Important Update Effective February 1, 2024!
Due to recent changes in Jira and Confluence, we've made the tough decision to discontinue the OpenID Connect (OIDC)/OAuth app and no longer provide new versions for the newest Jira/Confluence releases as of January 31, 2024.
This is due to some necessary components no longer shipping with Jira/Confluence, which would require some extensive rewrites of the OIDC App.
Important Update! This app will be discontinued soon!
Due to recent changes in Jira, which no longer ships with some components required for our Read Receipts app to run, we've made the tough decision to discontinue the app, as of Februar 5, 2025.
Important Update! This app will be discontinued soon!
We've made the tough business decision to discontinue the app, as of January 11, 2025.
OneLogin with Just-In-Time Provisioning
Goal
After completing this setup guide, you will have OneLogin with Just-in-Time Provisioning and your Atlassian product for the SAML SSO for Atlassian Server or Data Center app set up. Additionally, you will enable the SSO redirection and test SSO.
Prerequisites
To use the SAML SSO app for Atlassian Server or Data Center with OneLogin, you need the following:
A OneLogin subscription
A (trial) subscription for the SAML SSO app
Admin access to your Atlassian product
Video Guide
Step-by-Step Setup Guide
Install the SAML SSO App for Atlassian Data Center or Server
In your Atlassian product, open the in-product marketplace as described in the Atlassian documentation.
Search for "resolution saml" and click "Install" for SAML Single Sign On (SSO) by resolution Reichert Network Solutions GmbH.
After the installation is complete, click on Manage, then choose Configure.
Now, you are on the Add-on / app configuration page and the first step of the setup wizard will appear.
First Steps - Wizard
After you clicked "Configure", the wizard will be triggered. If not, or if you want to add another Identity Provider (IdP) to your existing configuration, click on "+ Add IdP". This guide assumes, that you there is no IdP configured.
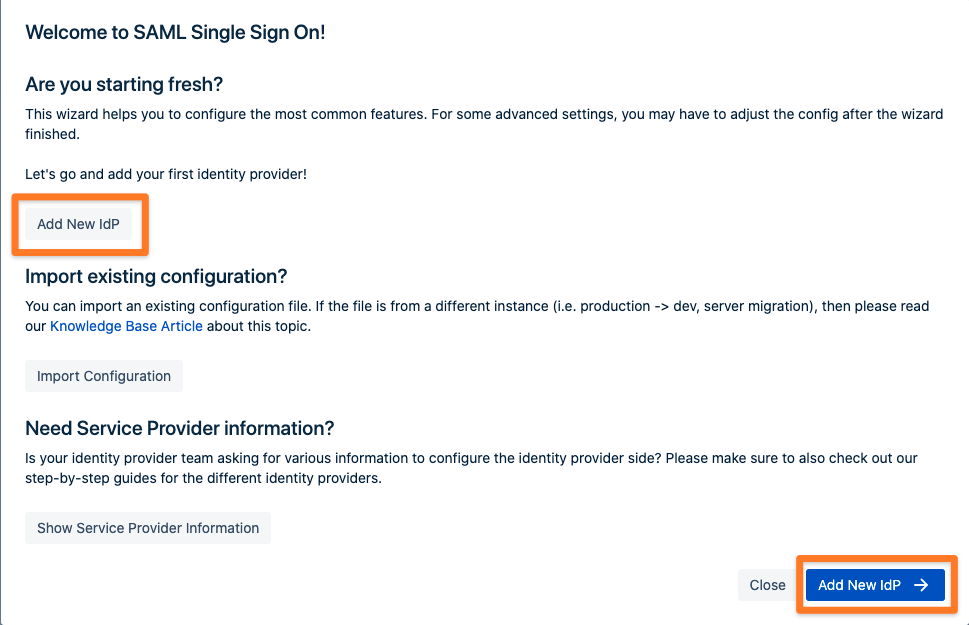
The wizard greets you with information, click on "Add new IdP" to proceed.
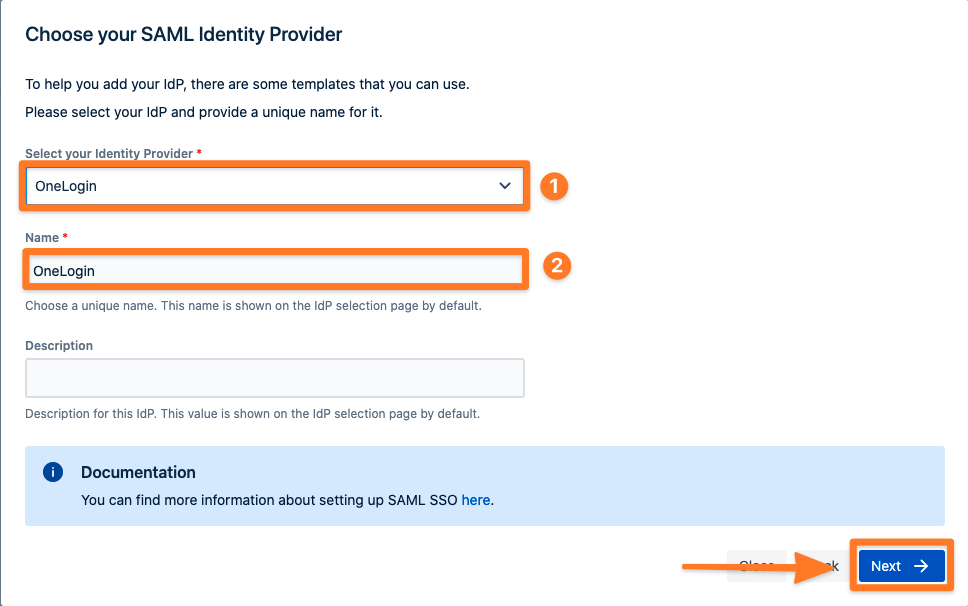
For the IdP Type, choose "OneLogin" then add a name. You can also optionally add a description. Click on "Next" to continue.
In the next step, you will configure OneLogin. Please keep this tab open or copy the information.
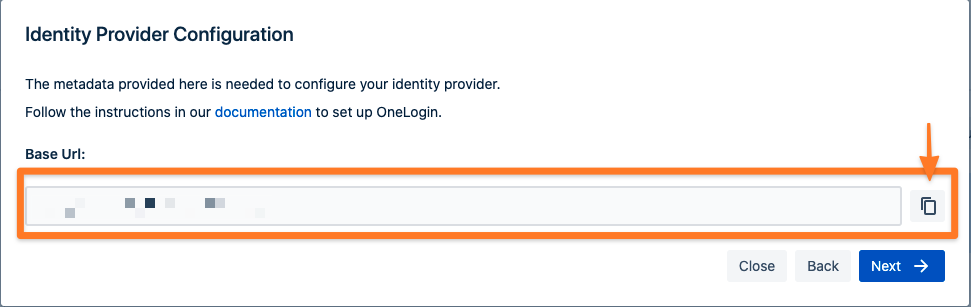
Create and Configure a OneLogin App for SAML SSO for Atlassian Data Center or Server
Adding an Application for the SAML SSO App
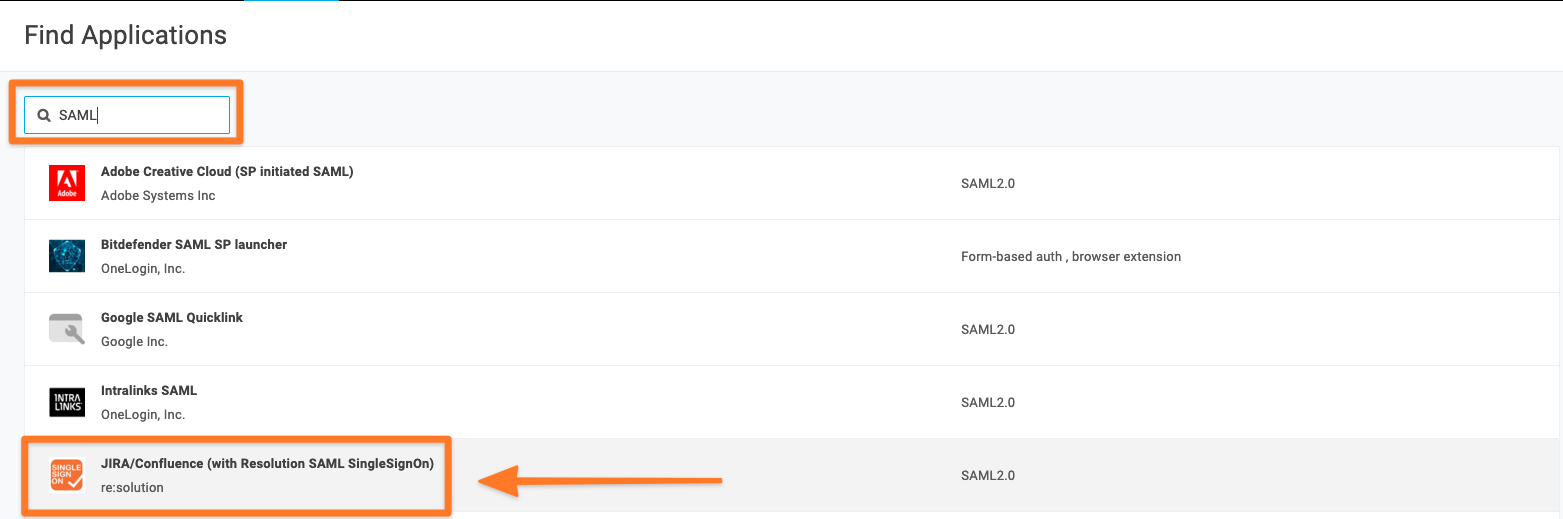
Log into the OneLogin Portal as an admin. Go to Applications > Add Apps, search for Resolution SAML, and select it.
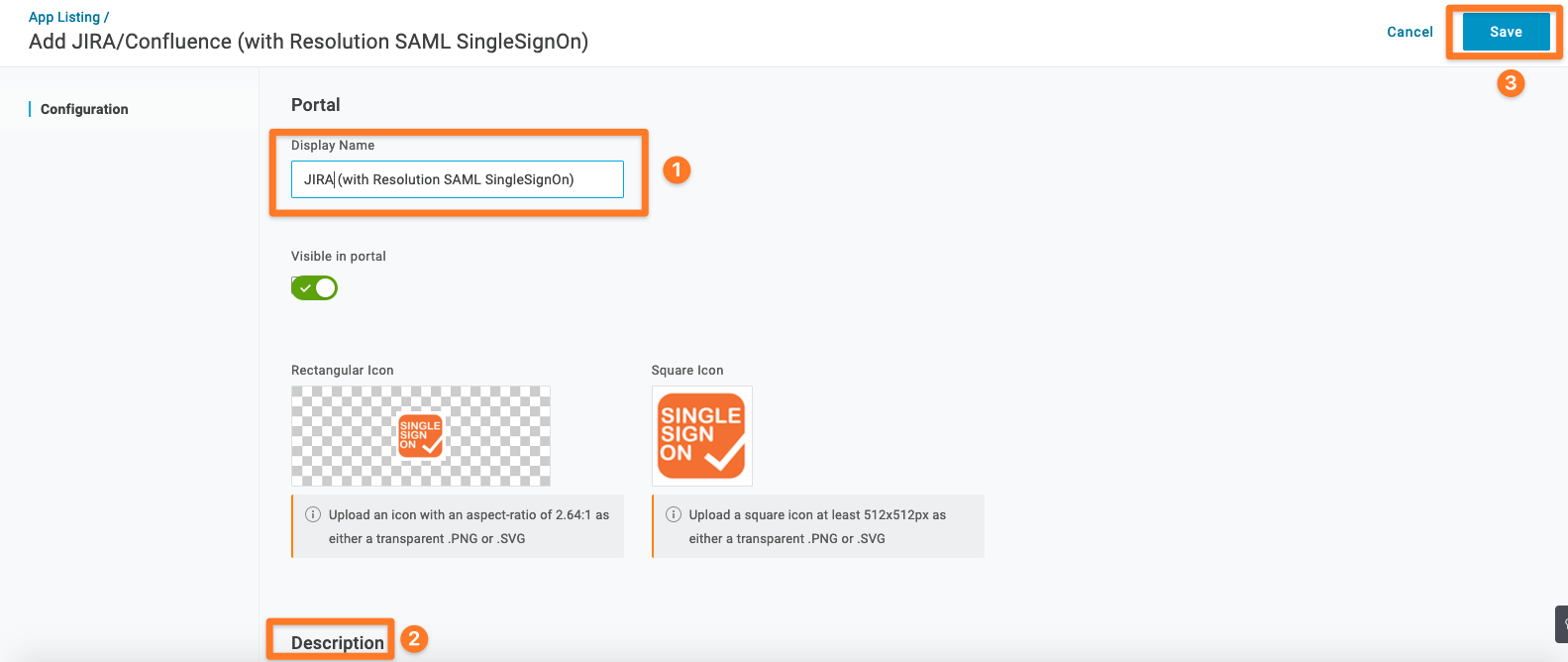
On the initial Configuration tab, click Save to add the app to your Company Apps and display additional configuration tabs. When you click Save, the Info tab appears.
Go to the Configuration tab and enter your Base URL (you only need to enter your subdomain). Click Save.
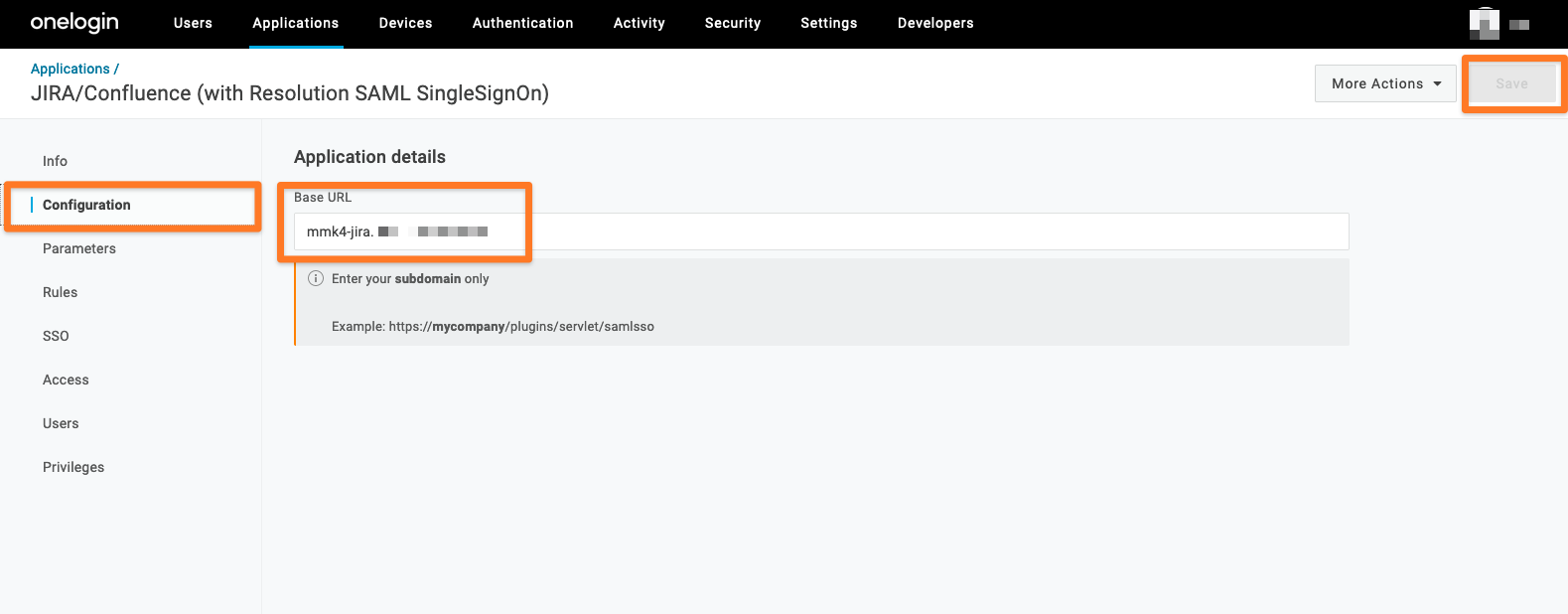
Afterwards, the following sections will be checked:
Parameters
Access
In our test setup, we will not change the value. The values will be sent during the SAML flow, and in our Just-in-Time setup we will use the values to create or update a user.
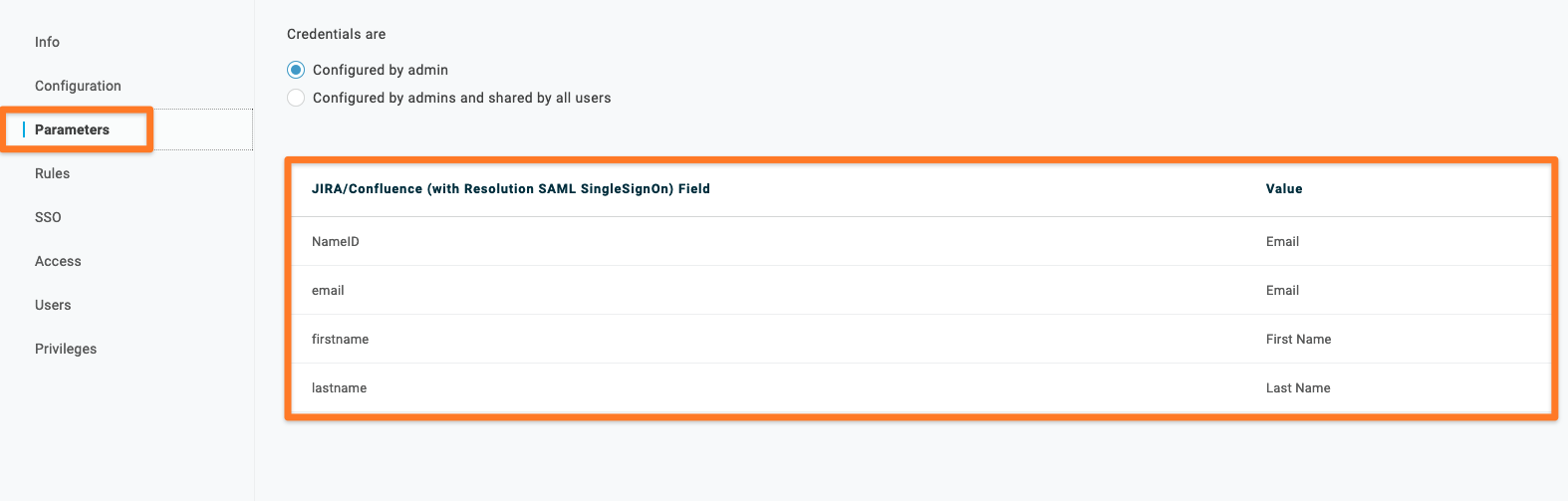
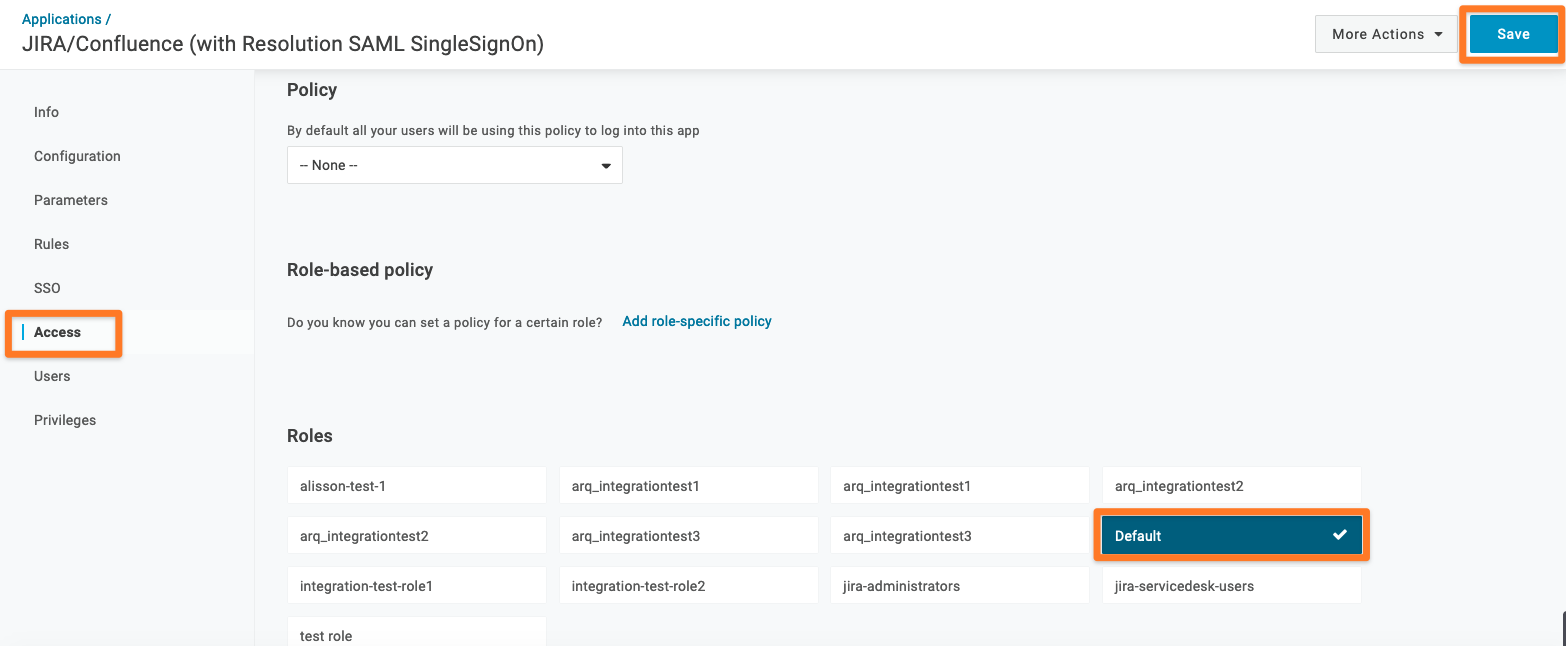
One important configuration part is the Access. You have the possibility to allow the access to the application on a Role-based policy. In our documentation, we will use the Role → Default (this means that everyone who is a part of the Default role has access to the application).
The next step is to copy the SAML Metadata. Just go to More Actions → SAML Metadata. It’s enough to hover over SAML Metadata, do a right mouse click and choose Copy Link Location.
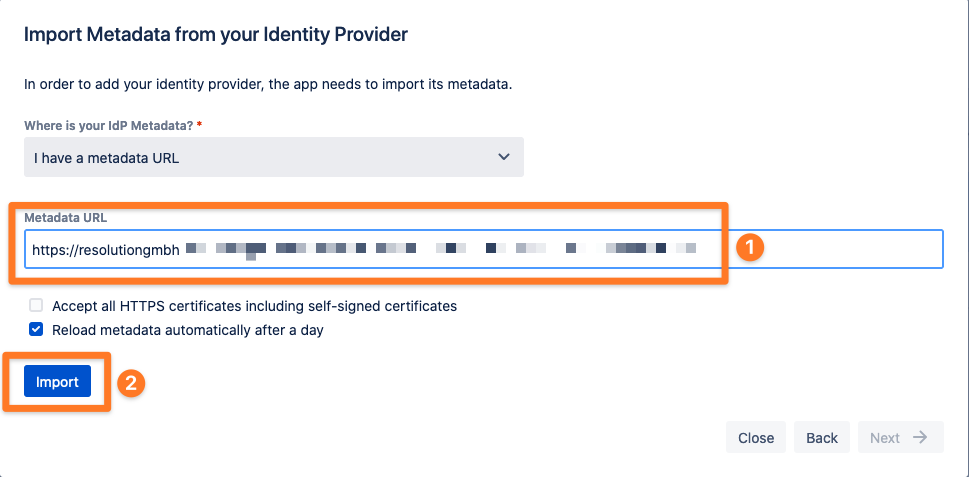
Now go back to the SAML SSO configuration, paste your Metadata URL and click Import. After a successful import, click Next.
Now, you have the possibility to configure the user ID attribute and its transformations options. In our setup, the user ID is sent in the NameID attribute of the IdP in a format that matches the one in the Atlassian product, so we don’t need to change anything here.
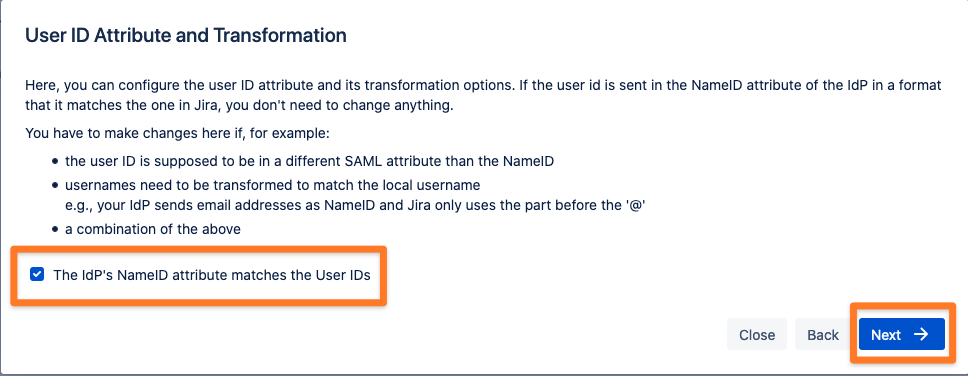
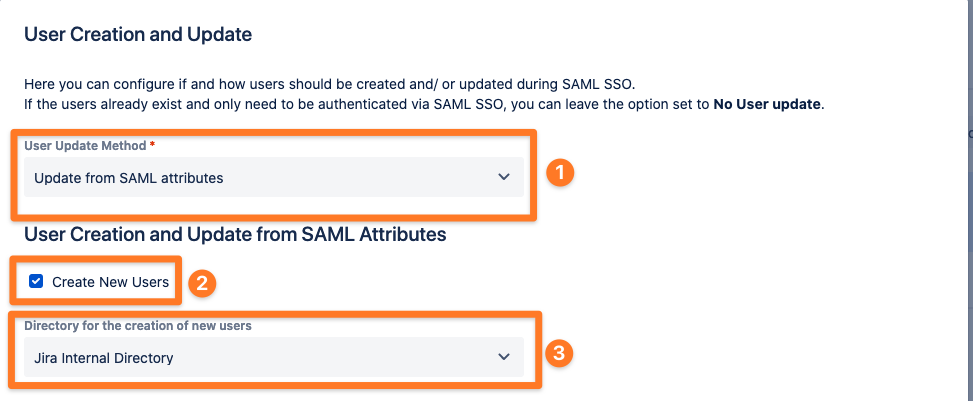
In this tutorial, we will create and update users from SAML attributes (we call this user provisioning method Just-In-Time Provisioning). Please choose ‘Update from SAML attributes’ as User Update Method.
Next to the User Update Method, enable the ‘Create New Users’ checkbox (based on the SAML attributes, SAML SSO will create a new user in your Atlassian instance if the user does not already exist).
You also have to decide in which directory SAML SSO will create the new user account. In this tutorial, all new users will be created in the default Jira Internal Directory.
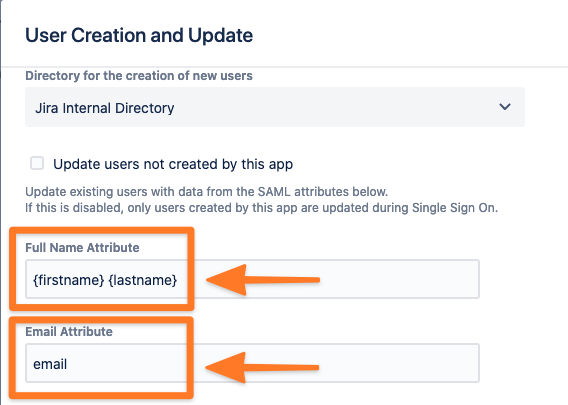
Then you need to configure a couple of attributes to be able to create/update the users. As a minimum, you need to add the Full Name and Email Attributes. These are already filled in based on the default OneLogin Parameters configuration, but you can change them if needed according to the values of your OneLogin Parameters configuration (you need to combine the firstname and the lastname to get the Full Name Attribute).
Our plugin can also take care of the group management. In this tutorial, we will always assign any newly created user to the group ‘jira-users’. This will give the user application access to the Atlassian Jira instance.
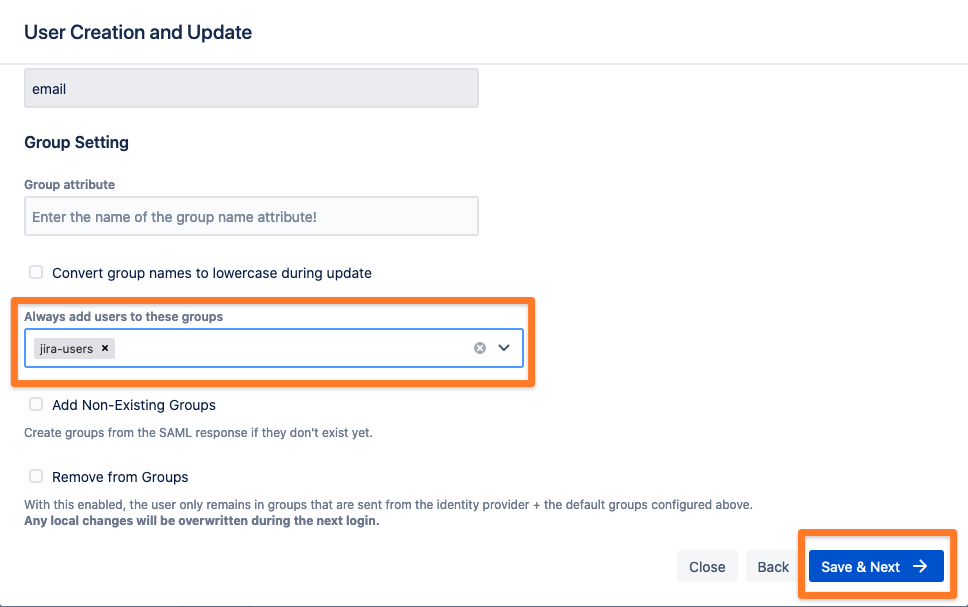
Now, you can save the configuration by clicking on the ‘Save & Next’ button.
Test
It’s time to test your settings. Our plugin will create a tracker link to test your configuration. Please click ‘Start’ and follow the instructions.
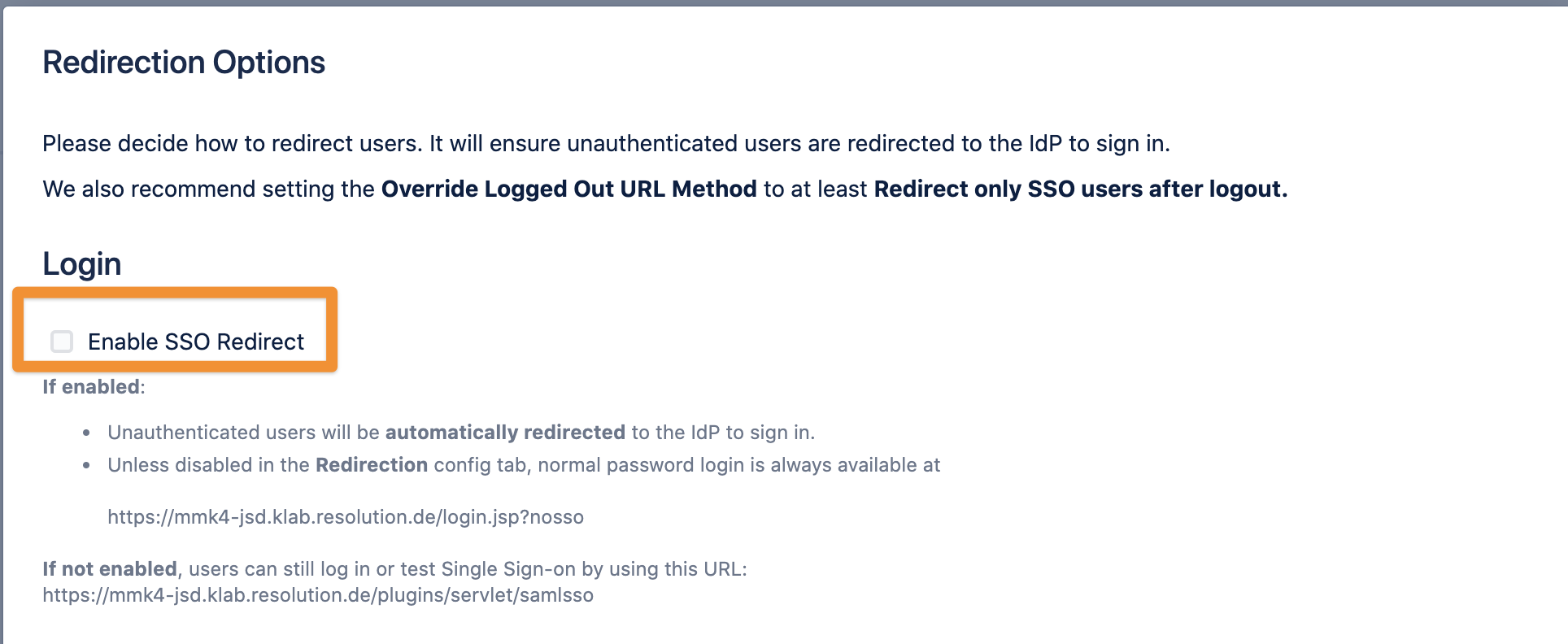
After a successful test, you can enable the ‘Enable SSO Redirect’ checkbox. From now on, every unauthenticated user will be automatically redirected to OneLogin to sign in.