Full Logging
If you get stuck during configuration or need help, please either create a support case via https://www.resolution.de/go/support or book a free screen share meeting via https://www.resolution.de/go/calendly. We are happy to help you with your setup.
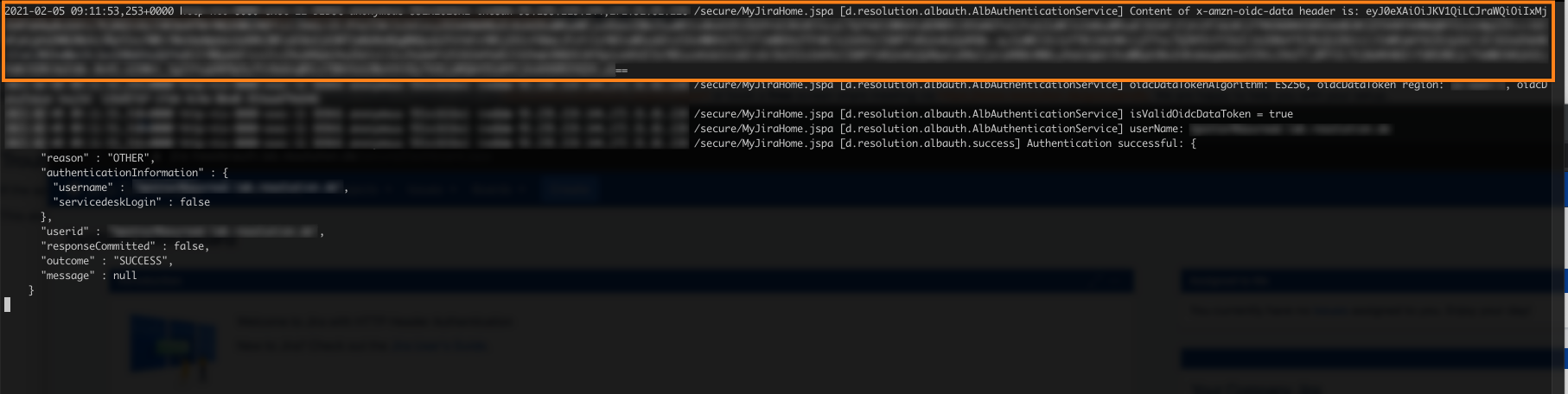
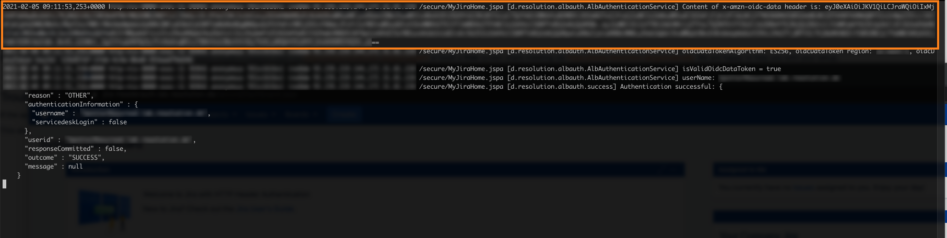
If the app is not working as expected, you turn on debug logging for the app by listening for de.resolution.albauth.
This also logs the value of the token used to extract the username from. With websites like https://jwt.io, this token can be made readable for troubleshooting:
Marked with orange are the used token from the configuration, x-amzn-oidc-data, and its value which starts with eyJ... and ends with ==. Copy this value.
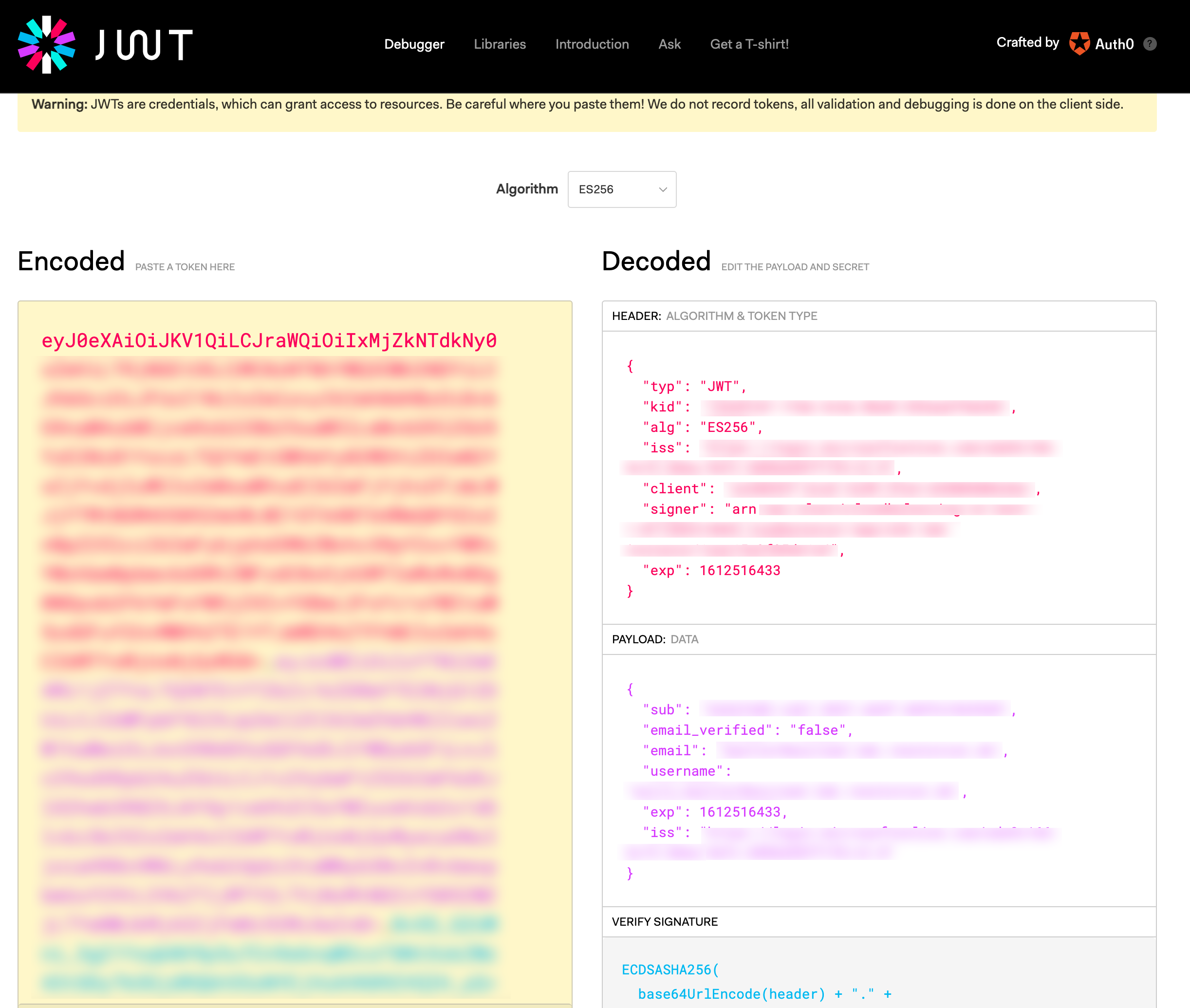
Go to a website like https://jwt.io. This allows you to make the token human-readable:
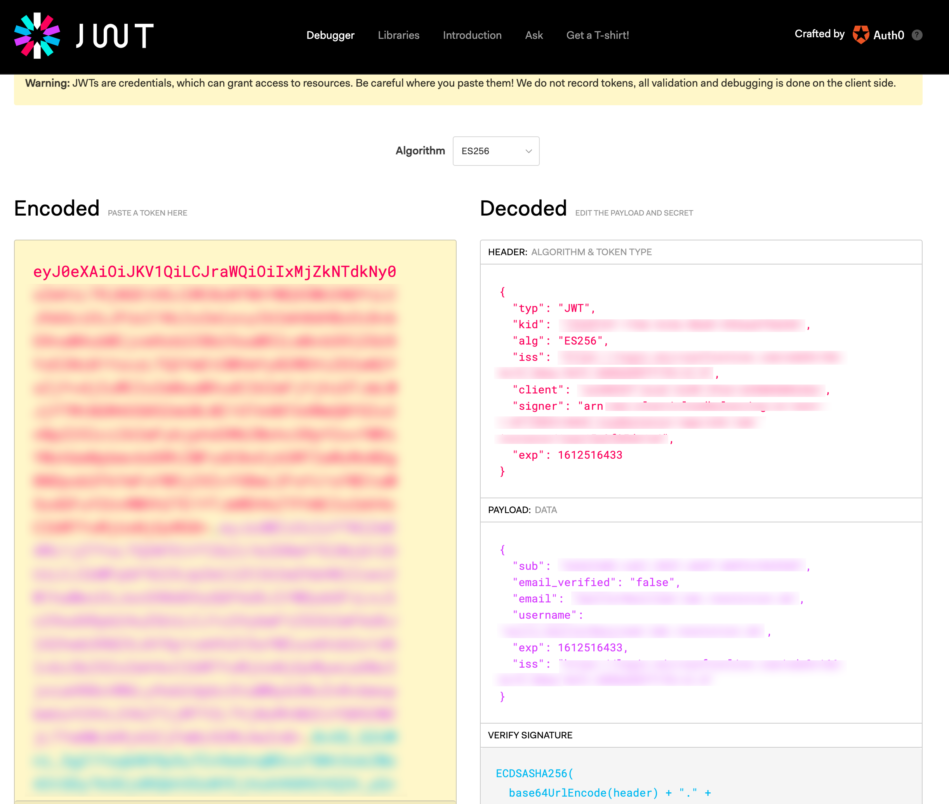
In case of a not working authentication, make sure that the Username Claim (e.g. upn or email) is part of the decoded token. If not, you must either change the used token, adjust your identity provider to send it, or choose a different Username Claim from the decoded token.