WebSudo Authentication kills session
Problem:
Websudo authentication is successfully triggered. However, after clicking "Ok" in the confirmation dialog the error message "Sending confirmation failed" is shown. When this happens, the current session is terminated, forcing the user to authenticate again.
Reason:
The session cookie (usually called JSESSIONID) is sent by Confluence or Jira without the SameSite flag.
Actual browsers interpret this absent value as "Lax". This leads to the following behaviour:
In the pop-up window for additional authentication, the user is sent to the SAML Identity Provider;
After authentication, the IdP triggers the browser to send a POST request to the Atlassian application, following the SAML POST binding;
The browser does not send the cookie in the POST request because it's initiated by a 3rd party (the SAML IdP).
the Tomcat server underneath Jira/Confluence creates a new session ID and sets a new session cookie. This causes the current session to get lost.
Diagnosis:
Confirm within the first two minutes of a session if everything works. Afterward, it fails (with the SameSite = LAX default treating in Confluence).
Disable the SameSite enforcement in the Chrome browser, by entering the below in the address bar, choose “Disable” instead of “Default, then click on the “Relaunch” button:
chrome://flags/#same-site-by-default-cookies
This should work as a local workaround for each individual user
Workarounds:
Option 1: Configure Tomcat to send samesite="none"
This fix only works in Tomcat versions > 9.0.28 onwards. This is covered in the Bundled Tomcat with Confluence versions > 7.3.4 onwards.
This option is currently not working even with the latest Jira version. You can check which Tomcat version Jira runs on here
Tomcat, the application server underneath Jira and Confluence, can be configured to send cookies with samesite="NONE". To do this:
Edit <Jira/Confluence installation directory>/conf/context.xml
Include <CookieProcessor sameSiteCookies="none"/> to <Context>
- <Context>
- ...
- <CookieProcessor sameSiteCookies="none"/>
- ...
- </Context>
After restarting the application, the JSESSIONID cookie should be sent with samesite="none" and WebSudo should work as expected.
Option 2: Use our open-source plugin
You can use our open-source Jira/Confluence plugin that sets the cookie correctly from within the Atlassian application.
You can upload it via the UPM (Upload from URL) and use the download URL to the latest version.
Option 3: Configure Reverse Proxy to rewrite set-cookie headers
Most reverse proxies allow rewriting request headers. The set-cookie-header should be rewritten to add the samesite="none"-flag when sending the JSESSIONID cookie.
Option 4: Configure IdP to send the SAML response using REDIRECT binding
The session cookie is preserved correctly if the SAML response is sent from the IdP with HTTP GET instead of POST. This can be achieved by configuring the IdP to use REDIRECT binding if supported. In this case, the setting "Protocol Binding" under Request settings in the IdP configuration of the SAML-plugin should be set to REDIRECT:
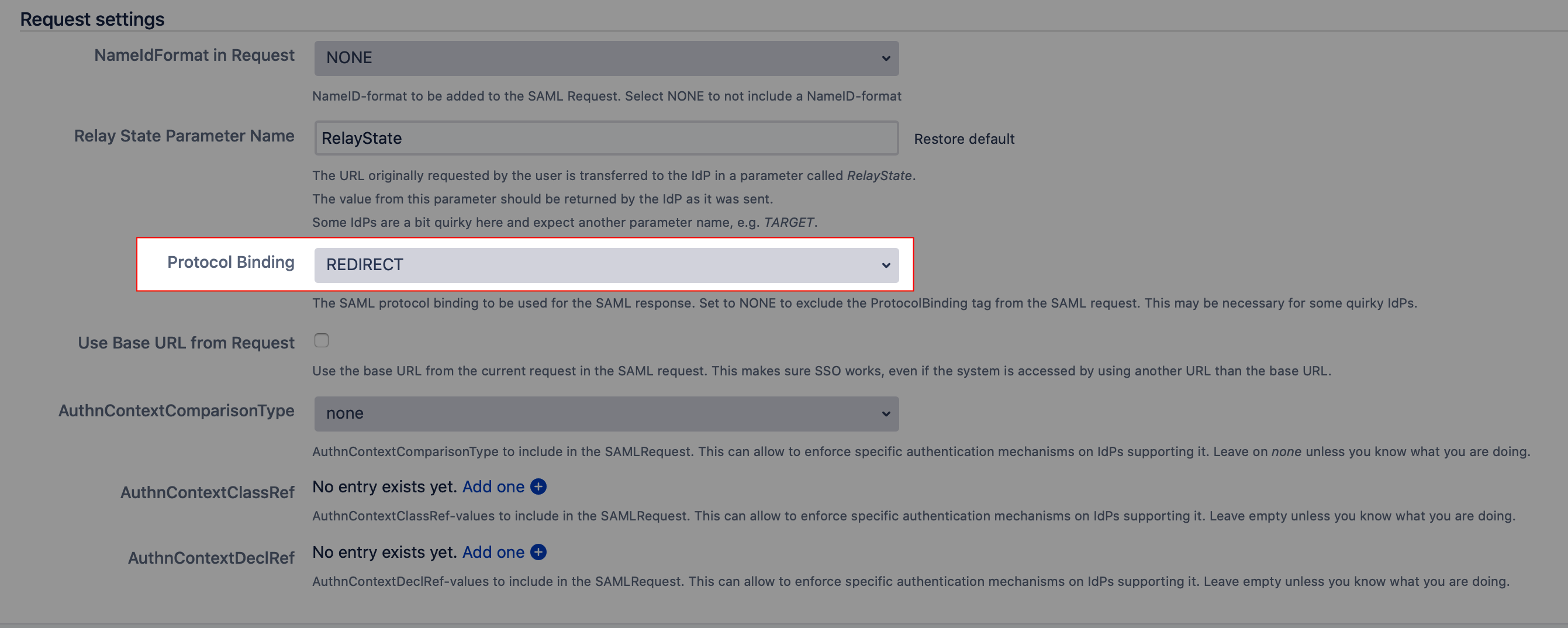
This may be not supported by the IdP - some IdPs will send the response with POST binding no matter what is set here.
