Important Update Effective February 1, 2024!
Due to recent changes in Jira and Confluence, we've made the tough decision to discontinue the OpenID Connect (OIDC)/OAuth app and no longer provide new versions for the newest Jira/Confluence releases as of January 31, 2024.
This is due to some necessary components no longer shipping with Jira/Confluence, which would require some extensive rewrites of the OIDC App.
SCIM Connectors and Authenticating Load Balancers
Problem
We have an authenticating load balancer in front of our instance and we cannot connect to the SCIM connector.
Solution
For the SCIM connector to work properly, your identity provider must be able to communicate with the SCIM endpoints provided by User Sync.
This means, that the authenticating load balancer must not authenticate this connection to your instance, because otherwise the request from your identity provider will be redirected to the login page of the identity provider.
Additionally, this also means that there is a path to the instance for which the connection is not authenticated.
To make a SCIM connector work in this scenario, you
- must get the connector id of the connector,
- create a second load balancer rule that does not authenticate when the identity provider tries to connect to the instance's SCIM endpoints
- and this rule must be above the other rule to not trigger the authentication.
See the following example for an AWS authentication load balancer. Please note that this might look differently for your authenticating load balancer:
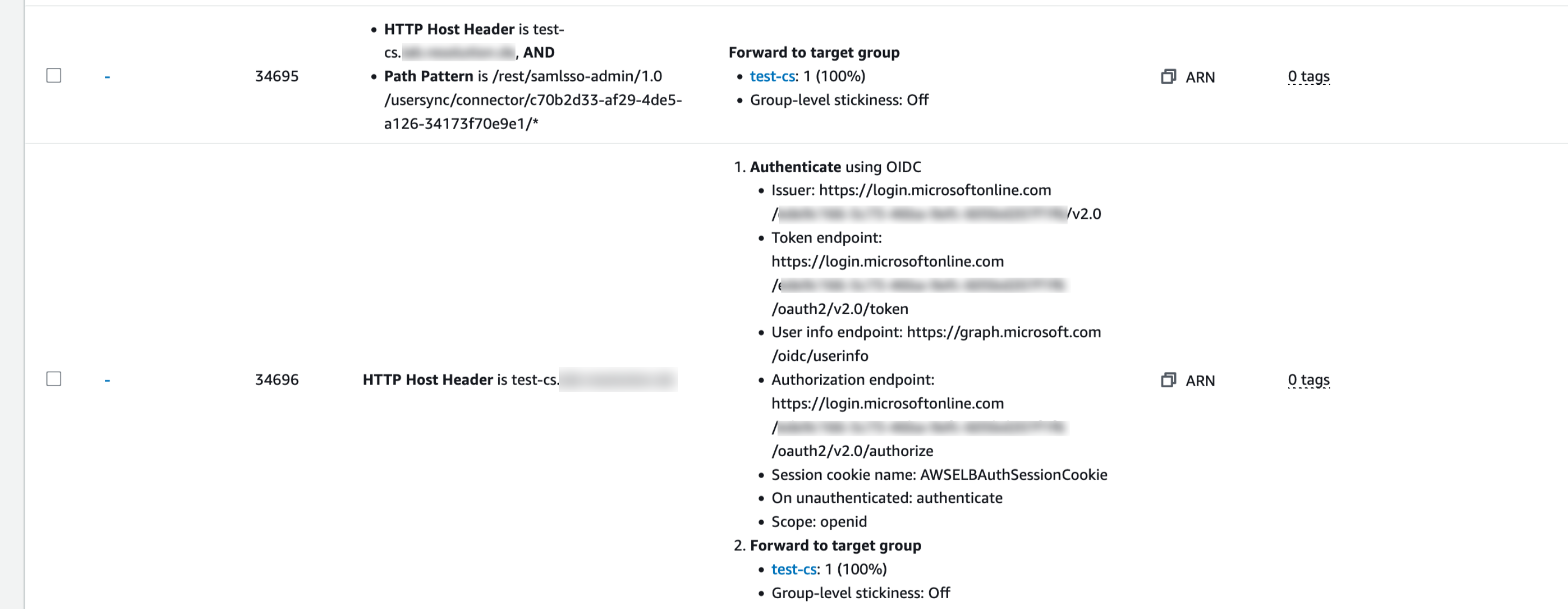
We created a second rule that forwards to the instance without authentication when the Path Pattern is
/rest/samlsso-admin/1.0/usersync/connector/<connector-id>/*This makes sure that all SCIM endpoints User Sync provides are reachable from the outside. Please note that instead of using the wildcard "*" you can also create or-ed rules for all endpoints described by the SCIM standard.
Please refer to your load balancer documentation for ways to exclude a path from being authenticated.
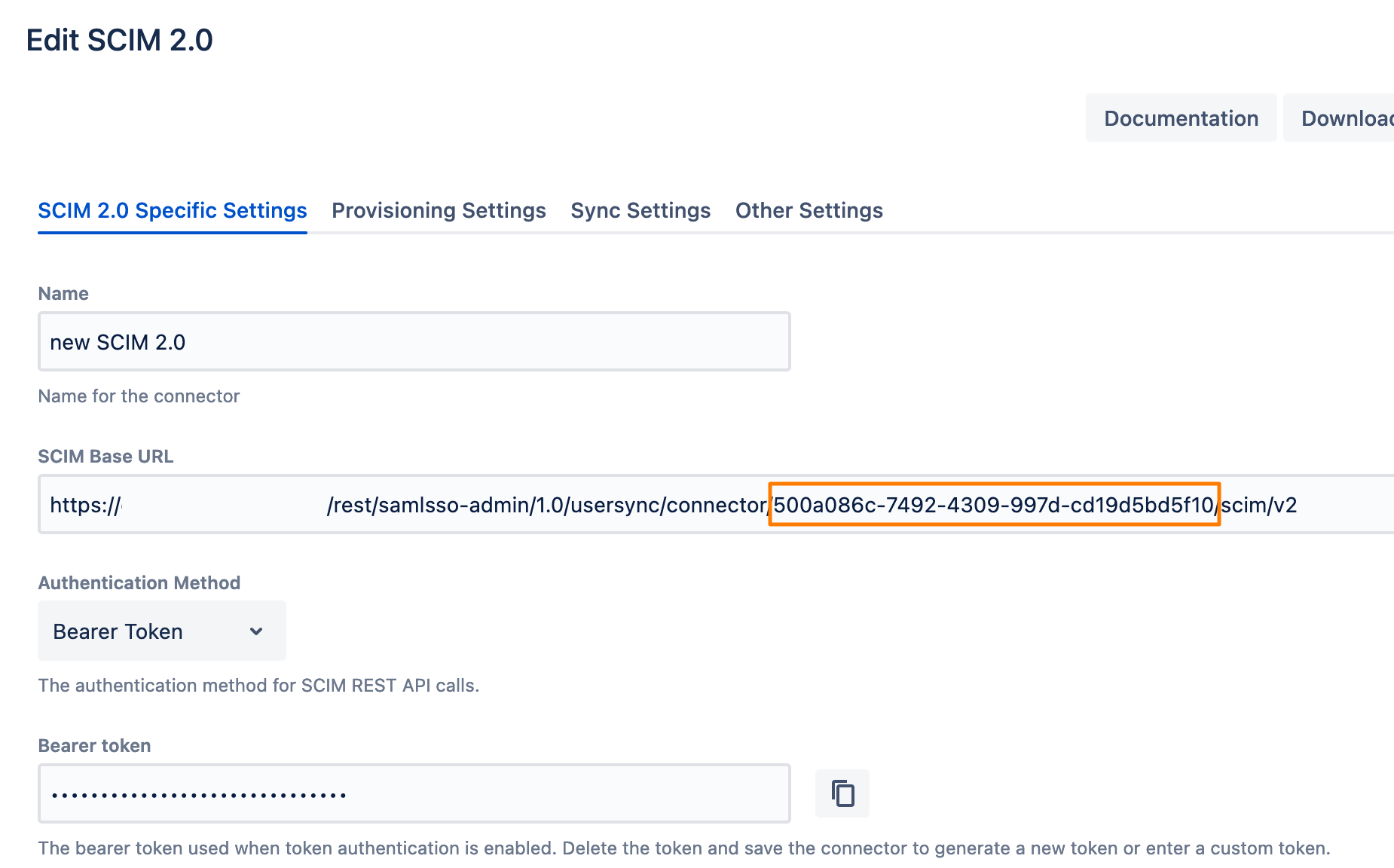
To find the connector id (and/or the URL), go to User Sync and click Edit for your connector: