JumpCloud With Just-In-Time Provisioning
Goal
After completing this setup guide, you will have a setup for JumpCloud as Identity Provider with Just-In-Time Provisioning and your Atlassian product for the SAML SSO app. Additionally, you will enable the SSO redirection and test SSO.
Prerequisites
To use the SAML SSO app with JumpCloud, you need the following:
A JumpCloud admin account
A (trial) subscription for the SAML SSO app
Admin access to your Atlassian product
Step-By-Step Setup Guide
Install The SAML SSO App
In your Atlassian product, open the in-product marketplace as described in the Atlassian documentation.
Search for "resolution saml" and click "Install" for SAML Single Sign On (SSO) by resolution Reichert Network Solutions GmbH.
After the installation is complete, click on "Manage", then choose "Configure".
Now, you are on the Add-on/app configuration page, and the first step of the setup wizard will appear.
First Steps - Wizard
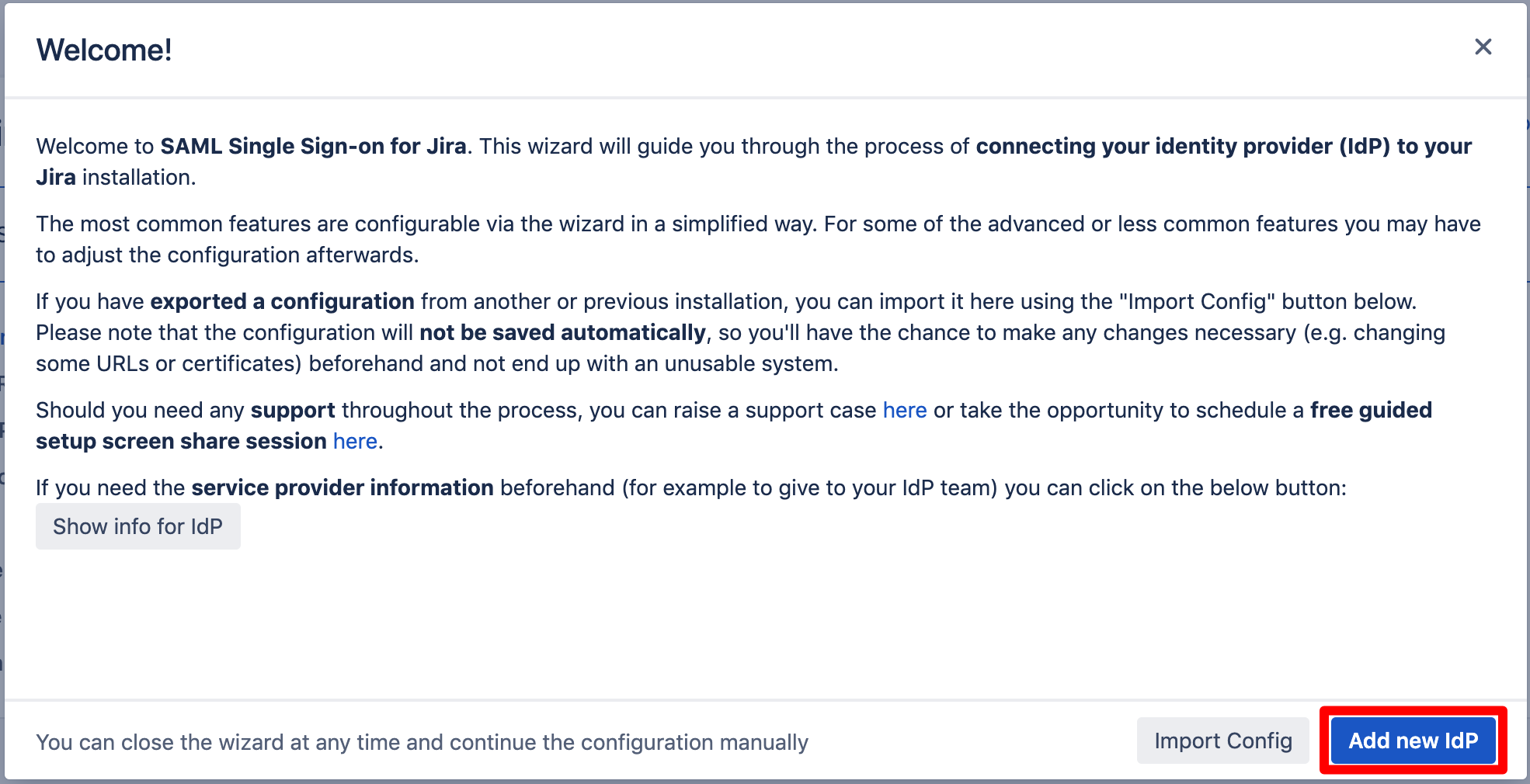
After you click "Configure", the Wizard will be triggered. If not, or if you want to add another Identity Prover (IdP) to your existing configuration, click on "+ Add IdP". This guide assumes, that there is no IdP configured.
The Wizard greets you with information, click on "Add new IdP" to proceed.
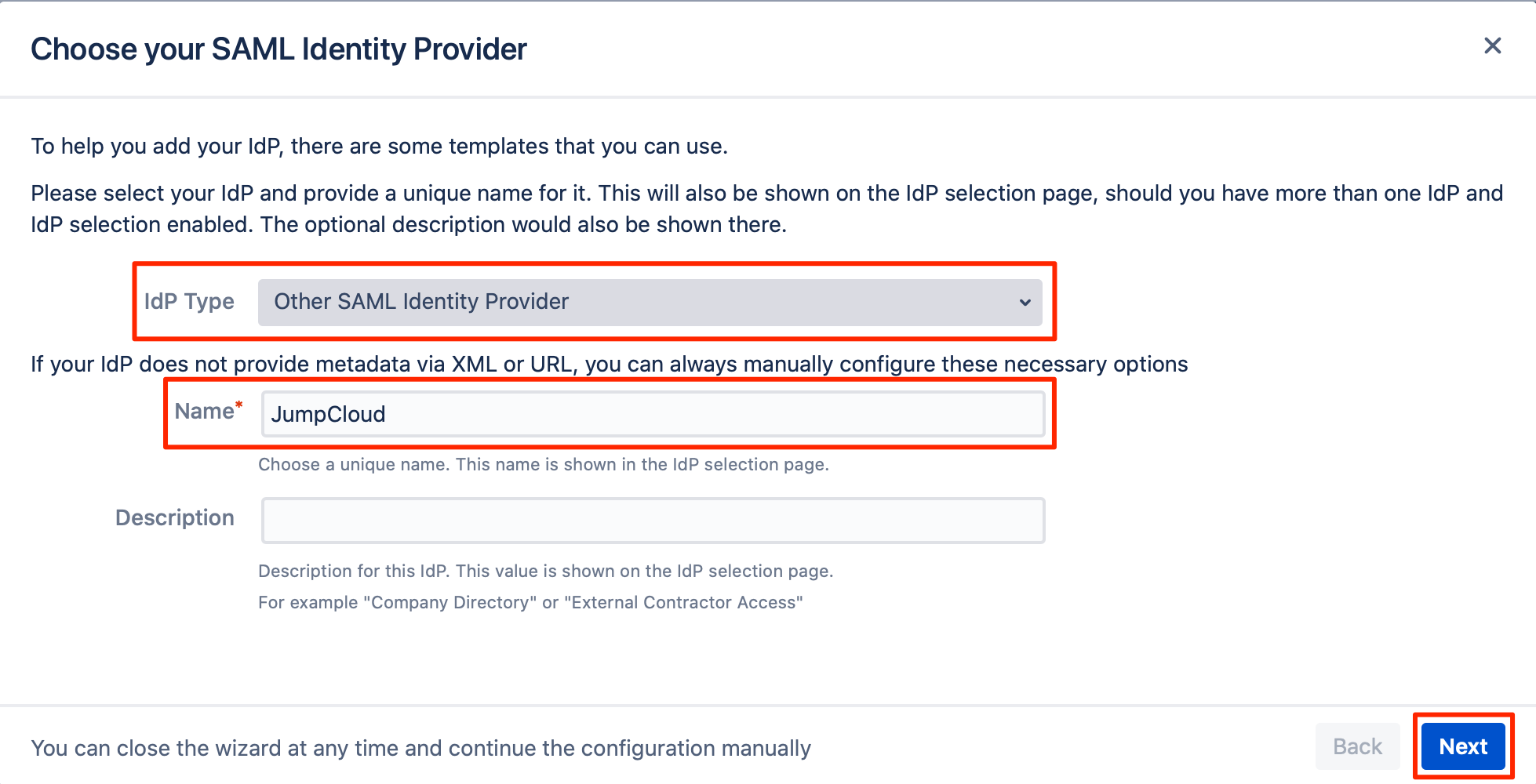
For the IdP Type, choose "Other SAML Identity Provider", and enter a name in the Name field.
You can also enter a description, but it's not mandatory. Click on "Next" to continue.
Right-click on the URL in the Metadata URL field, and download the metadata XML file.
In the next step, you will configure JumpCloud Identity Provider. Please keep this tab open or copy the information.
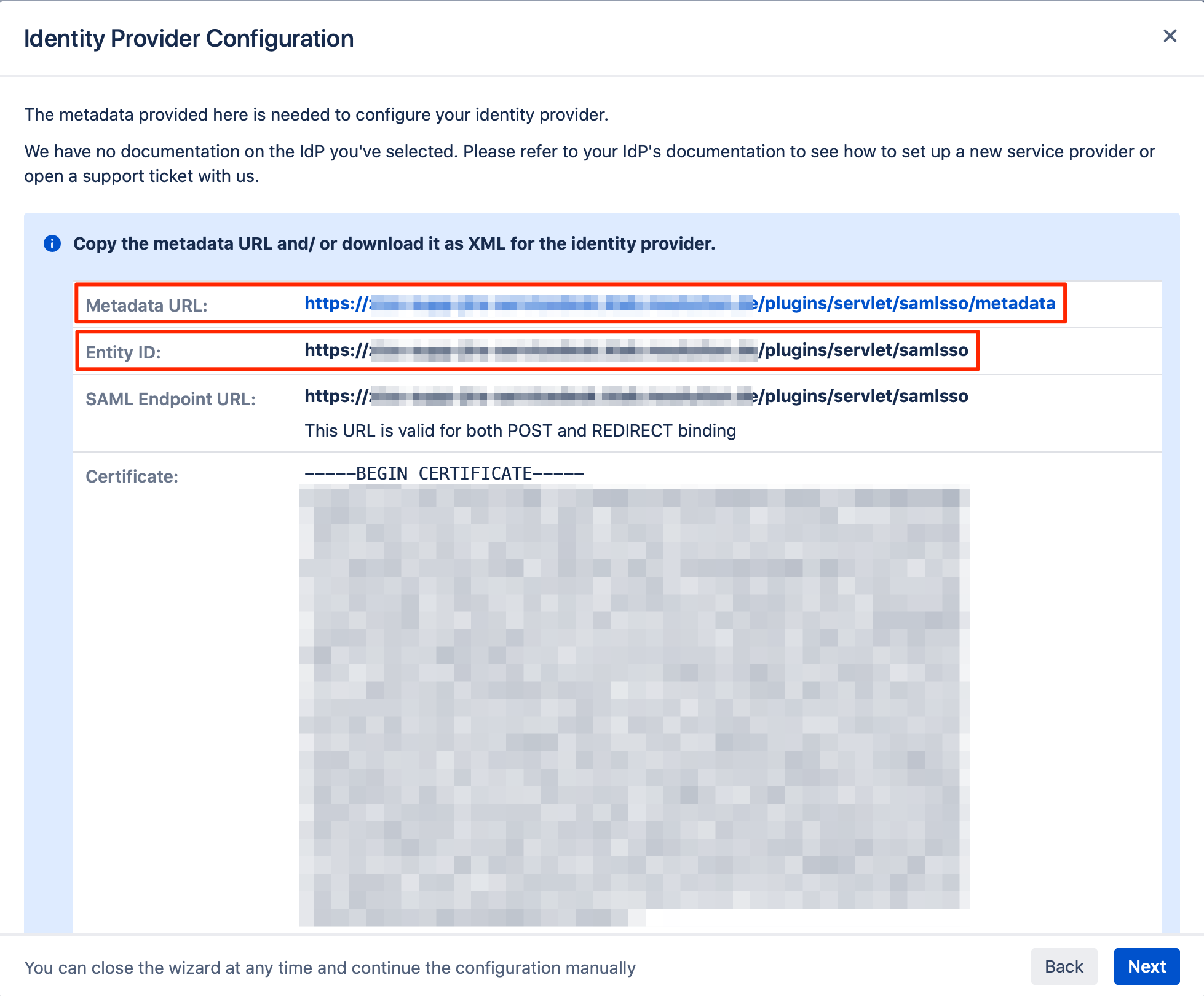
Configure JumpCloud As IdP For SAML SSO
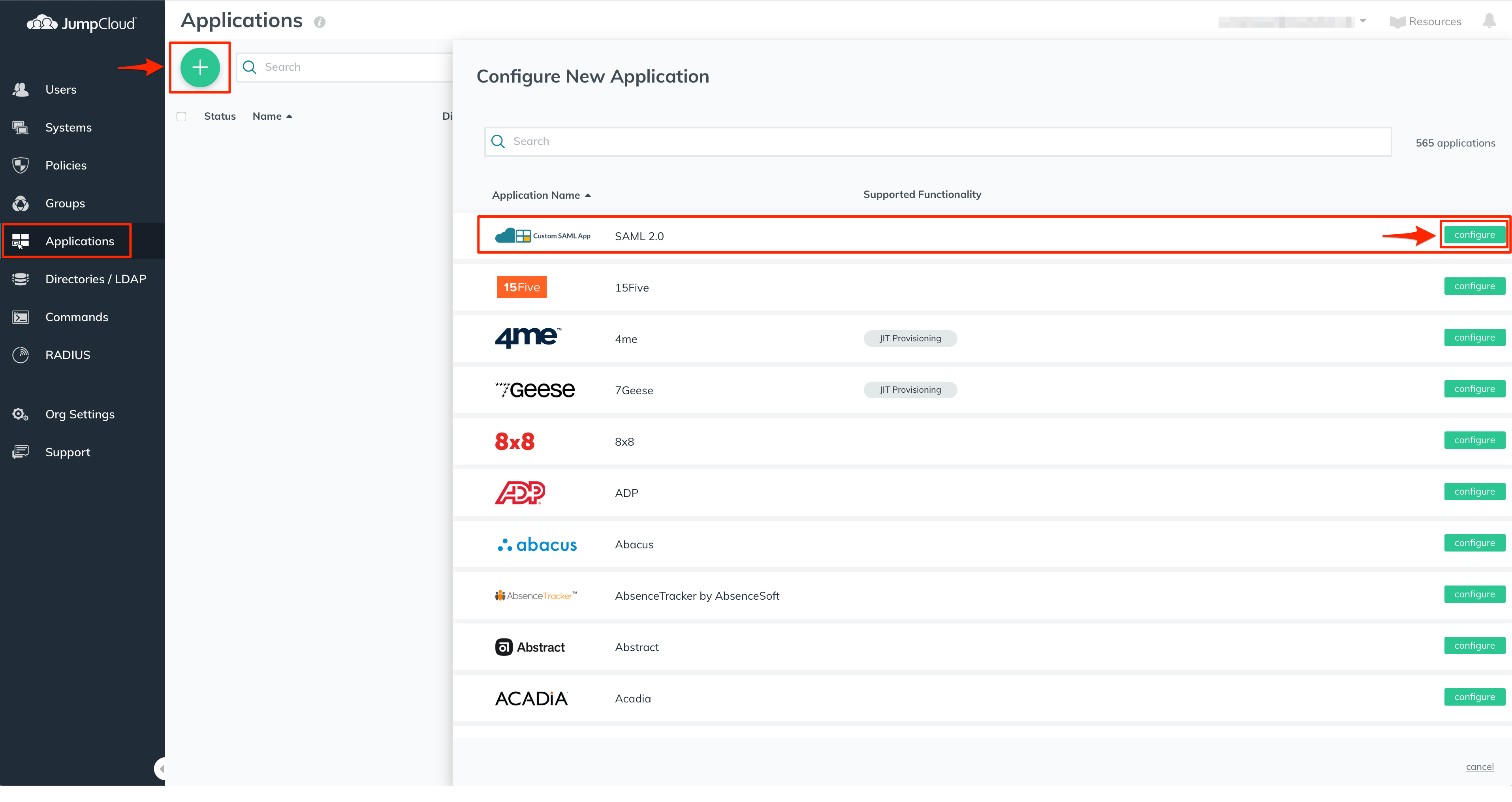
Navigate to the "Applications" page, and click on the + button to configure a new application.
Choose the "Custom SAML App", which should be the first option in the app list, and click on the "configure" button.
In the "Display Label" field, add a name for your application.
Click on the "Upload Metadata" button in the "Service Provider Metadata" field, and upload the metadata XML file that you've downloaded earlier from the plugin.
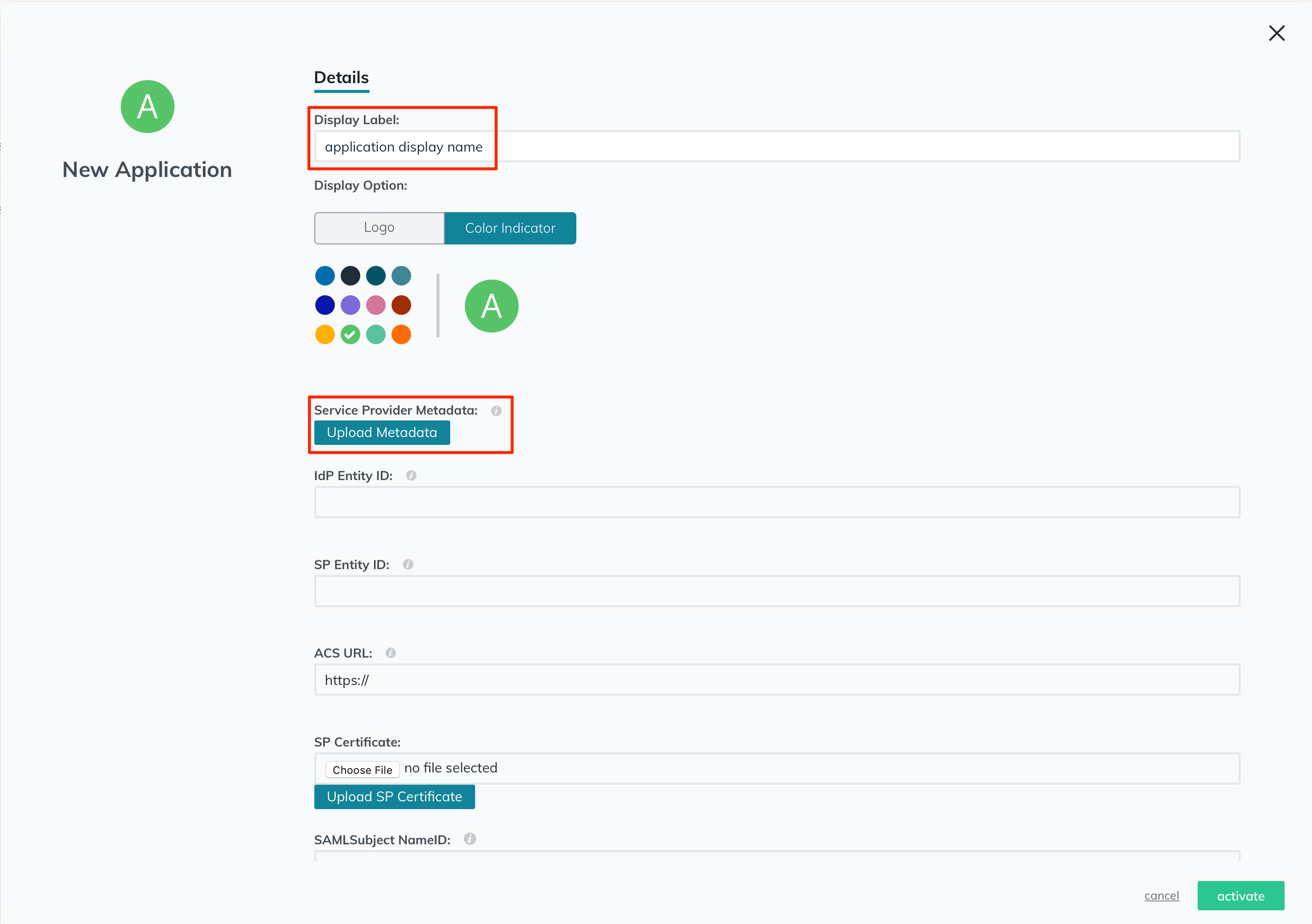
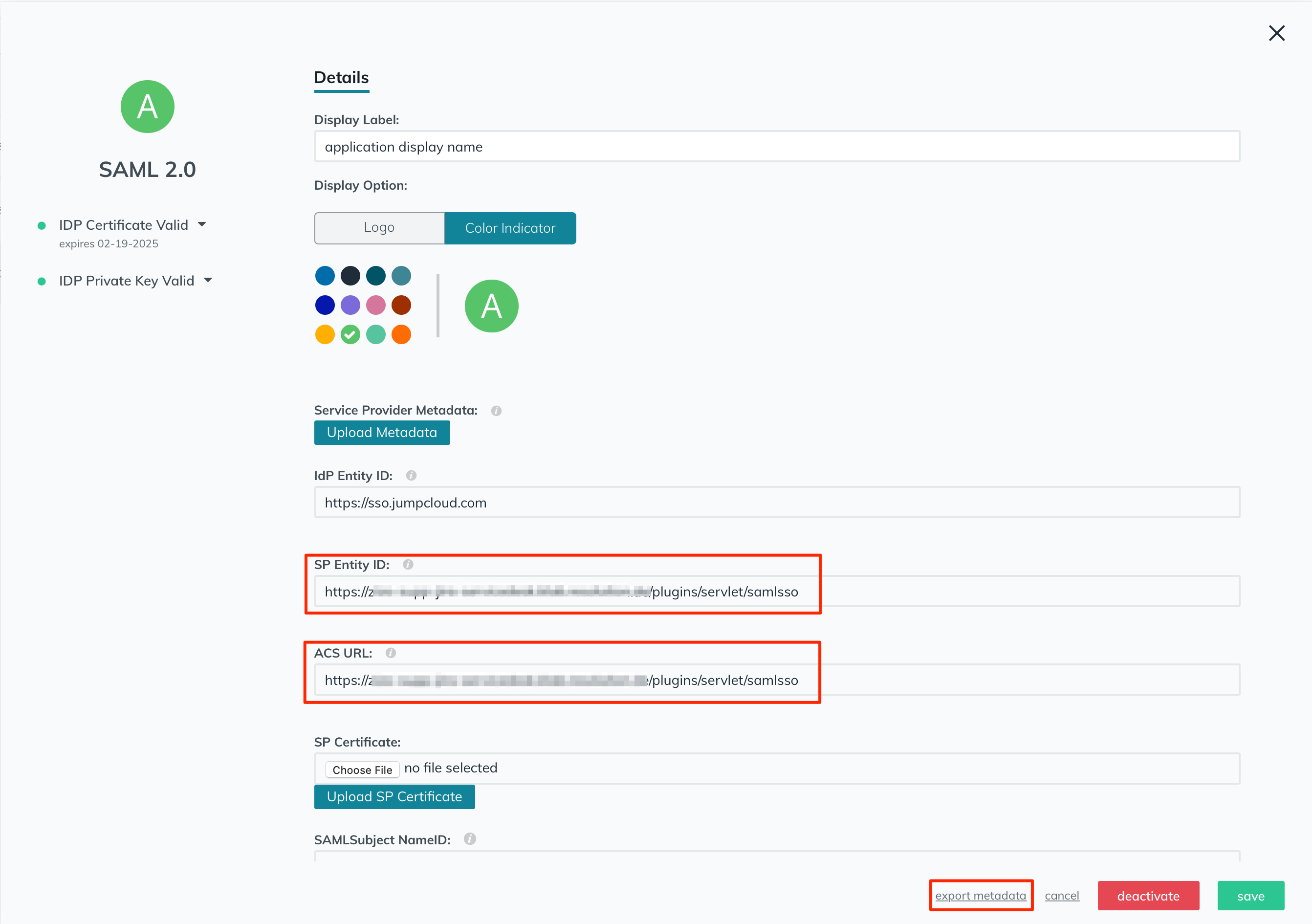
Please note that after uploading the metadata XML, the content (SP Entity ID, ACS URL,...) will not be displayed in the current window until you click on the activate button, which we're going to do later after completing the other required fields.
You should see a notification popup when the metadata is uploaded and read successfully.
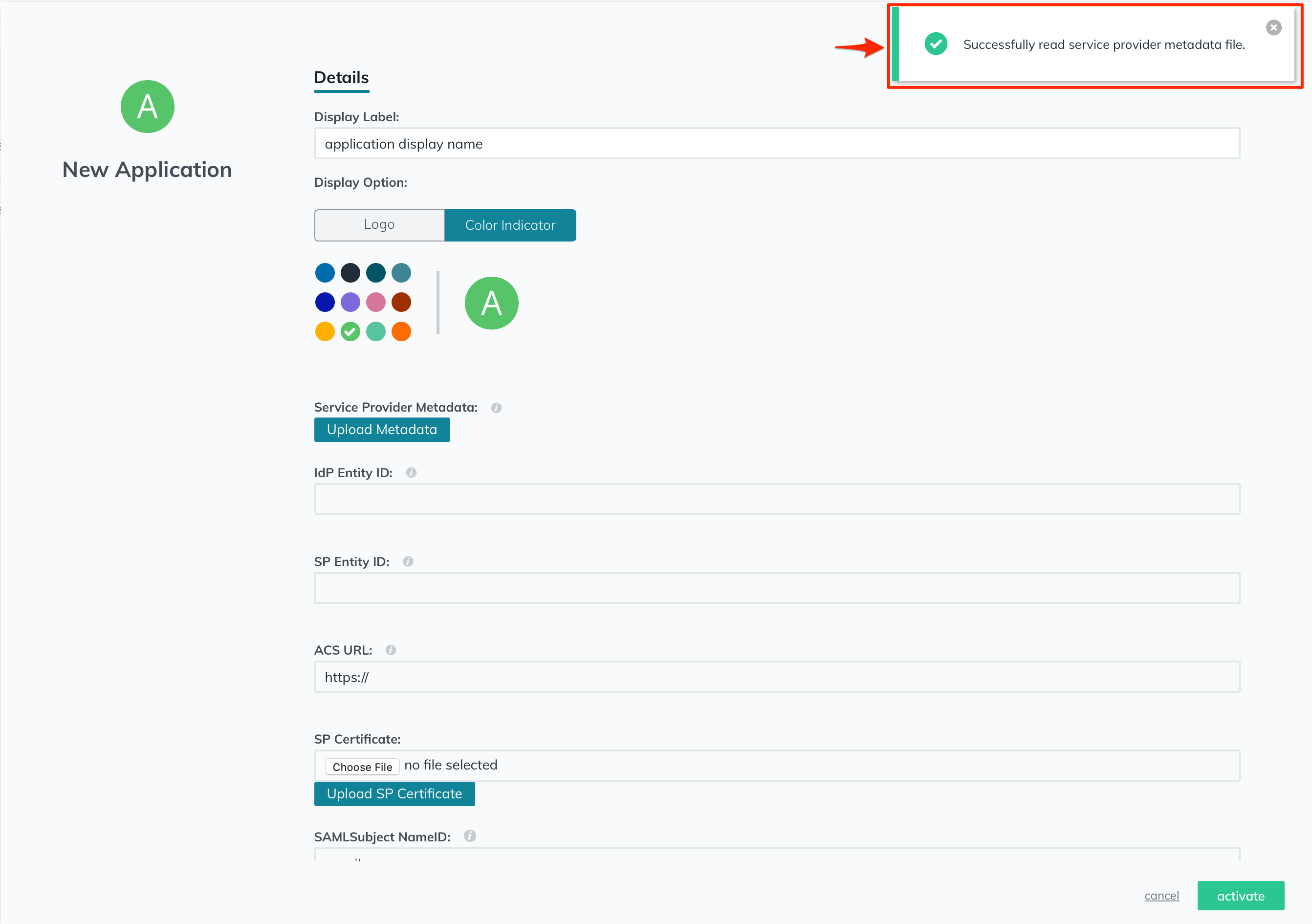
Enter the "IdP Entity ID": https://sso.jumpcloud.com
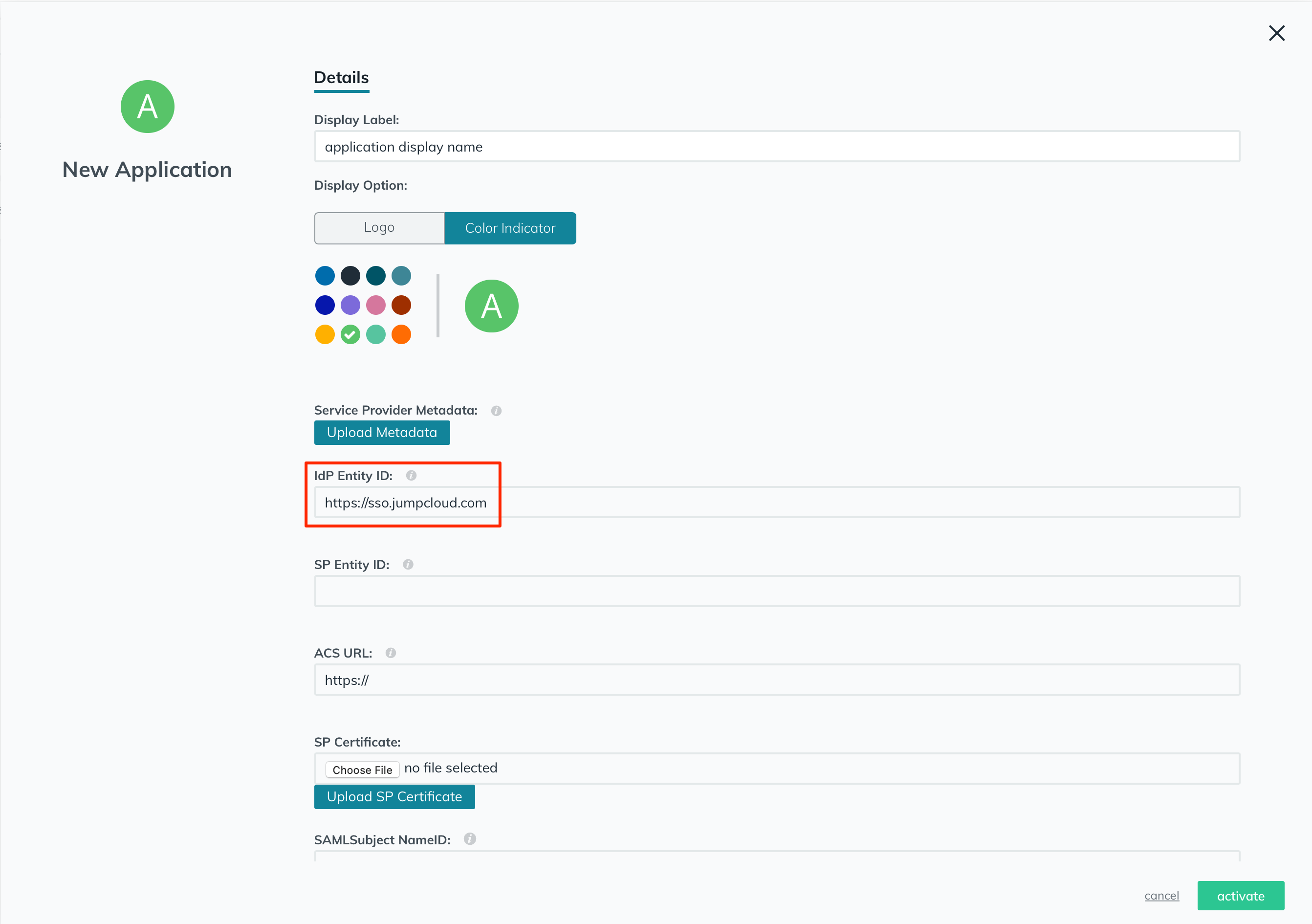
In the "SAMLSubject NameID" field, choose "username" from the dropdown list.
Keep the "SAMLSubject NameID Format" with the default option chosen: "urn:oasis:names:tc:SAML:1.0:nameid-format:unspecified".
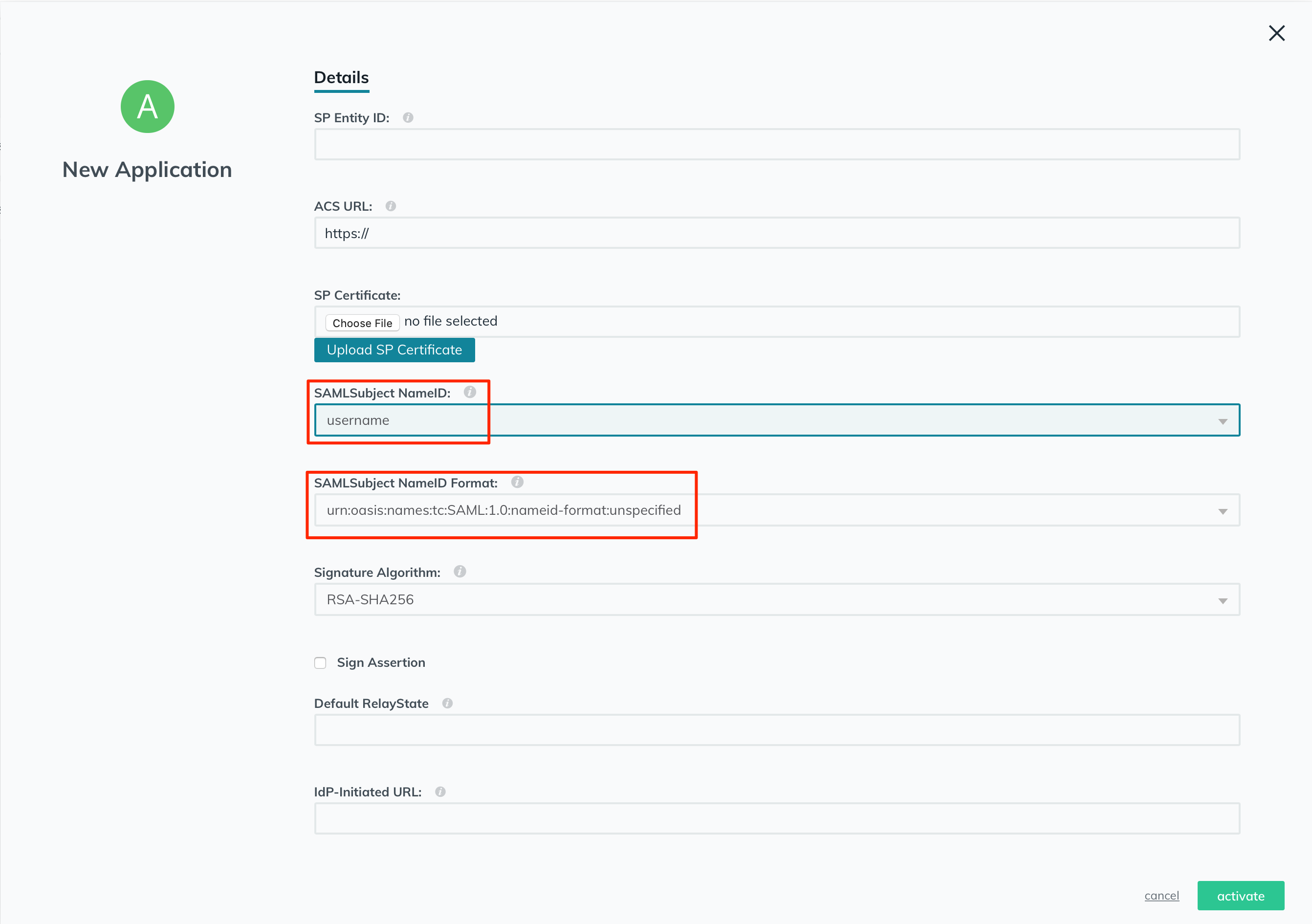
In the "IdP URL" field, enter a unique name in the text field, so it would be the unique IdP URL for this application.
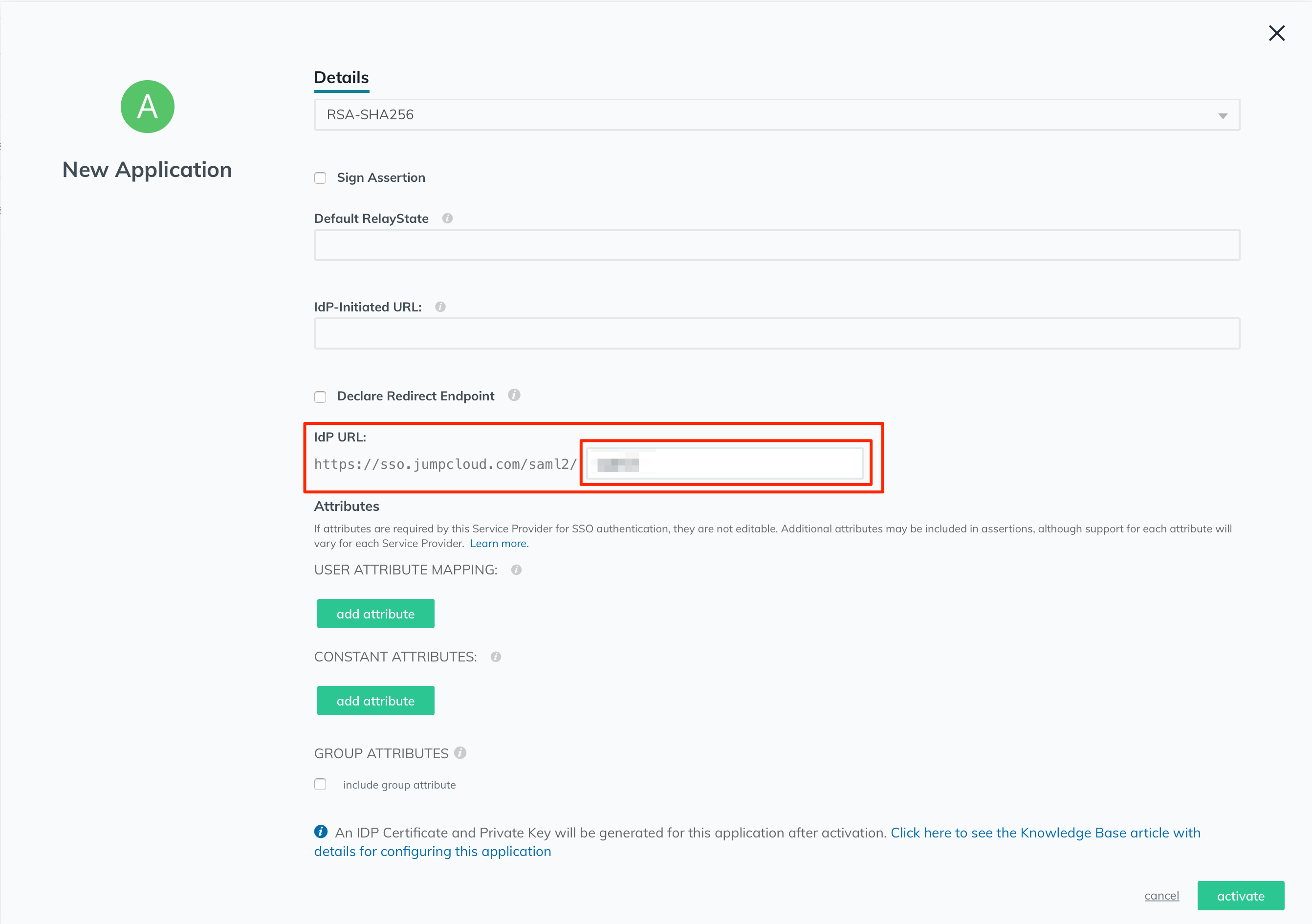
In the "Attributes" section, click on the "add attribute" button to start configuring the user attributes.
Start with adding in the first name attribute, as follows:
Service Provider Attribute Name: firstName
JumpCloud Attribute Name: firstname
Then click on the "add attribute" button again to add the rest of the attributes.
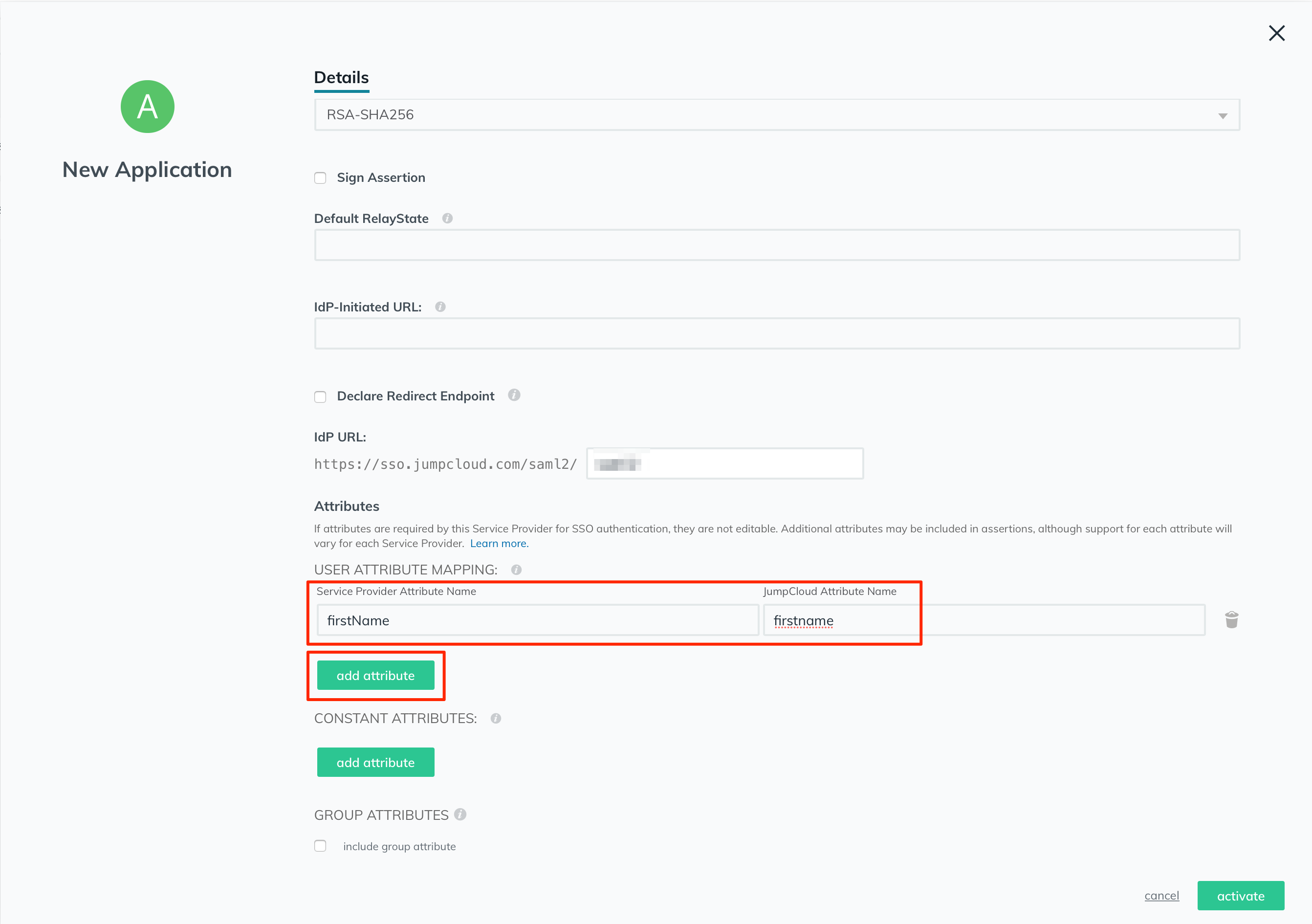
Similarly, add the following details for the last name and email attributes:
Service Provider Attribute Name: lastName
JumpCloud Attribute Name: lastname
And
Service Provider Attribute Name: email
JumpCloud Attribute Name: email
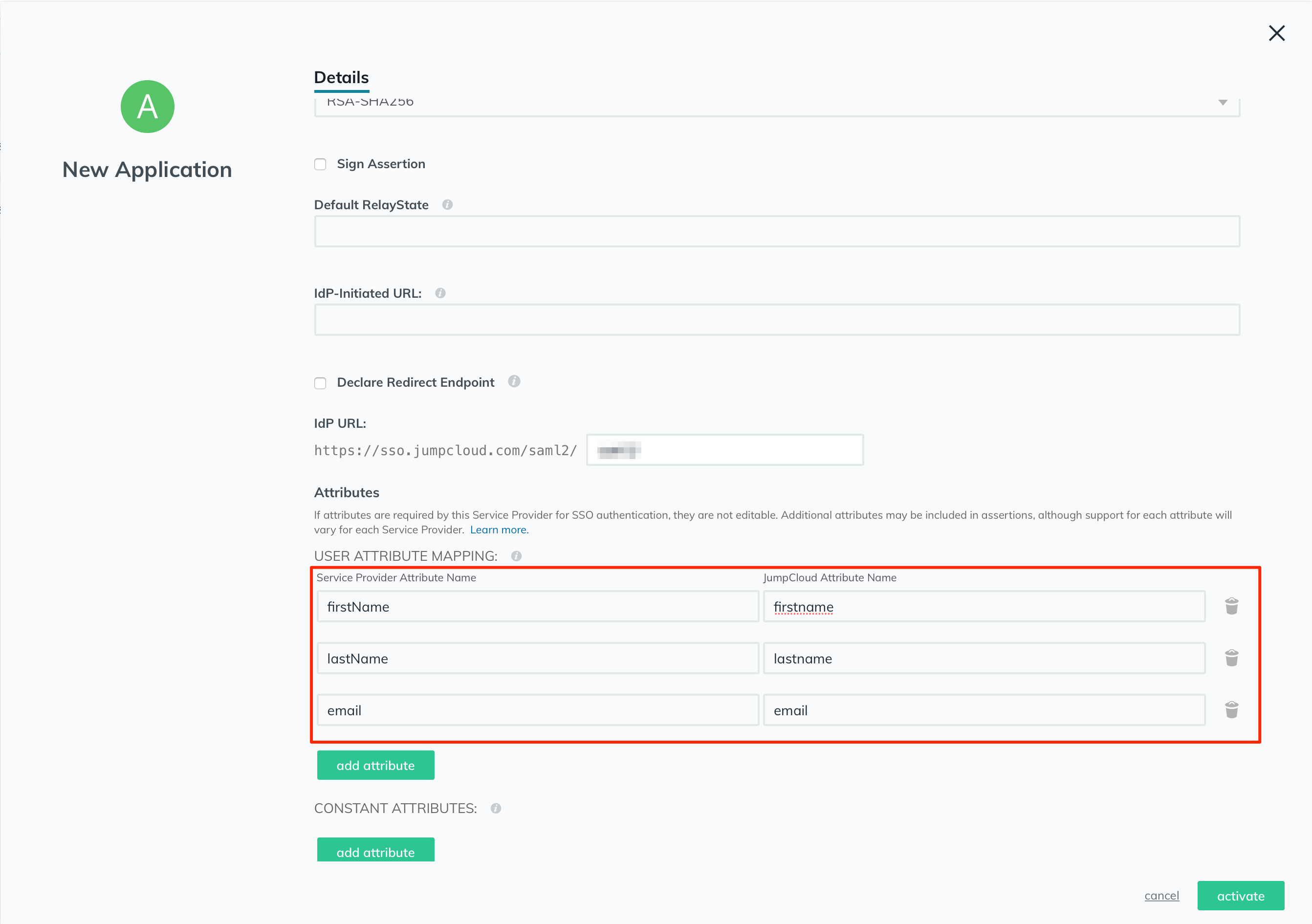
In the "GROUP ATTRIBUTES" section, tick the "include group attribute" checkbox, and write down "group" (without the quotes).
Then click on the "activate" button to activate your application.
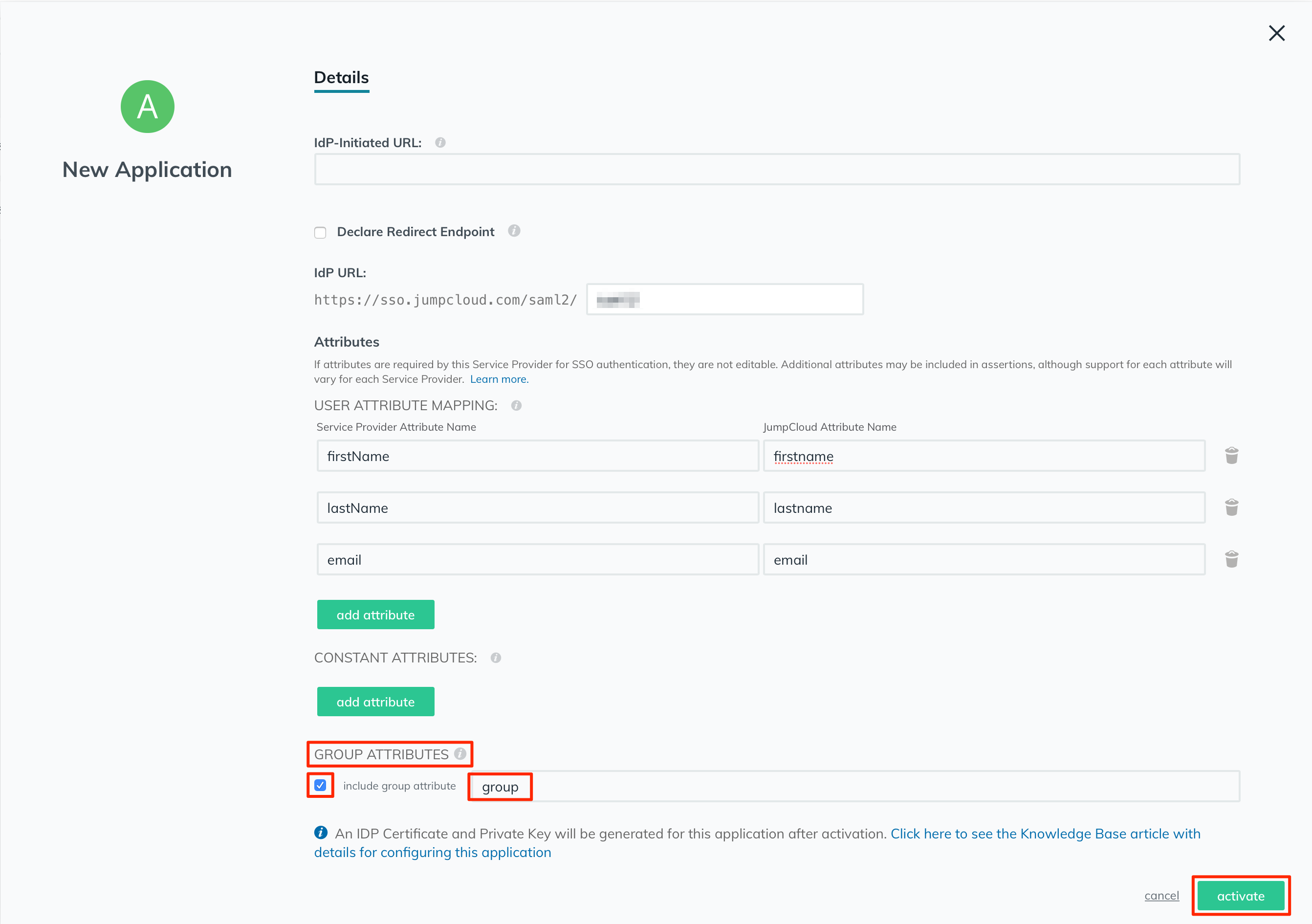
You will get a confirmation popup as follows. Click on the "continue" button.
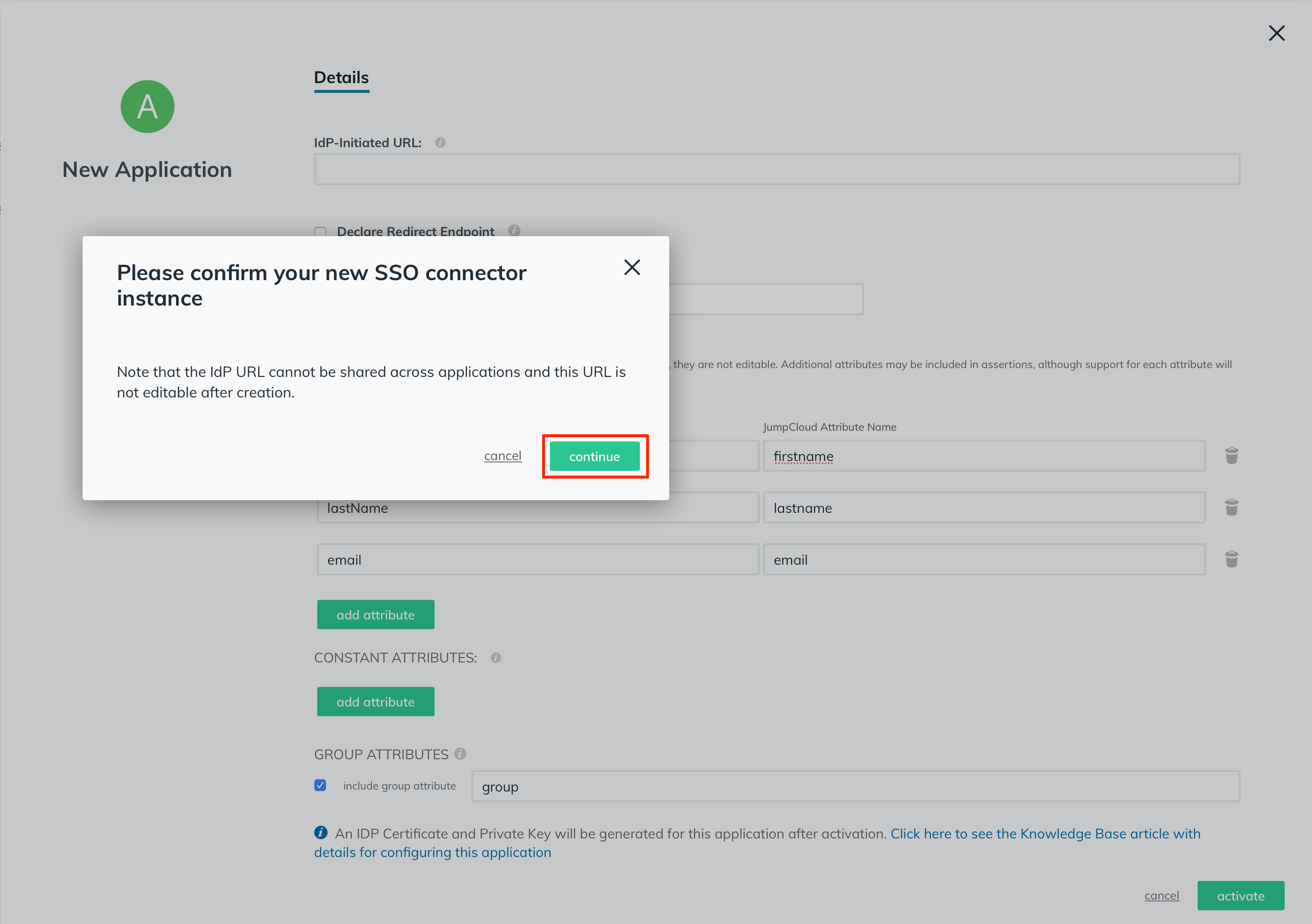
Now you will see the fields populated with the service provider metadata that you've uploaded earlier.
Click on the "export metadata" link to download the IdP metadata XML file.
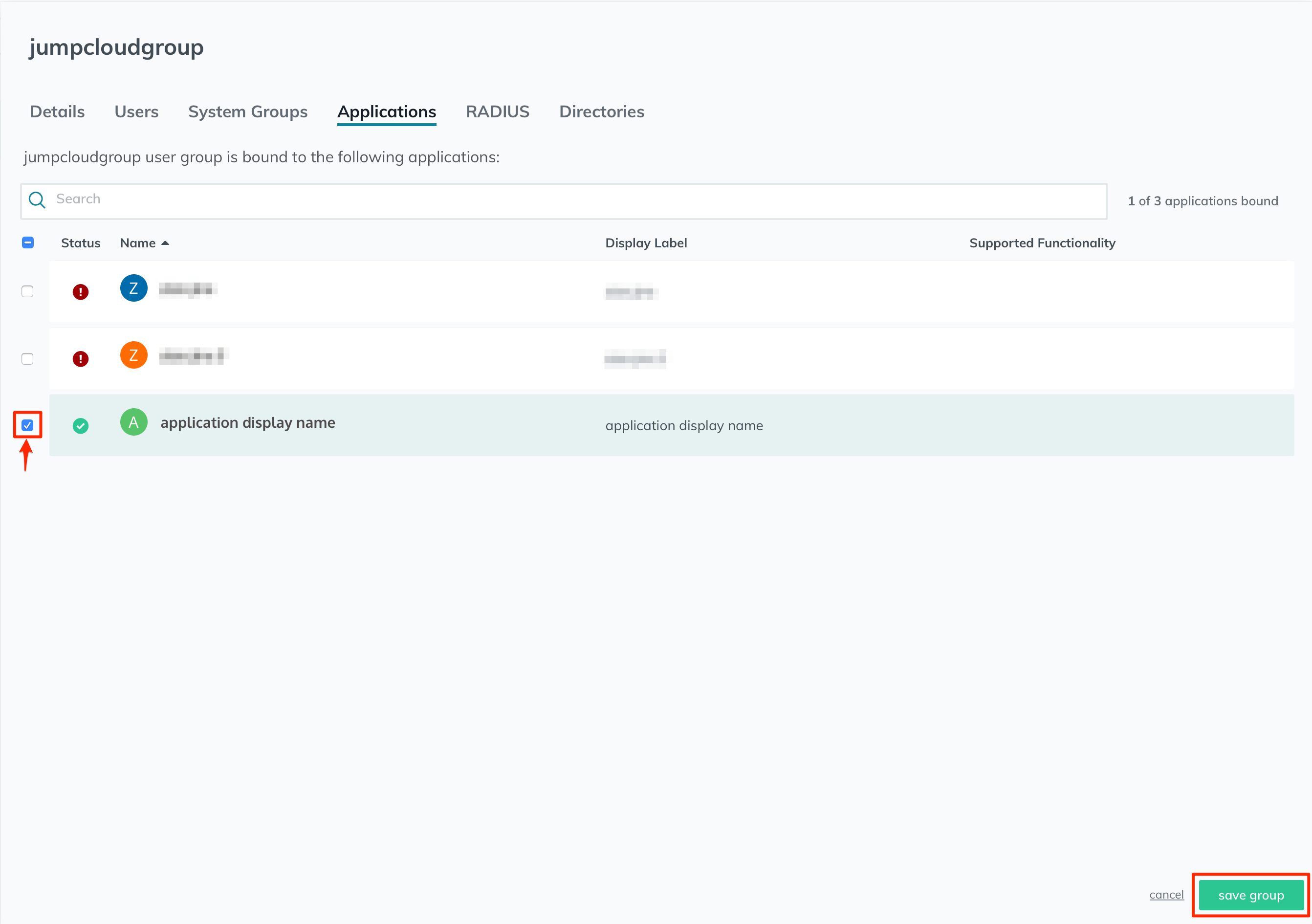
Ensure that the users' group is bound to the application you've just created and activated.
Go to the group settings, click on the "Applications" tab, and ensure your application is enabled here.
Then click on the "save group" button.
The configuration in JumpCloud is now finished. In the next step, we will finish the configuration in the SAML SSO wizard.
Finishing The Configuration - Wizard
Choose "I have a metadata XML file" from the dropdown list of the "Metadata Upload" field.
Click on the "Select metadata XML File" button, and choose the metadata XML file that you've exported from JumpCloud.
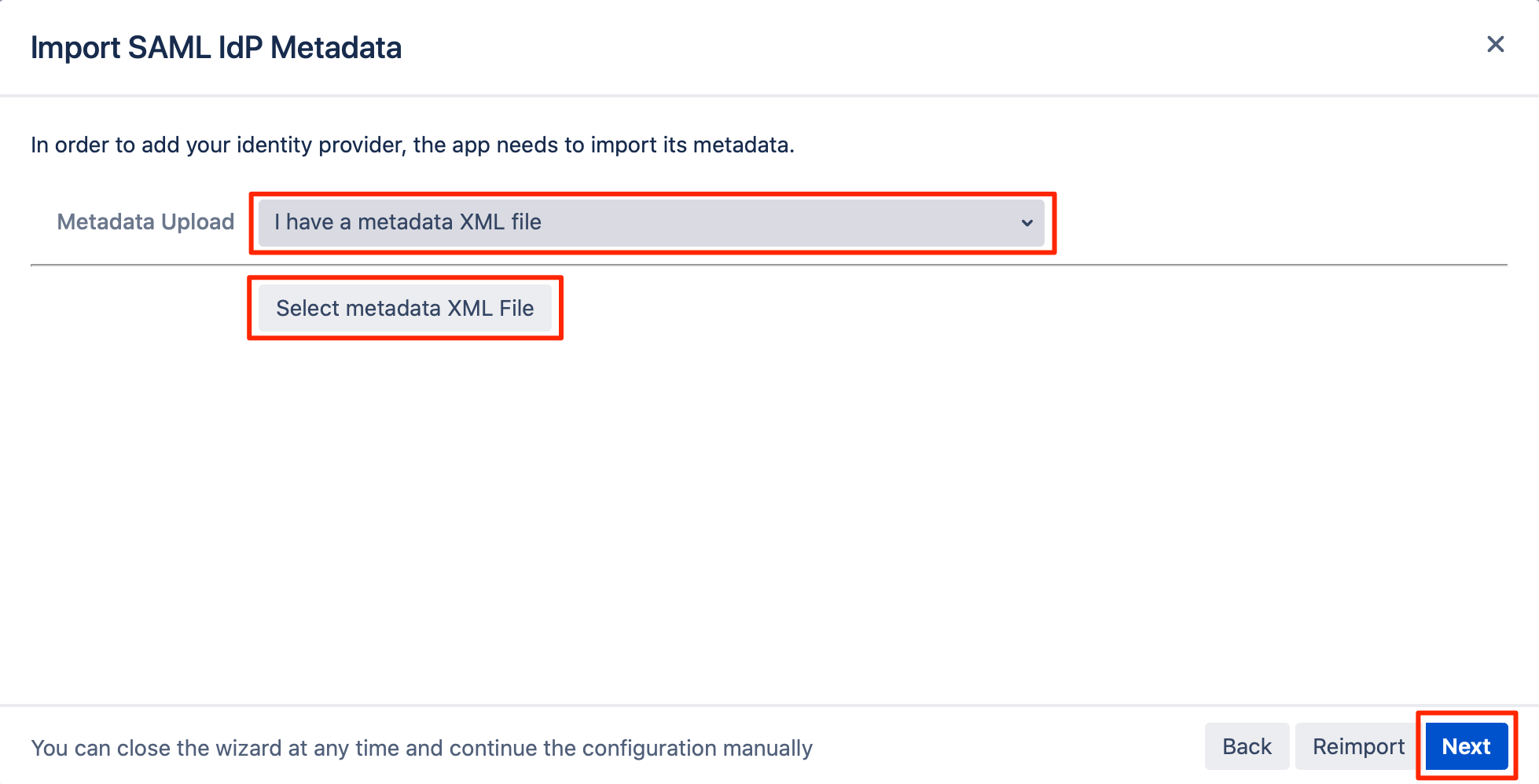
Click on "Next".
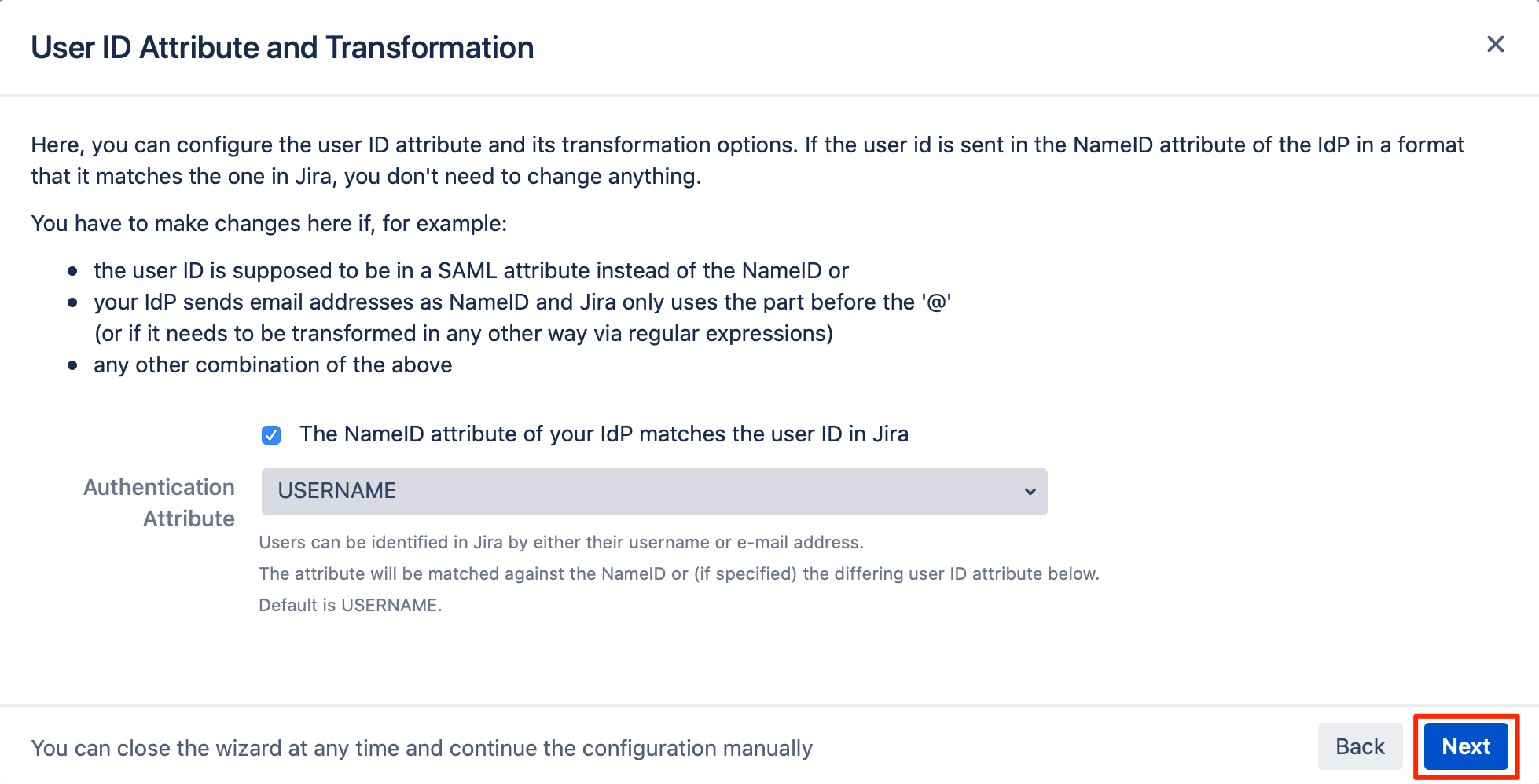
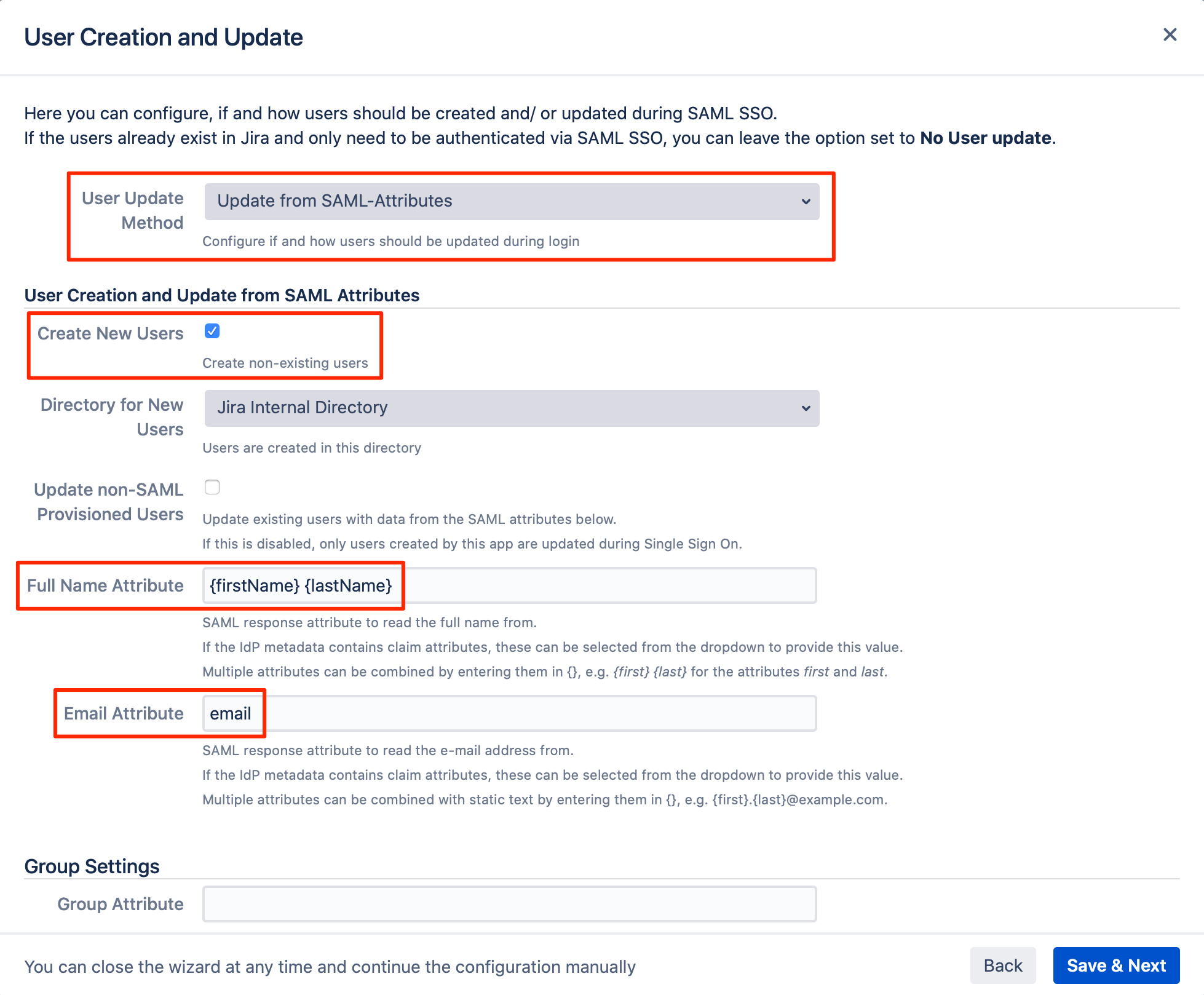
For the "User Update Method", choose "Update from SAML-Attributes" from the dropdown list.
Tick the "Create New Users" checkbox, to create non-existing users in your Atlassian product.
Enter the following attributes:
Full Name Attribute: {firstName} {lastName}
Email Attribute: email
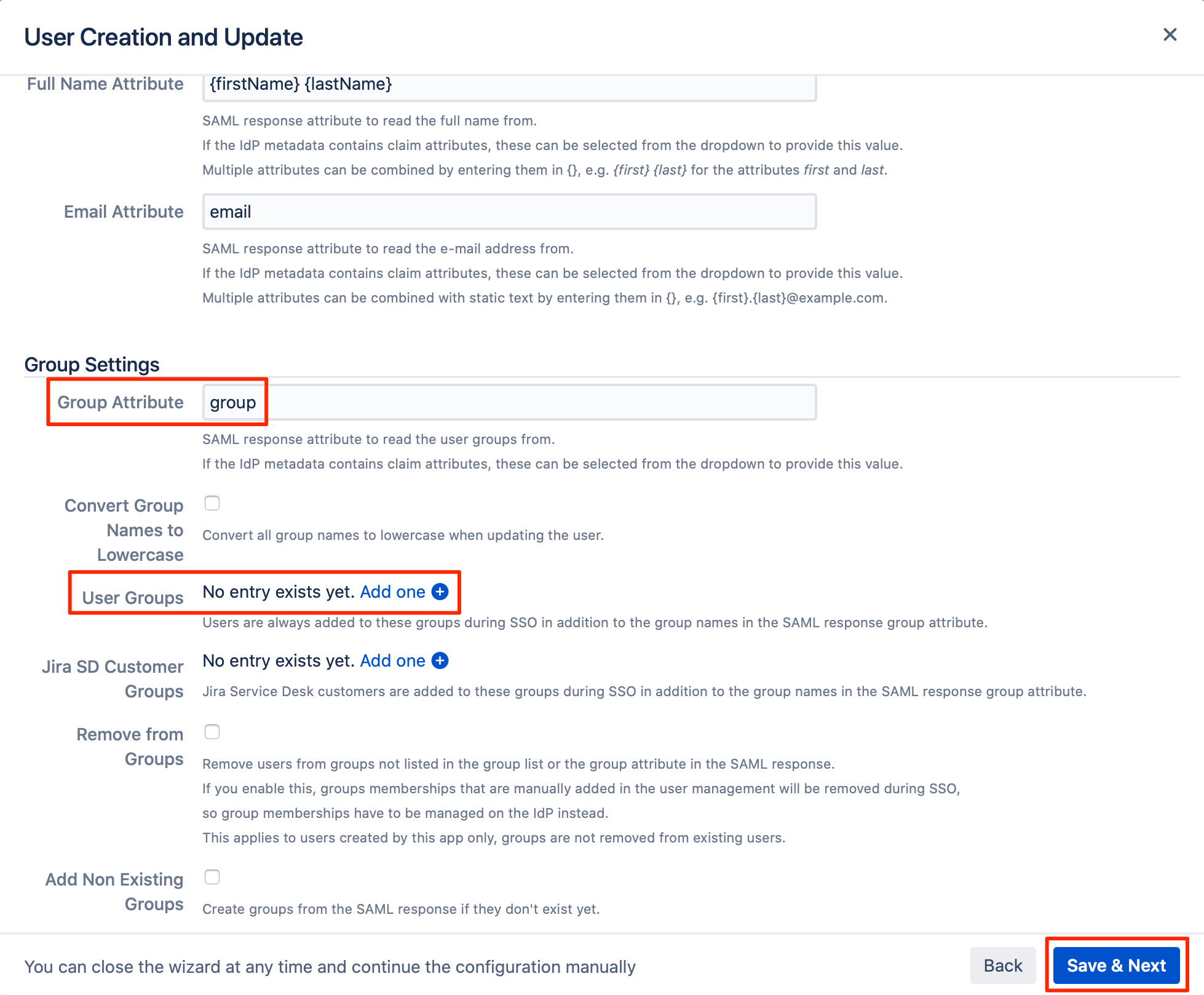
Scroll down to the Group Settings.
Add the following:
Group Attribute: group
Optionally, you can add entries in the User Groups field, if you'd like to assign a group(s) by default to everyone who's logging in (the application access group for instance).
Then click on the "Save & Next" button.
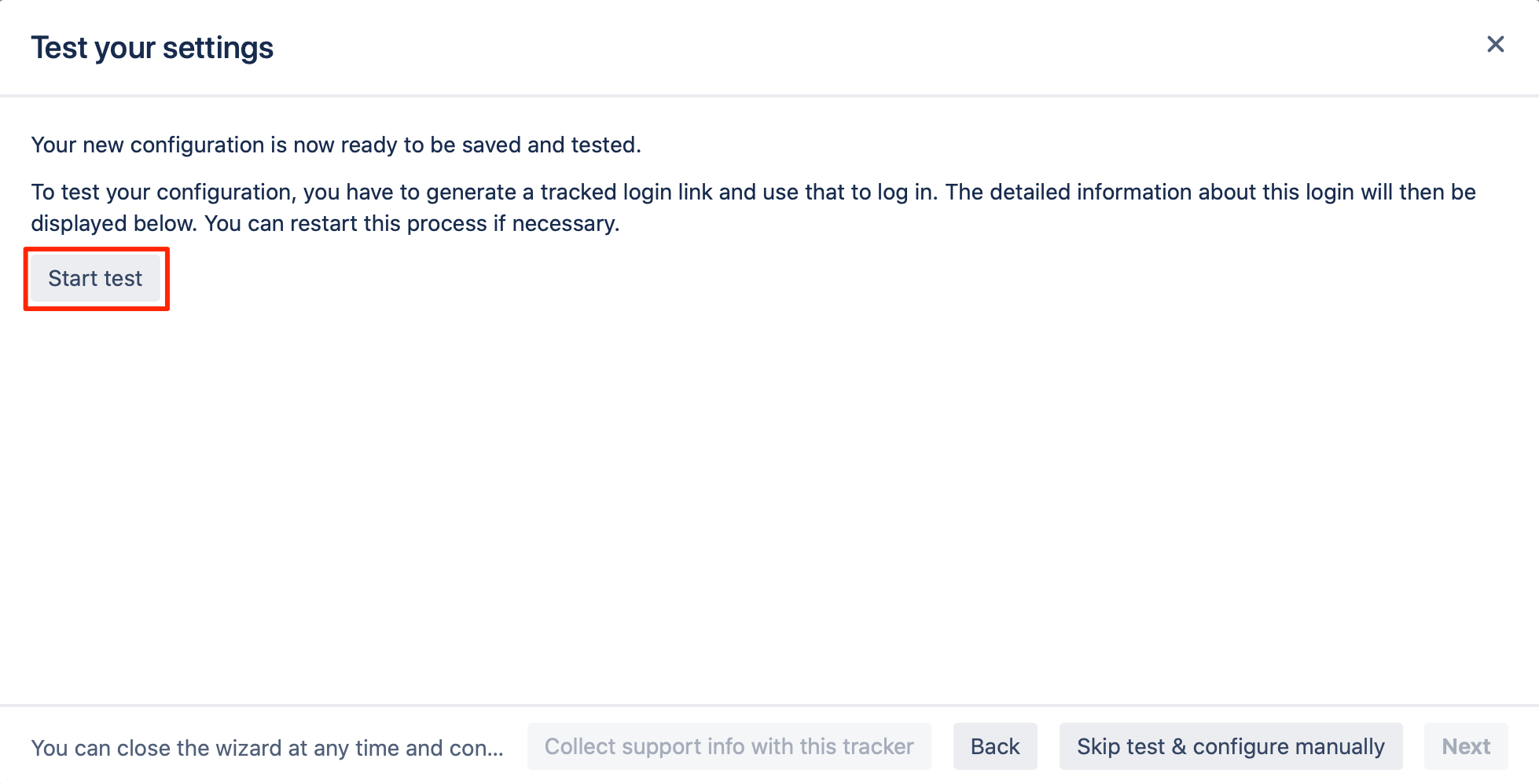
Testing SSO
The wizard also allows testing the Single Sign On. Just follow the steps to test if the login works as expected.
Click on "Start test" to proceed.
Copy the red marked link, and open a new incognito/private tab or a different web browser. Then, paste the link and navigate to it.
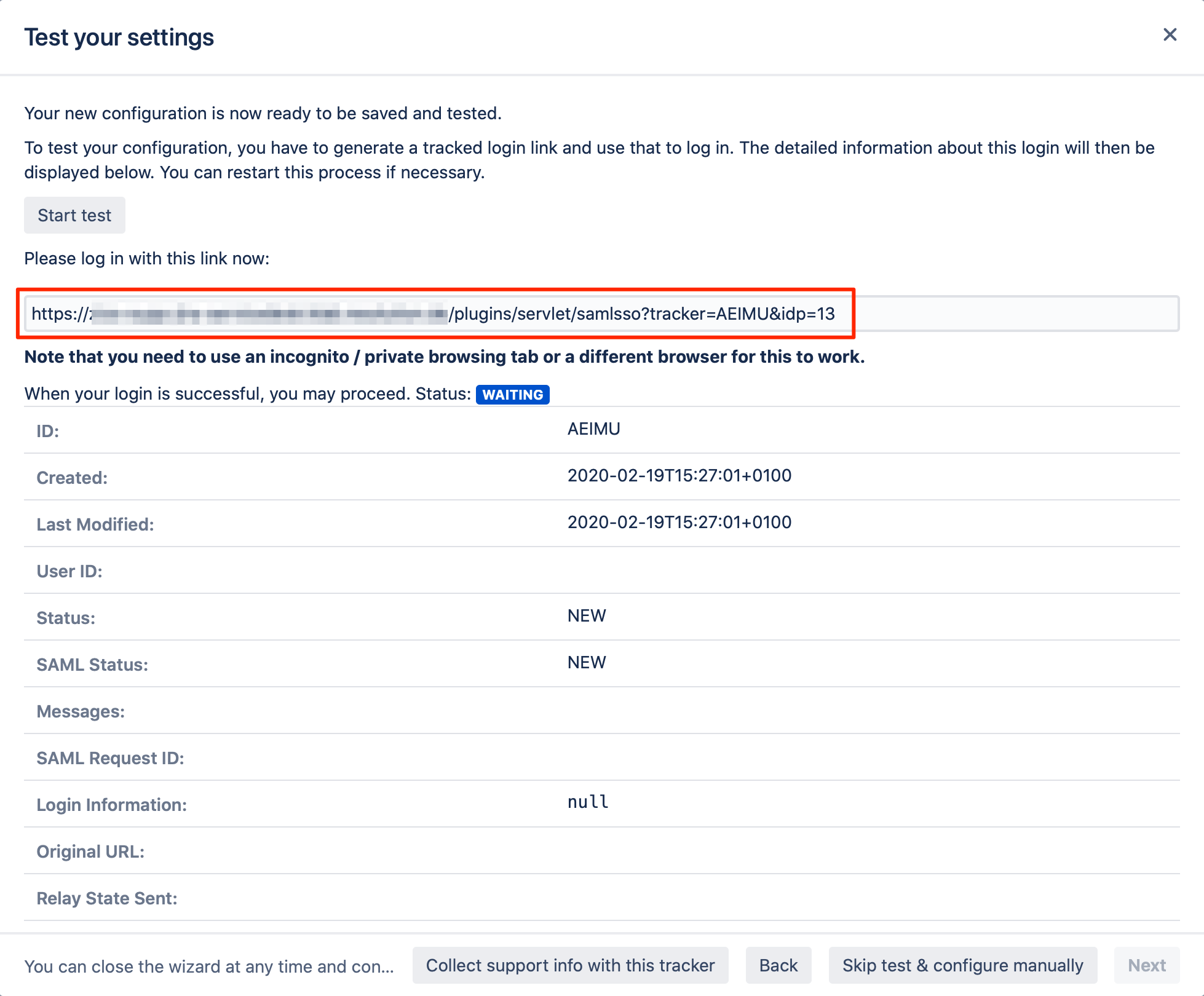
You should be redirected to JumpCloud login page. Enter your SSO credentials to proceed.
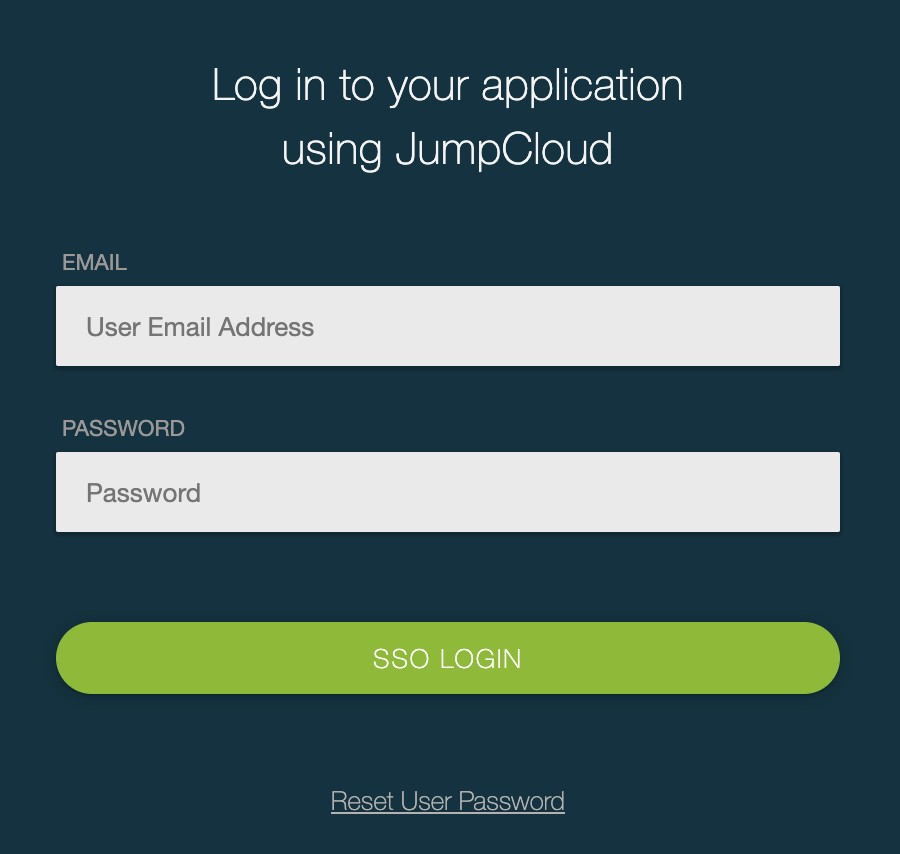
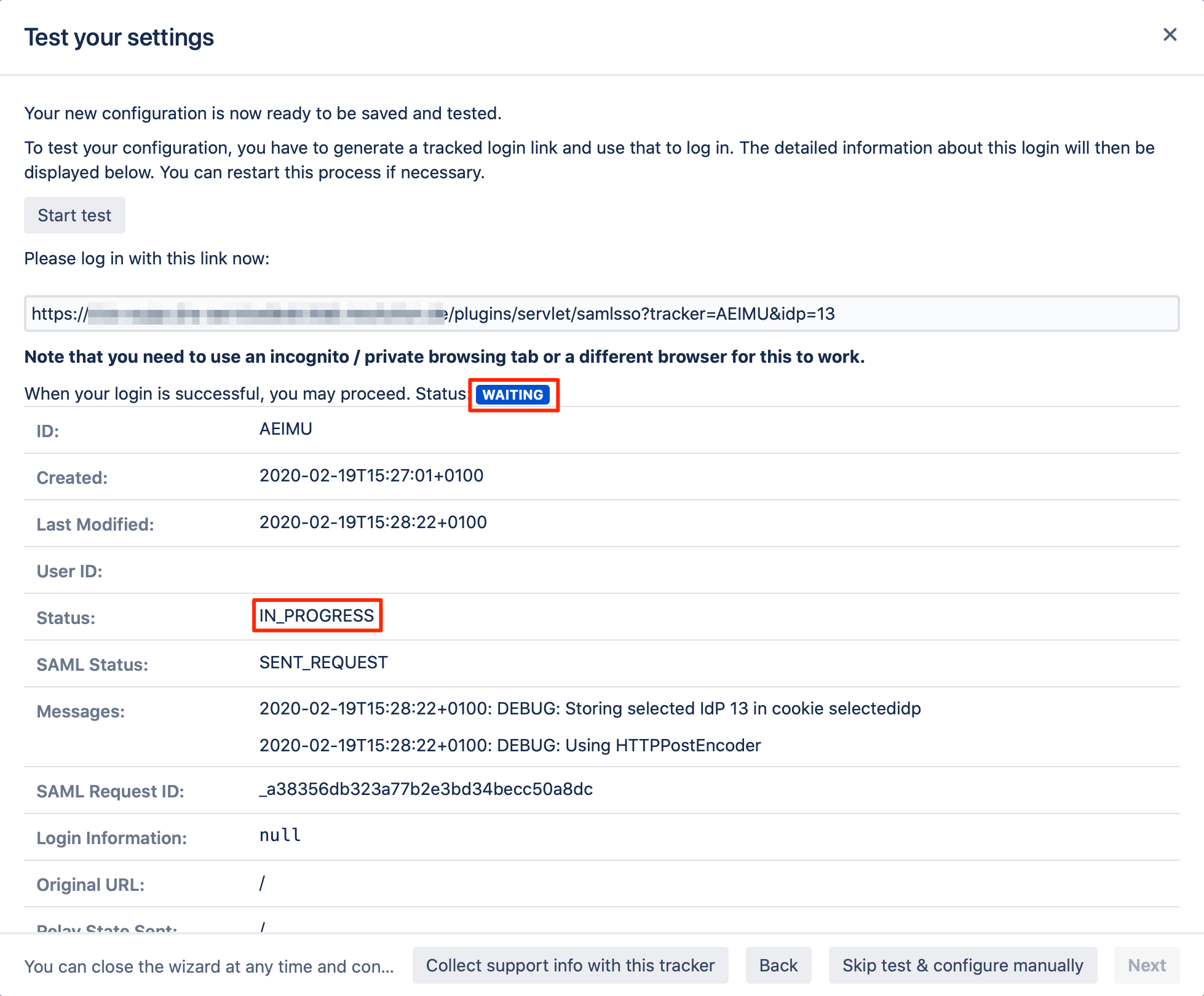
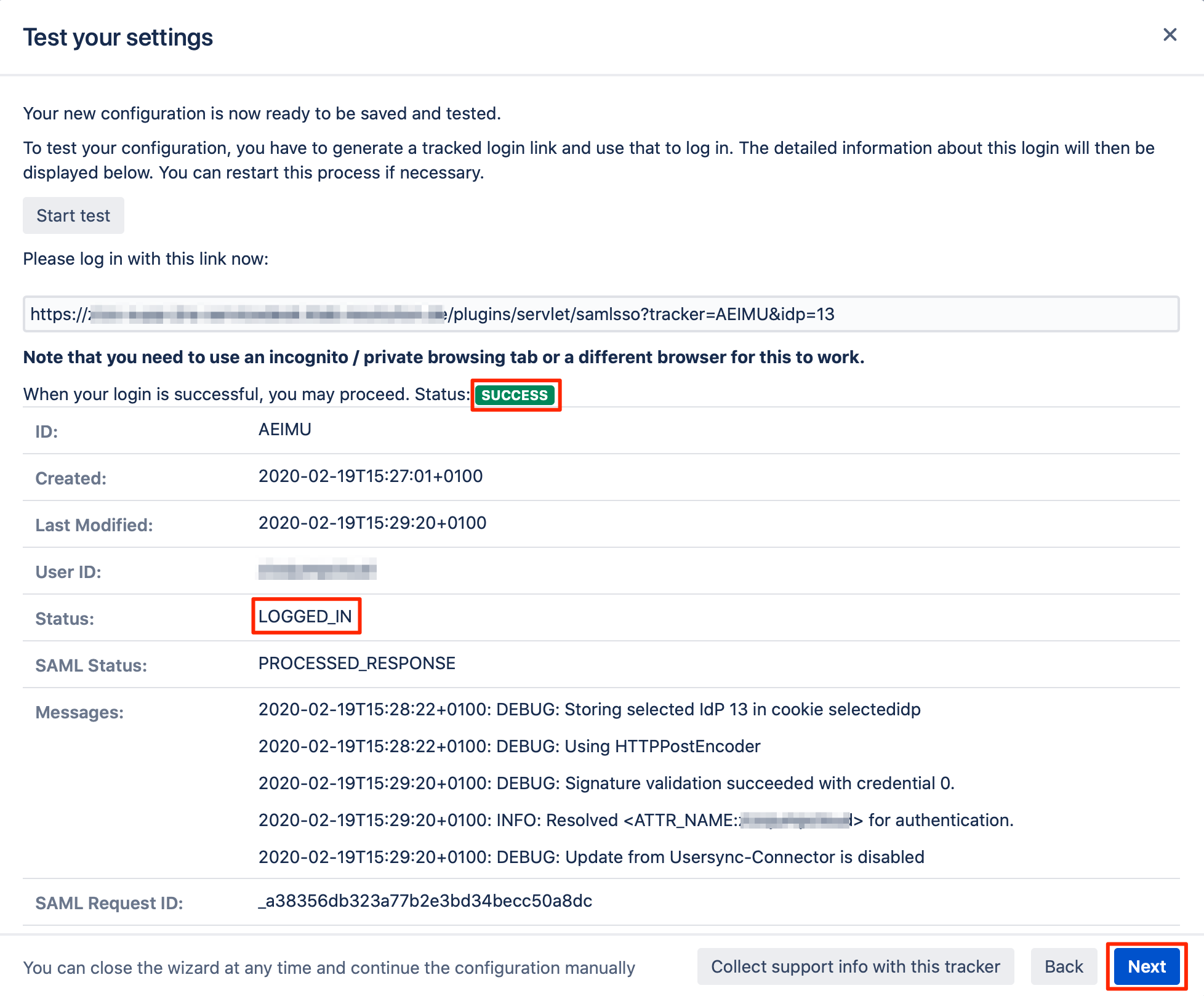
If everything works fine, you will be logged into your Atlassian product. In the other tab/browser in which you were configuring the SAML SSO plugin, you can also see the "SUCCESS" status.
Click "Next" to proceed.
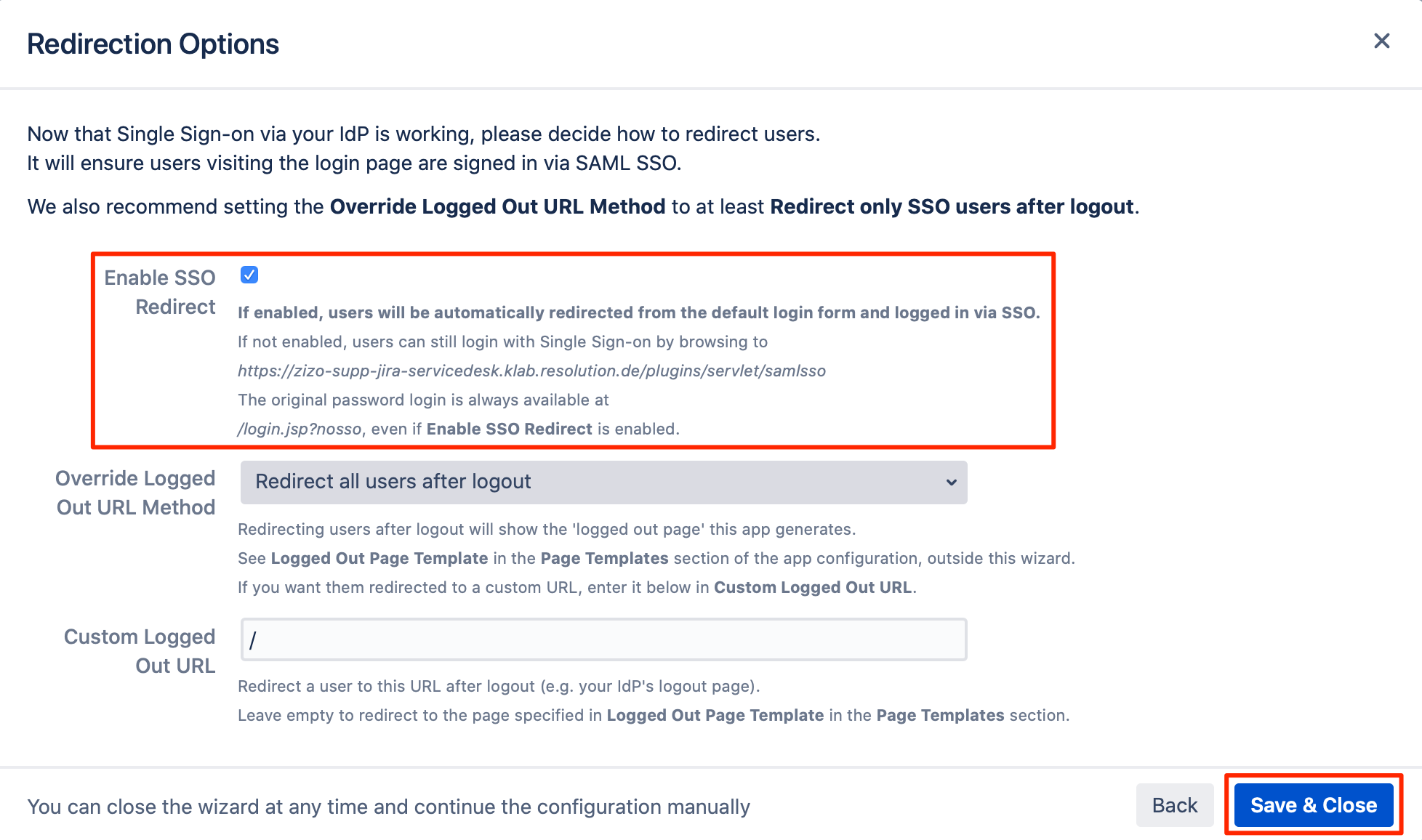
SSO Redirection
As a last step, you can set the "Enable SSO Redirect" option. If set, all users will be redirected to Single Sign On, thus they will be logged in via the IdP.
Click on "Save & Close" to finish the configuration.