Update existing User and Remove from Groups
Starting with SAML Single Sign On for JIRA/Confluence 0.14.2, we've further refined the functionality around user and group membership provisioning.
Based on customer feedback, the following has been added or changed:
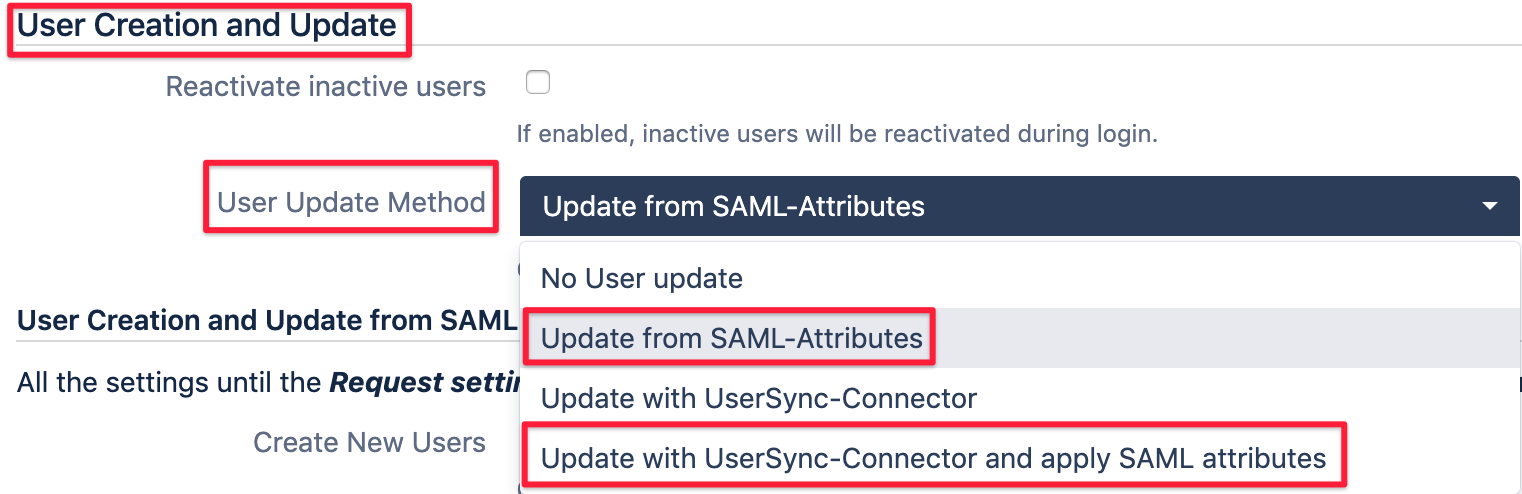
The options mentioned here are only shown, if User Update method in User Creation and Update are set to
Update from SAML-Attributes or Update with UserSync-Connector and apply SAML attributes (if using User Sync in combination with our app)
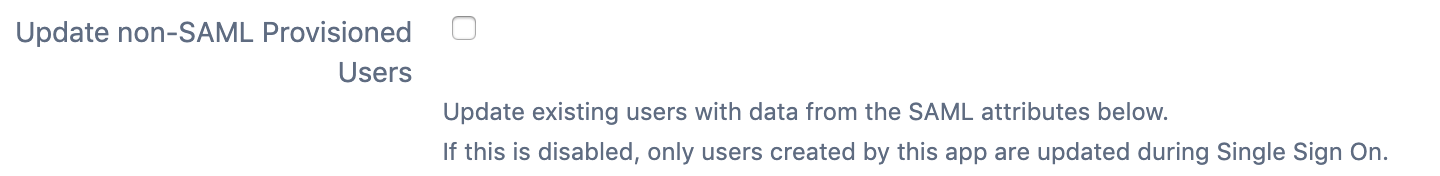
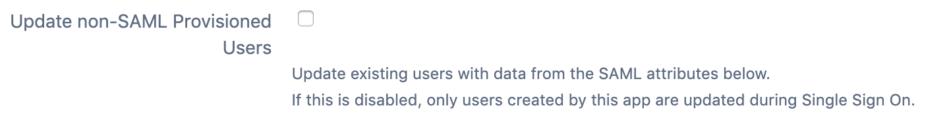
Update non-SAML Provisioned Users: if checked, existing local users, that were not created by the SAML SSO app, can be updated now as well
Remove from groups: if checked, users are being removed from groups not sent in the SAML attributes or manually provided in "User Groups"
in "User Creation and Update from SAML Attributes"/ "Group Settings" section of the SAML SSO app configuration (the groups provided have to exist)
Even with "Update non-SAML Provisioned Users" checked, users won't be removed from groups, unless they've been created by the SAML SSO app.
Should you want to convert existing users to SAML SSO users, you can use the SAML SSO toolbox (more details here).
https://wiki.resolution.de/doc/saml-sso/latest/all/troubleshooting/saml-sso-toolbox#SAMLSSOToolbox-Manipulatingusers describes how to do this.
Please be aware that admin * users are excluded from that operation, for safety reasons and to prevent users locking themselves out.
It is always best practice to leave one ore more admin users in the internal directory, not managed on the identity provider via SAML SSO.
* admin users are identified by using the Atlassian API functions "isAdmin" or "isSysAdmin"
Should you really need to convert admin users to SAML users, the only workaround is to temporarily revoke administrative access,
converting them to SAML users with the toolbox and assign administrative permissions back to the users.
As the SAML toolbox UI only allows manual conversion user by user, you can also the REST API endpoint of the toolbox to perform a bulk conversion:
- PUT - https://<jira-baseurl>/rest/samlsso-toolbox/1.0/converttosamluser - Returns "202 Accepted" as response and starts the conversion process
- GET - https://<jira-baseurl>/rest/samlsso-toolbox/1.0/converttosamluser - Shows the current conversion status, return code 200 if there is a valid status, 404 if a conversion never happened before
- DELETE - https://<jira-baseurl>/rest/samlsso-toolbox/1.0/converttosamluser - Stops a conversion process
Make sure you are running these commands with curl, especially the GET will only then return the above status codes.
Below some examples:
- curl -u admin:adminpassword -D- -X PUT https://<jira-baseurl>/rest/samlsso-toolbox/1.0/converttosamluser # starts the conversion process
- curl -u admin:adminpassword -D- -X GET https://<jira-baseurl>/rest/samlsso-toolbox/1.0/converttosamluser # get the conversion status
- curl -u admin:adminpassword -D- -X DELETE https://<jira-baseurl>/rest/samlsso-toolbox/1.0/converttosamluser # stops it