Replace the self-signed certificate for request signing and assertion decryption
Starting with version 0.15.0, SAML SingleSignOn allows signing authentication requests and handle encrypted SAML responses.
During the plugin installation, a private key and a self-signed certificate is generated with a validity of 10 years. This certificate is included in the SAML Metadata to be loaded by the IdP.
This certificate and key can be replaced in the Plugin configuration's advanced settings:
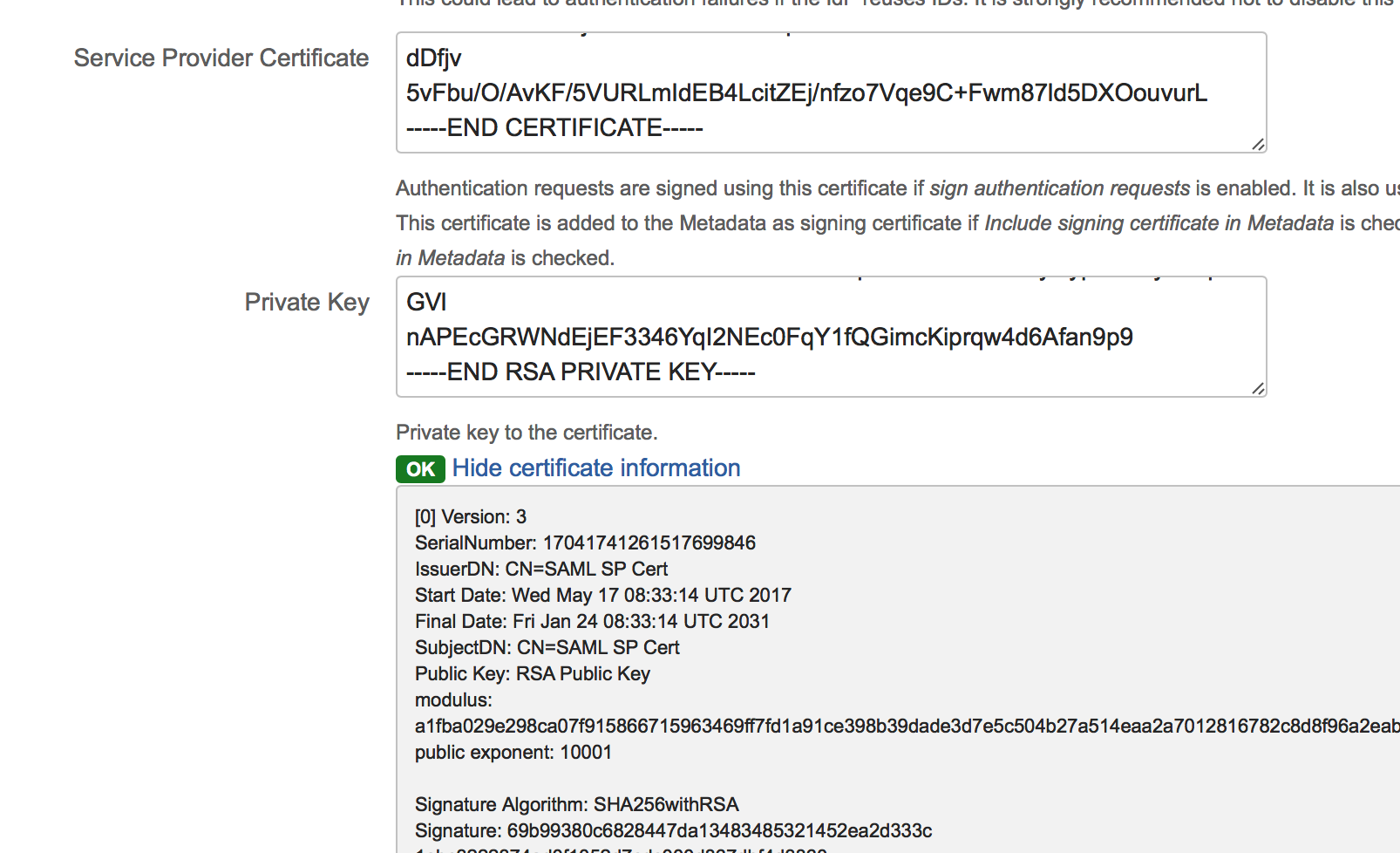
To replace the certificate and key, paste it into the Certificate and Private Key- fields. The indicator below the private key field shows ok if:
certificate and private key can be decoded (the private key must have no password set)
the private key matches the certificate
Create a new self-signed certificate
If any of the created certificate's parameters (e.g. the validity date) are not suitable, this is one possible solution to create a new one.
OpenSSL must be installed, it has been tested with OpenSSL 0.9.8zh under macOS Sierra 10.12.4 and OpenSSL 1.0.1k-fips under Amazon Linux 2016.09
- openssl req -x509 -sha256 -newkey rsa:2048 -days 5000 -nodes -out samlsp_cert.pem -keyout samlsp_key.pem -subj '/CN=SAML SP Cert'
This command creates a new private key (RSA 2048 bits) and a self-signed certificate with a validity of 5000 days and the Subject CN=SAML SP Cert. The certificate is written to samlsp_cert.pem and the key to samlsp_key.pem.
Be aware that the private key has no passphrase here (due to the parameter -nodes)
