Important Update Effective February 1, 2024!
Due to recent changes in Jira and Confluence, we've made the tough decision to discontinue the OpenID Connect (OIDC)/OAuth app and no longer provide new versions for the newest Jira/Confluence releases as of January 31, 2024.
This is due to some necessary components no longer shipping with Jira/Confluence, which would require some extensive rewrites of the OIDC App.
Important Update! This app will be discontinued soon!
Due to recent changes in Jira, which no longer ships with some components required for our Read Receipts app to run, we've made the tough decision to discontinue the app, as of Februar 5, 2025.
Important Update! This app will be discontinued soon!
We've made the tough business decision to discontinue the app, as of January 11, 2025.
Setup SAML SSO with G Suite/Google Apps (Confluence)
This guide describes how to complete the initial setup for SAML Single Sign On (SSO) for Confluence with G Suite (Google App), applicable from plugin version 0.14.5.
Technical Support:
If you need any further support please feel free to contact us at our customer support portal. Or you can schedule a screen share session with us at a time of your convenience.
Visit us at Atlassian Marketplace:
SAML SSO for Confluence https://marketplace.atlassian.com/plugins/com.resolution.atlasplugins.samlsso.Confluence/server/overview
Step1 Install the plugin | Step2 Setup the ADFS (A-E) | Step3 Configure the Plugin (A-B) |
|---|---|---|
Step4 Test | Step5 Enable login redirection | Advanced Configuration |
Prerequisites
- G Suite Account, click here for more information.
- JIRA must be accessible via HTTPS. See https://confluence.atlassian.com/jira064/running-jira-over-ssl-or-https-720411727.html for instructions.
Step 1: Install the plugin
Click Add-ons under Confluence Administration on the top right corner of your Confluence interface. Then, choose Find new add-ons and you will be taken to Atlassian Marketplace. Search for SAML SSO and click on Free Trial to install.
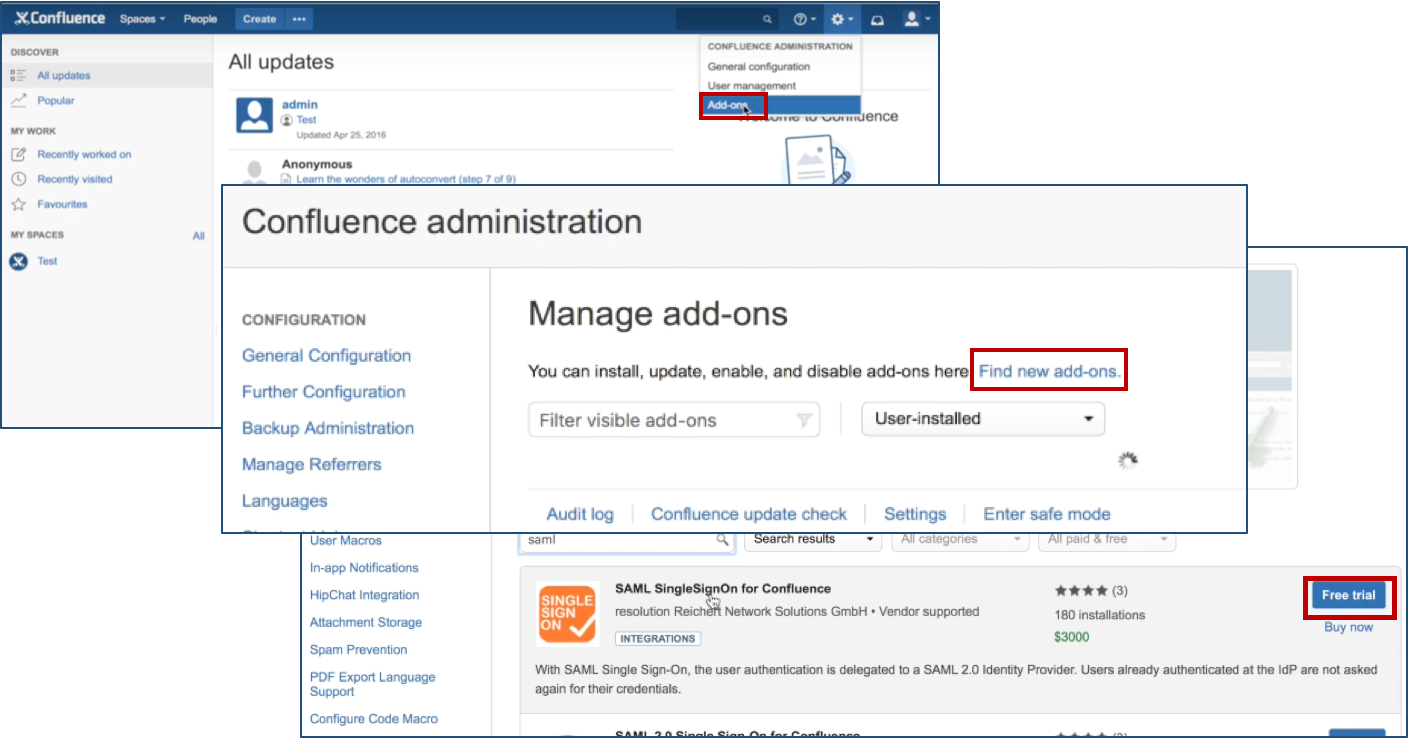
After installation succeeded, click on Manage, then choose Configure. Now, you are on the plugin configuration page.
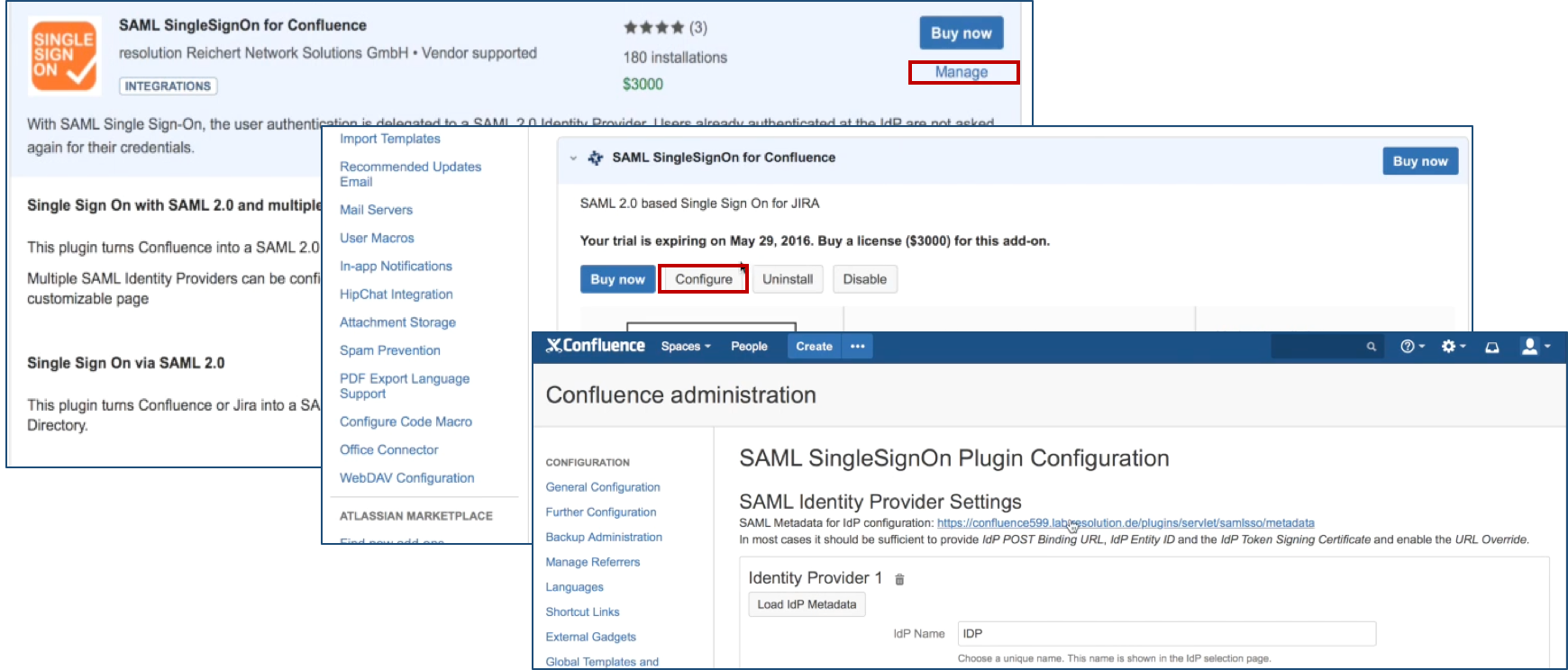
Step 2: Setup G Suite
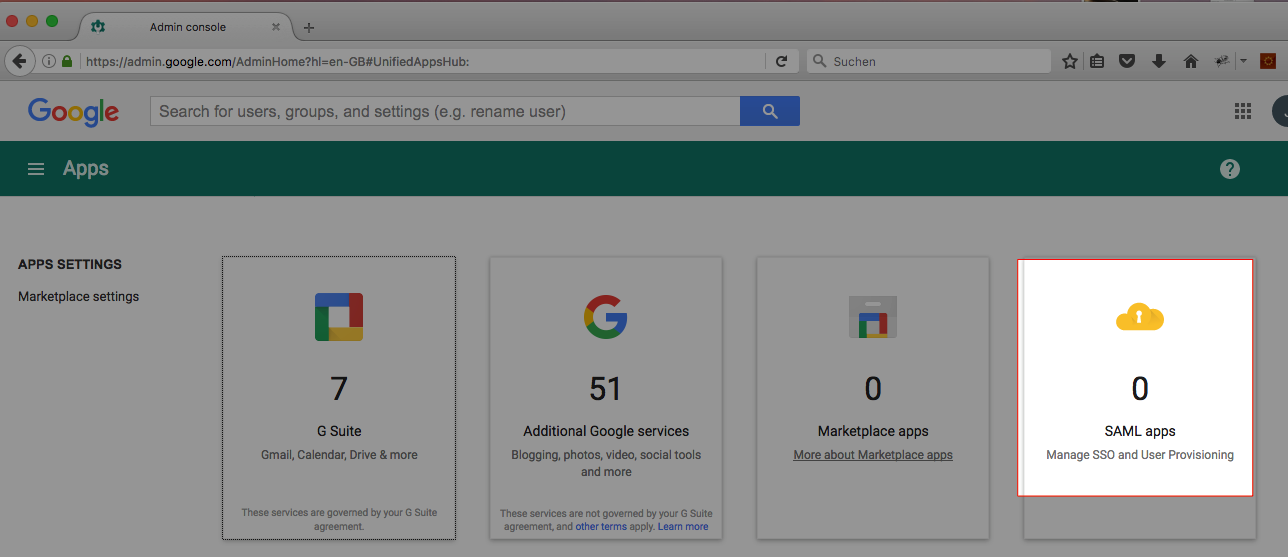
Login to the Google Admin console at https://admin.google.com
Substep A. Download IdP Meta Data.
- Click Apps.

- Click SAML-Apps.
- Click Add a Service/App to your domain.
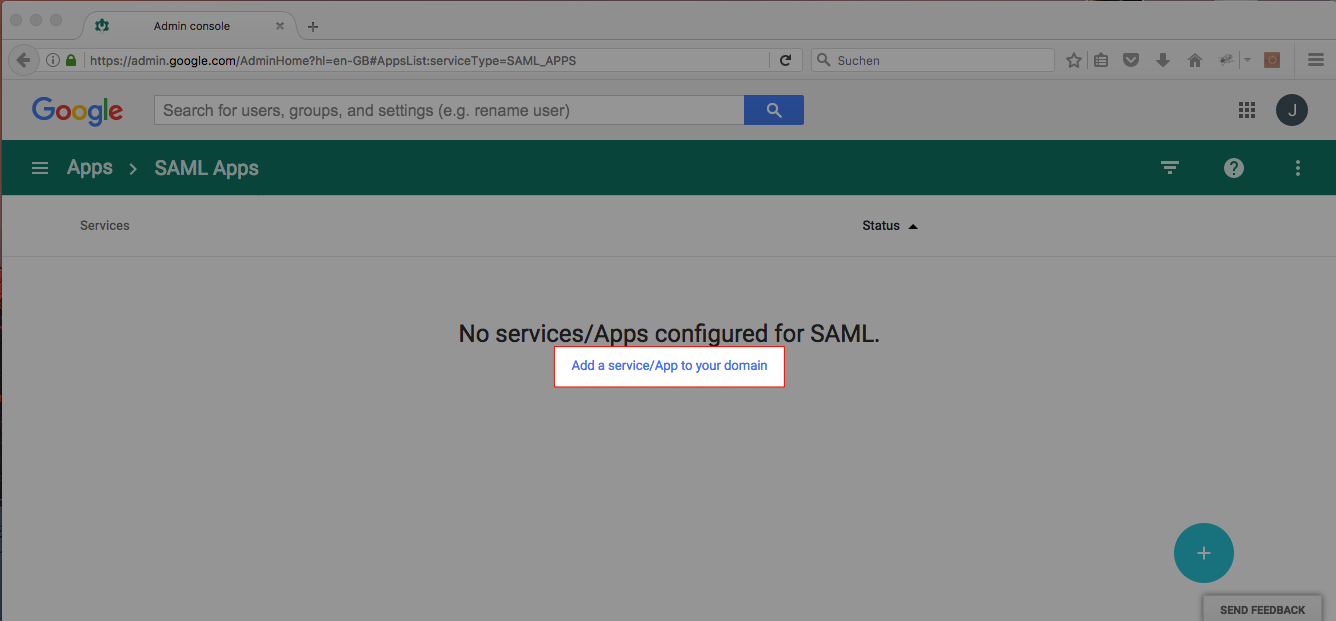
- Click Setup My Own Custom App.
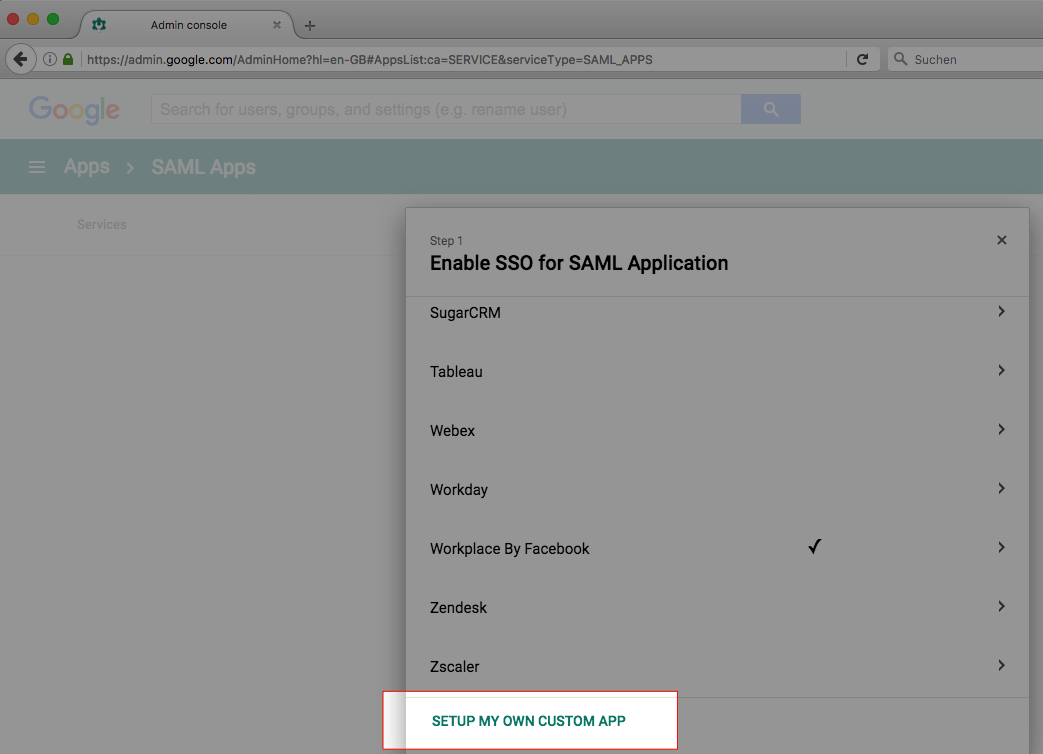
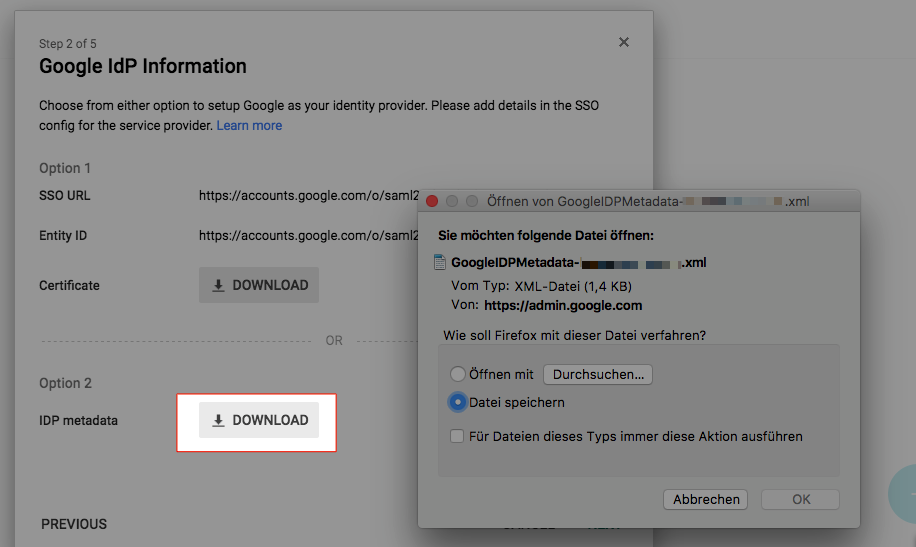
- Click Download for IDP-Metadata and Save the XML file.
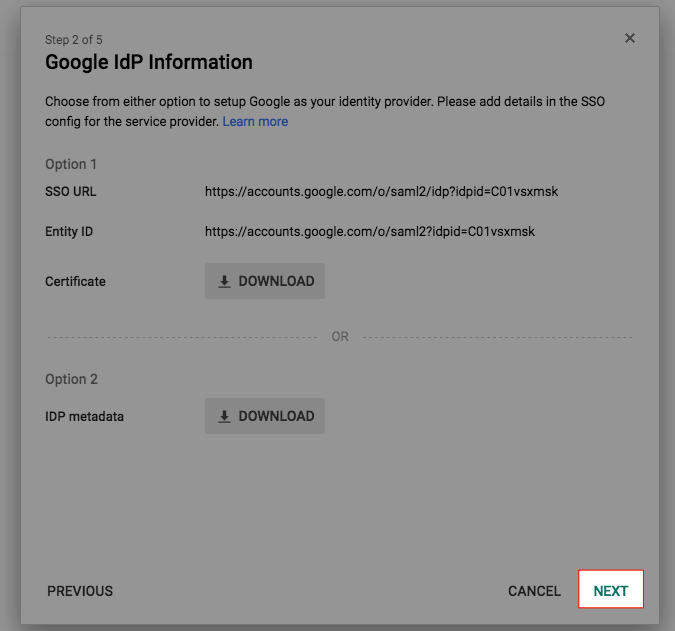
Substep B. Fill in Application Name and Description
- On the G Suite admin page, click Next.
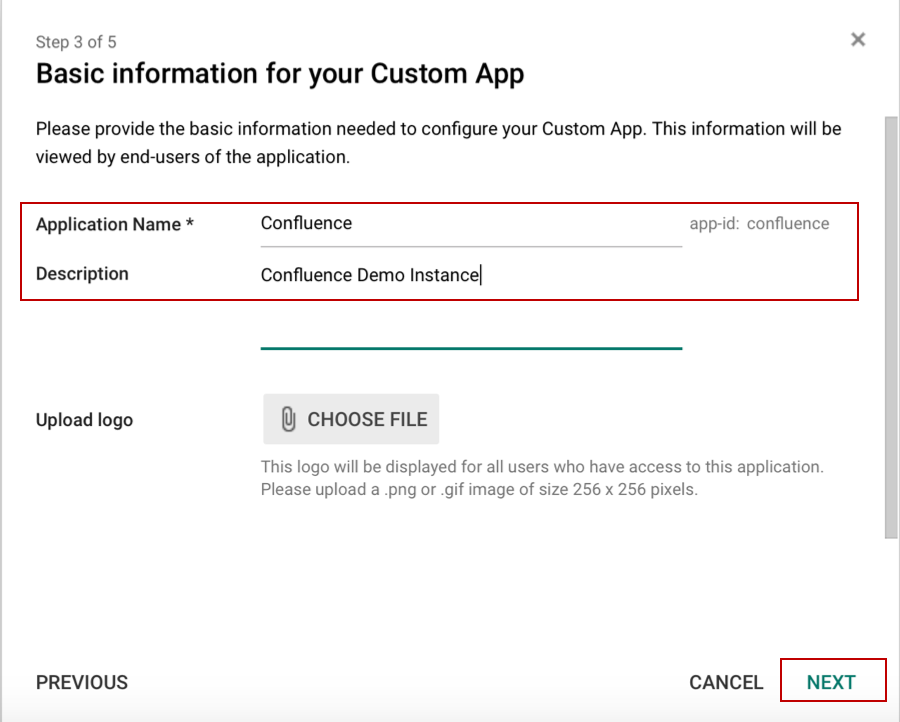
Choose an Application Name and Description and click Next.
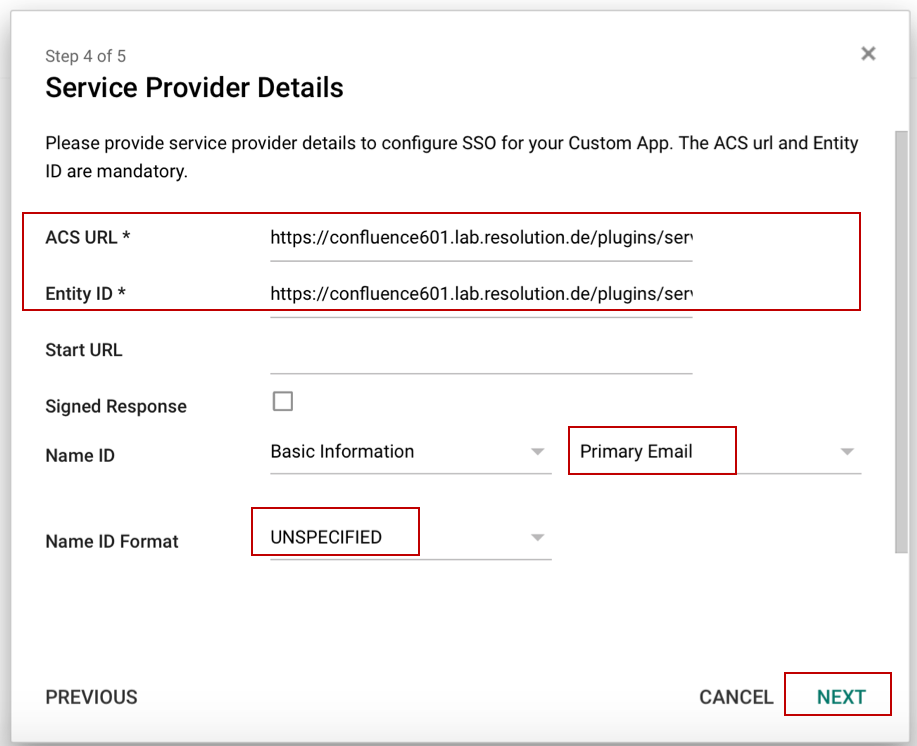
Substep C. Enter the Service Provider Details.
- Both ACS URL and Entity ID are https://<base-url>/plugins/servlet/samlsso.
- Select Primary Email as NameID and UNSPECIFIED as Name ID Format.
- Click Next.
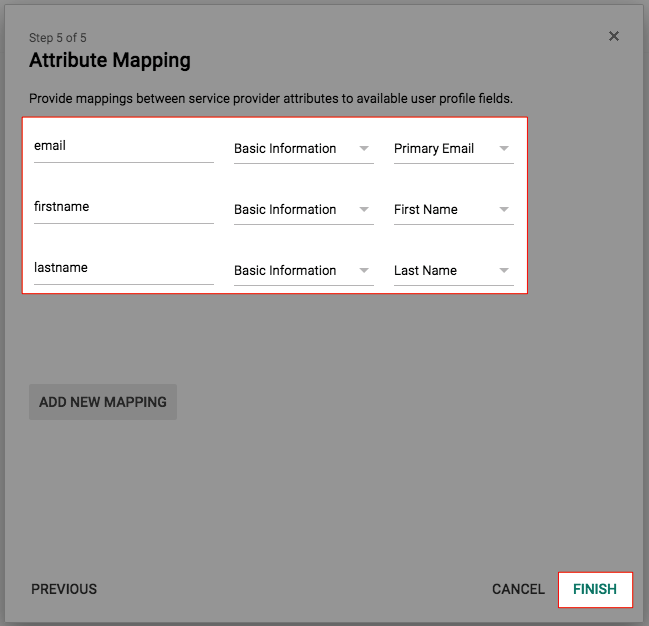
Substep D. Configure the Attribute Mapping
- This Mapping defines which values are contained in the SAML-Response. Use ADD NEW MAPPING to add in new value.
- In this example, 3 fields email, firstname and lastname are defined (the attribute names can be choosen) which are mapped to Primary Email, First Name and Last Name.
- Click Finish.
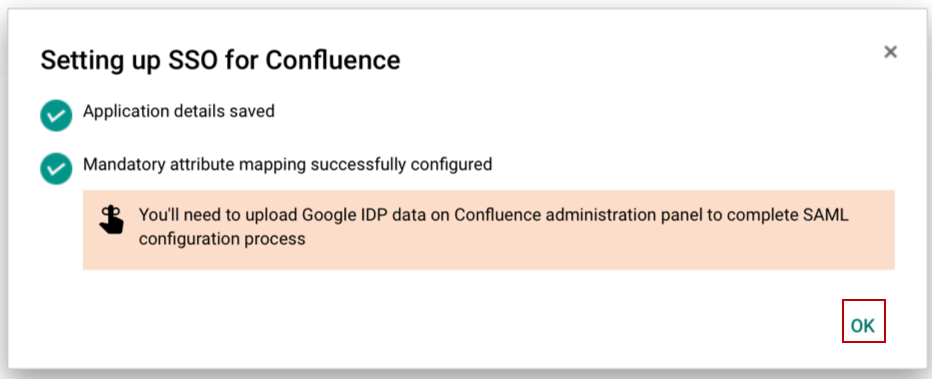
- Click OK to close the Wizard.
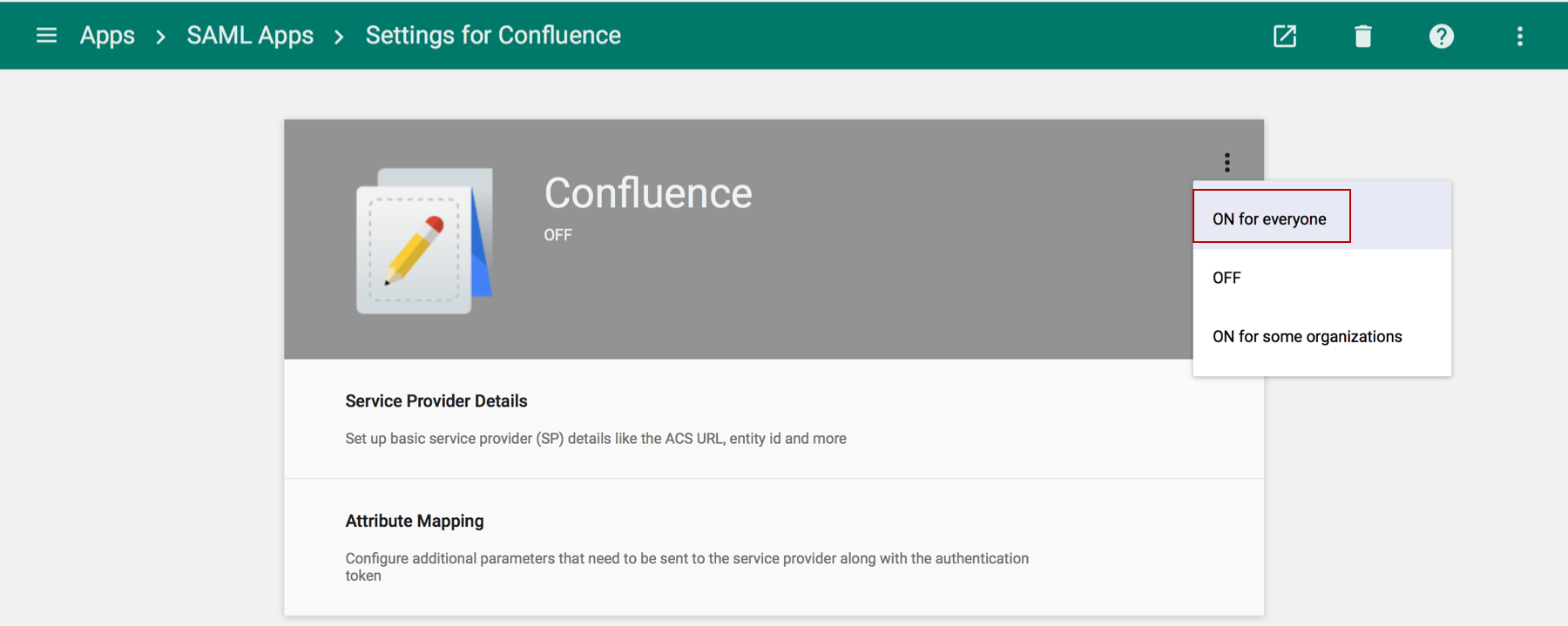
Substep E. Enable the IdP
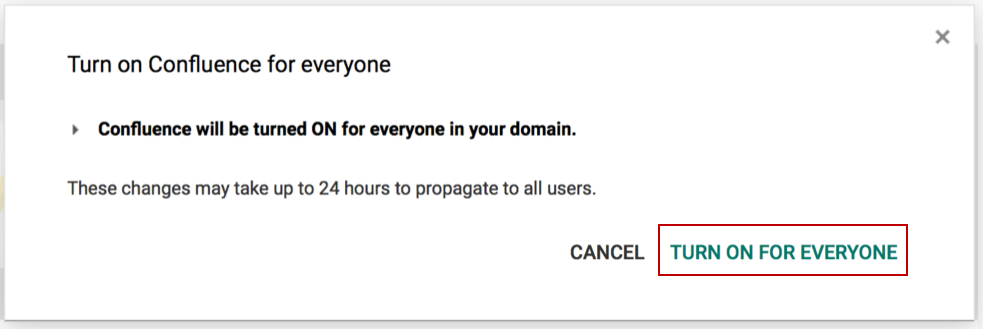
- Enable the IdP by selecting ON for everyone or ON for some organizations and confirming it.
Step 3: Configure the Plugin
To continue Step 3, please go back to the plugin configuration page opened in Step1.
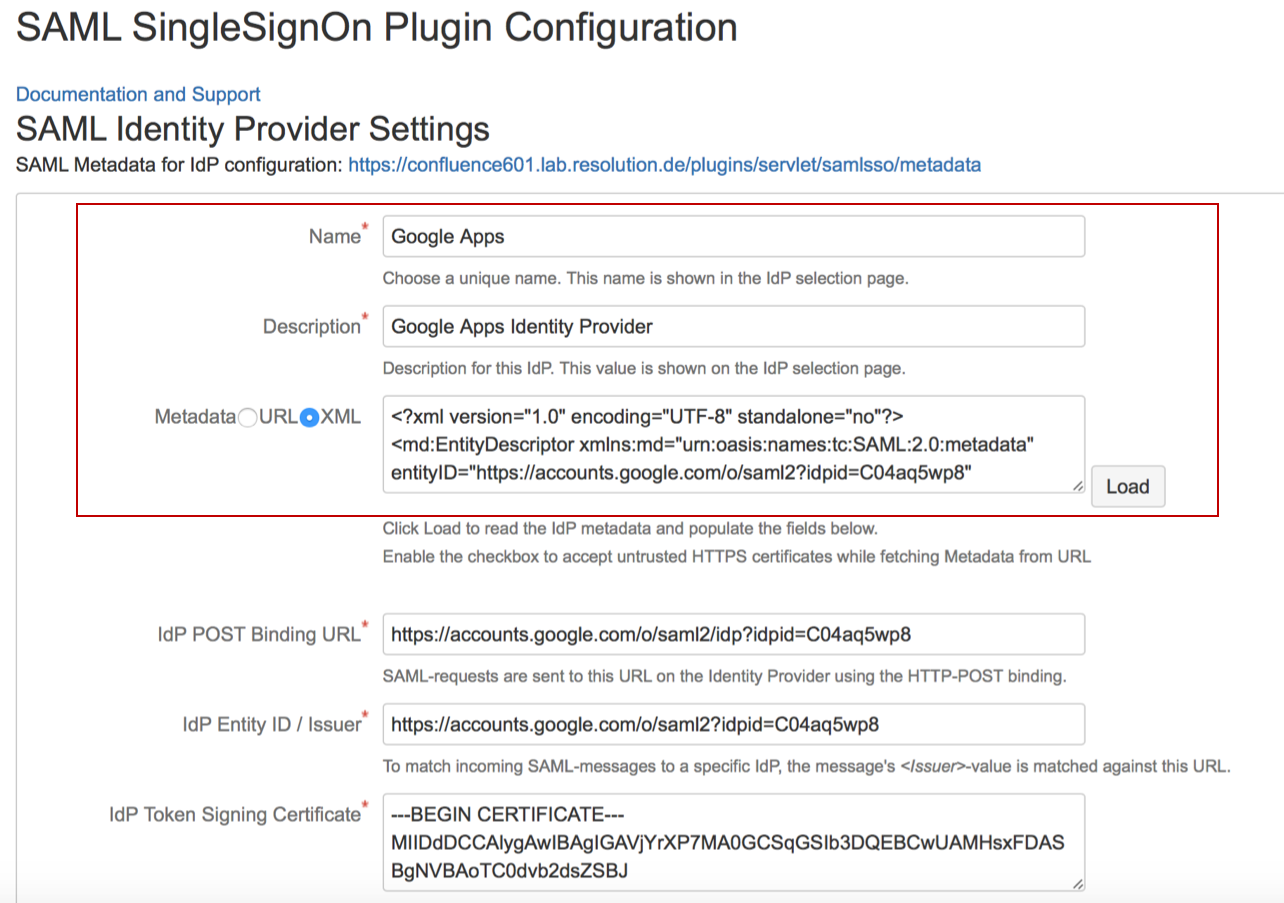
Substep A: Load G Suite Meta Data.
- On the Plugin Configuration Page, choose a Name and Description.
- Select the XML radio button, paste the content from the Metadata file downloaded in Step2 Substep1 and click the Load button.
- The IdP POST Binding URL, Entity Id and Certificate fields will be filled automatically.
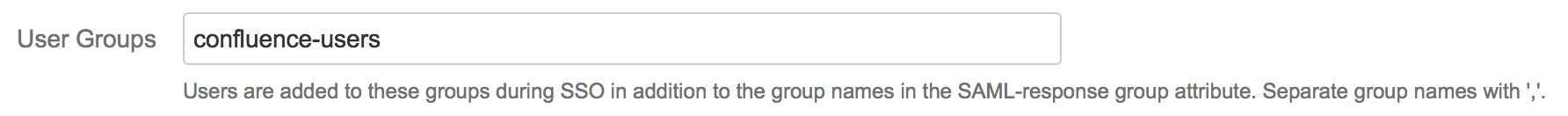
Substep B: Configure general Confluence groups
If a user logs in using SAML, he will be added to the groups specified in the User Groups section. This applies to all users. The user is assigned to these groups in addition to the groups in the SAML-response's attribute. The standard group in Confluence is called "confluence-users".
- Click Save settings to store the configuration
Step 4: Test
Create a Confluence user which has his G Suite email address as userid (if no such user already exists).
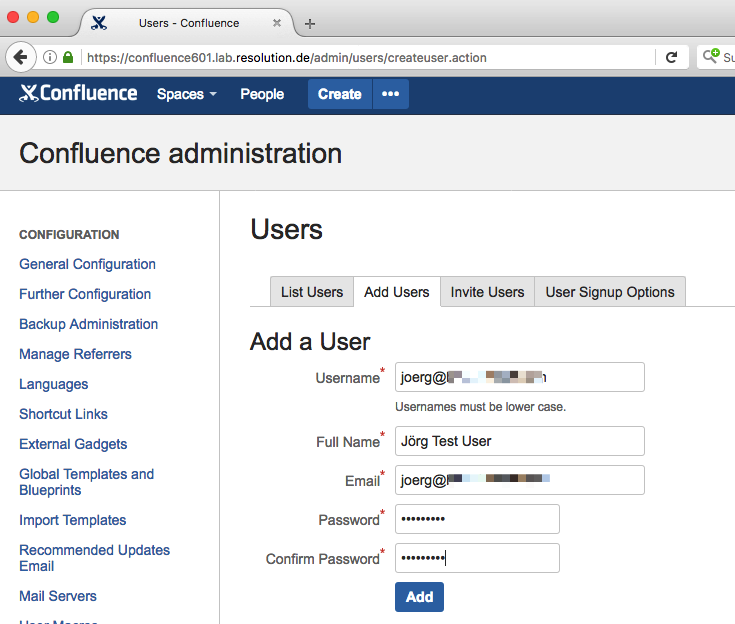
If the user should use SSO only, we recommend using a long string of random characters for the password.
- Open a private browser window (or another browser with no active session in Confluence).
- Enter the SSO-URL- https://<base-url>/plugins/servlet/samlsso.
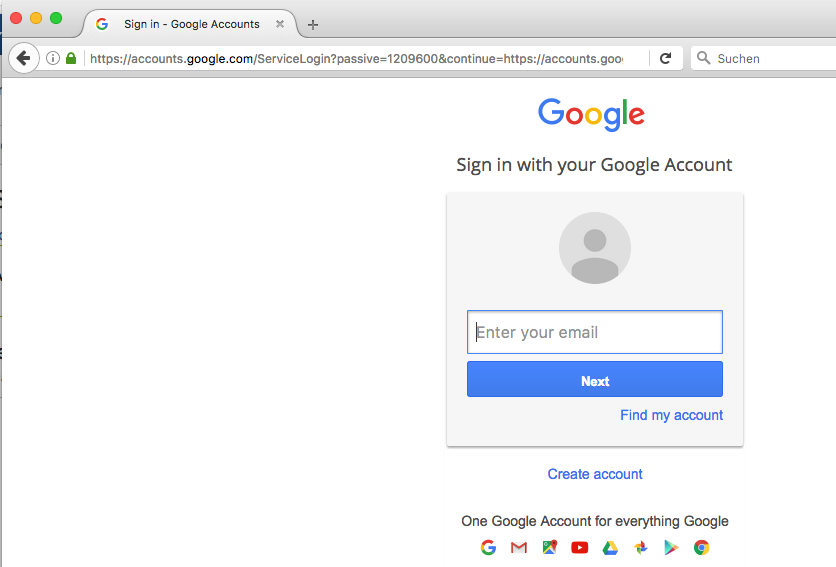
- You should be redirected to the Google login.
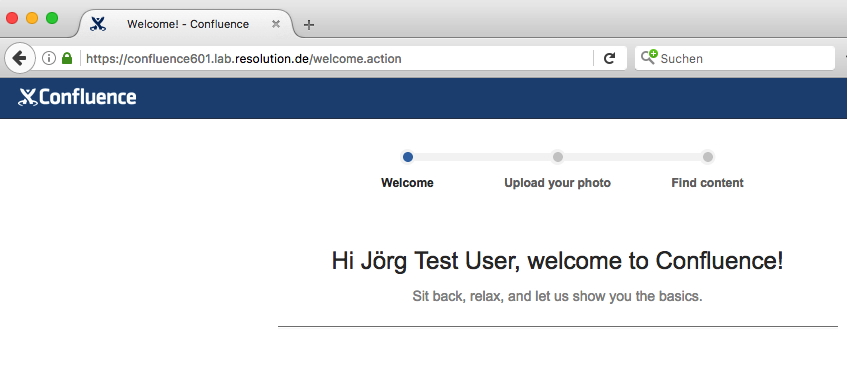
- After logging in to Google, you should be logged into Confluence:
Step 5: Enable login redirection
- After the setup has been tested successfully, the automatic redirection at the IdP can be enabled by checking the Enable SSO Redirect and Override Logged Out URL checkboxes:
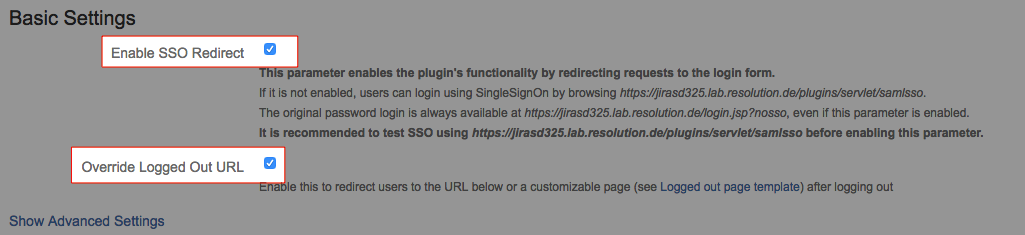
With these settings, users accessing Confluence will be automatically redirected to the IdP. So if they already logged in at Google, then they would be also instantly logged in to Confluence.
Advanced Configurations
Advanced IdP settings
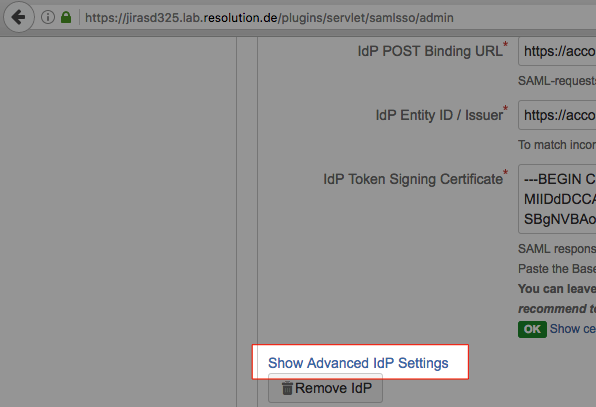
- To see advanced Idp-specific settings, click Show Advanced IdP Settings in the IdP section of the configuration.
Advanced general settings
- To see advanced general settings, click Show Advanced Settings in the general settings section.
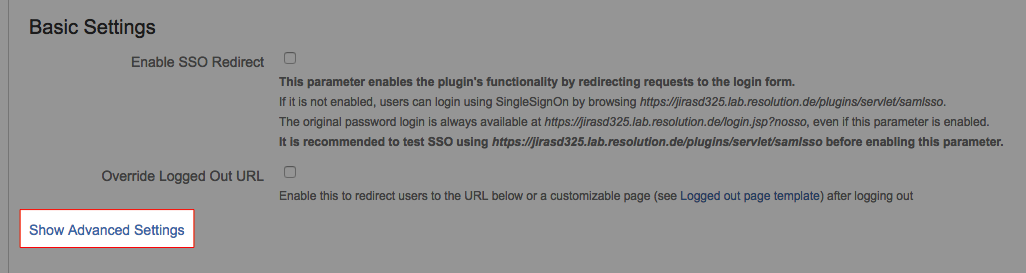
All changes require clicking the save button to be active.
Userid transformation
G Suite can only provide the email address as userid. If your JIRA usernames are e.g. user with the email address user@example.com, you can transform it.
- On the Plugin Configuration Page, click Show Advanced IdP Settings.
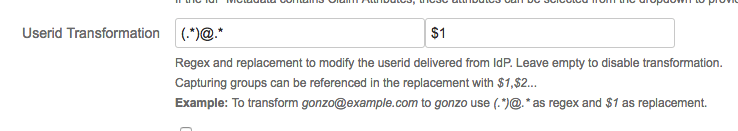
- In the Userid Transformation field, enter (.*)@.* and $1. This will strip the @ and domain-part away.
User creation/update with combined fields
Users can be created during their first login (see Create or update users through SAML Attributes)
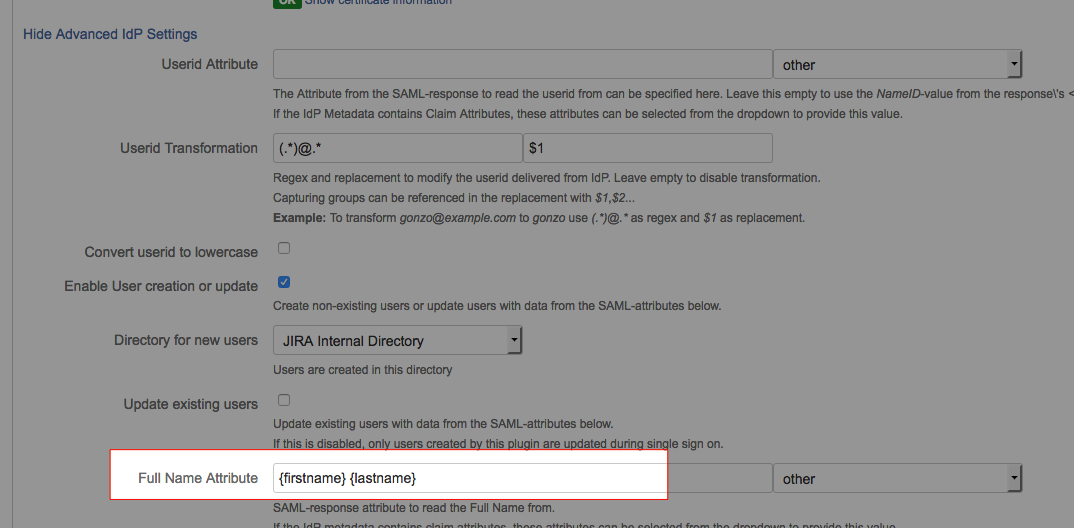
G Suite cannot provide the full name as a single field. This is why the full name attribute setting allows a special syntax:
Multiple attributes can be combined by enclosing the attribute names in {}.
You might also find following documentation helpful:
