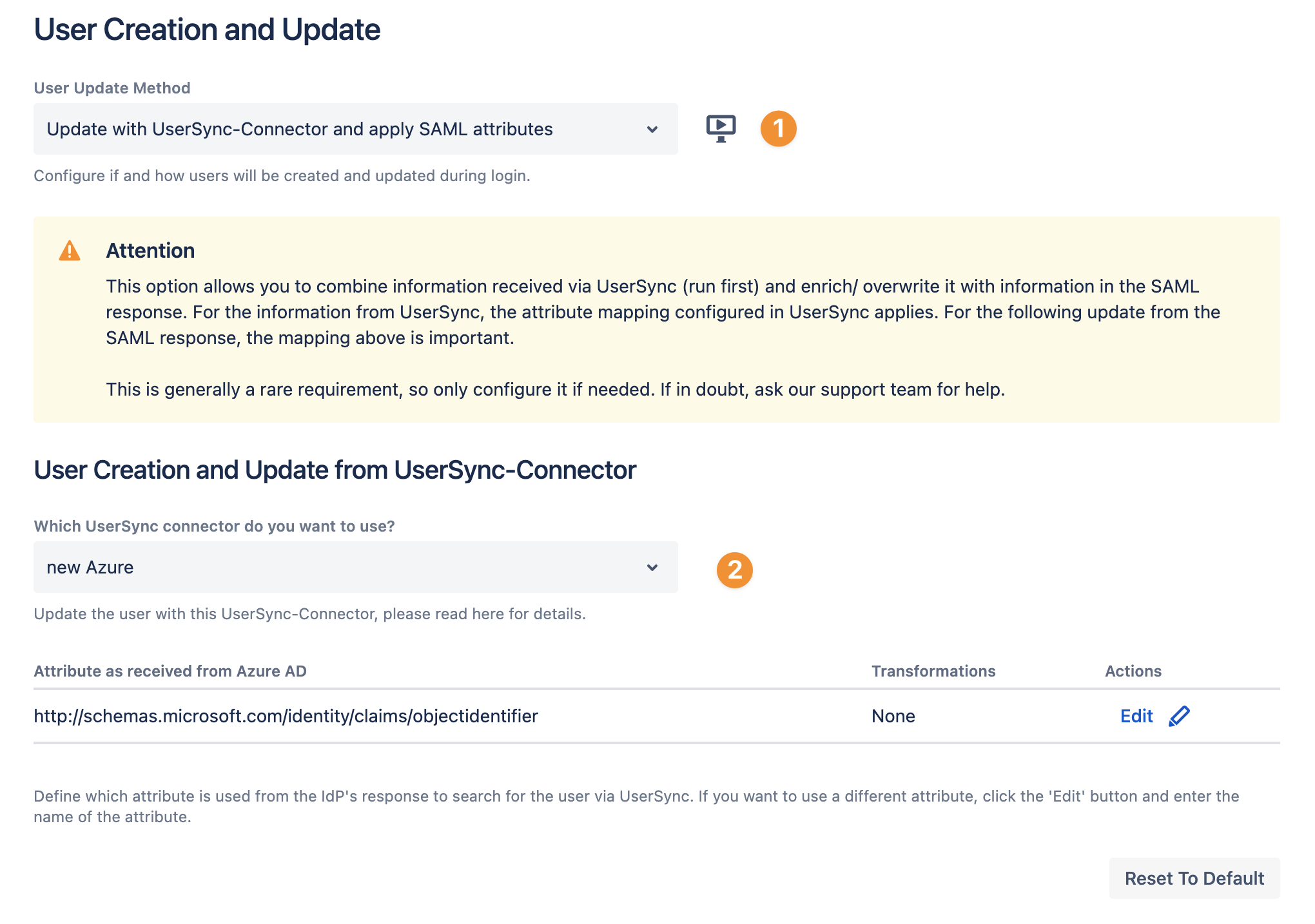
As User Update Method, use Update with UserSync-Connector and apply SAML attributes
Select the User Sync connector you want to use to update the user
If required, you can change the attribute which is used from the IdP's response to search for the user via User Sync.
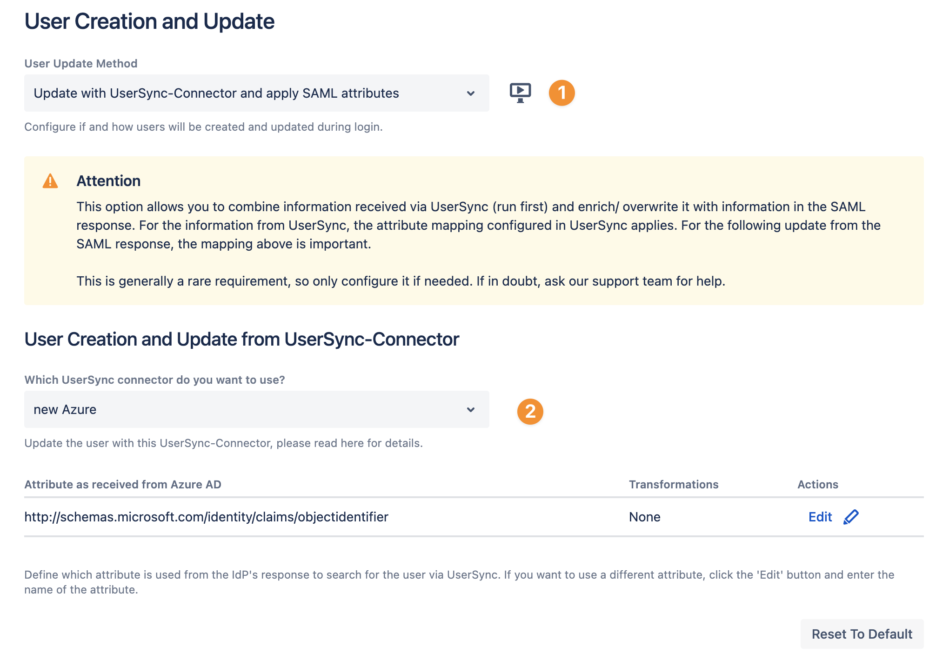 us_samlandus
us_samlandus
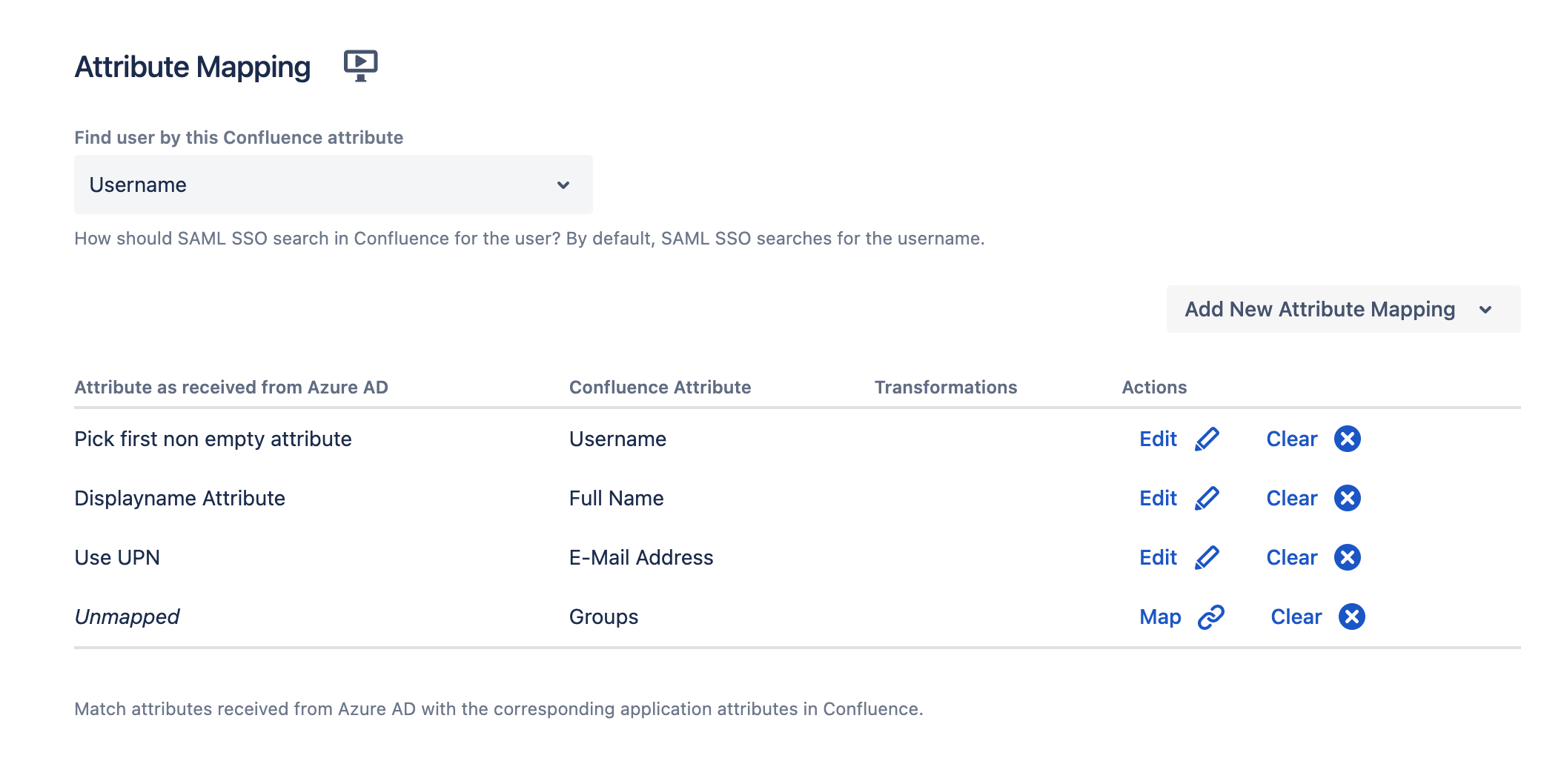
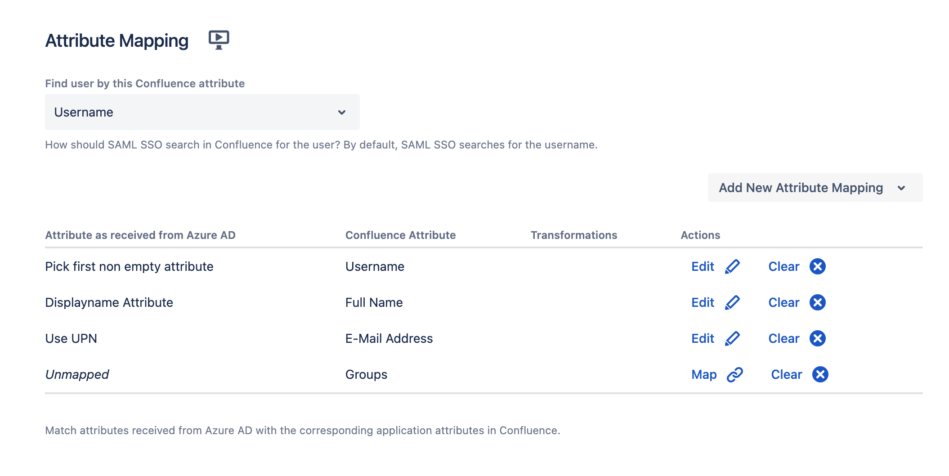
Enter or select the SAML attributes delivered by the identity provider for Username (ID), Full Name, E-Mail Address, and Groups or other attributes you might need
Next to the User Update Method and User Sync connector, you can configure two options
Allow connector to set the user's active state
If users were removed and later added again to the required group on the identity provide, User Sync is not activating them again by default. Enabling this option will cause User Sync to activate the user again.
The option Reactivate inactive users during login will activate users again after a successful SAML authentication
 options_us_usercreationandupdate
options_us_usercreationandupdate
Save the configuration
Perform a Single Sign On and check if the user is correctly created or updated