WebSudo Authentication kills session
Problem:
Websudo authentication is successfully triggered. However, after clicking "Ok" in the confirmation dialog the error message "Sending confirmation failed" is shown. When this happens, the current session is terminated, forcing the user to authenticate again.
Reason:
Confluence or Jira sends the session cookie (usually called JSESSIONID) without the SameSite flag.
Actual browsers interpret this absent value as "Lax". This leads to the following behaviour:
In the pop-up window, the user is sent to the SAML Identity Provider for additional authentication.
After authentication, the IdP triggers the browser to send a POST request to the Atlassian application, following the SAML POST binding.
The browser does not send the cookie in the POST request because it's initiated by a 3rd party (the SAML IdP).
The Tomcat server underneath Jira/Confluence creates a new session ID and sets a new session cookie. This causes the current session to get lost.
Workarounds:
Option 1: Use the integrated functionality since version 4.0.7
Customers using Jira versions earlier than 10 and Confluence versions earlier than 9 can use this option to ensure that the SameSite flag is set correctly.
Important:
If you plan to upgrade Jira or Confluence to a Platform 7 version in the future, it is recommended to use Option 2 instead. After upgrading to Platform 7, Option 1 will no longer work.
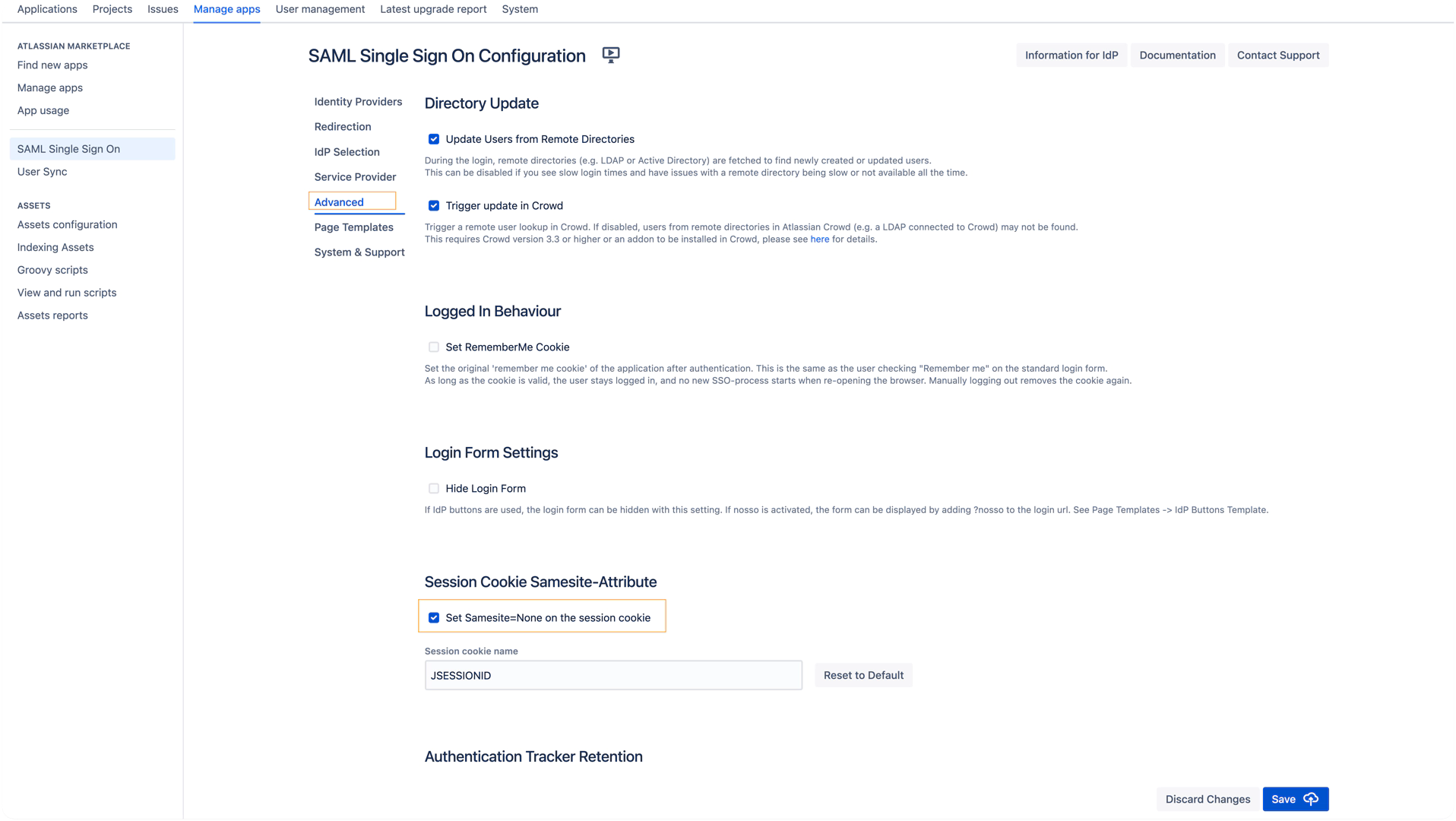
Steps to enable Option 1:
Navigate to the Advanced Settings.
Enable the checkbox Set SameSite=None on the session cookie.
Save the settings.
Option 2: Configure Tomcat to send SameSite="none"
This fix only works with Tomcat versions 9.0.28 or higher. In Confluence, this requirement is met starting from versions 7.3.4 and later, as they include a compatible bundled Tomcat version.
While newer Jira versions may now support newer Tomcat versions, it is still important to verify which Tomcat version your Jira instance is using. You can check the Tomcat version for your Jira instance here
Tomcat, the application server used by Jira and Confluence, can be configured to send cookies with SameSite=None.
To do this:
Open the file:
<Jira or Confluence installation directory>/conf/context.xmlAdd the following line inside the
<Context>tag:
- <Context>
- ...
- <CookieProcessor sameSiteCookies="none"/>
- ...
- </Context>
After restarting, the JSESSIONID cookie should be sent with SameSite=None, and WebSudo should work as expected.
Option 3: Configure Reverse Proxy to rewrite set-cookie headers
Most reverse proxies allow rewriting response headers. The Set-Cookie header should be rewritten to add the SameSite=None attribute when sending the JSESSIONID cookie.
Option 4: Configure IdP to send the SAML response using REDIRECT binding
The session cookie is preserved correctly if the SAML response is sent from the Identity Provider (IdP) using HTTP GET instead of POST.
This can be achieved by configuring the IdP to use Redirect Binding, if supported.
To apply this in the SAML plugin configuration:
Go to the Identity Provider settings under Request Settings.
Set the Protocol Binding option to REDIRECT.
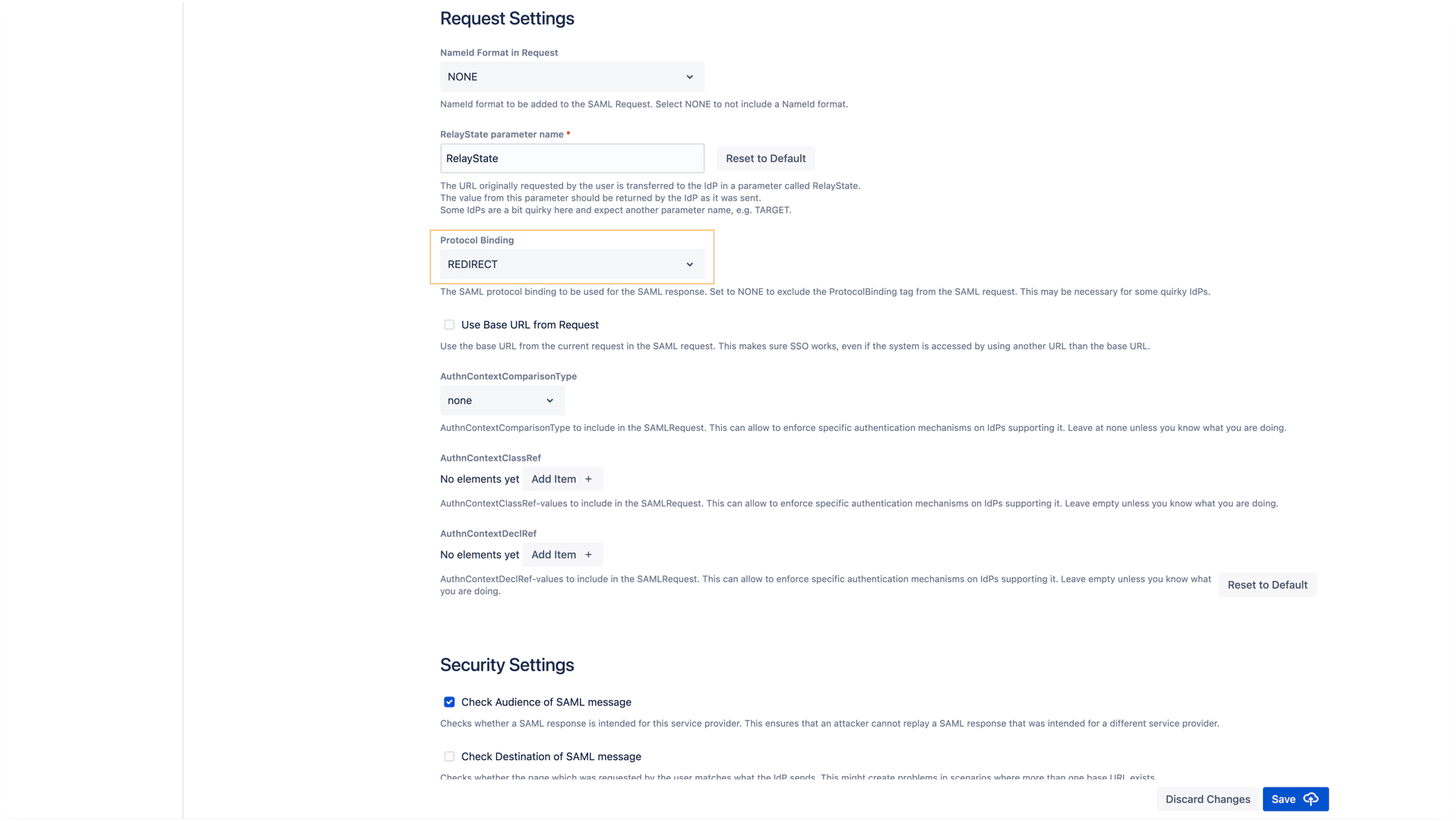
This may not be supported by the IdP - some IdPs will send the response with POST binding no matter what is set here.
