SAML2 Single Logout (SLO)
SAML Single Sign-On supports SAML Single Logout (SLO) for all Atlassian Data Center applications: Jira, Confluence, and Bitbucket.
Single Logout consists of two parts:
Closing the session on the Identity Provider if logging out of the Atlassian Data Center application
Closing the session on connected Atlassian applications if it is closed on the IdP
Our app supports both, but the support differs from IdP to IdP (see below).
Configure your Data Center product
To configure Single Logout, perform the steps below:
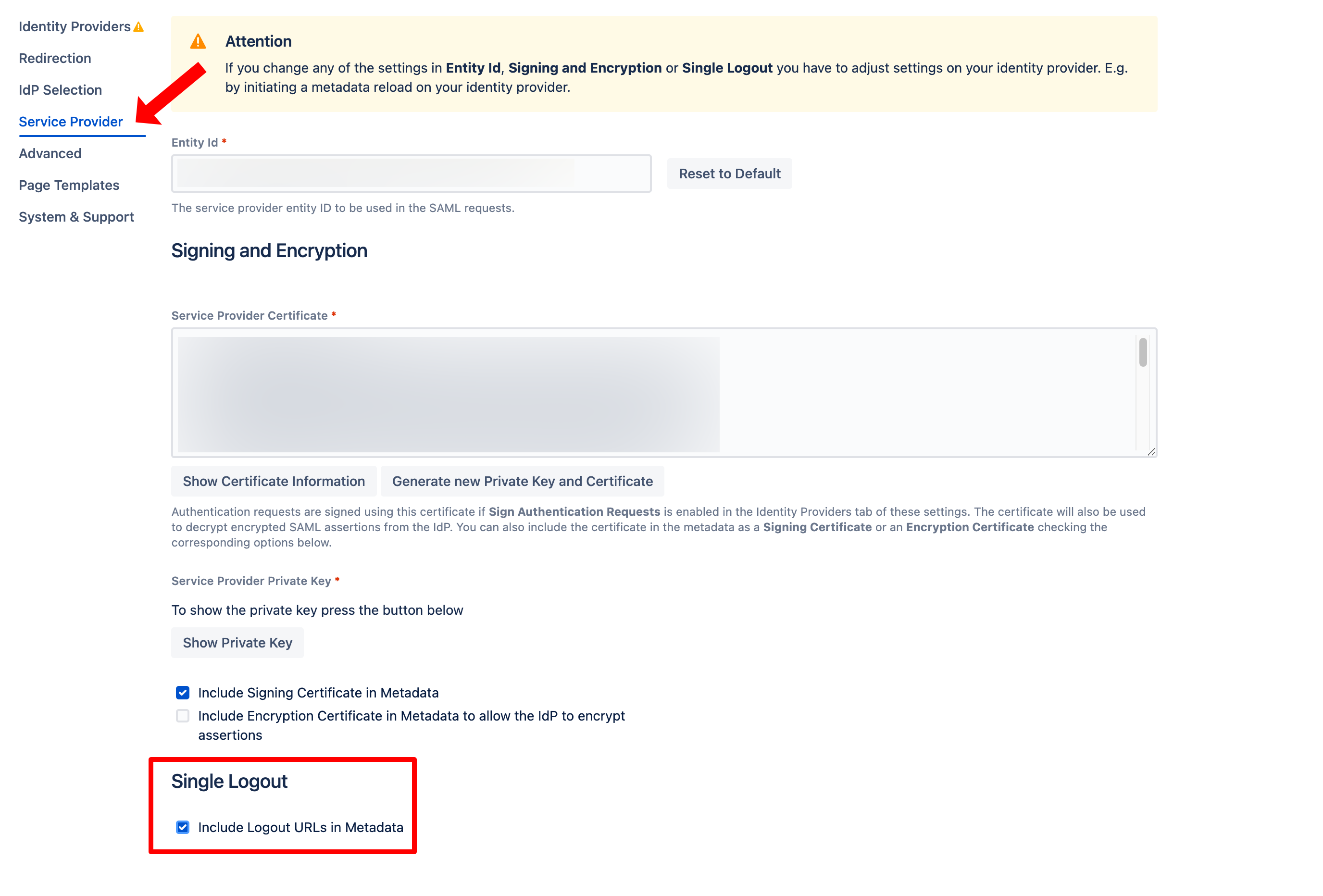
To provide the Single Logout-URLs in the SAML-Metadata, either enable the checkbox Include Logout URLs in Metadata in the app configuration tab Service Provider
or use this URL when fetching the Metadata on the IdP: https://<baseUrl>/plugins/servlet/samlsso/metadata?slo
In the app configuration tab for the IdP, select POST or REDIRECT for the Logout Binding and set the Single Logout-URL.
If you've loaded the identity provider's metadata and the IdP supports single logout, this URL should have been set automatically already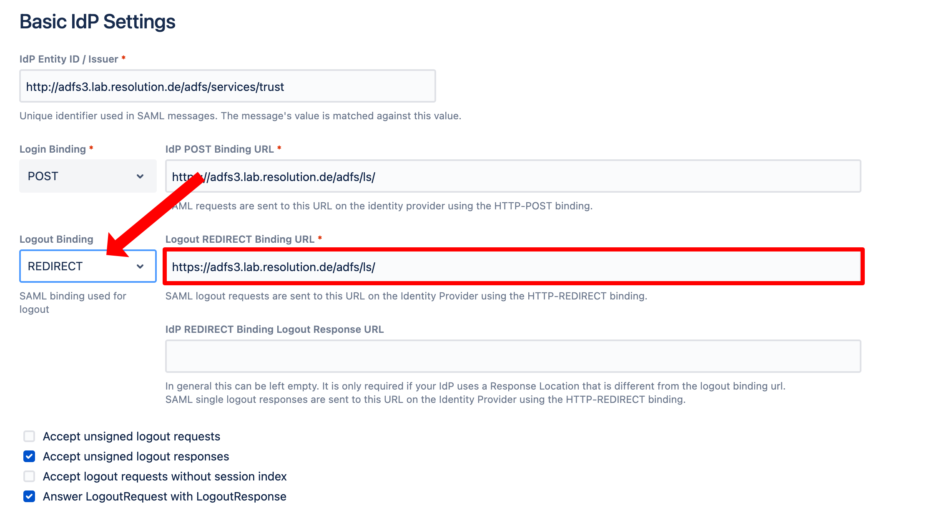
Save the configuration
Configure the IdP for Single Logout
Idp-specific configuration and limitations
Single logout has been tested so far with the following SAML IdPs. It should work with any other IdP supporting SLO.
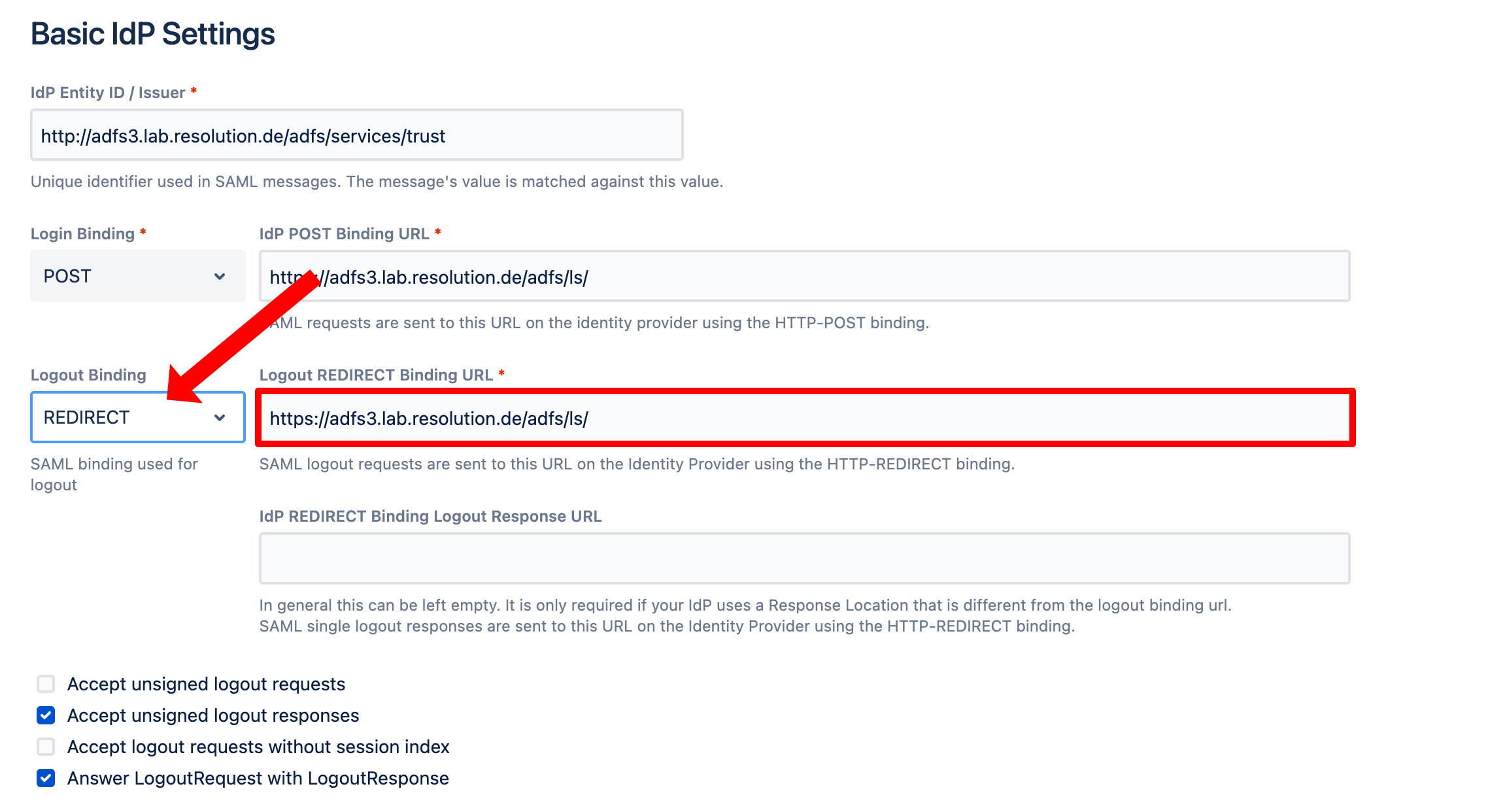
ADFS
ADFS fully supports single logout. No special configuration is necessary if metadata with the SLO-URLs is imported. After importing, check that the signing certificate and the logout endpoints are included in the configuration:
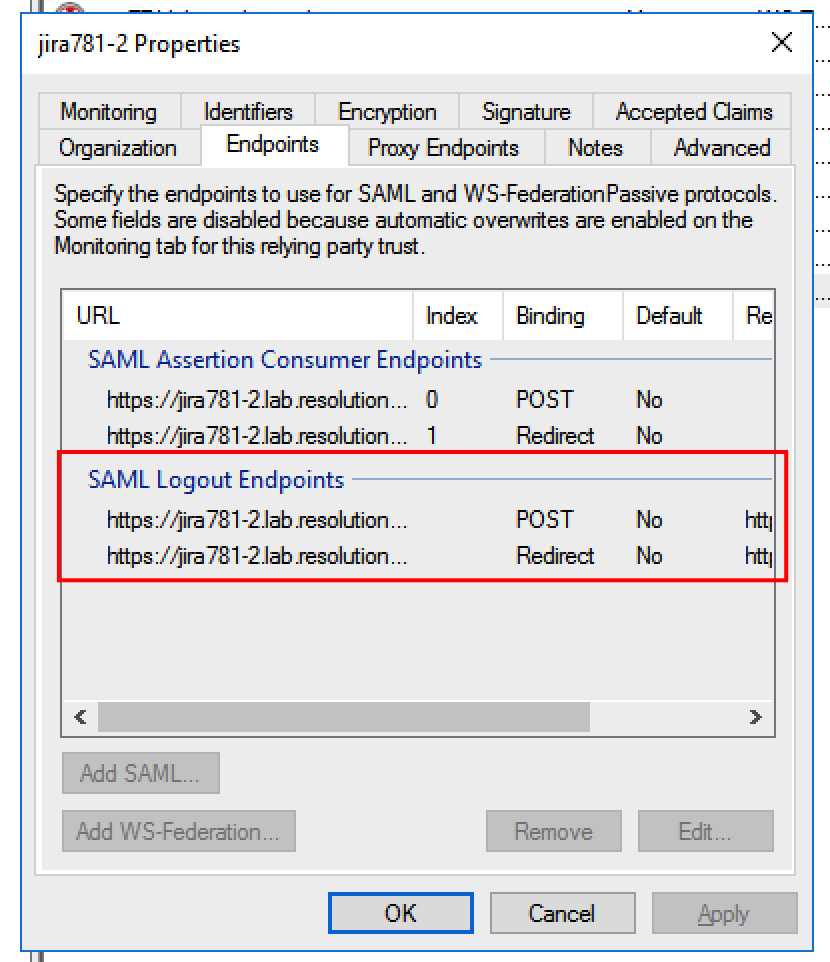
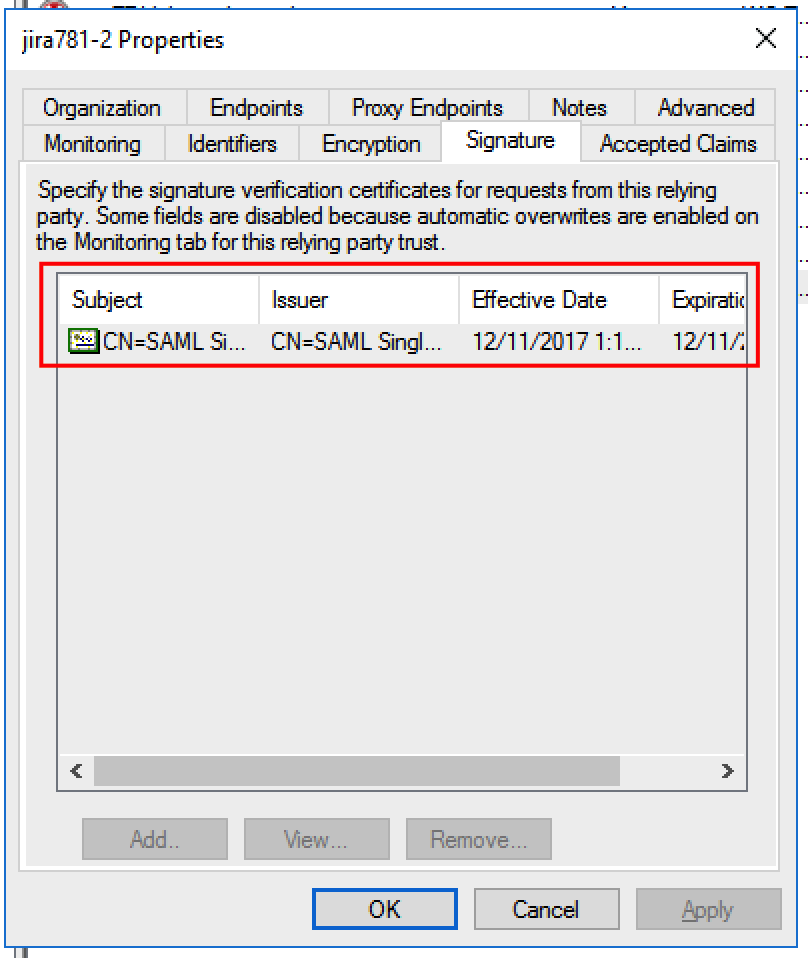
Azure AD
For Azure AD, make sure that the SAML SSO configuration looks as follows. Especially make sure that Answer LogoutREquest with LogoutResponse is NOT checked (like below).
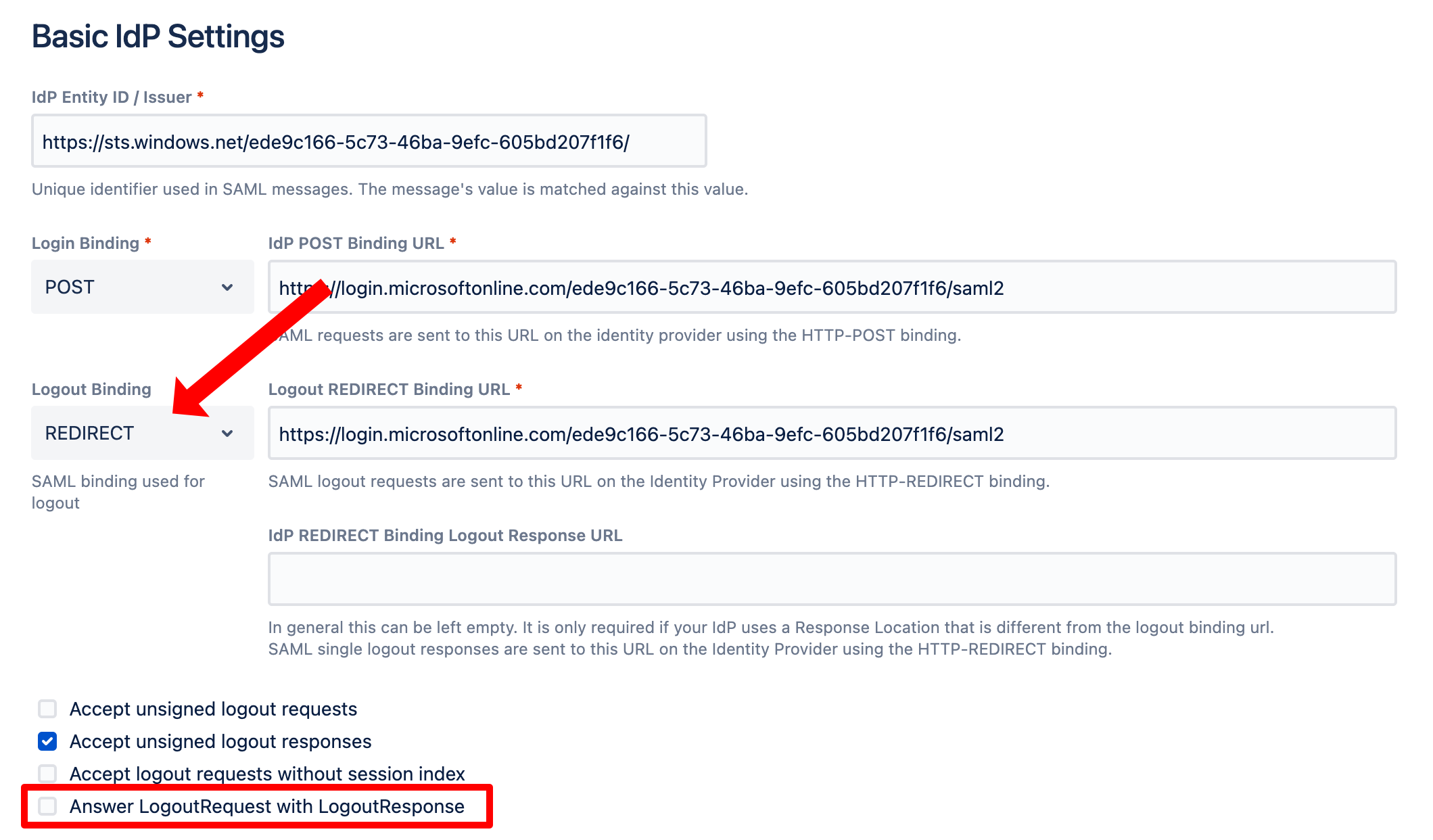
Next, go to the Azure portal to the Enterprise Application you have configured for your Atlassian Data Center product. Click Single sign-on and click the pen symbol for the Basic SAML Configuration:
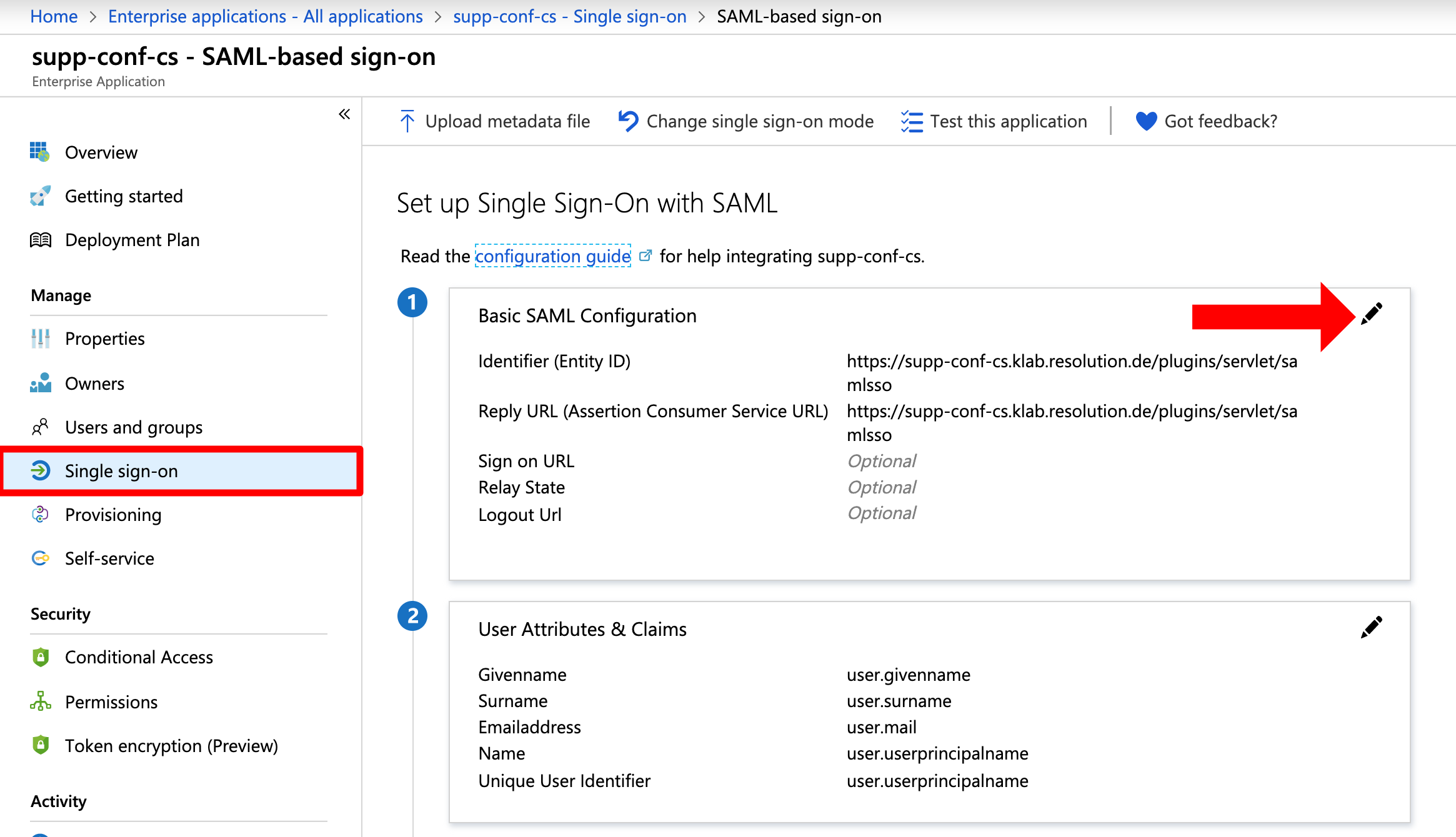
Copy & paste the URL you used for the Identifier (Entity ID) and Reply URL to the Logout Url: <baseURL>/plugins/servel/samlsso . Click Save.
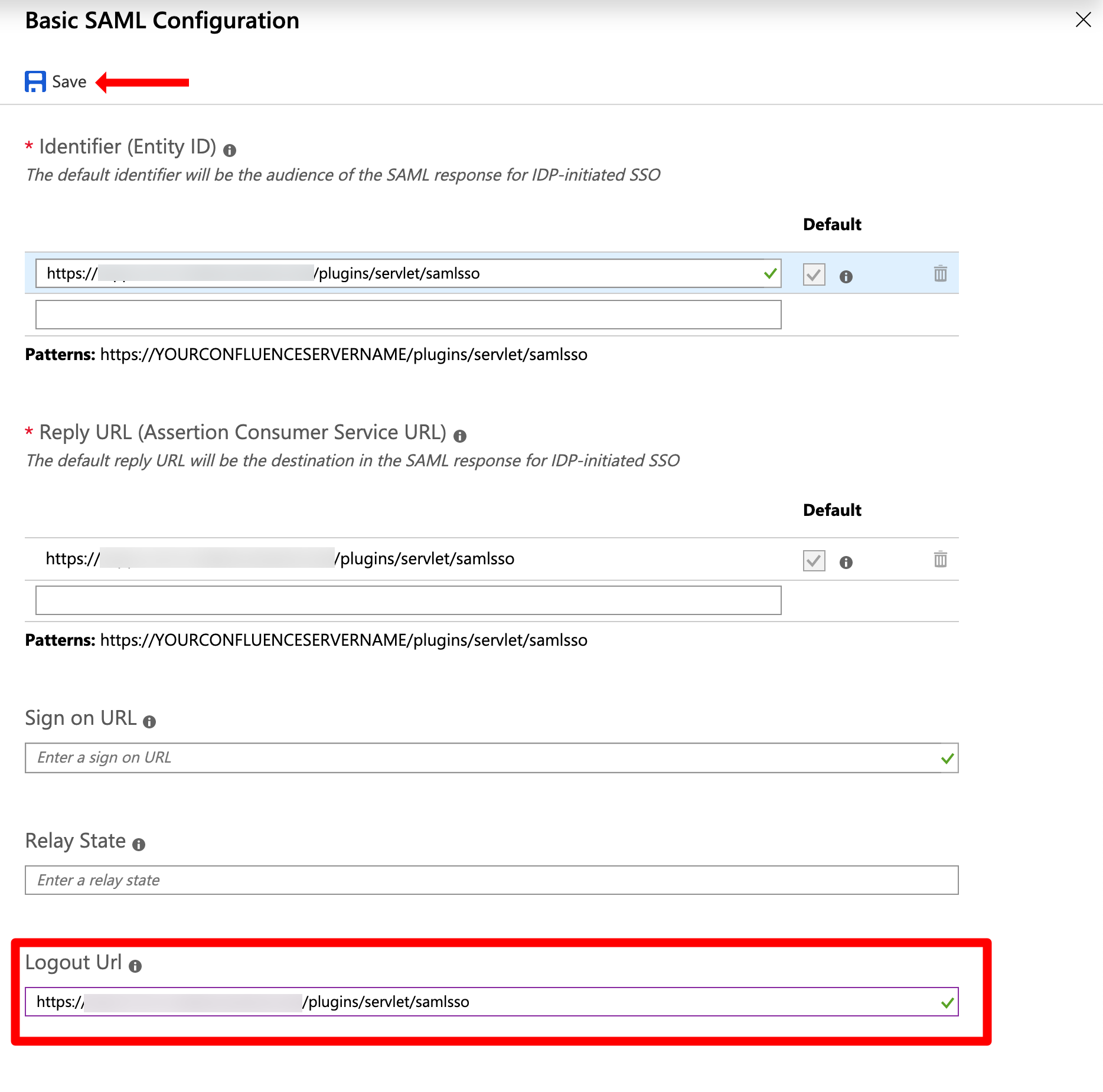
SLO for Azure AD is now configured.
OneLogin
OneLogout supports Single Logout, but does not sign the SAML logout requests and does not include the session index in the logout requests. To make it work, enable these checkboxes in the Addon's IdP configuration:
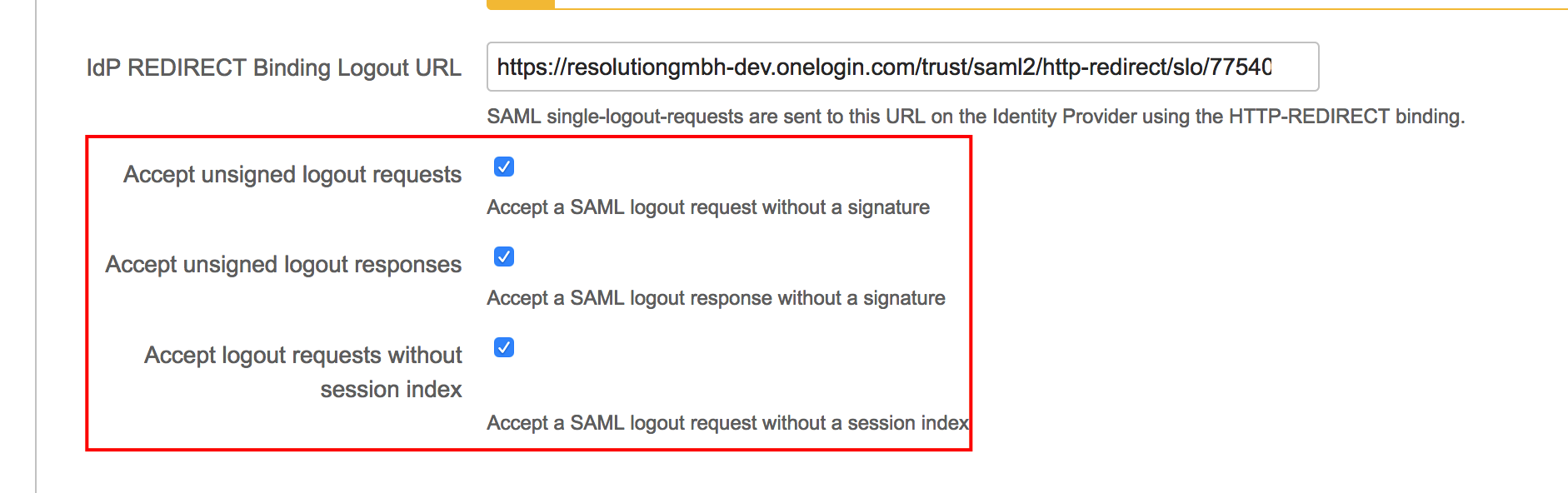
To configure OneLogin for Single Logout, use the SAML Test Connector (IdP w/attr) and set the logout URL to https://<baseUrl>/plugins/servlet/samlsso
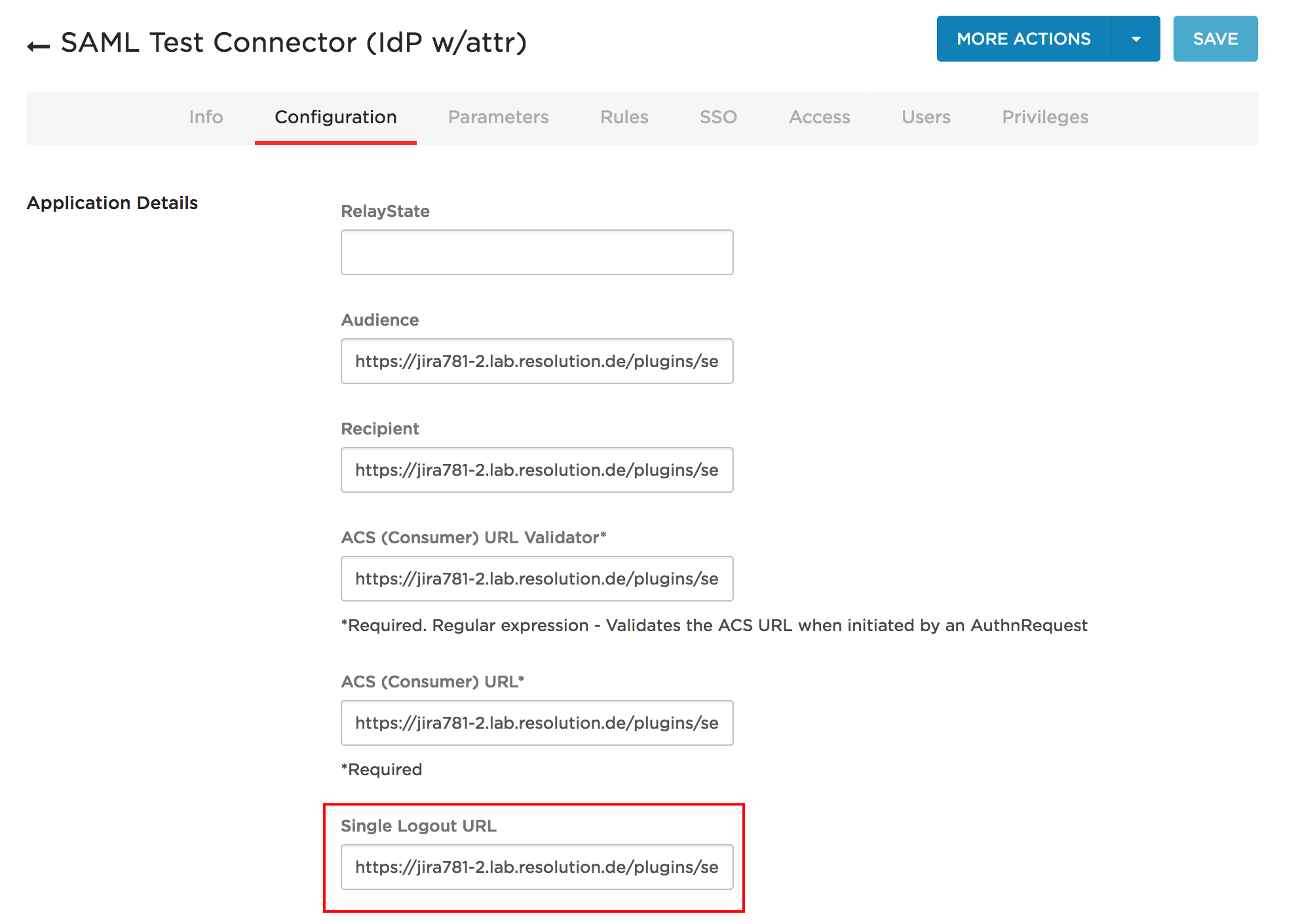
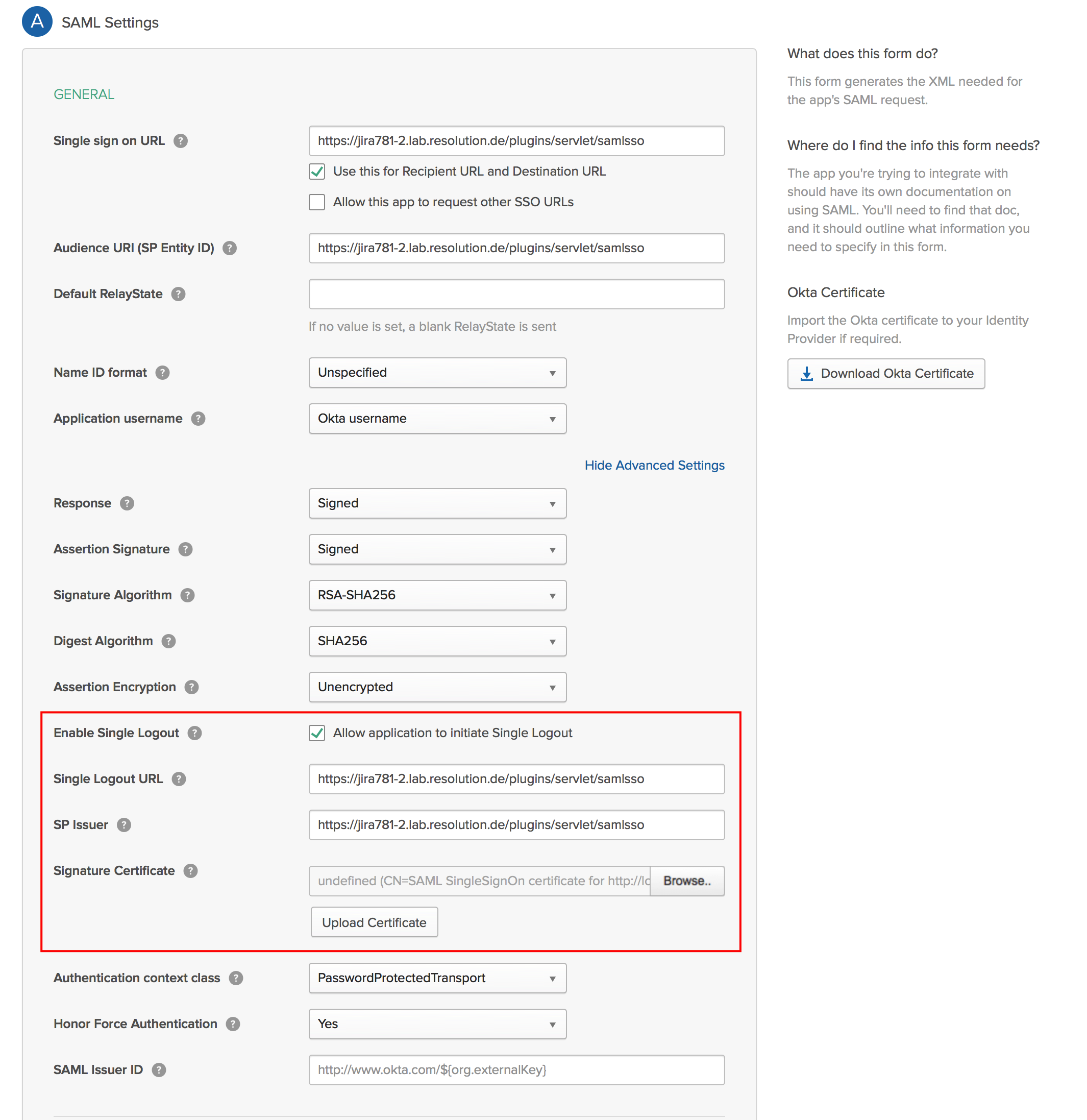
Okta
Okta support for Single Logout is limited:
If you log out of the Atlassian Data Center application, the session on Okta is closed, but the sessions on other applications stay active
If you have multiple applications configured and you log out of the first one, then you get the logout screen. If you then log out of the second one, you will see the Okta login screen. After logging in there, the logout process is completed and no new Okta session is created. The internal Okta ticket-id for this issue is OKTA-164419.
To enable Single Logout, set the appropriate values in the Application's SAML-settings:
Keycloak
To configure Keycloak for Single Log Out, please do the following
Go to your Keycloak instance and log in as an administrator.
Go to Clients and select the client you have configured for SAML SSO.
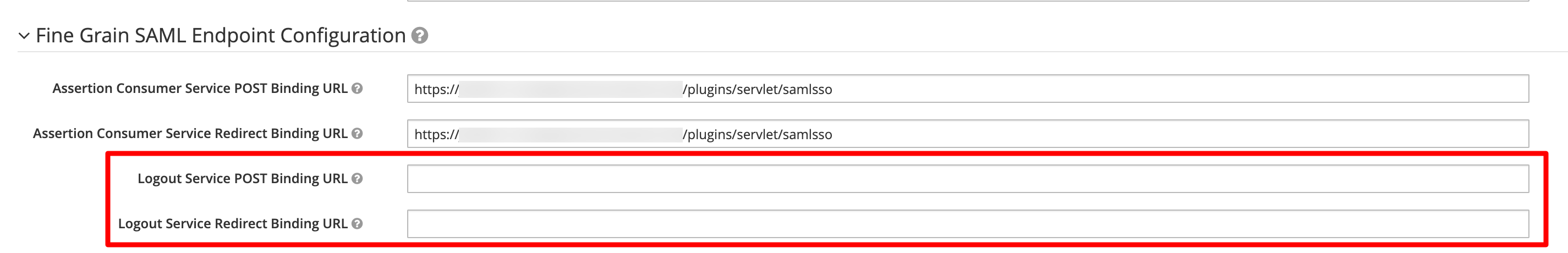
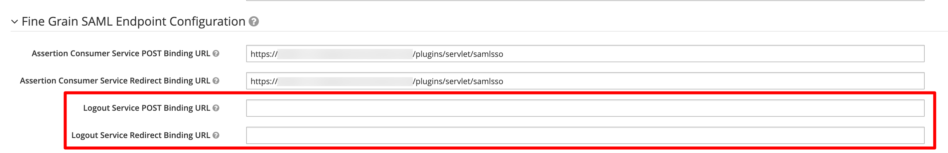
Scroll down and expand Fine Grained SAML Endpoint configuration. If there is no entry for the Logout Service POST Binding URL and the Logout Service Redirect Binding URL, use the same URL as for the other fields above: <baseURL>/plugins/servlet/samlsso
Save the configuration.