Alternate AssertionConsumerServiceURL in SAML-Request
Starting with version 2.2.0, the AssertionConsumerServiceUrl in the SAML request can be derived from the URL the initial request was made to. This allows the use of SSO in systems which are accessed through different base URLs.
Please be aware of these limitations:
The Atlassian Server or Data Center applications should always accessed using the configured base URL. Even if this is working in most cases, it is not supported (see https://confluence.atlassian.com/adminjiraserver/configuring-the-base-url-938847830.html or https://confluence.atlassian.com/doc/configuring-the-server-base-url-148592.html)
In Atlassian Data Center environments, only the configured base URL will work
The alternate URLs are not included in the Metadata, so they need to be added to the IdP manually
Please verify that your IdP supports this configuration. You may have to add the second SSO URLs to the Service Provider Setting on your IdP. Depending on your IdP the step is sometimes called “add multiple requestable SSO URLs” or “Allow this app to request other SSO URLs”, “multiple Reply-Urls”.
Since the URL is derived from the host header, this may allow for a host header injection. Please see https://wiki.resolution.de/x/b4VMC
There will also be potential Issues with URLs in E-Mail notifications for example.
Also note that you may have to do other re-writes on your reverse proxy to make other Confluence / Jira functions work, that have nothing to do with our SAML Single Sign On Plugin as such. Unfortunately, we don’t know of a good guide that lists all of those
To enable a Confluence or Jira running under two (or more) different URLs at the same time you have to enable Use Base URL from Request in the Request Settings section on the Identity Providers settings tab: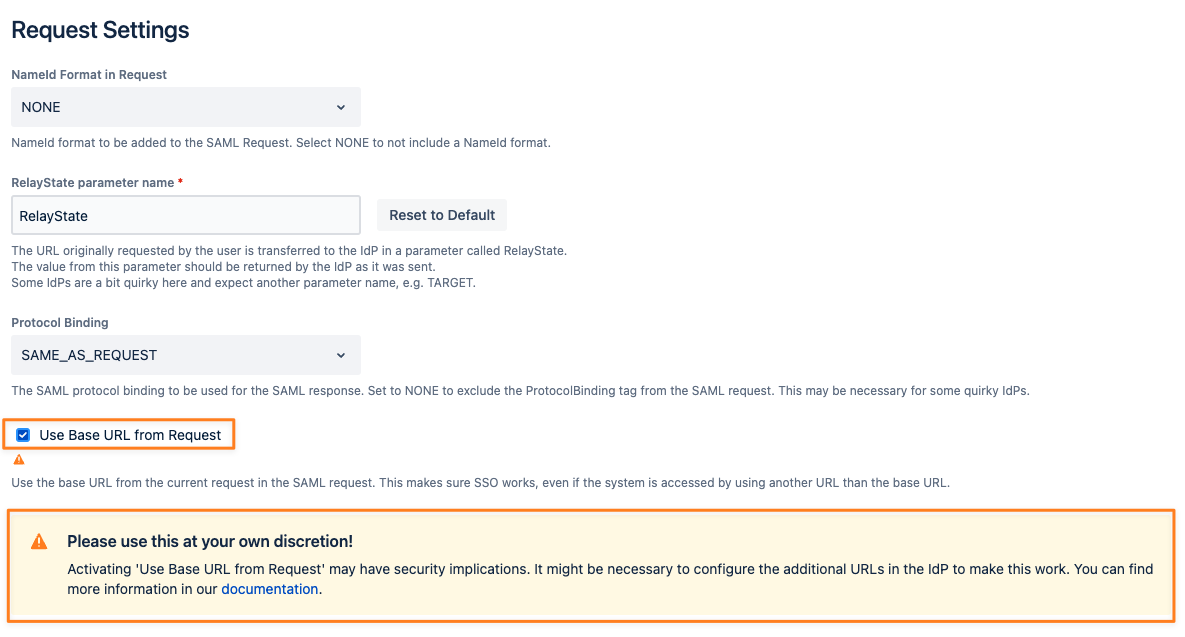
Example with Jira Server or Data Center:
A Jira instance with the base URL https://jira.internal.example.com is also available at https://jira.external.example.com. A SAML-Request usually looks like this:
- <?xml version="1.0" encoding="UTF-8"?>
- <saml2p:AuthnRequest
- xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol" AssertionConsumerServiceURL="https://jira.internal.example.com/plugins/servlet/samlsso" Destination="https://someidp.example.com" ID="_b655e6b787907cb93fb98344e0560c3f" IssueInstant="2018-05-07T08:45:24.563Z" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Version="2.0">
- [...]
- </saml2p:AuthnRequest>
If you enable Use Base URL from Request and access the system via https://jira.external.example.com, it will look like this:
- <?xml version="1.0" encoding="UTF-8"?>
- <saml2p:AuthnRequest
- xmlns:saml2p="urn:oasis:names:tc:SAML:2.0:protocol" AssertionConsumerServiceURL="https://jira.external.example.com/plugins/servlet/samlsso" Destination="https://someidp.example.com" ID="_b655e6b787907cb93fb98344e0560c3f" IssueInstant="2018-05-07T08:45:24.563Z" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Version="2.0">
- [...]
- </saml2p:AuthnRequest>
