The signed in user is not assigned to a role for the application
Problem
When using SSO with Azure AD you might receive an error from Azure after providing the username and password:
The signed in user is not assigned to a role for the application
AADSTS50105: The signed in user 'azure-username' is not assigned to a role for the application 'a33eedec-d848-4552-bb59-af60a2aeb63c'(name-of-the-sso-enterprise-app in Azure).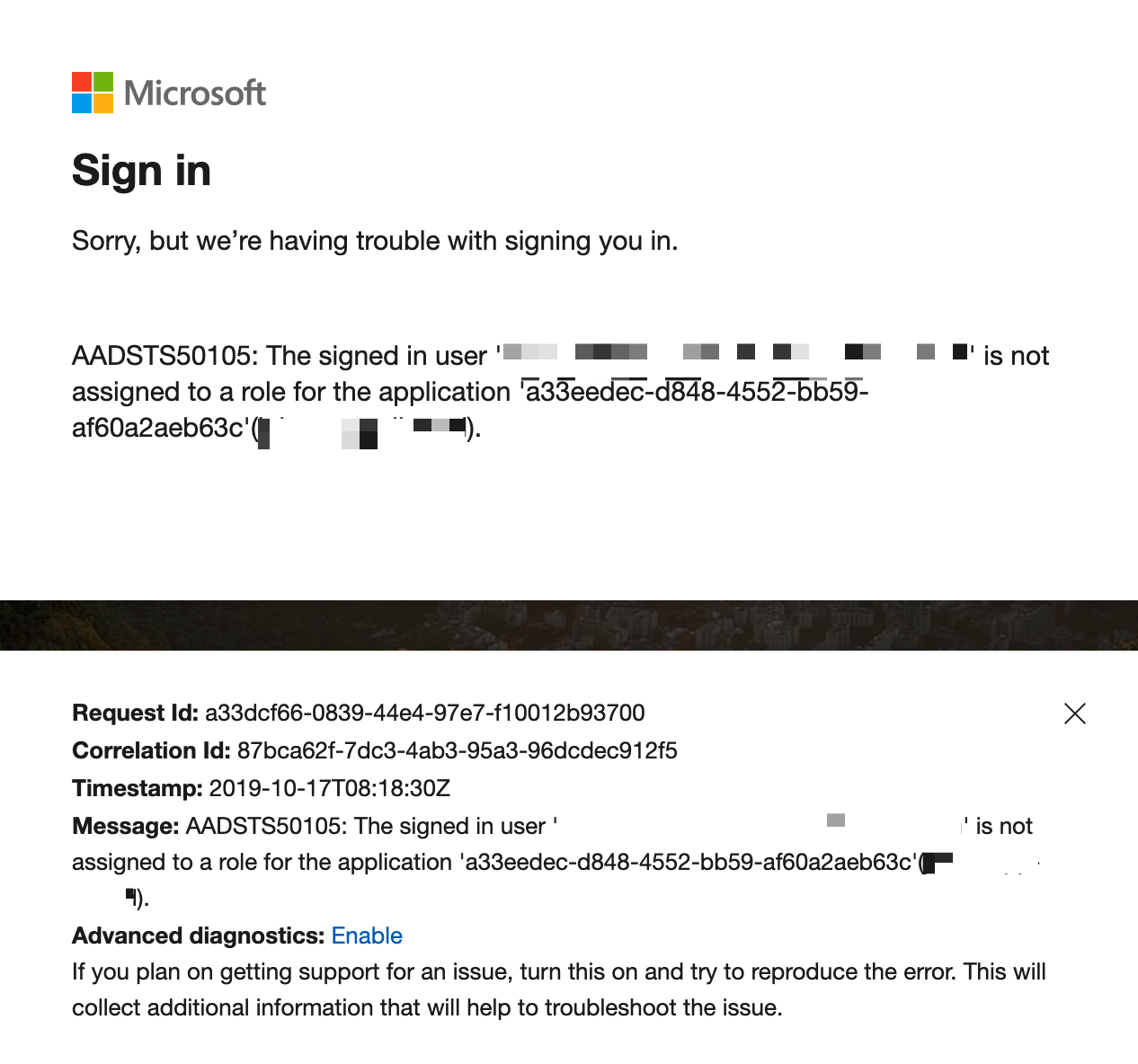
Solution
If you don't allow all users to access to SAML SSO via Azure (described in all of our Azure AD SSO setup guides,
i.e. here: Azure AD Enterprise app configuration), you need to add the user to the SSO app you've created.
In the below screenshot User assignment required is enabled (usually we recommend to disabled it)
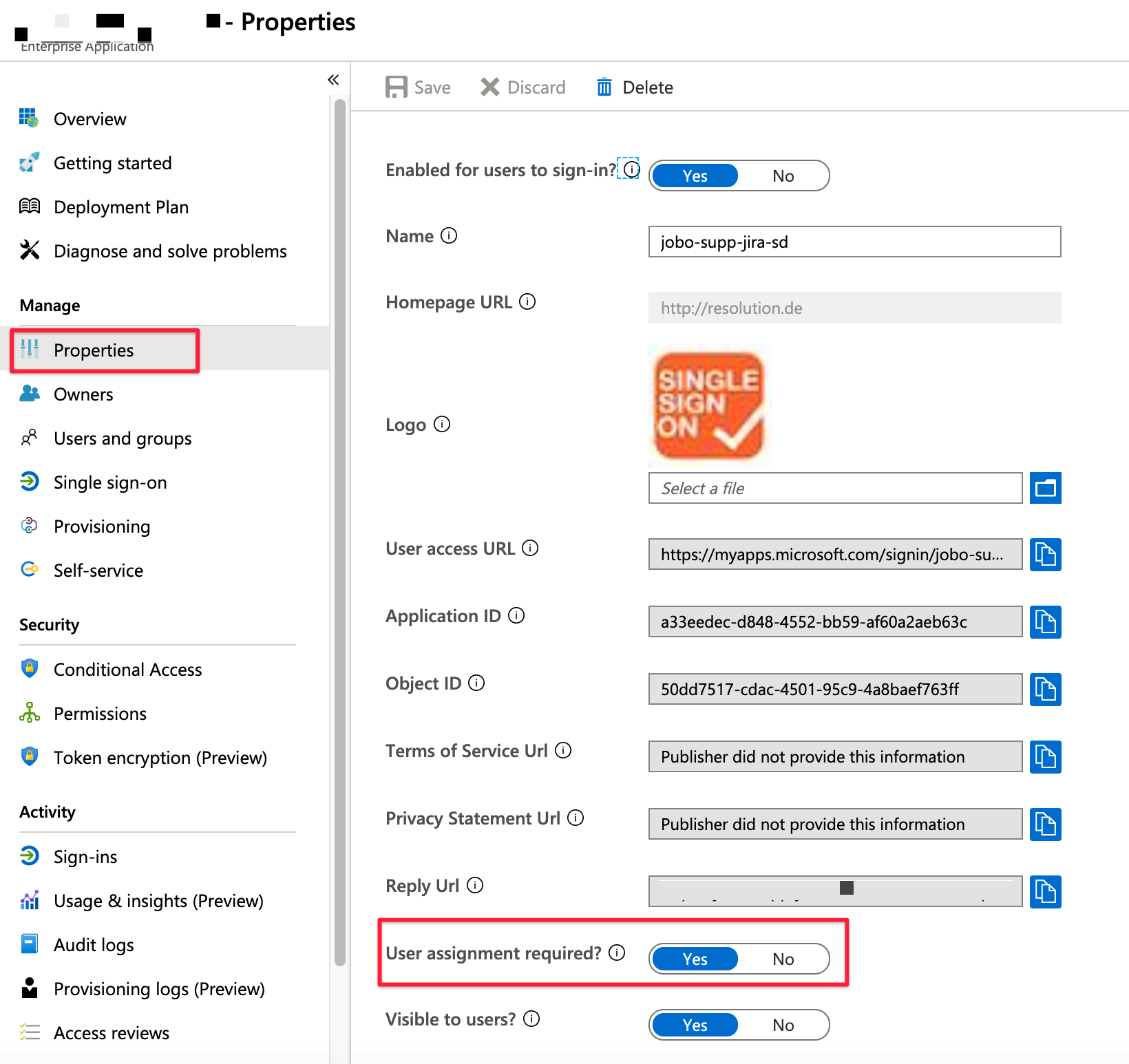
If you need to keep these settings, you'd need to assign the users via Users and groups
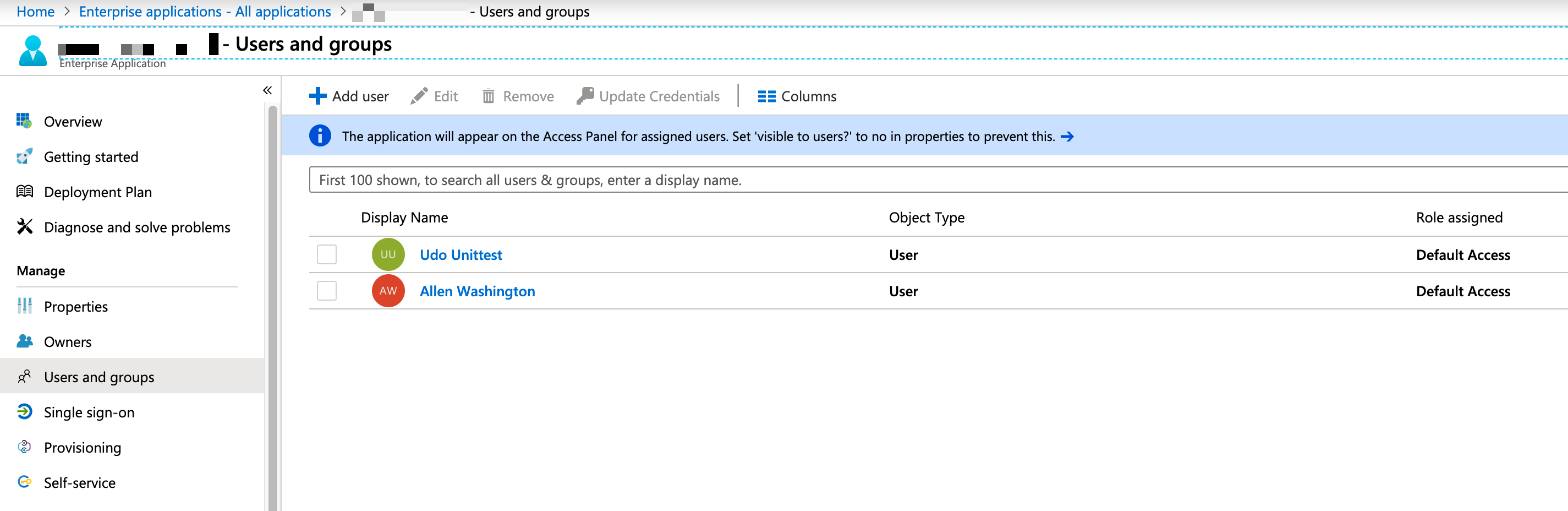
As this can become quite an effort when managing many users, Azure also allows that for groups, but not with every Azure AD subscription plan.
