OpenID Connect for Microsoft Entra ID (formerly Azure AD) with User Sync
Goal
After completing this setup guide, you will have set up Microsoft Entra ID (formerly Azure AD) and your Atlassian product for the SAML SSO app and also User Sync, using the OpenID Connect protocol. Additionally, you will enable test the SSO.
Prerequisites
To use the SAML SSO app with Microsoft Entra ID (formerly Azure AD), you need the following:
An Microsoft Entra ID (formerly Azure AD) subscription
A (trial) subscription for the SAML SSO app
Admin access to your Atlassian product
Video Guide
Step-by-Step Setup Guide
Install the SAML SSO App
In your Atlassian product, open the in-product marketplace as described in the Atlassian documentation.
Search for "resolution saml" and click "Install" for SAML Single Sign On (SSO) by resolution Reichert Network Solutions GmbH.
After the installation is complete, click Manage Apps/Addons.
Configure User Sync
Go to http://portal.azure.com and click the Microsoft Entra ID.

In the Microsoft Entra ID click App registrations.
Click New registration to create a new app.
Enter a name for your application and click on Register to proceed.
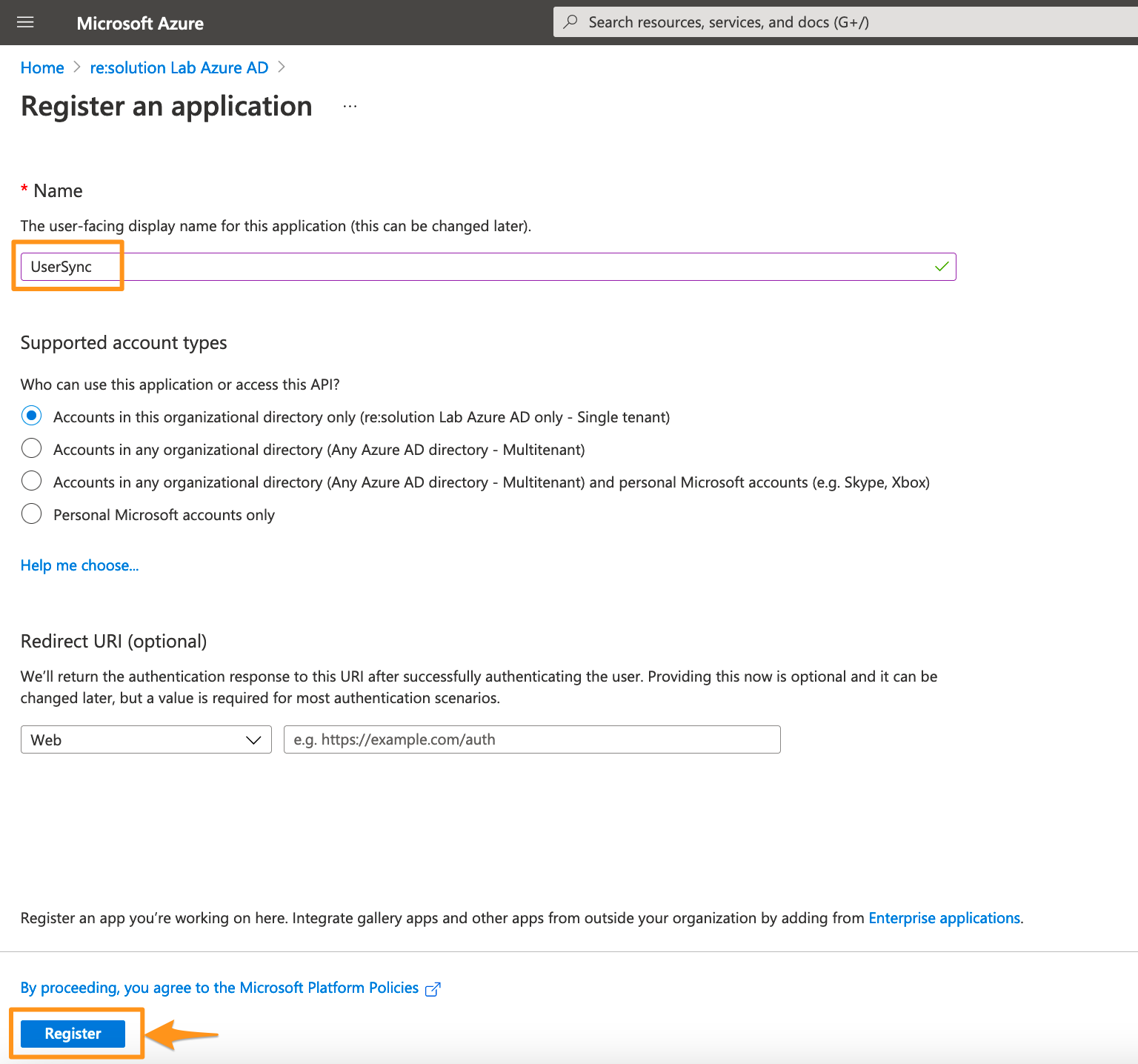
Click API permissions in the left panel.
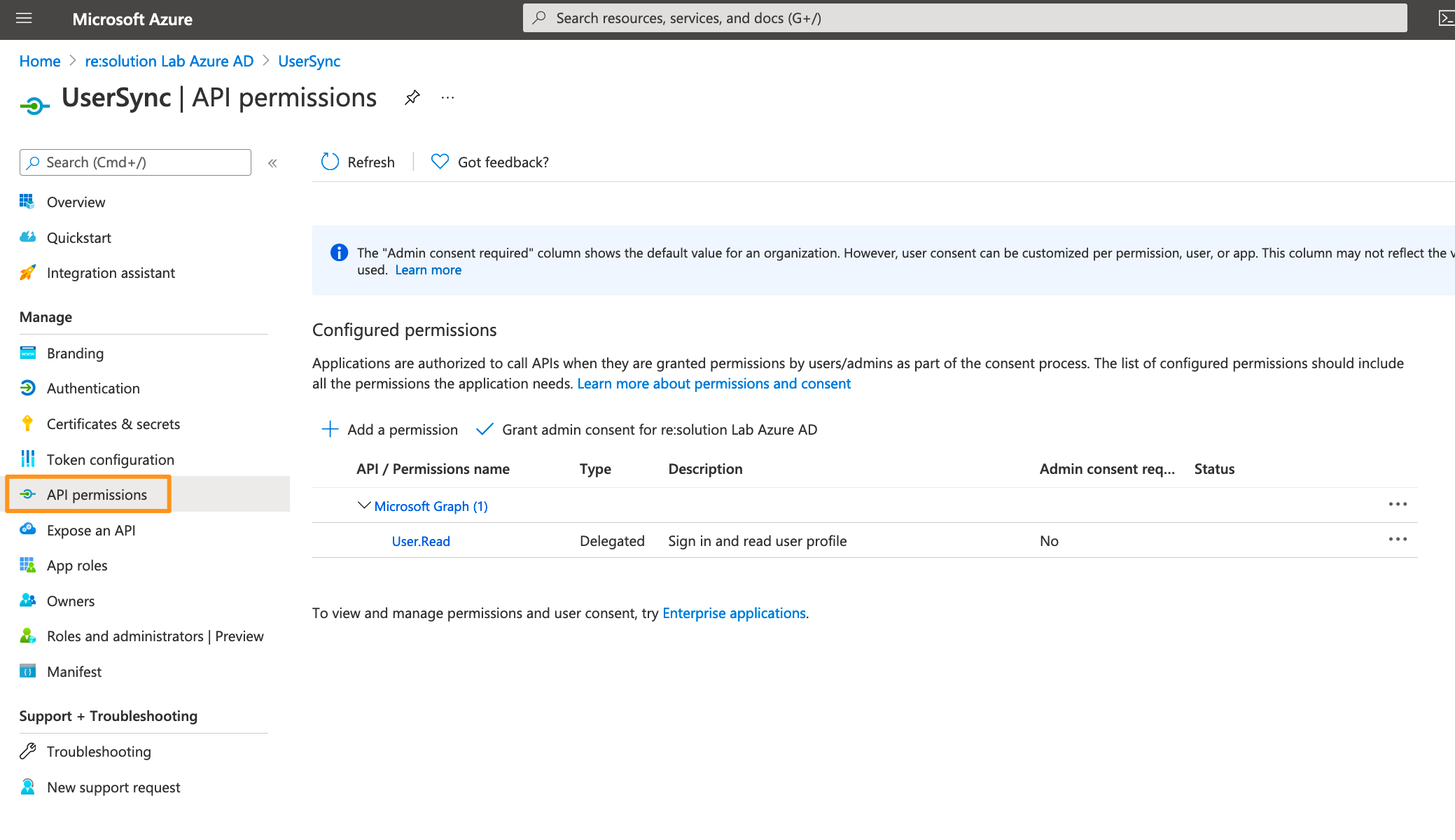
Delete the default created permission since it's not needed.
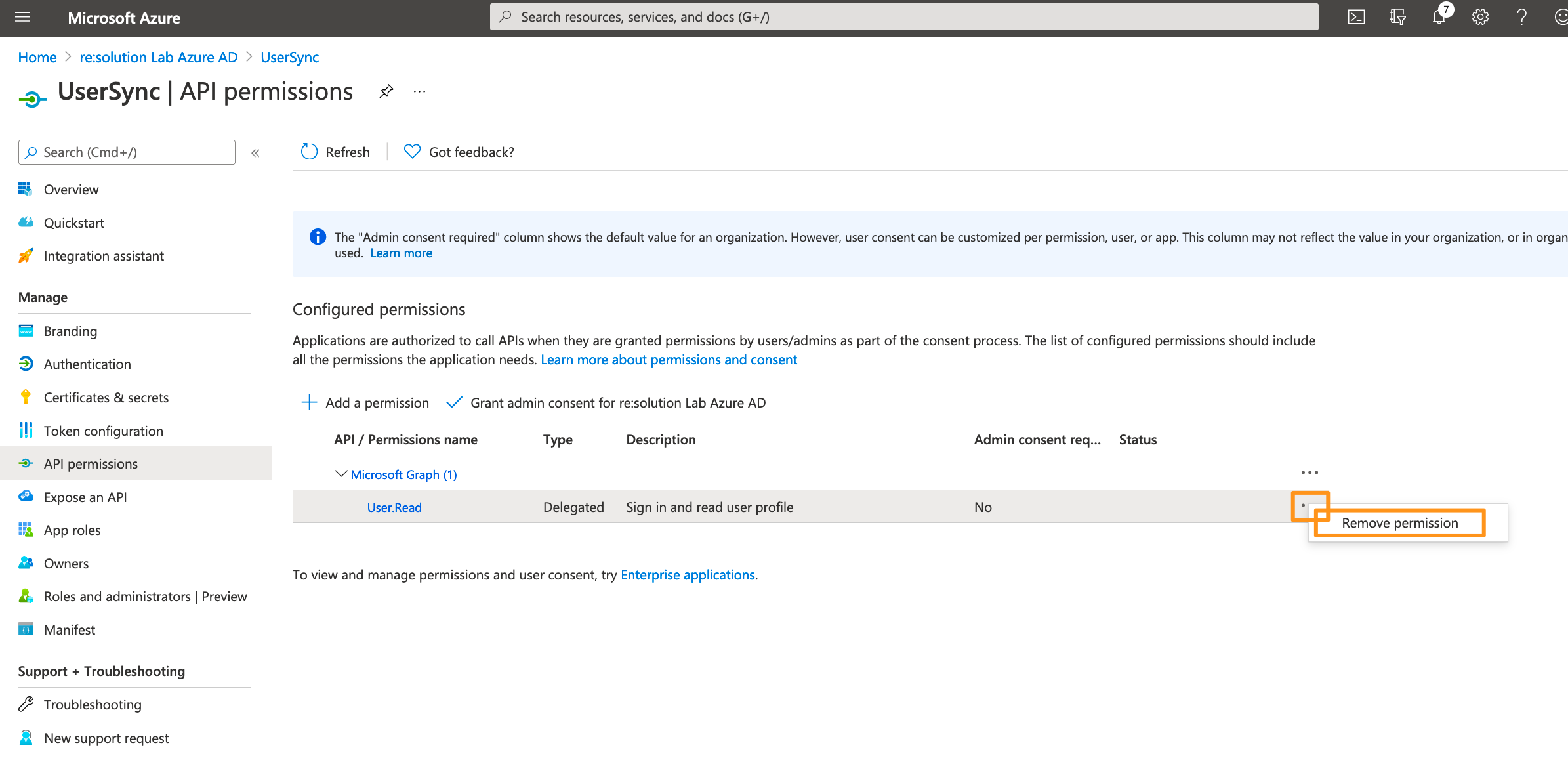
Click on Add a permission.
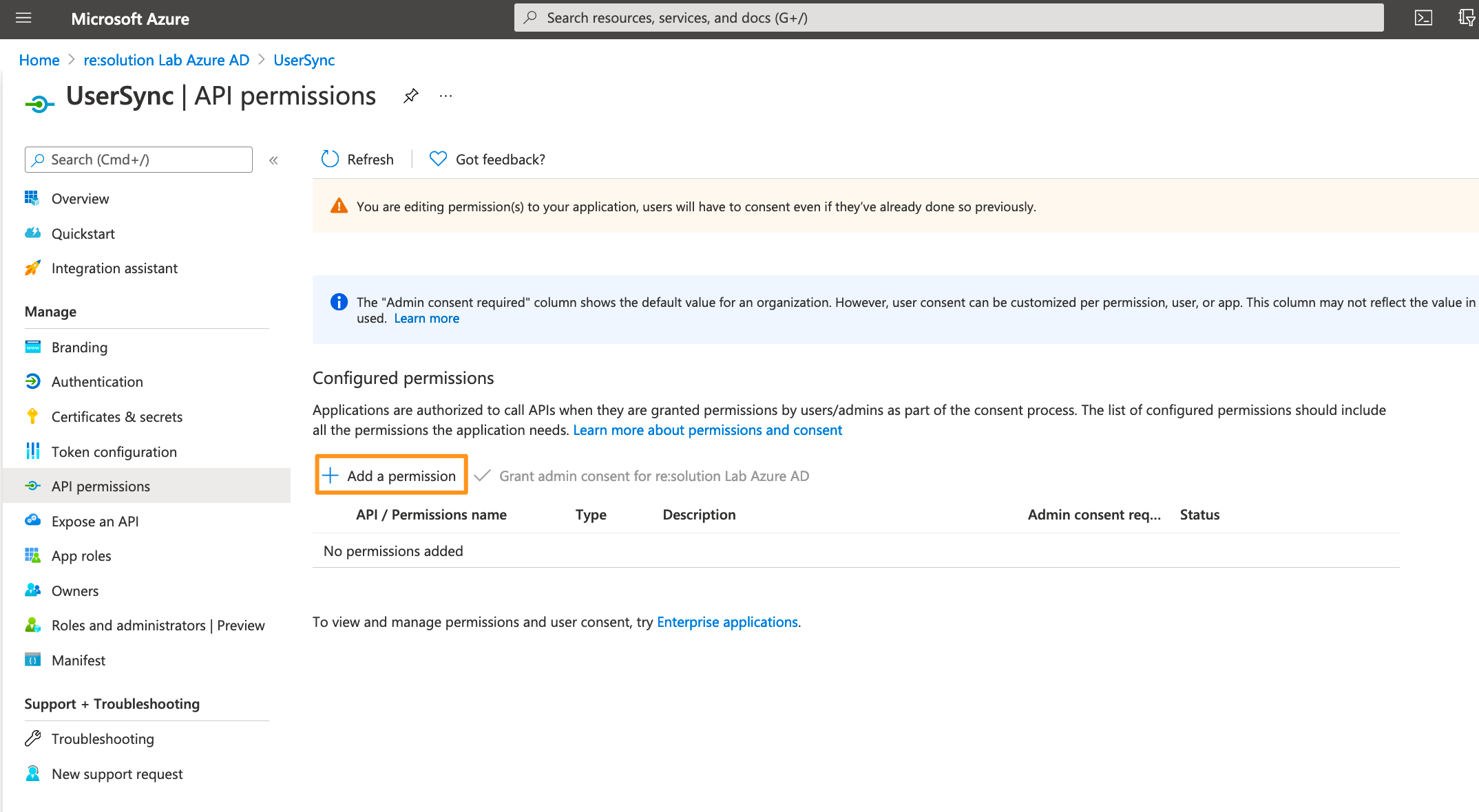
Select Microsoft Graph.
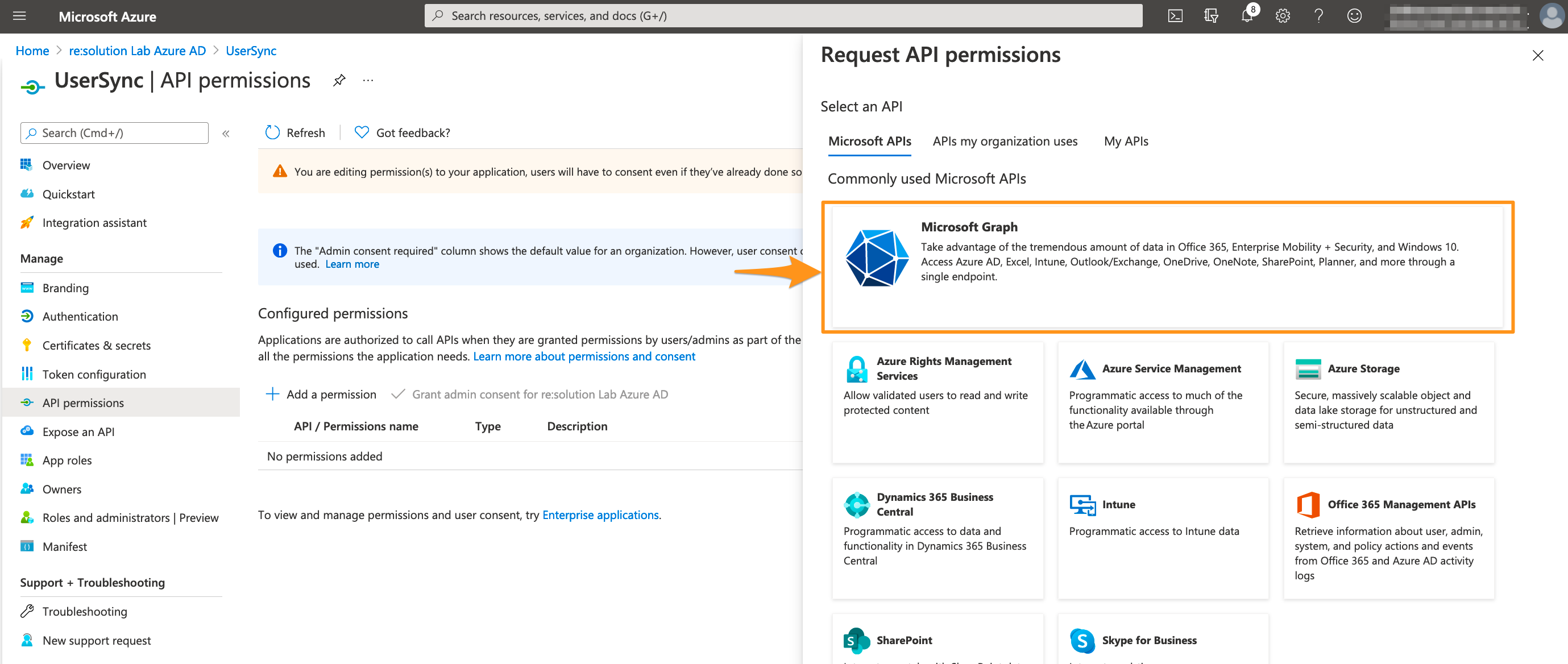
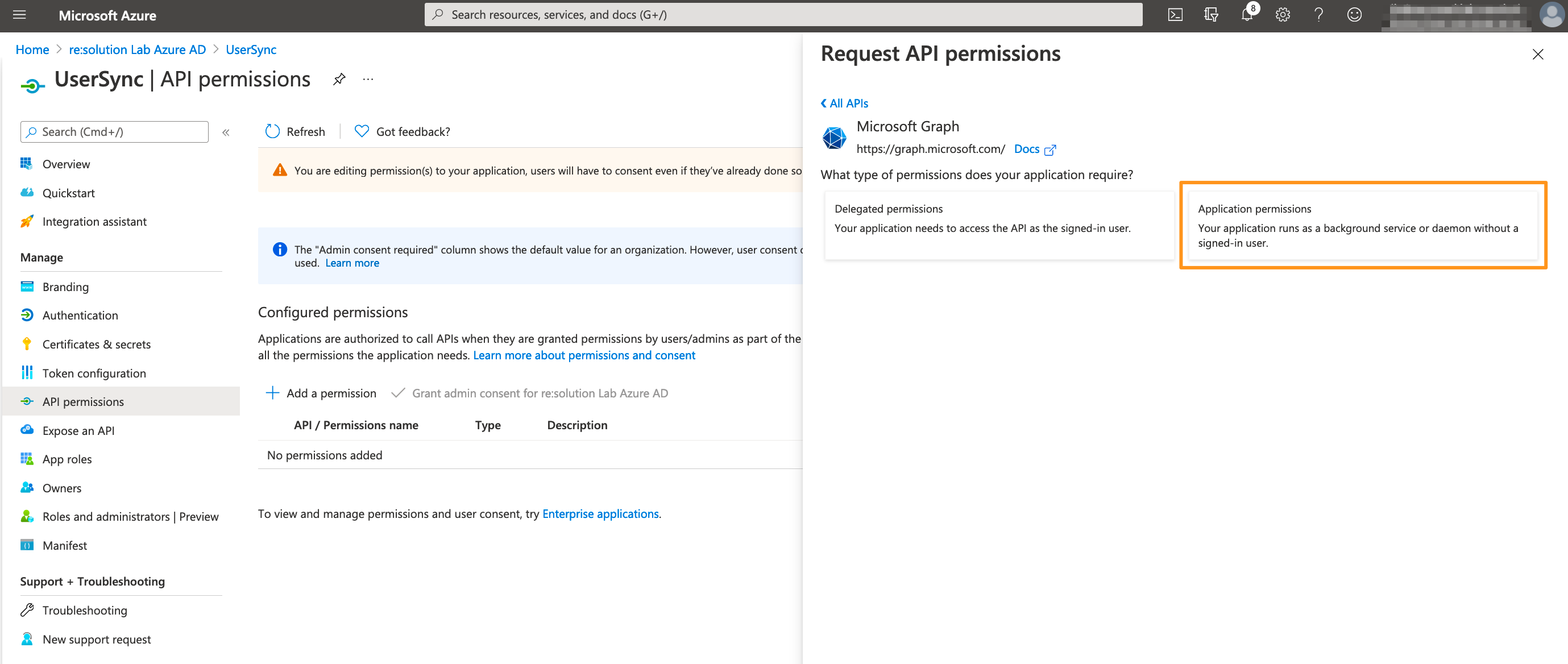
Choose Application permissions.
Expand Directory and tick Directory.Read.All
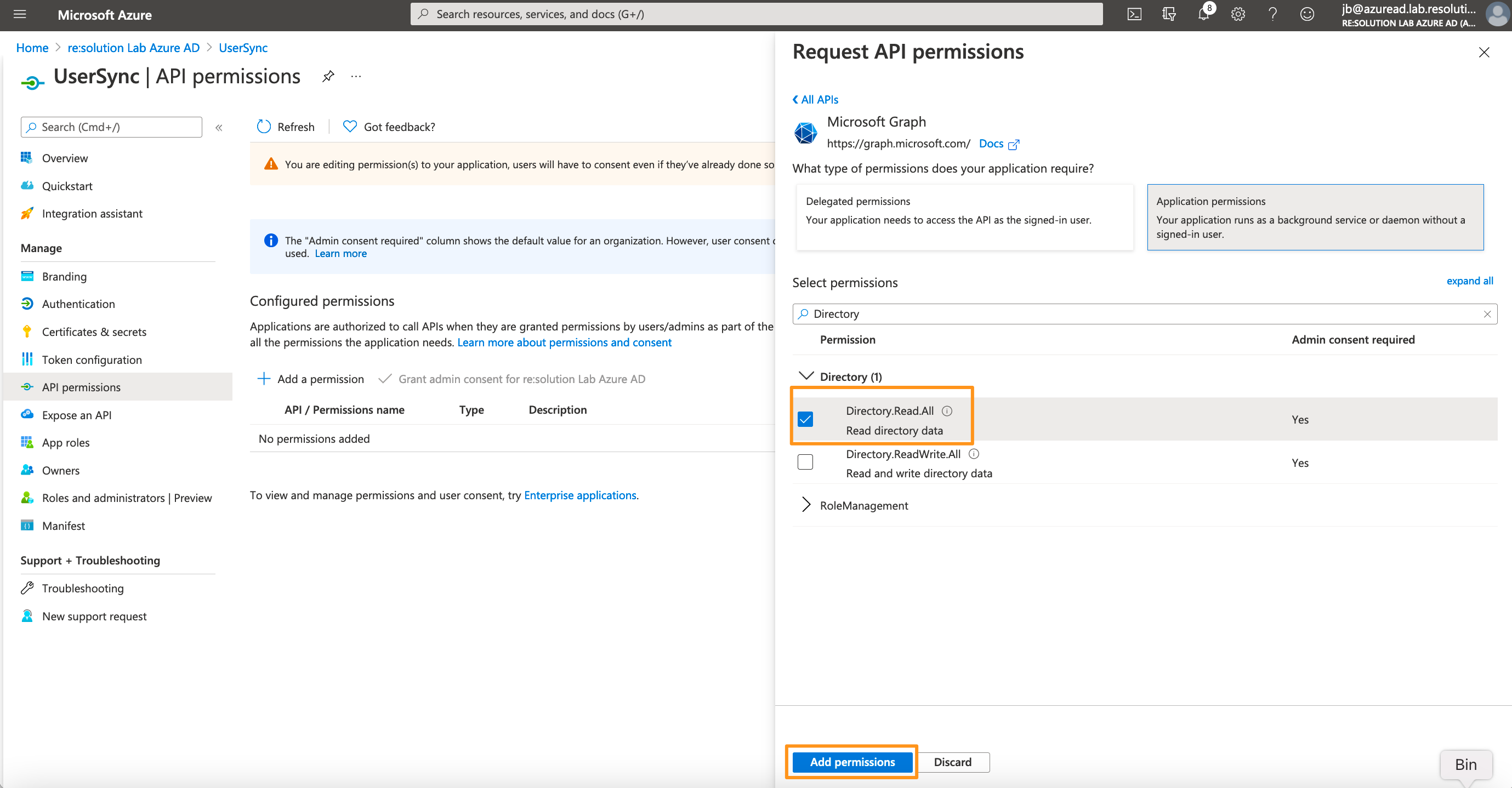
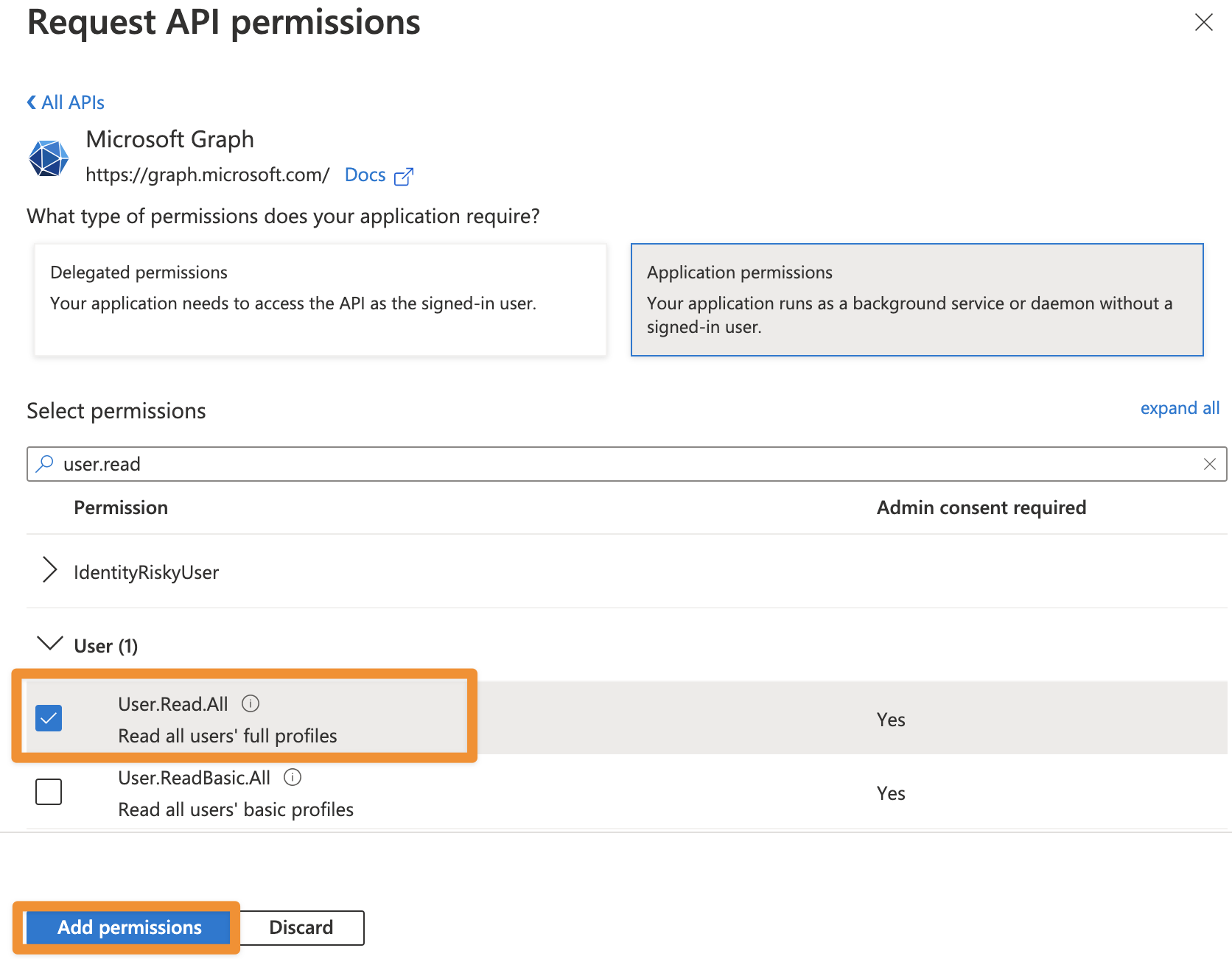
From SAML version 6.3.0 or User Sync 2.7.0 User Sync also supports syncing the profile pictures of users in Azure AD. To be able to use this feature, you additionally need to add User.Read.All as permission.
Click on "Grant admin consent for ...".
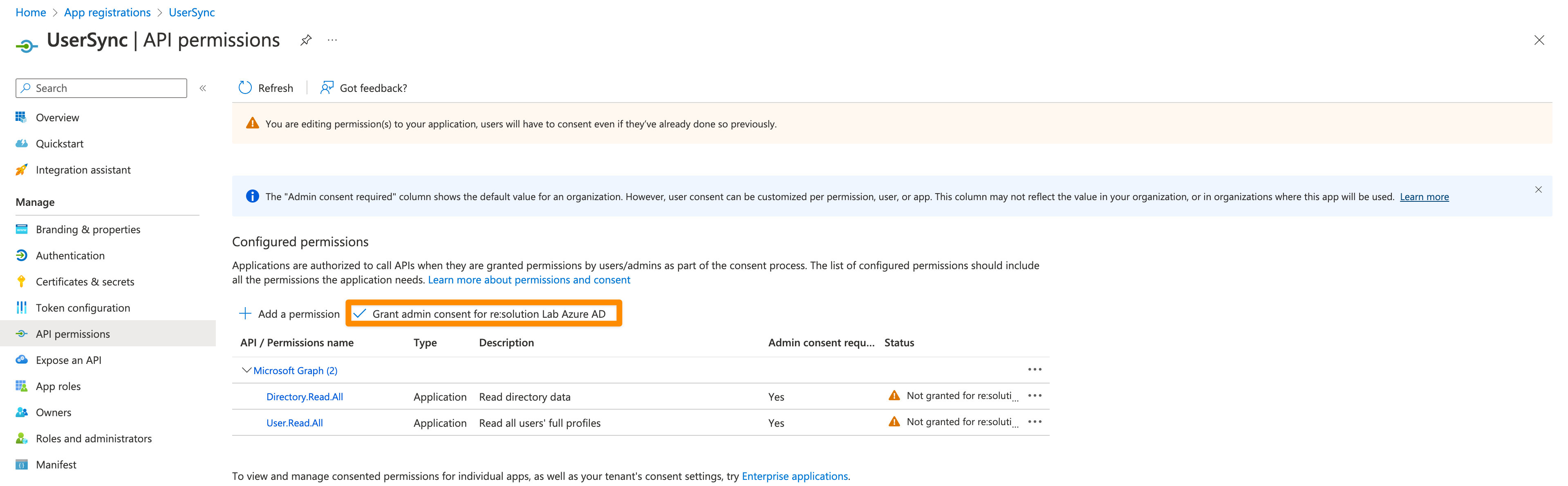
It should look like this after granting admin consent:
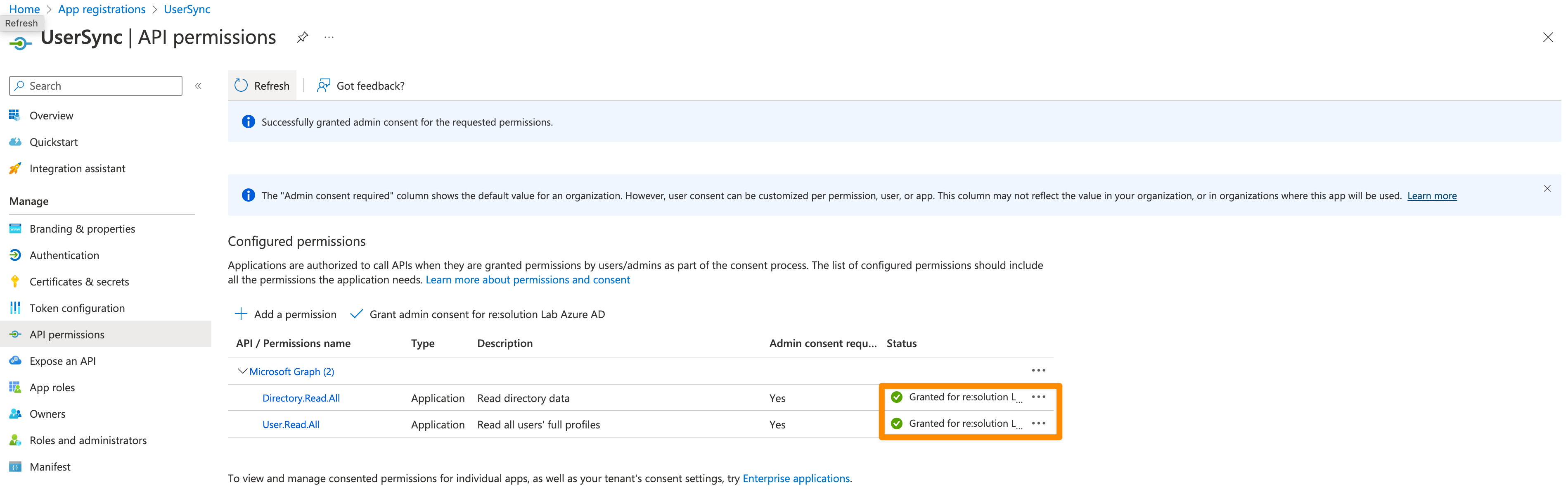
For the next step, click on Certificates & secrets in the left panel, and then click on New client secret.
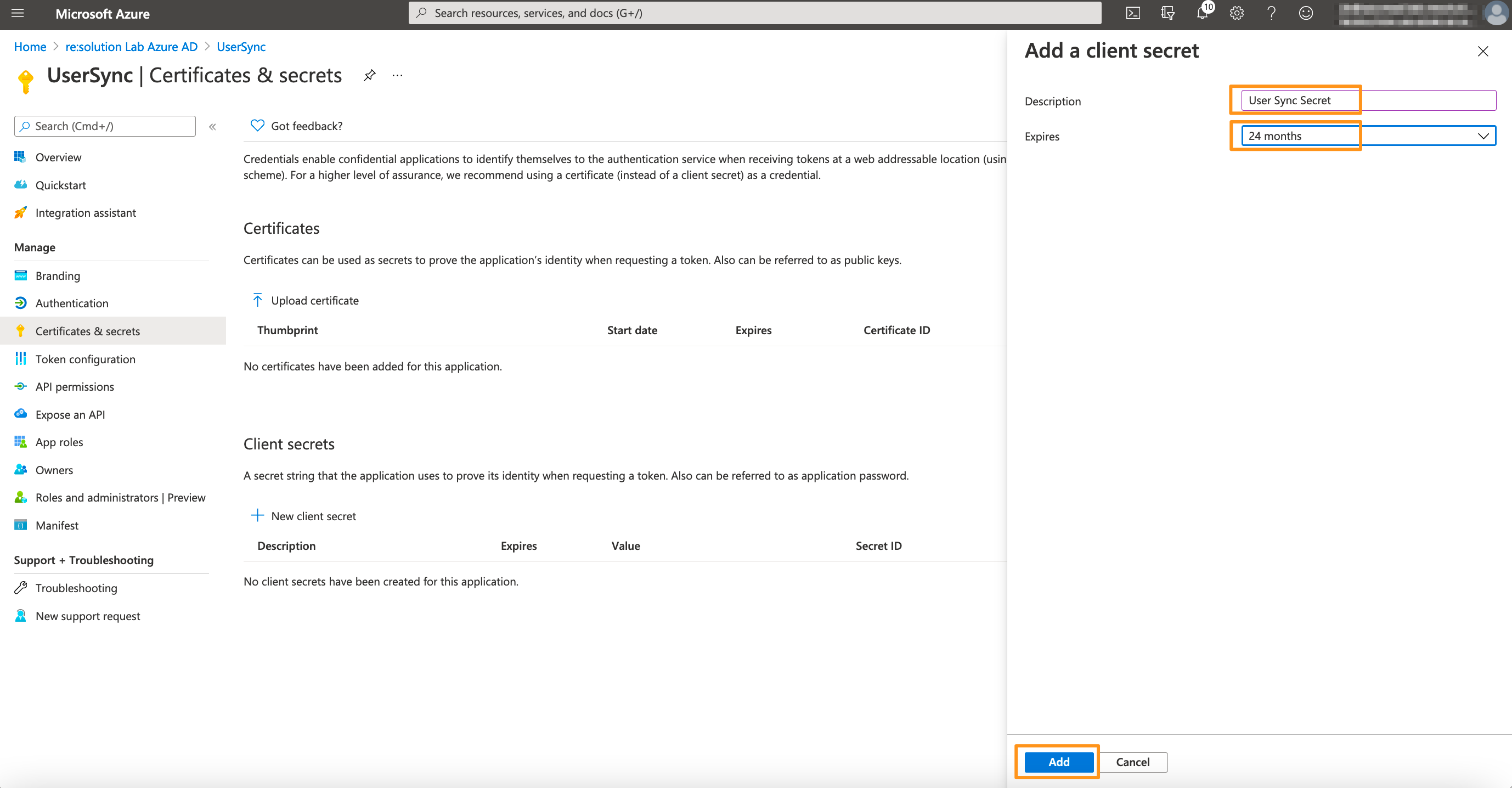
Enter a description for the secret and also set an expiry date. Click on Add to confirm.
Please note that your secret will expire after 24 months. If syncs start failing in 24 months, you must create a new secret and update the secret in the connector.
Your Client secret will display only once, thus copy the secret. Of course, it is possible to create a new secret, if you lost your secret.
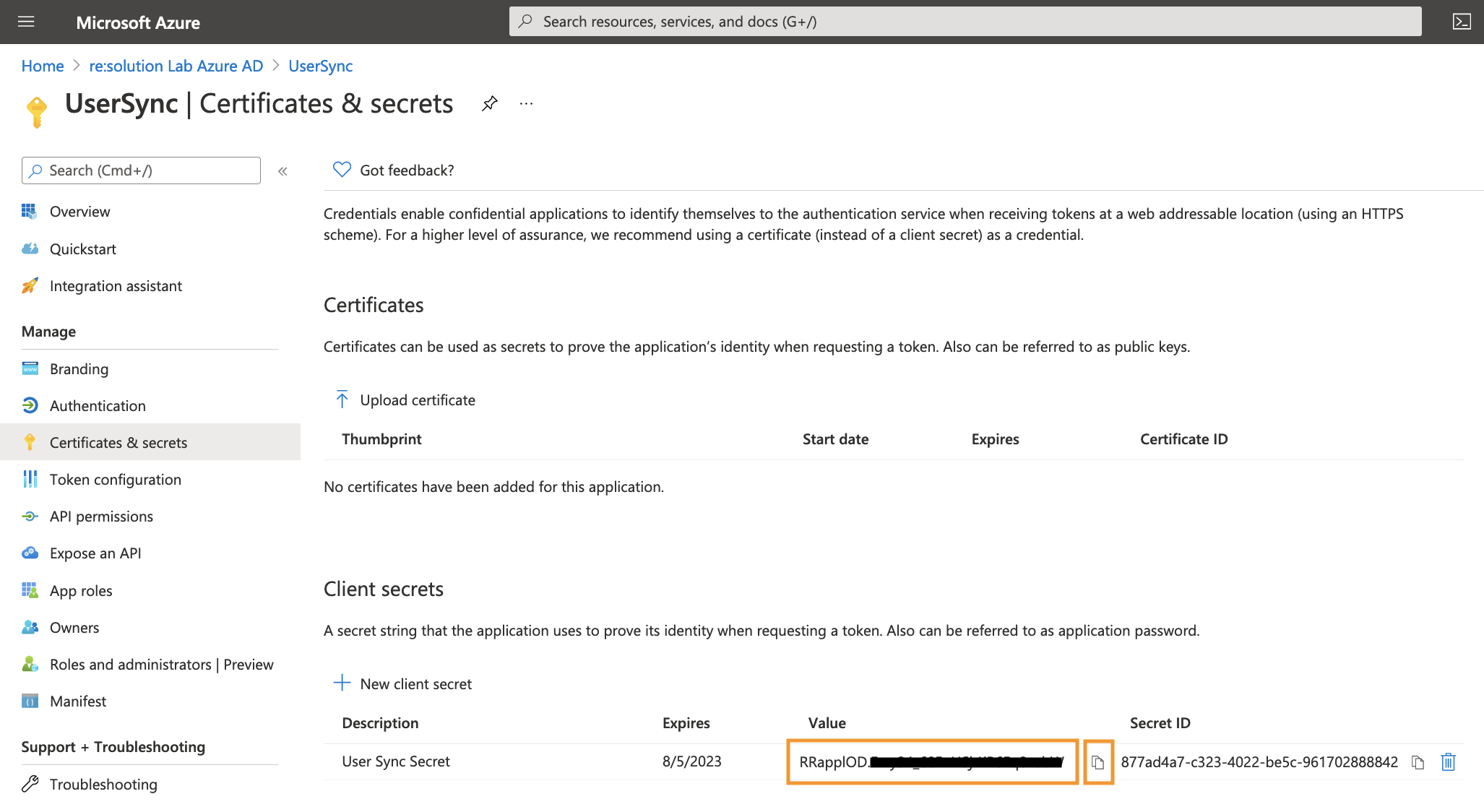
Go overview page of the Microsoft Entra ID app. Copy the Application ID and the Directory (tenant ID). Now, it is time to head over to your Atlassian application.
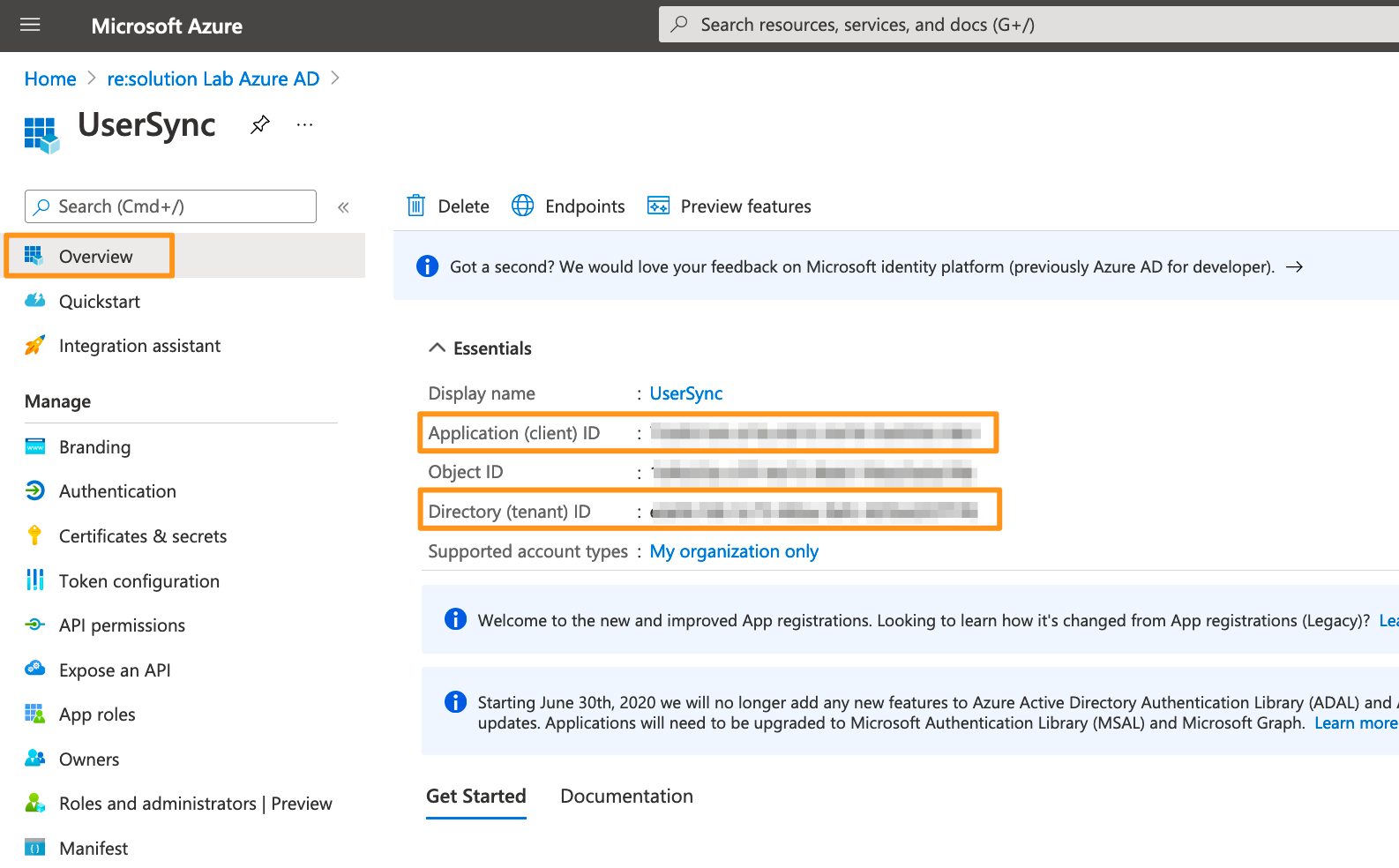
In your Atlassian application, go to User Sync, click Create Connector, and choose Azure.
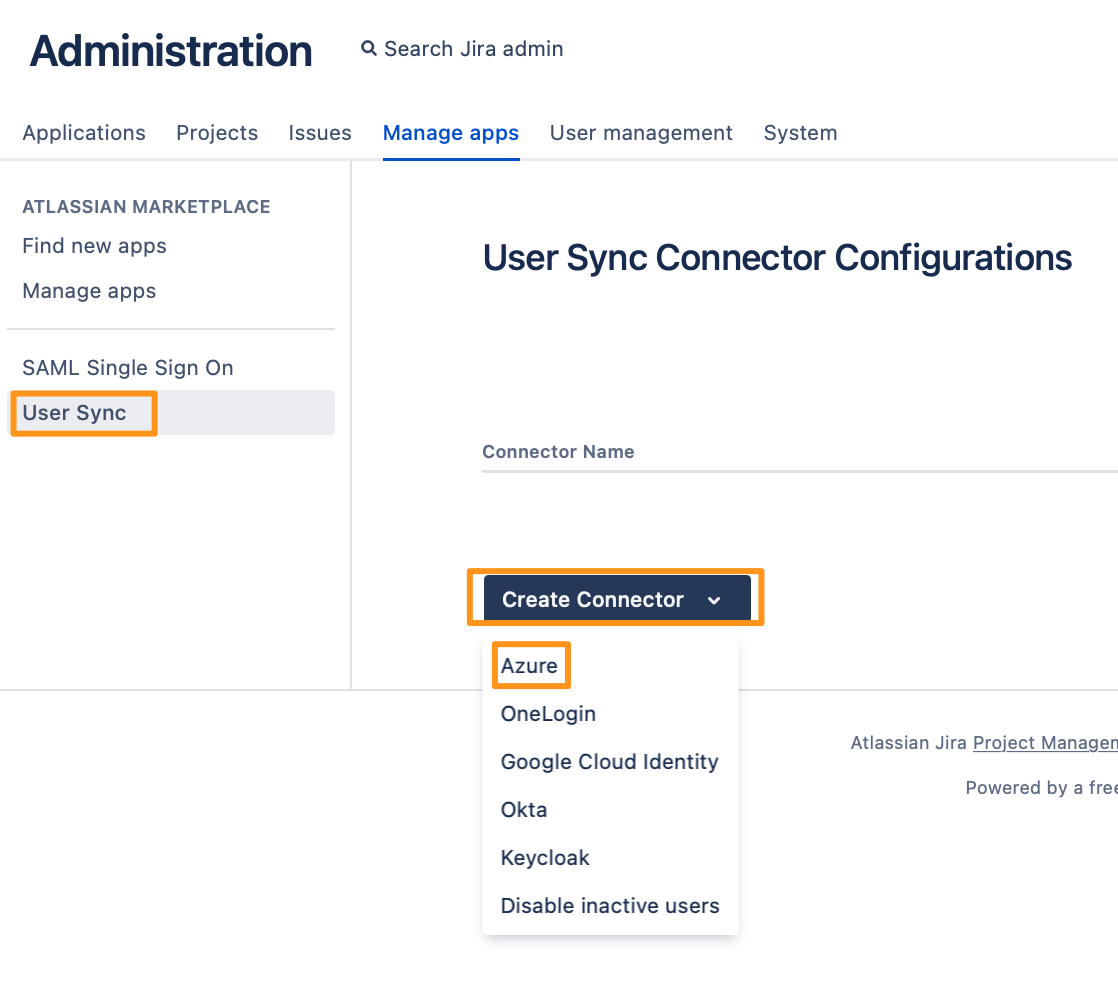
Add the Application ID, Directory ID, and the Application secret. Use the Save and Test Connection button to check whether Azure's API endpoints are reachable and API permissions are set correctly.
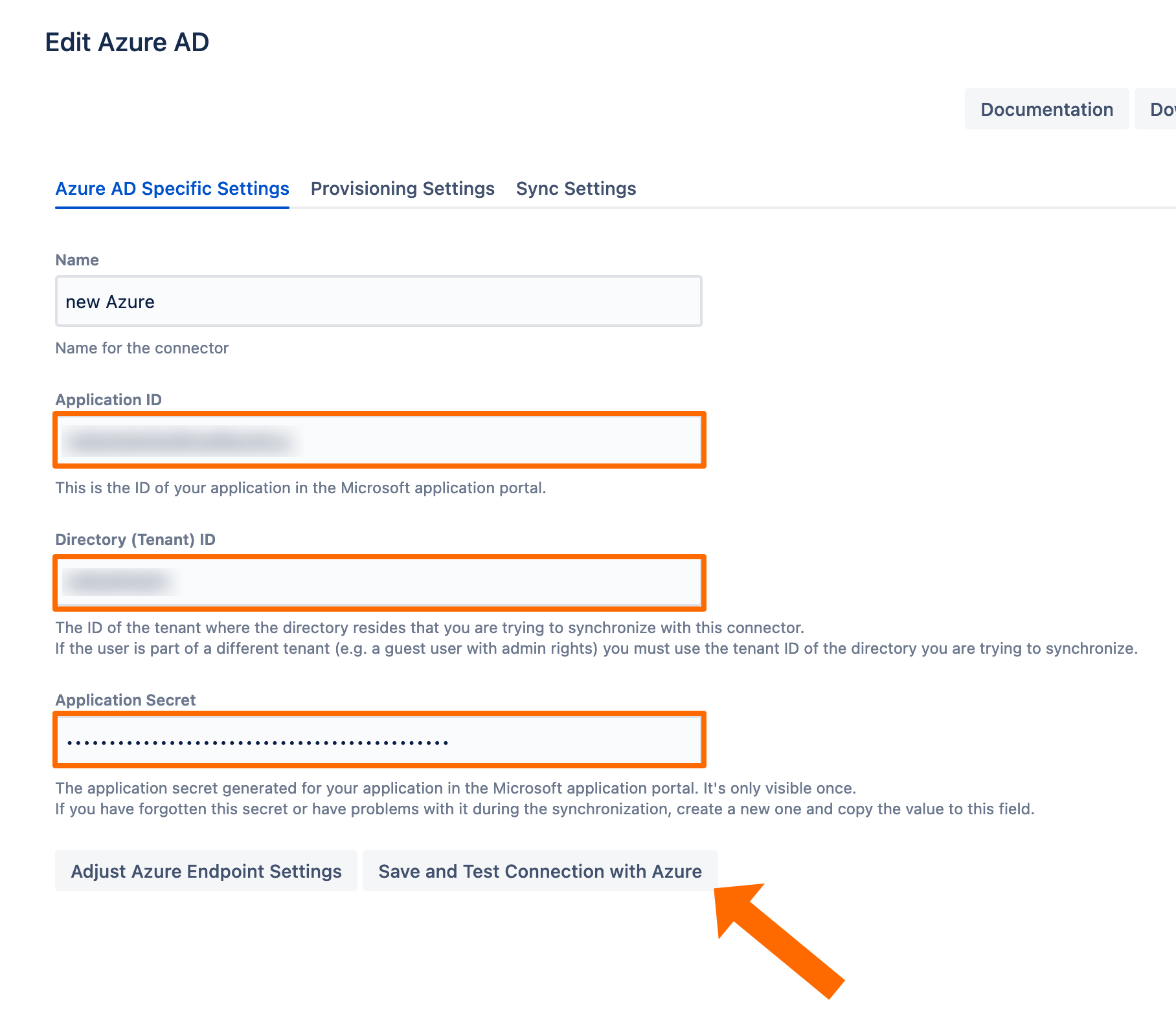
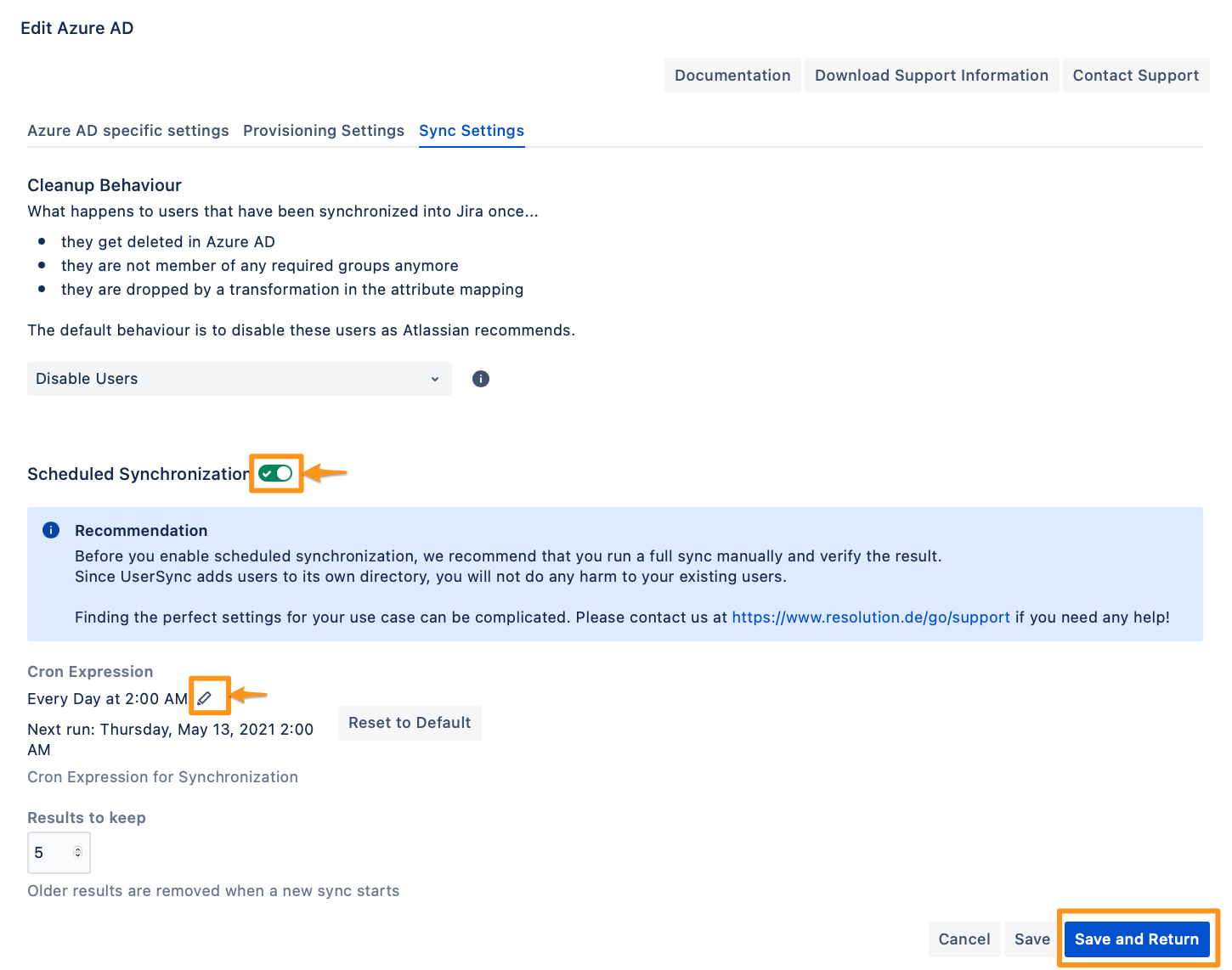
To take full advantage of User Sync, go to the Sync Settings tab and enable "Scheduled Synchronization". You can control the sync interval via a Cron Expression.
Do not forget to save your configuration by clicking on "Save and Return".
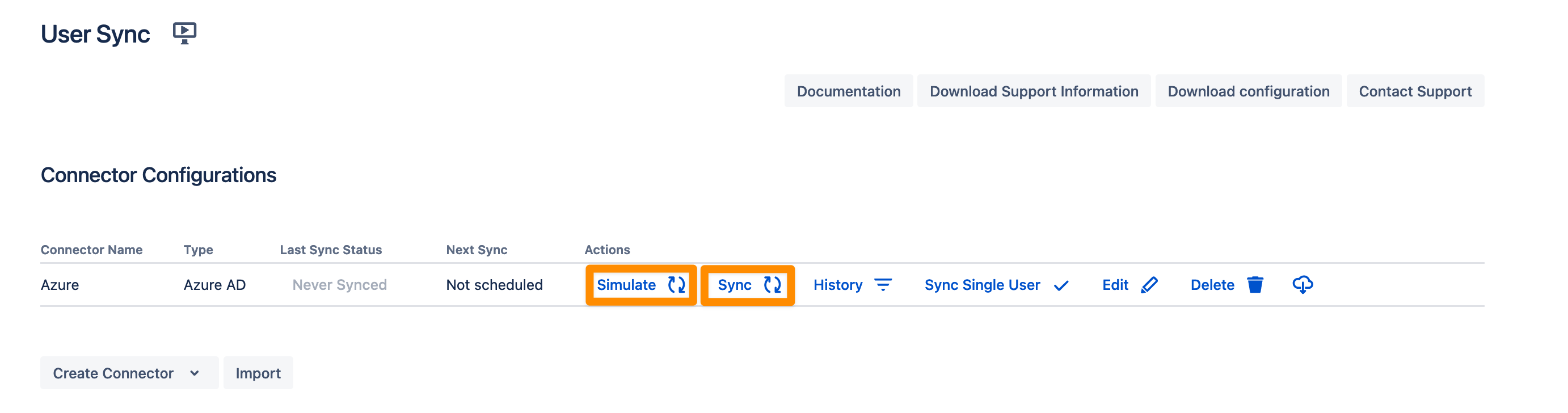
You are now ready to commence either a simulated or a full sync. By simulating the sync first you will be able to verify your configuration and see what changes User Sync would apply like what users will be added, modified, or not modified. With the full sync, User Sync will apply those changes. Both sync actions will run a full sync and will have the same sync duration. For more information on the sync simulation, please refer to Using the Simulated Sync Feature.
Configure SAML SSO
For the next steps, please go to Manage apps (or addons), choose SAML SSO and click Configure.
First Steps - Wizard
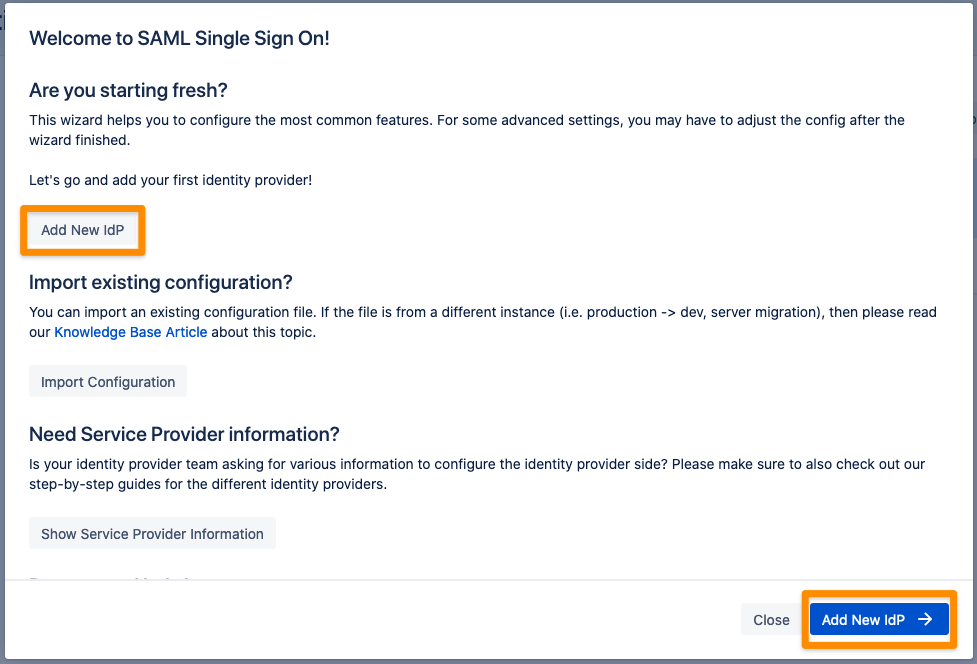
After you clicked "Configure", the Wizard will be triggered. If not, or if you want to add another Identity Prover (IdP) to your existing configuration, click on "+ Add IdP". This guide assumes, that there is no IdP configured.
The Wizard greets you with information, click on "Add new IdP" to proceed.
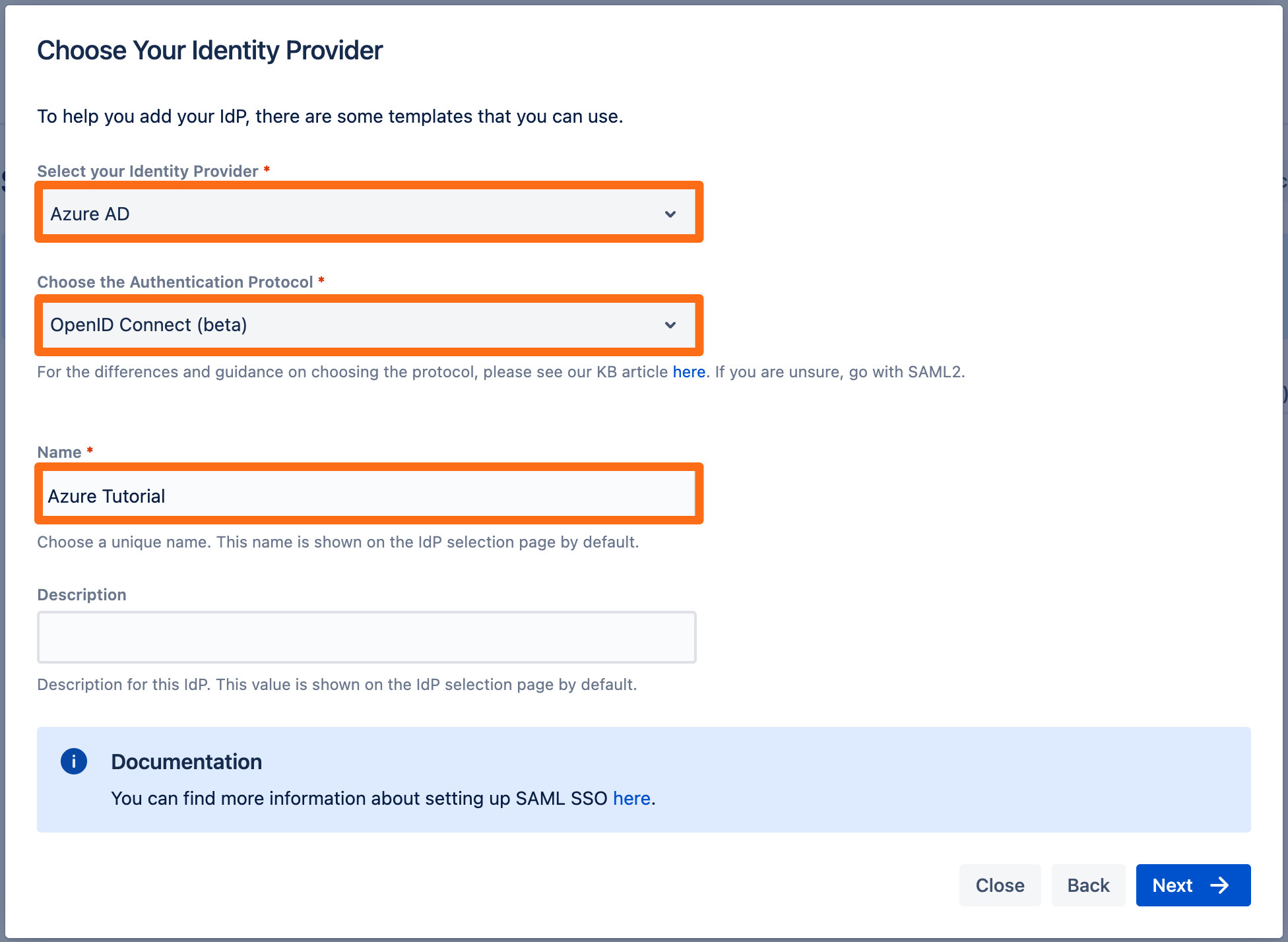
Select Azure AD for your identity provider and select OpenID Connect for the authentication protocol. Enter a unique name and click Next to continue.
Copy the callback url to your favourite text editor. 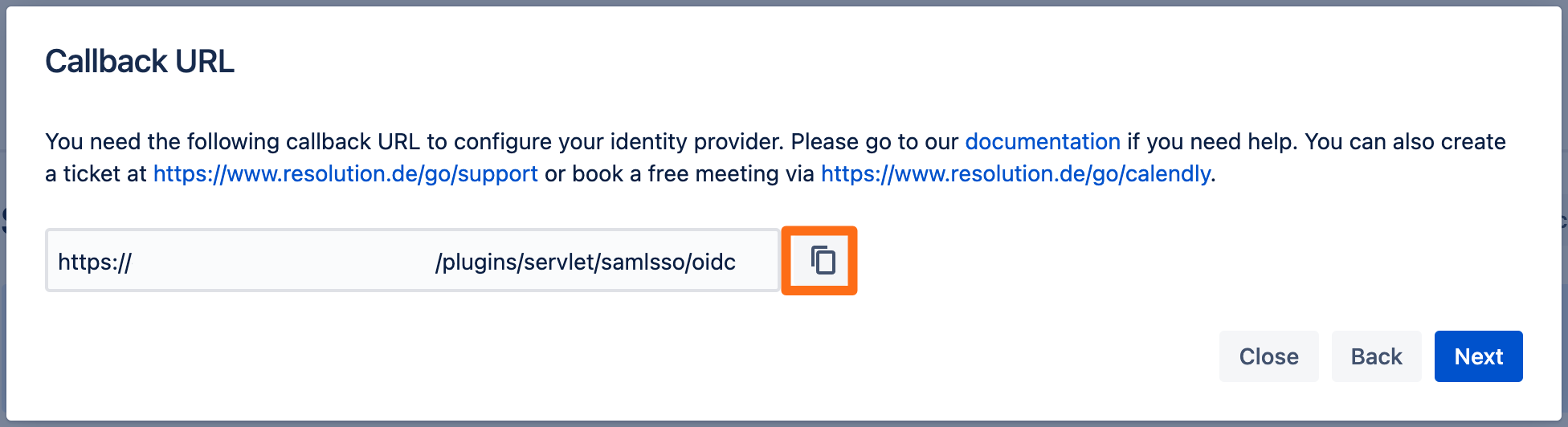
Next, go to https://portal.azure.com.
Then, click App registrations and click New registration.
Enter an app name and the copied oidc callback url into the Redirect URI. 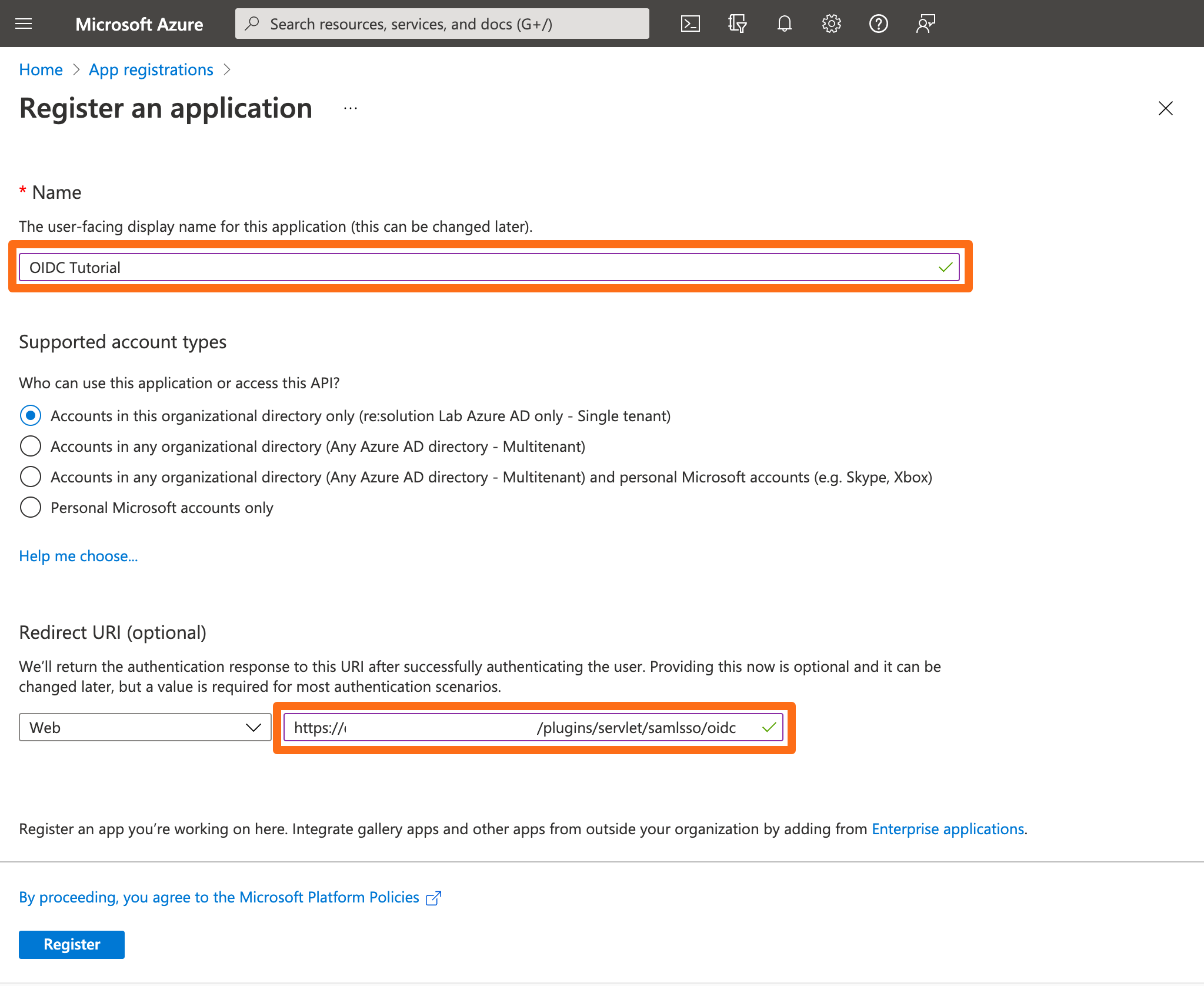
After the creation of the app, copy the Application (client) ID and the Directory (tennant) ID into a texteditor of your choice.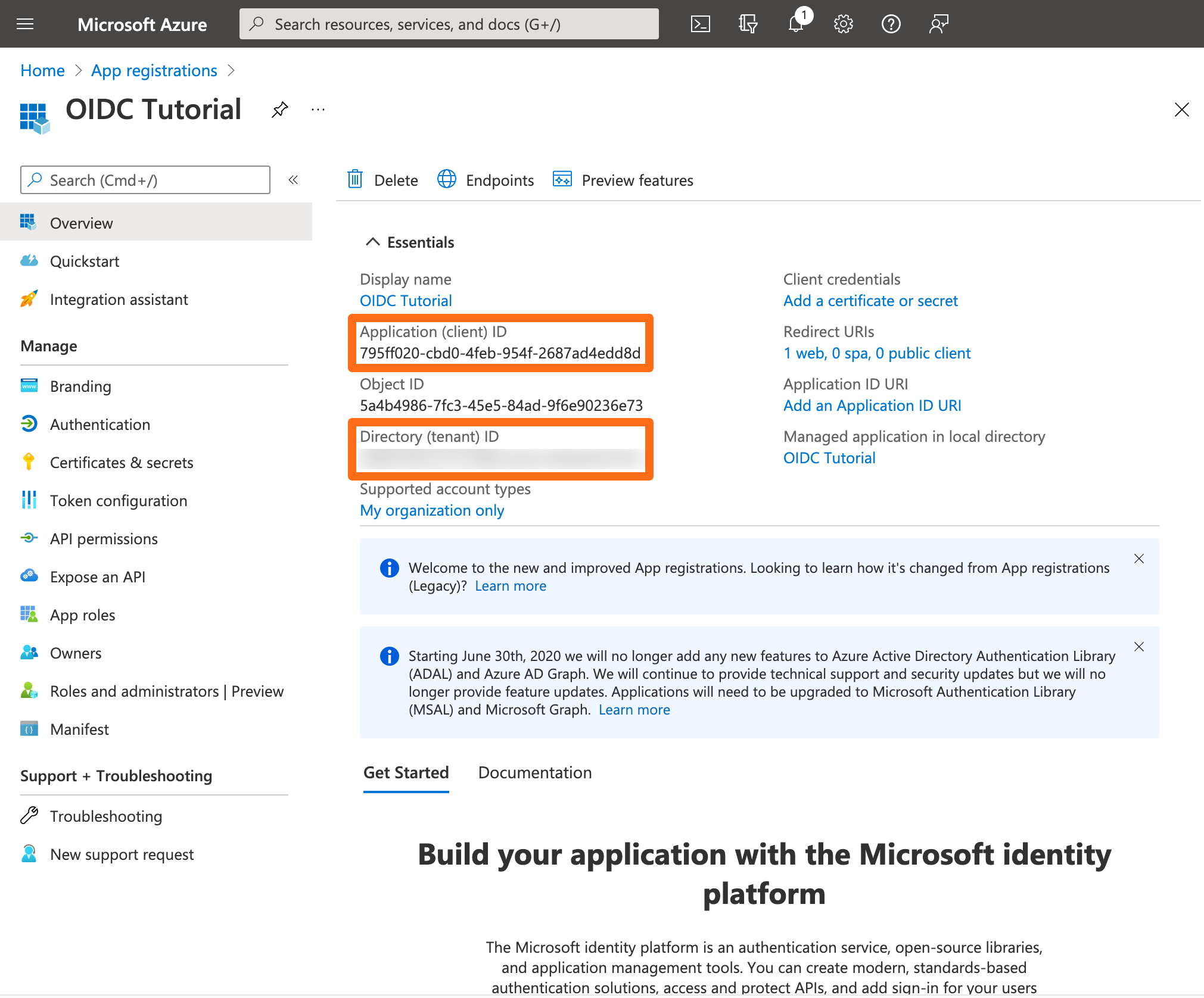
Next, go to Certificates & secrets and click New client secret.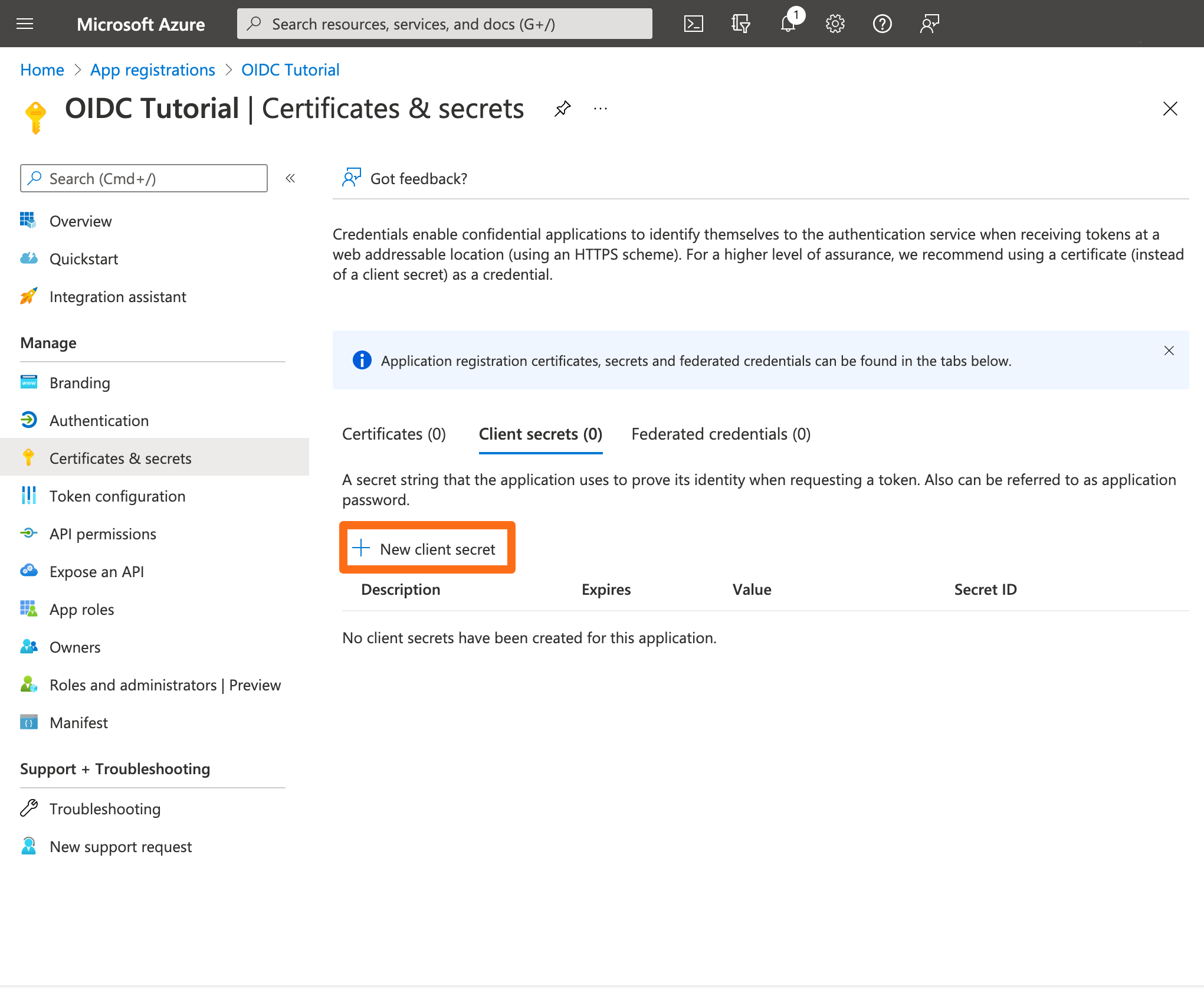
Set the expiry to your needs (we recommend 24 months) and click Add.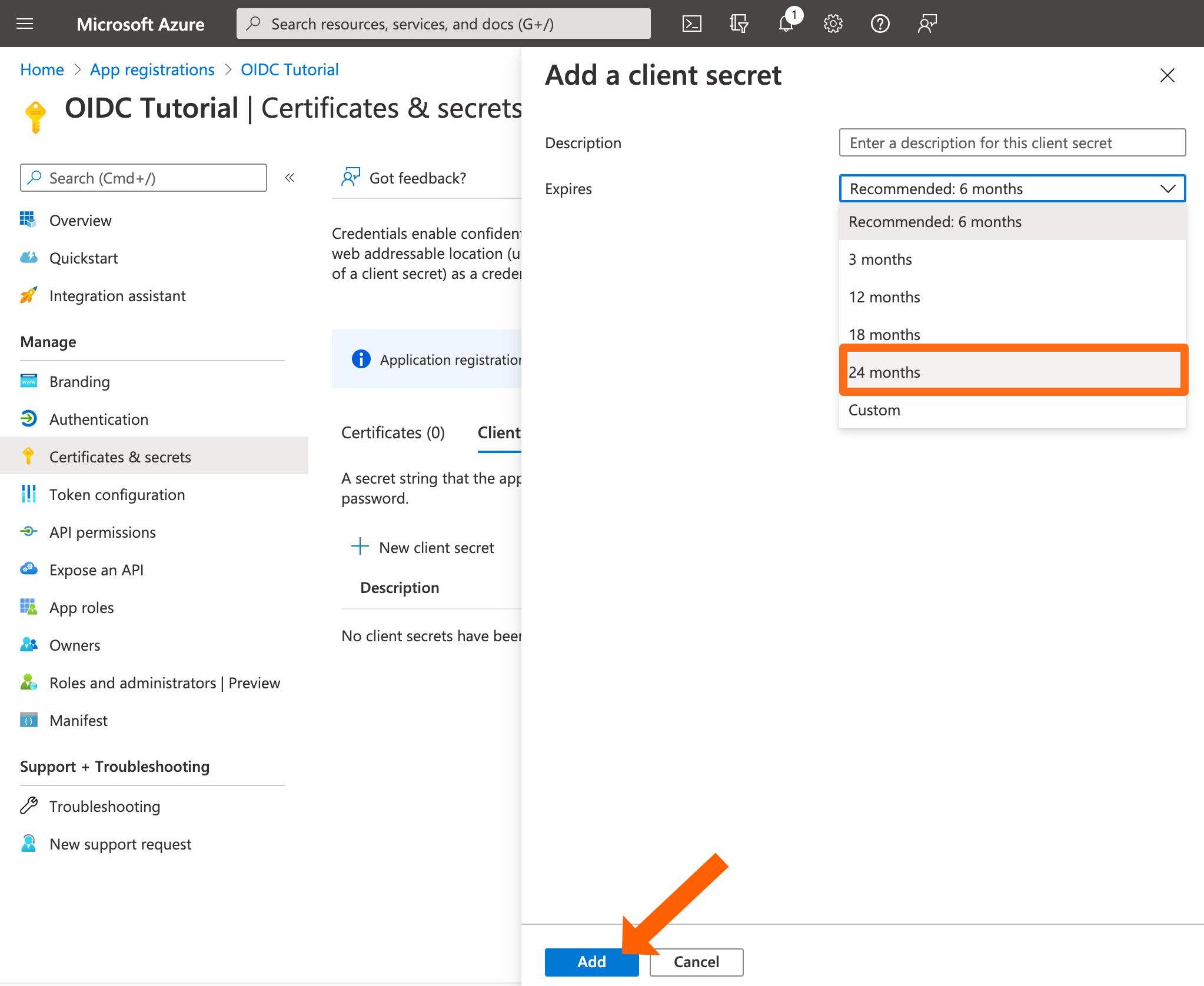
Copy the secret value (but not the id) to your editor.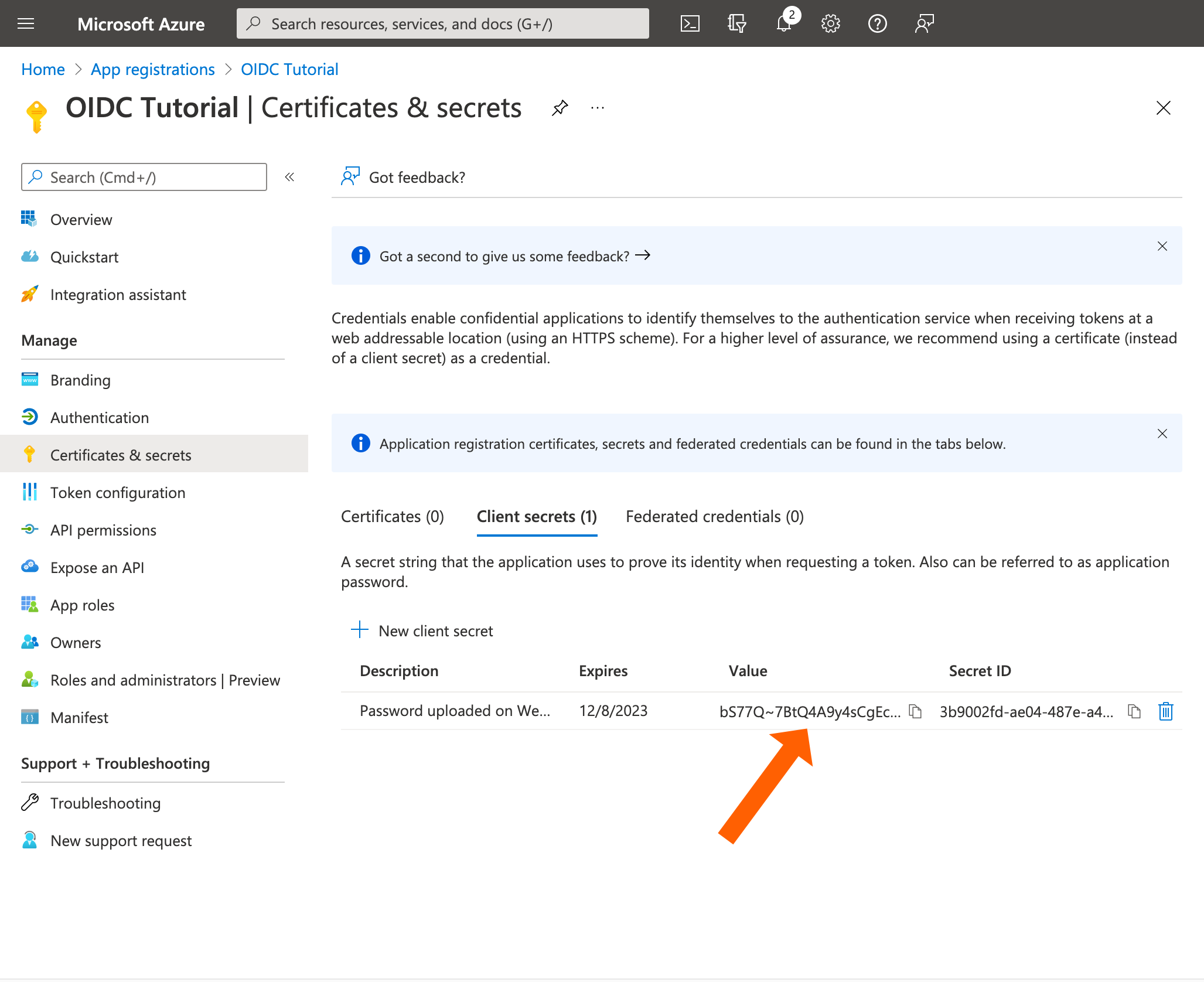
Next, go to Token configuration and click Add optional claim.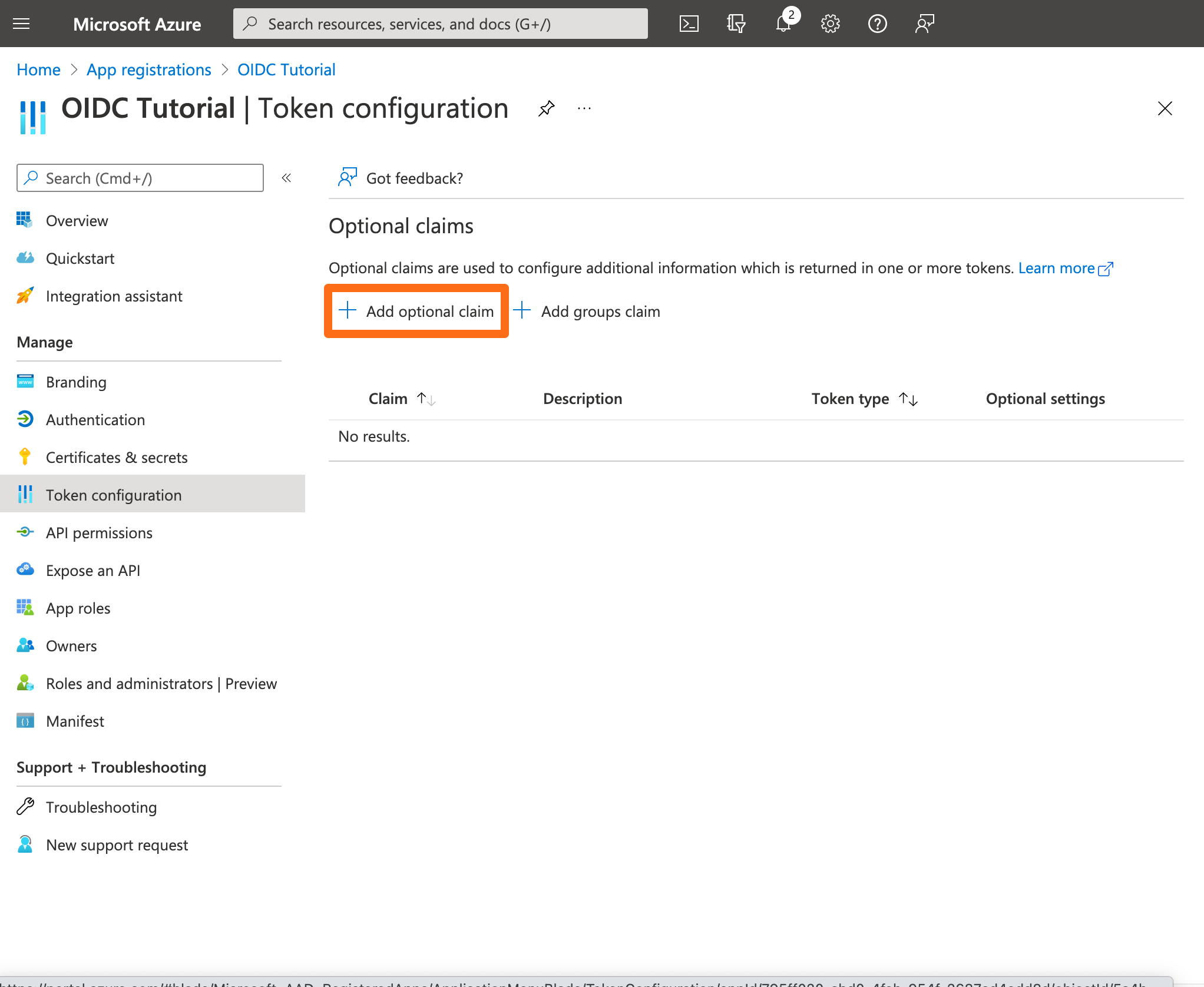
For the Token type, use ID. For the claim select UPN. Click Add.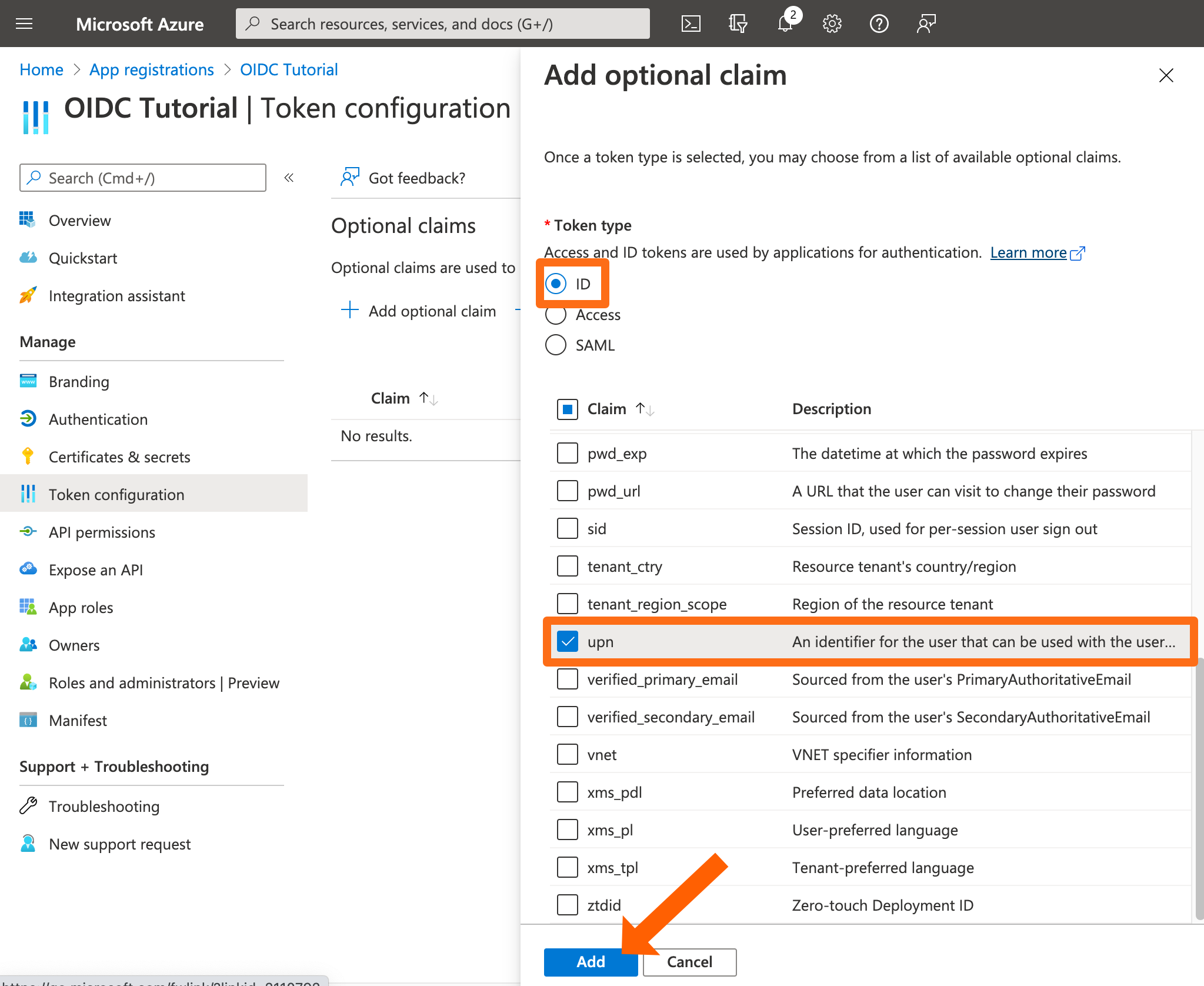
If Azure asks for the Microsoft Graph profile permission, please do so. 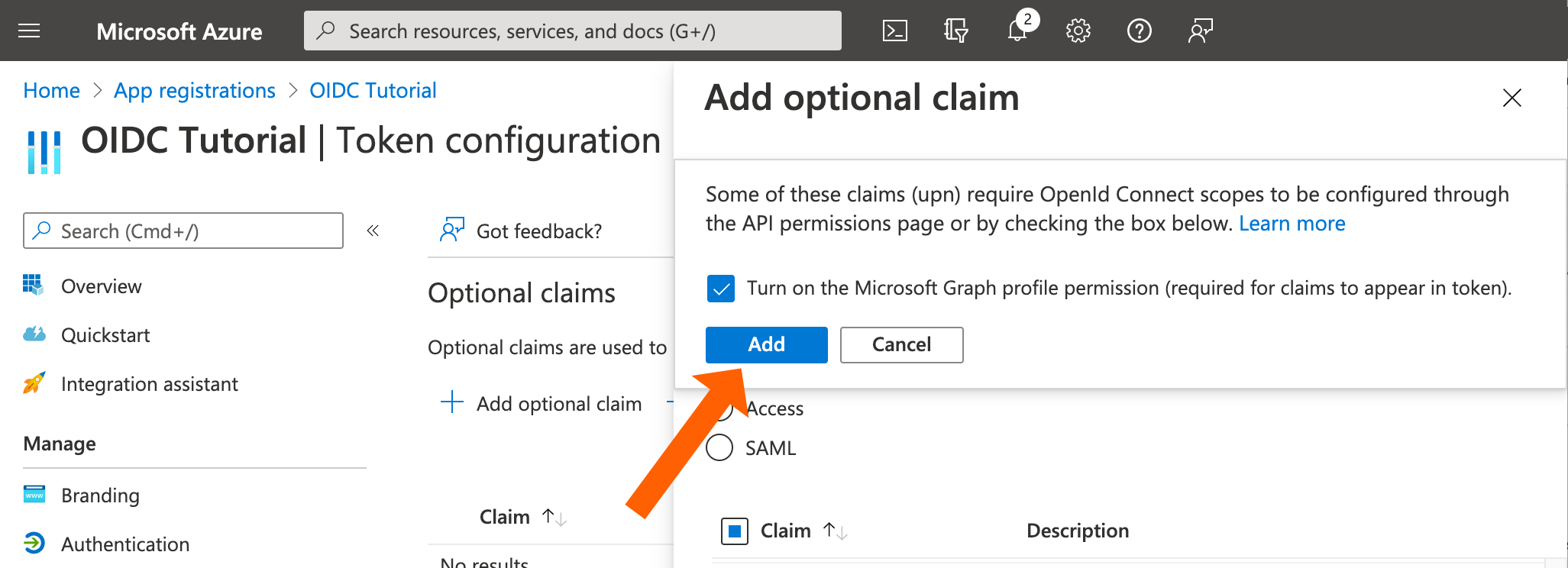
If you have guest users in Azure AD who would also use SSO, then you would need to do the following:
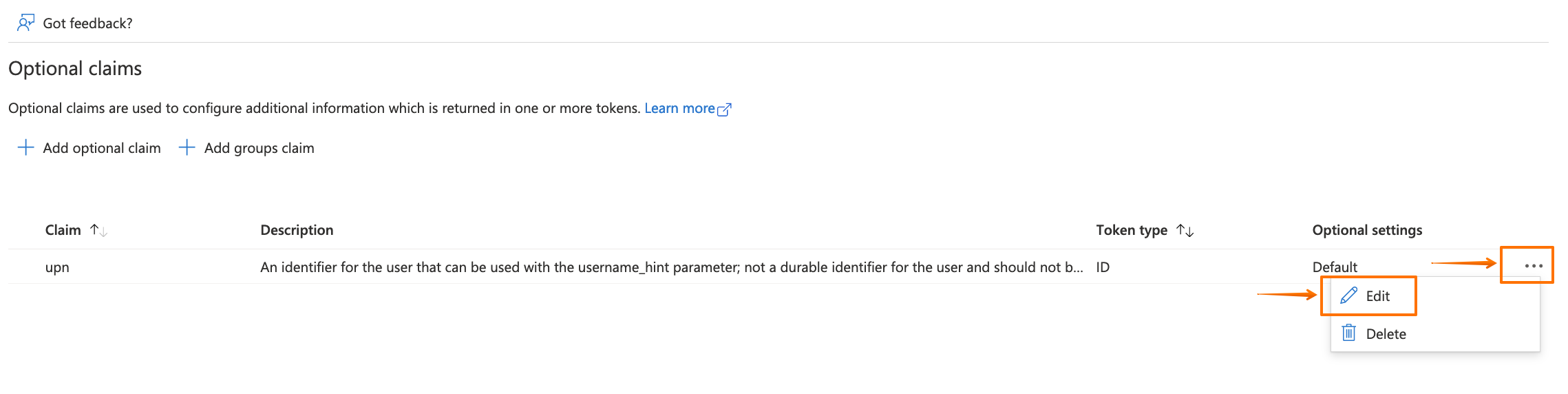
Click on "..." for the upn claim, and click on Edit.
Then enable the Externally authenticated option, and click on Save.
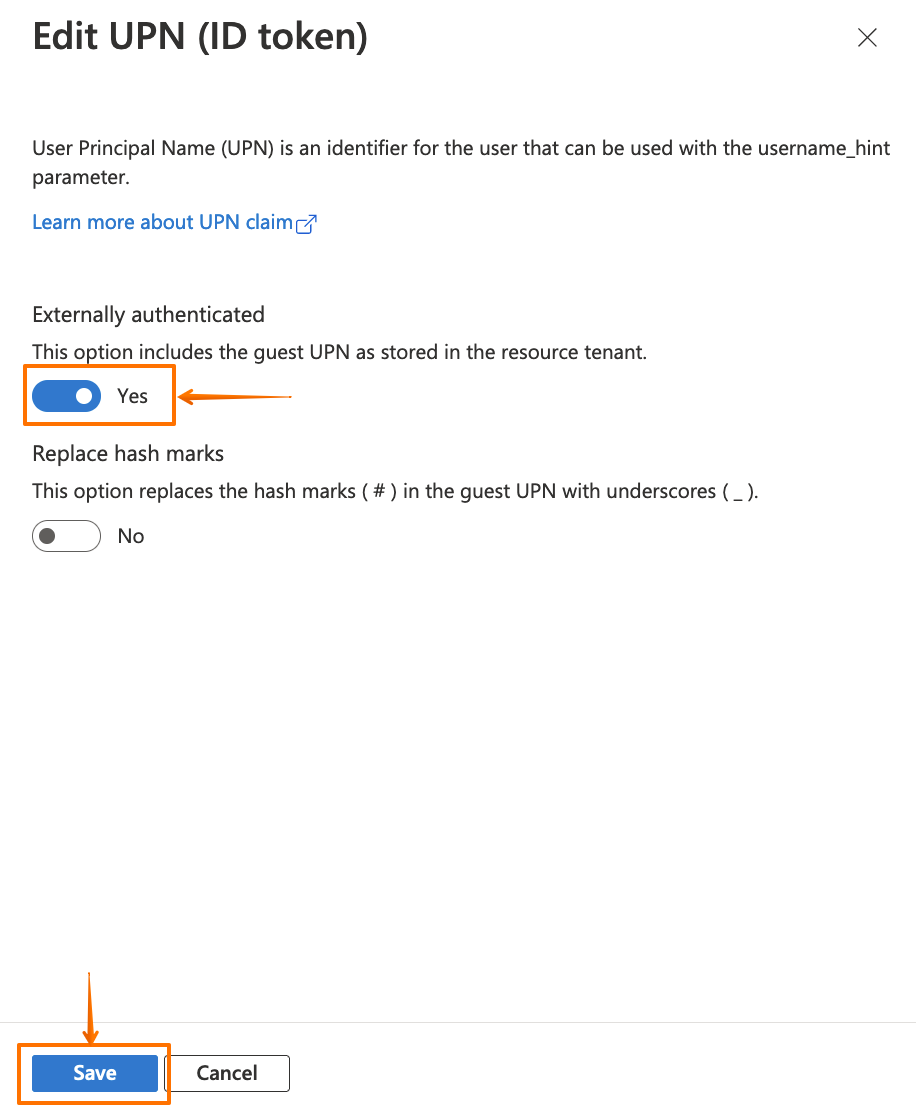
Now, go back to your Atlassian application to finish the wizard.
Enter the Client ID and Client Secret from before.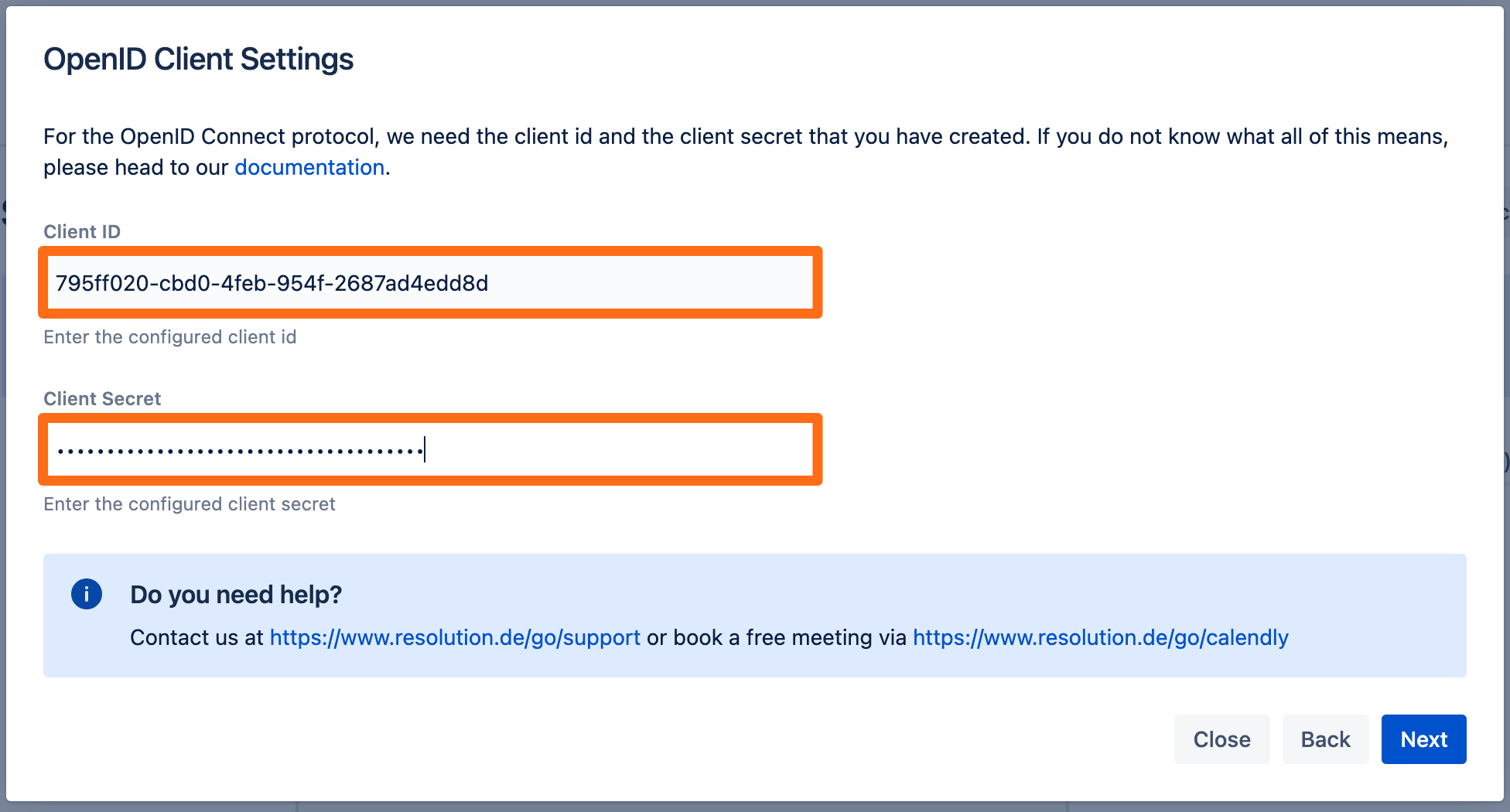
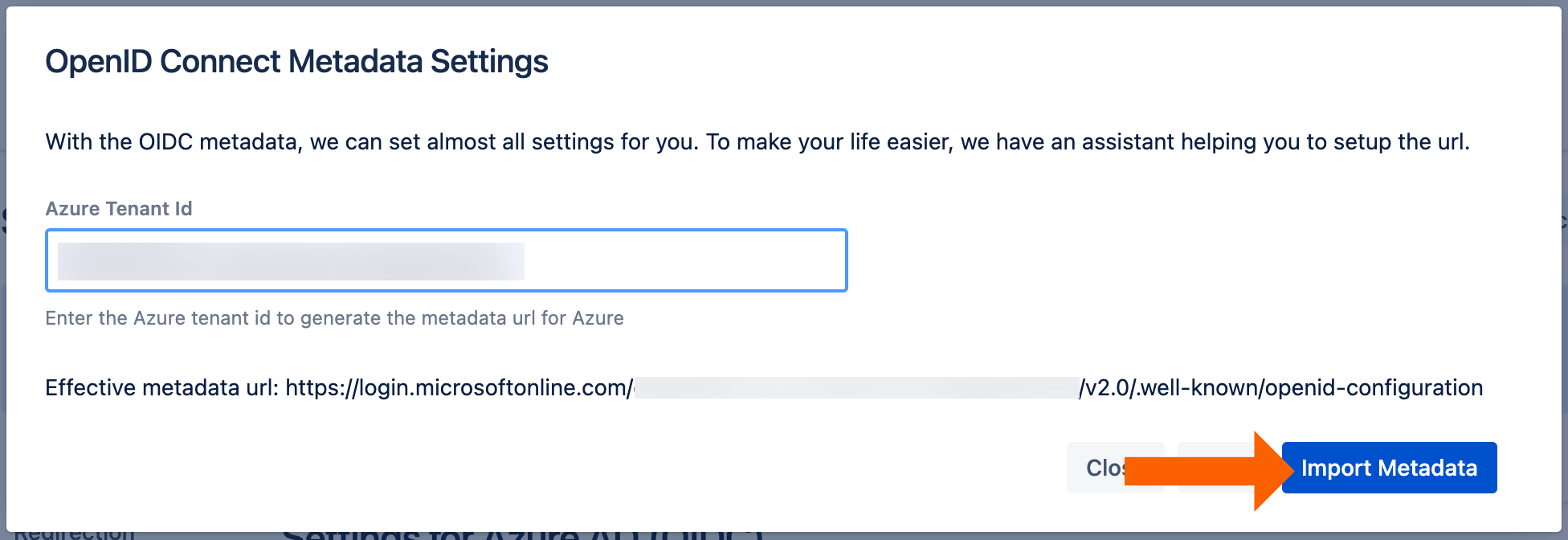
Next, enter the Azure tennant ID from before and click the Import Metadata button.
You will see this message if the import was successful.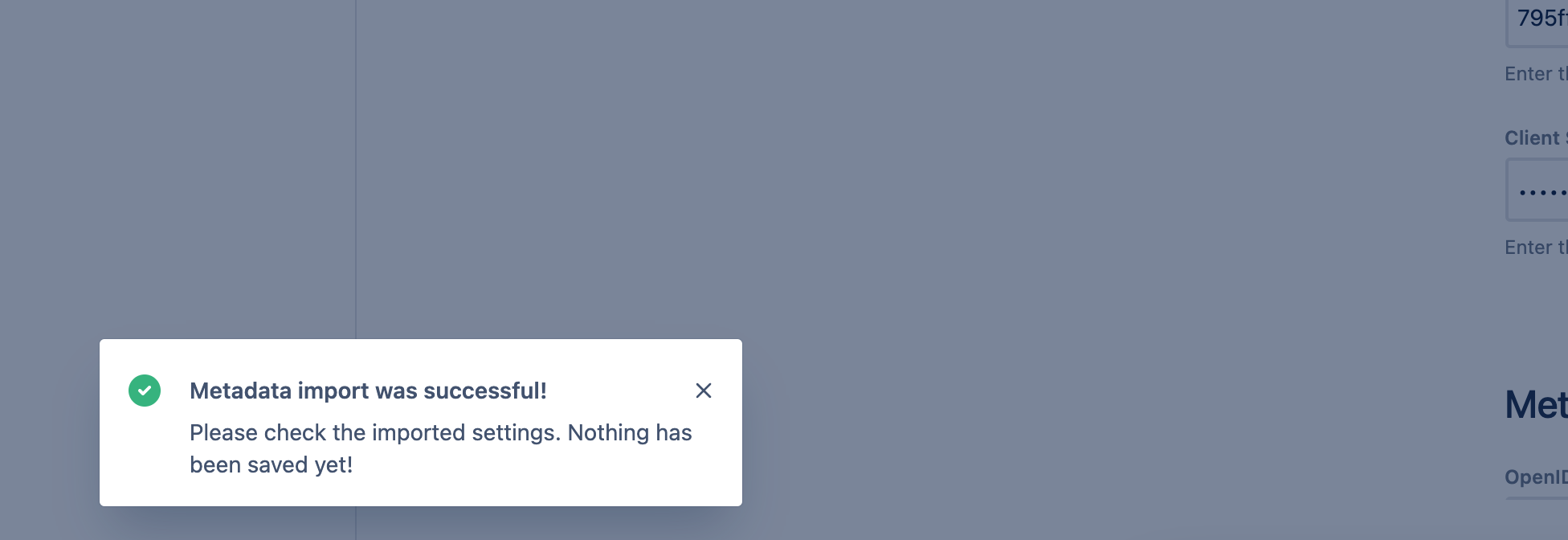
To finish the wizard, click Save and Close.

Next, scroll down to the User Creation and Update section. Choose Update with UserSync for the User Update Method.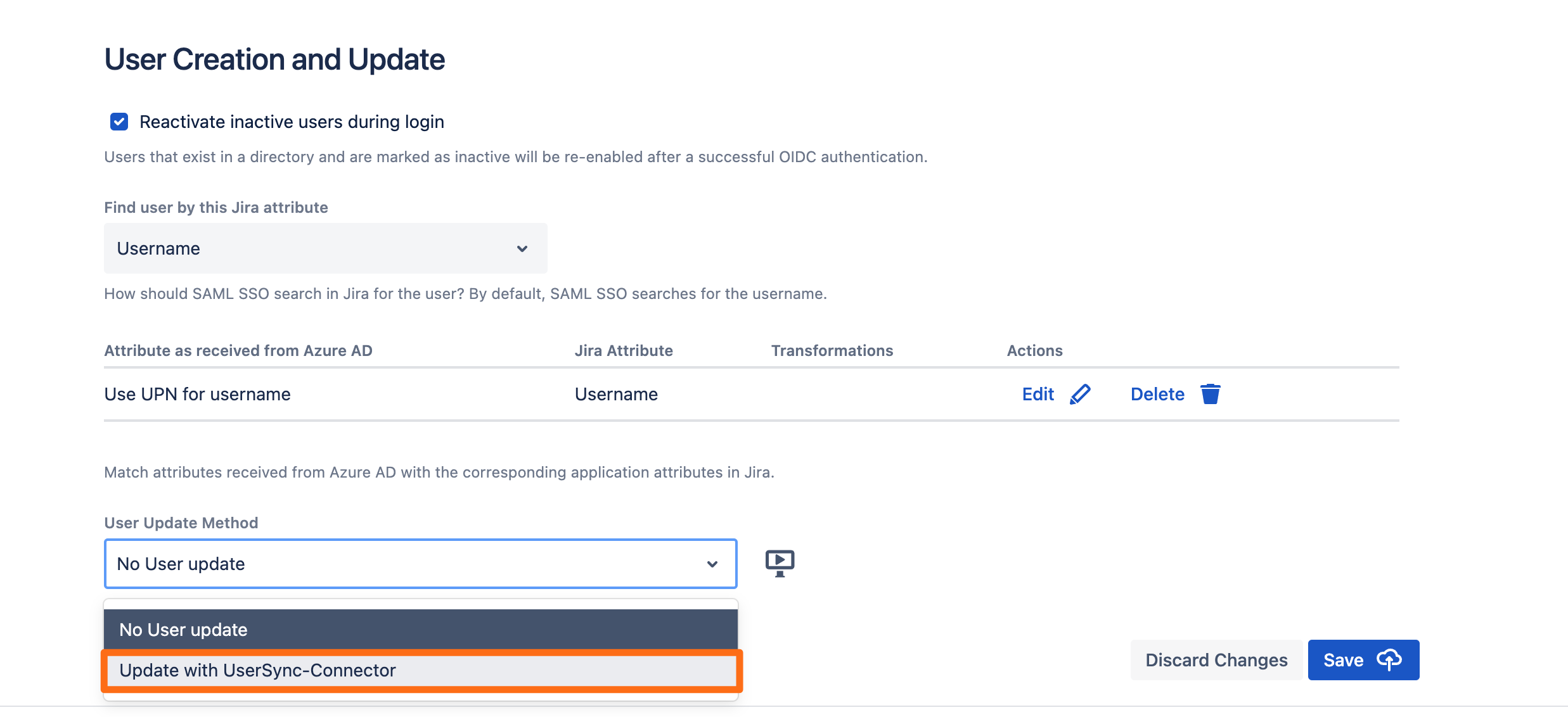
Select the connector you have created before and click Save.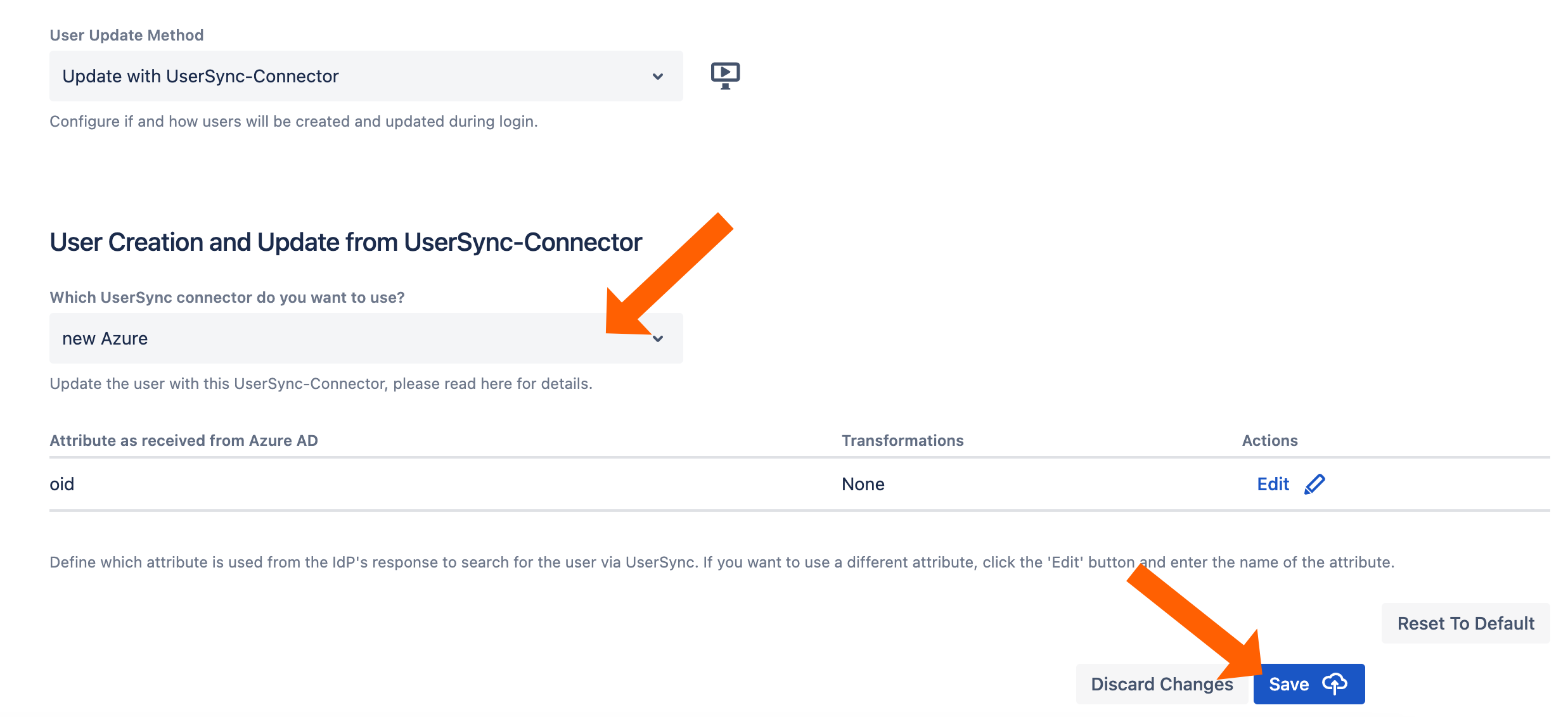
Testing SSO
To test you configuration, go to the System & Support section of the app and scroll down to the Tracker List.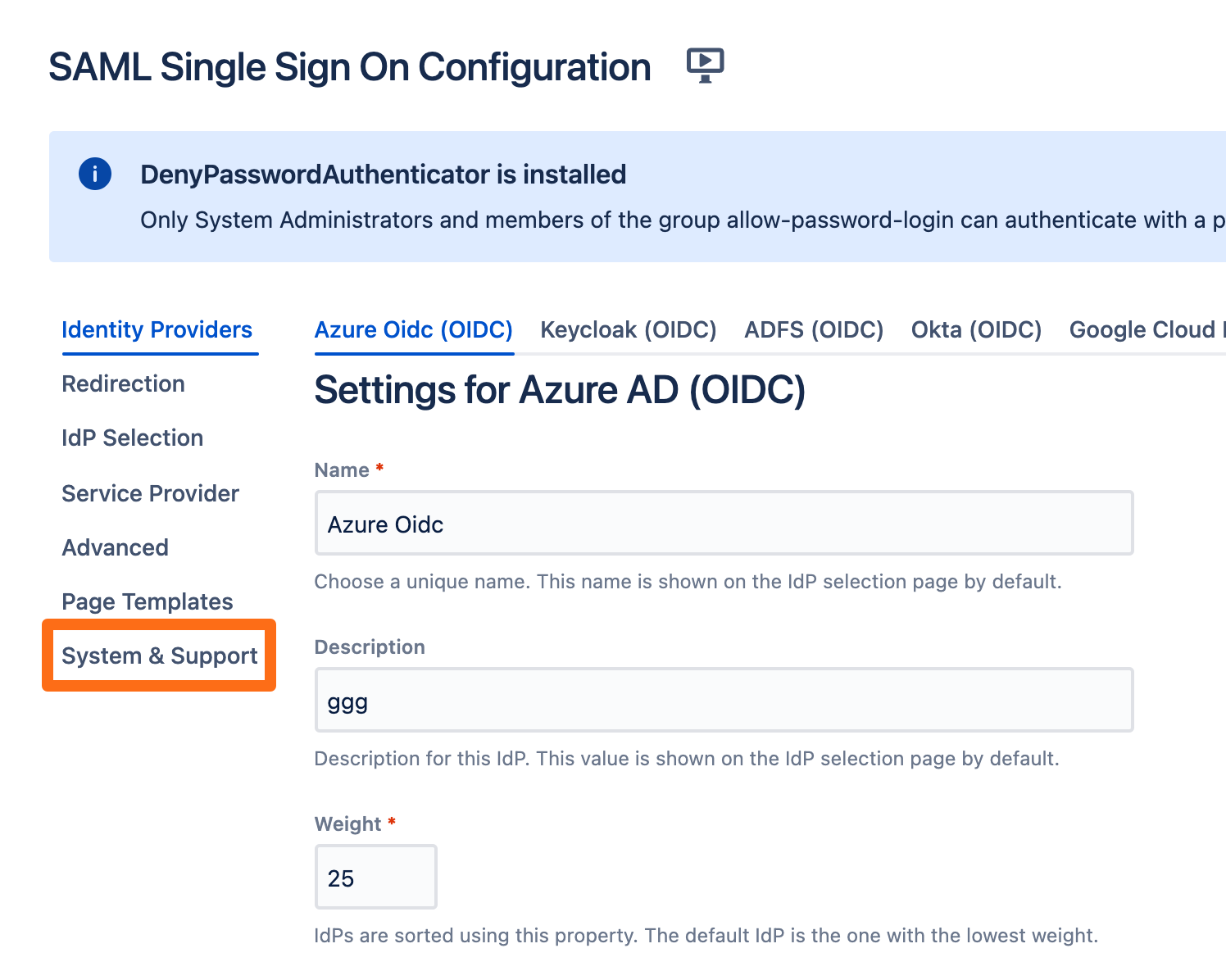
Click New Tracker. If you have more than one identity provider configured, you must choose which configuration should be used for the log in test.
Copy the test url and open the link an incognito web browser. If something goes wrong during the test, you can easily create a support ticket that includes this tracker by click Contact Support. Additionally, you can contact us by going to https://www.resolution.de/go/support or booking a free meeting via https://www.resolution.de/go/calendly.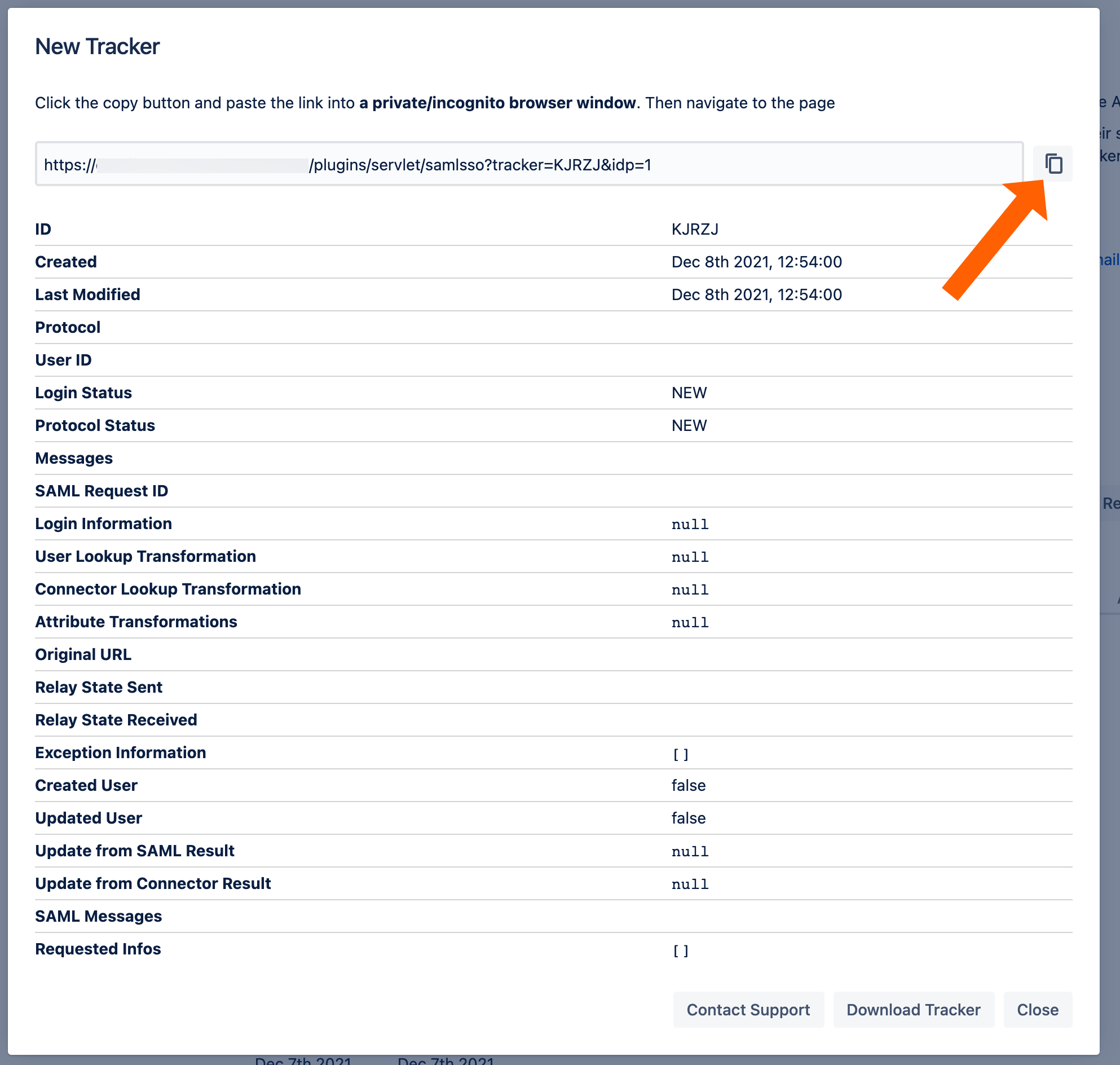
Redirect to SSO
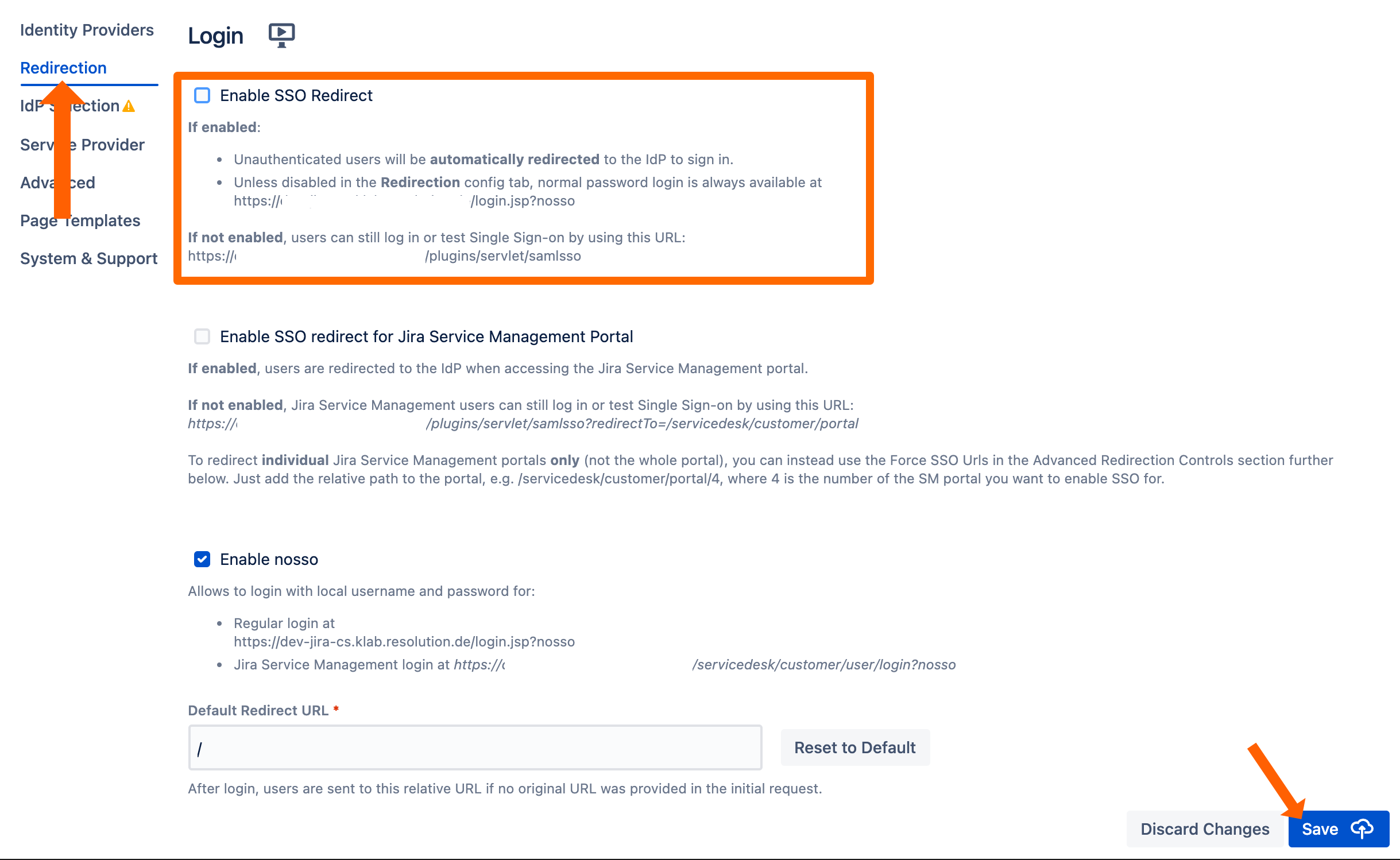
After a successful test, the next step is to configure the redirection. With the redirection setting, the app can automatically redirect users to log in via OpenID Connect.
Go change this setting, go to Redirection from the middle panel.
By checking Enable SSO Redirect, users will get redirected to the configured SSO provider for login. If you are running JSM, you find a second option below.
Click Save to finish the configuration