Multiple IdPs: Send Users automatically to the desired IdP based on their Operating System
Problem:
Send users to different Identity Providers, based on the operating system of the user's machine. In this example, Windows users should be redirected to ADFS and Macbook users to Okta.
Solution:
This article describes how to achieve this using the HTTP Request Header information send by the user when trying to access the service provider application.
Here is the information that we see in a typical HTTP request that hits our Plugin:
- {
- "sourceIpAddress": "100.x.x.x",
- "requestHeaders": {
- "x-request-id": "c9728cda25a2eb69ce07ee6914158524",
- "x-forwarded-proto": "https",
- "accept-language": "en-gb",
- "cookie": "INGRESSCOOKIE=1606394780.938.1009065.973284",
- "x-forwarded-port": "443",
- "x-forwarded-for": "91.x.x.x",
- "accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
- "x-real-ip": "91.x.x.x",
- "x-original-forwarded-for": "91.x.x.x",
- "x-forwarded-host": "jira8-5-core-test.test.de",
- "host": "jira8-5-core-test.test.de",
- "x-scheme": "https",
- "accept-encoding": "gzip, deflate, br",
- "user-agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/13.1.3 Safari/605.1.15"
- }
The user-agent field at the bottom contains information about the operating system. In this example, it shows a Macbook user. (Macintosh; Intel Mac OS X 10_15_7)
This information can be used in the IdP Selection configuration page of our plugin.
Under IdP Selection → Request Headers is it possible to specify certain HTTP header key-value pairs and map them to specify IdPs. The header keys are case sensitive and the values can be regular expressions.
Coming back to the original scenario the configuration can be done as below:
Click on → Add one and enter the following keys and values and select the desired IdP.
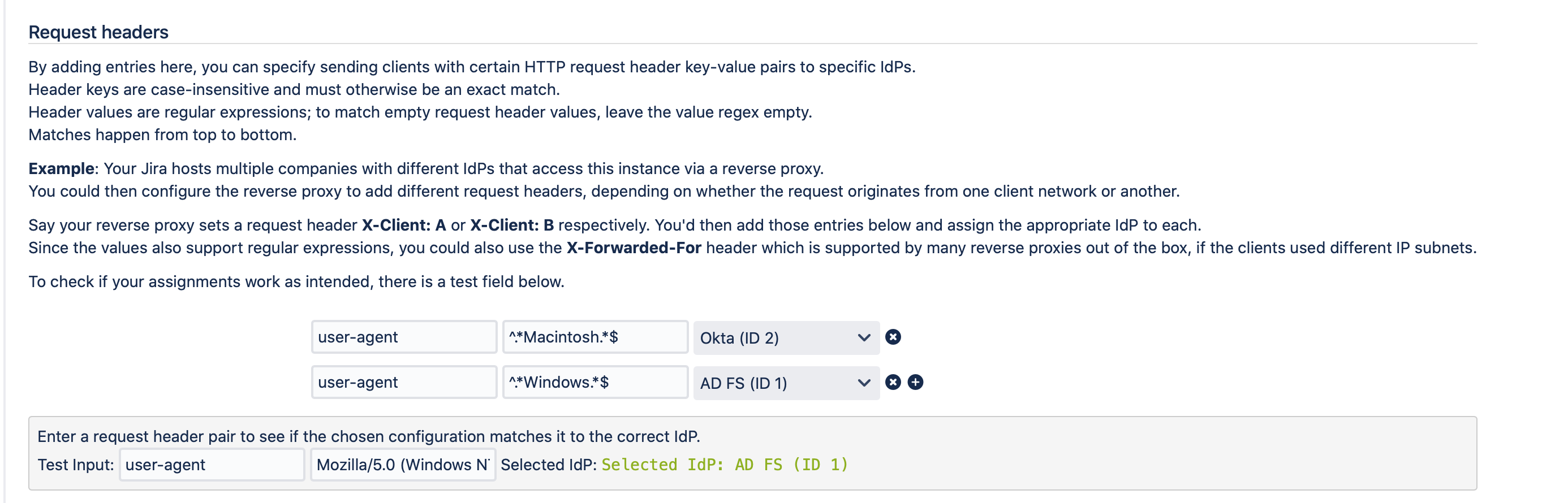
Here are the regular expressions for cut & paste:
- ^.*Macintosh.*$
- ^.*Windows.*$
It is also possible to test your settings as shown at the bottom of the picture. Just add the user-agent key and copy and paste the information from the HTTP request header. You can find examples in the Systems & Support sections under Tracker for users that have connected to the service provider application.
After a bit of research, here are some additional Regular expressions that you may want to (some may be for rather old machines)
Platform | |
|---|---|
Mac | ^.*Macintosh.*$ ^.*MacIntel.*$ ^.*MacPPC.*$ ^.*Mac68K.*$ |
Windows | ^.*Windows.*$ ^.*Win32.*$ ^.*Win64.*$ ^.*WinCE.*$ |
IOS | ^.*iPhone.*$ ^.*iPad.*$ ^.*iPod.*$ |
Android | ^.*Android.*$ |
It is almost impossible to detect the user's OS with 100% accuracy, but this configuration gets relatively close.
The beauty about our HTTP Header method also is, that in case none of the value-key pairs match - the IdP selection will go back to the method chosen in the IdP Selection Method drop down menu (above). So you have any of the other methods like "IdP selection Page" as a fallback.
