Okta with User Sync
Goal
Connect and configure Okta and your Atlassian product to work with the SAML SSO app in combination with User Sync.
Prerequisites
To use the SAML SSO app with Okta, you need the following:
an Okta subscription
SAML SSO app which includes User Sync already
admin access to your Atlassian product
Video Guide
The video below is an installation guide for setting up our SAML SSO app with Okta (watch on YouTube).
Step-by-Step Setup Guide
Install the SAML SSO app
In your host intance, open the in-product marketplace as described in the Atlassian documentation.
Search for "resolution saml" and click Install for SAML Single Sign On (SSO) by resolution Reichert Network Solutions GmbH.
After the installation is complete, do not click on Manage yet. The first part of the configuration is User Sync related,
please read the next chapter. The configuration of the SAML SSO app will follow at a later step.
Configure Okta for User Sync
Log in to your Okta organization as a user with administrator privileges.
Any type of administrator role is fine. If you limit this administrator role to manage only specific groups,
only users in those groups are synced. API tokens have the same permissions as the user who creates them,
and if the user permissions change, the API token permissions will also change.
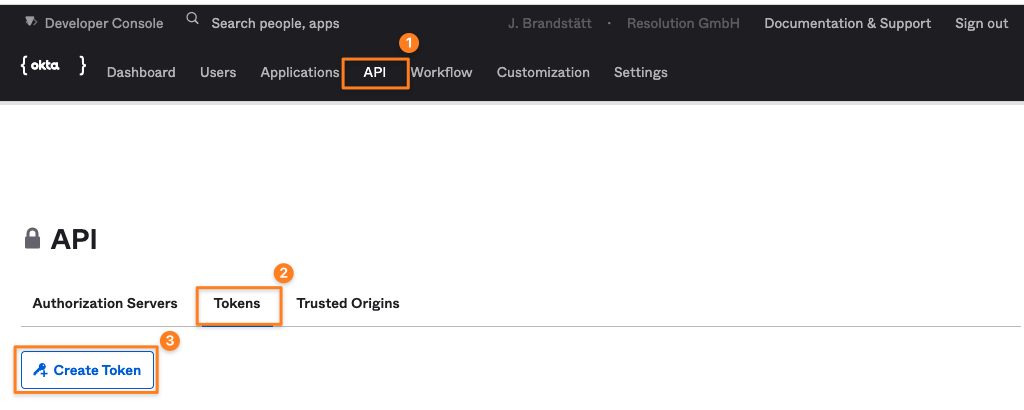
Okta Regular UI
Click on API (2)
Click on Tokens (3)
Click on Create Token (4)
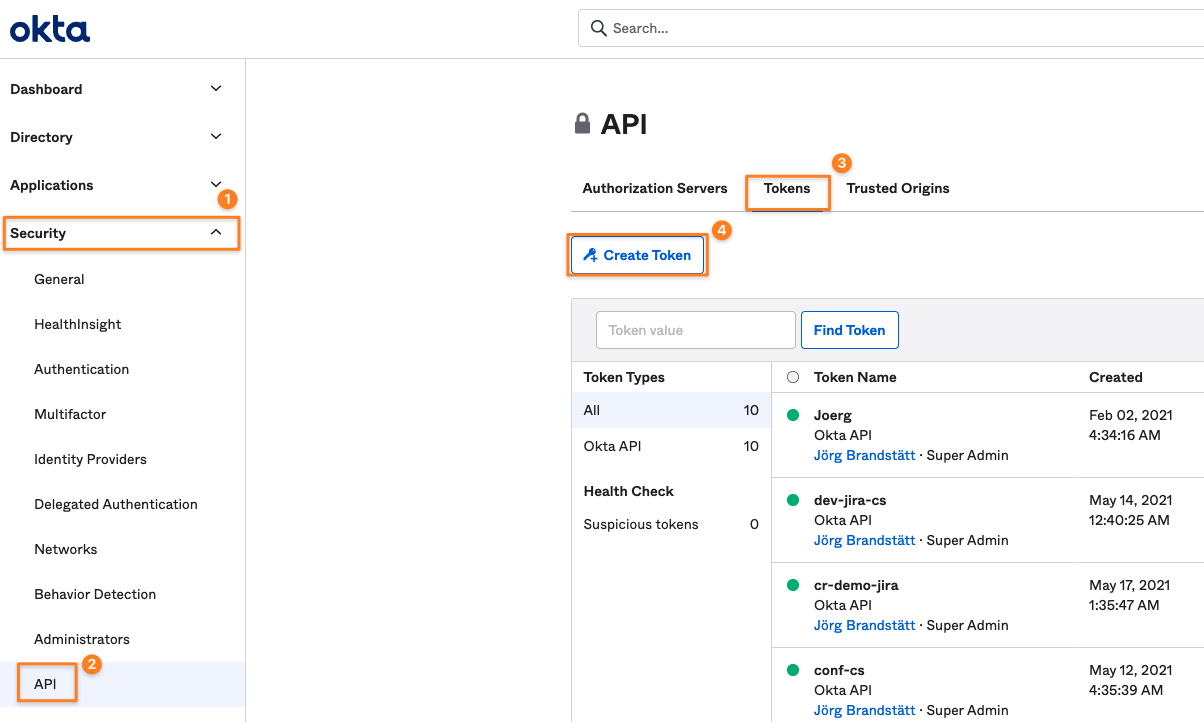
Okta Developer Console/ Classic UI
Expand the Security node (1)
Click on API (2)
Click on Tokens (3)
Click on Create Token (4)
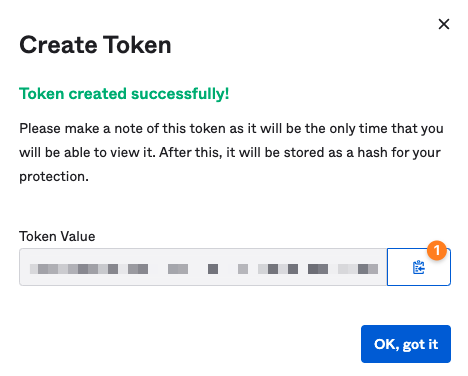
Name and Create Token
Name the token and create it
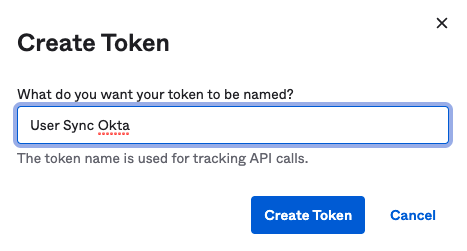
copy its value (1), it will be only displayed once. Of course, you can create a new token if you lost the old one
Create User Sync Connector For Okta
Navigate to the administration console for Jira, Confluence, Bitbucket, or Bamboo and search for User Sync here:
Confluence: Confluence Administration/ General Configuration, search for USERS & SECURITY
Jira: User management tab
Bitbucket: Administration/ Accounts
Bamboo: Administration/ Security
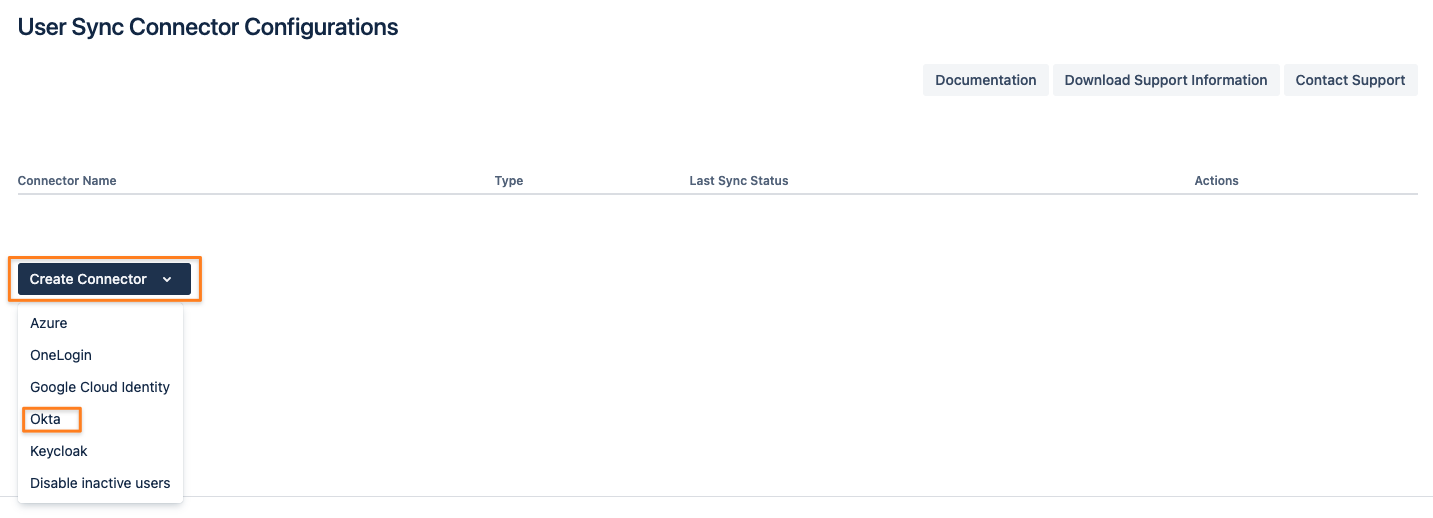
Now it is time to configure User Sync in your Atlassian product. Click on Create Connector and select Okta:
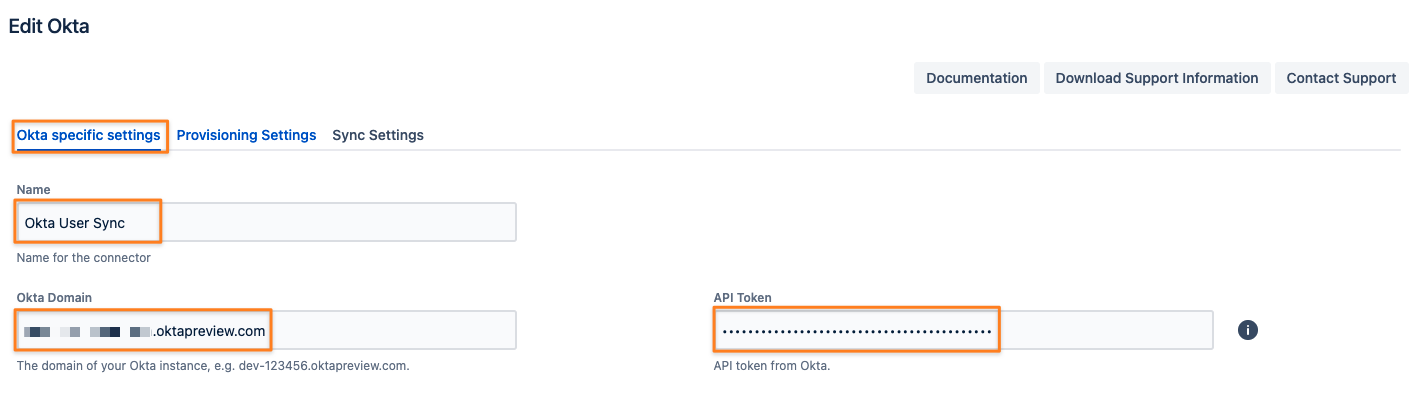
Set a Name, insert your Okta Domain without protocol (HTTPS://), and paste the token value to the API Token field
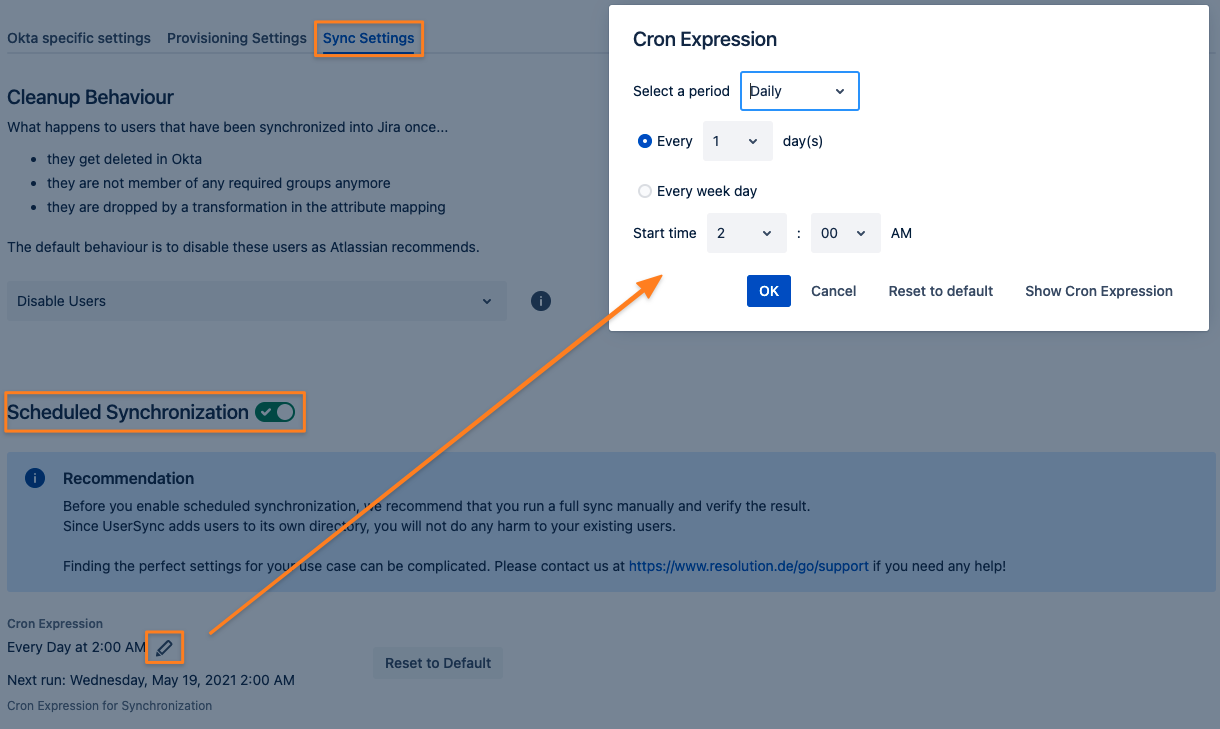
To take full advantage of User Sync, click on the Sync Settings tab and Enable Scheduled Synchronization.
You can control the sync interval with the modal but also by editing the Cron expression.
Do not forget to save your configuration. Scroll down to the bottom of the page and press Save or Save and Return.
Configure the SAML SSO App
To start the wizard and to configure Okta as your new identity provider, navigate to the administration console and search for SAML Single Sign On here:
Confluence: Confluence Administration/ General Configuration, search for USERS & SECURITY
Jira: User management tab
Bitbucket: Administration/ Accounts
Bamboo: Administration/ Security
Fisheye/ Crucible: Administration/ Security Settings
Click on it and the wizard start page will appear.
Add new Identity Provider (IdP)
Click on Add new IdP to start the wizard.
Adding a new IdP can also be done without the wizard in the app configuration section Identity Providers/ Add new IdP
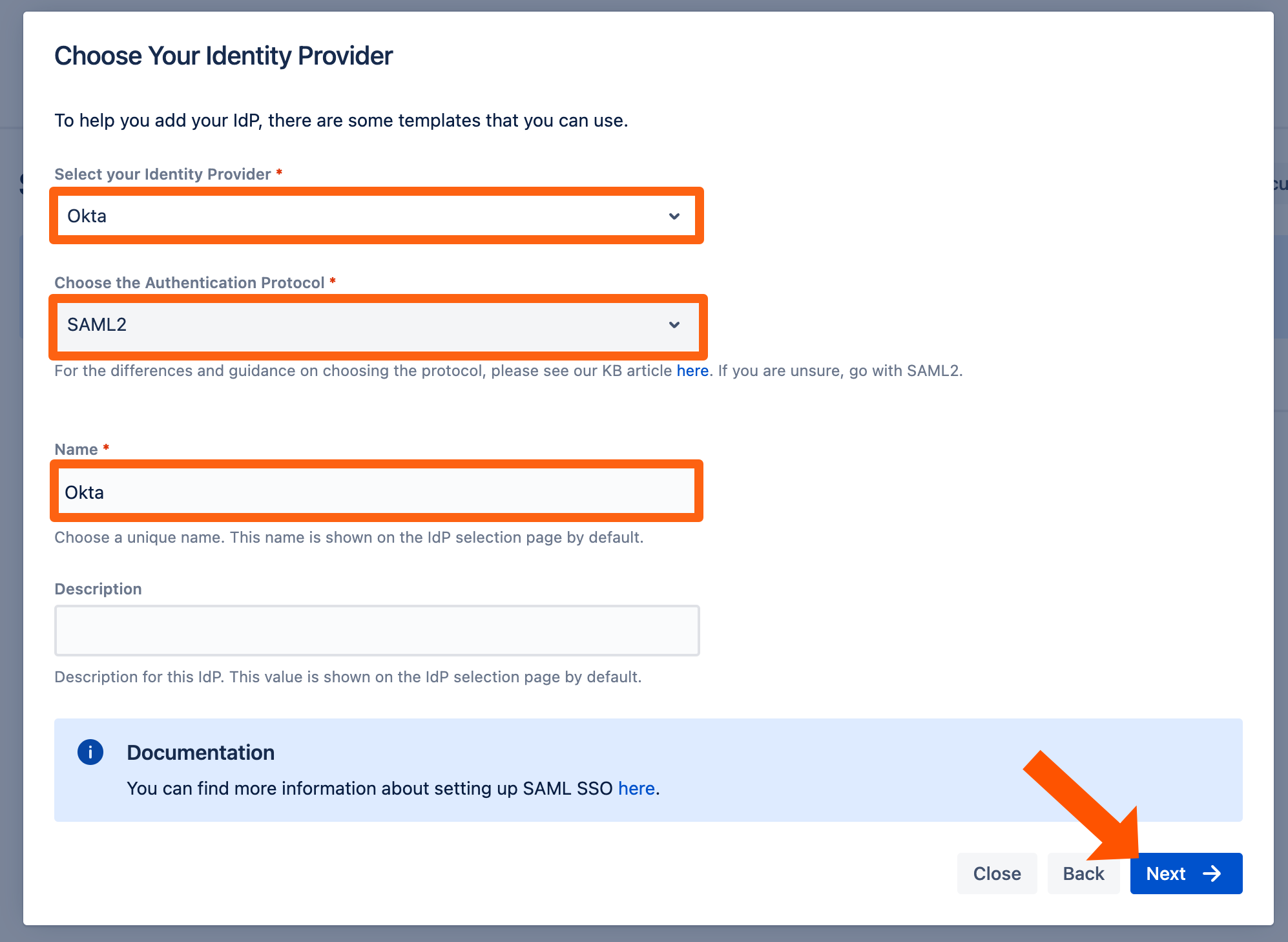
Select Okta as IdP Type.
You may also change the name and add a description. The name needs to be unique.
Keep the Authentication Protocol set to SAML2.
Click on Next.
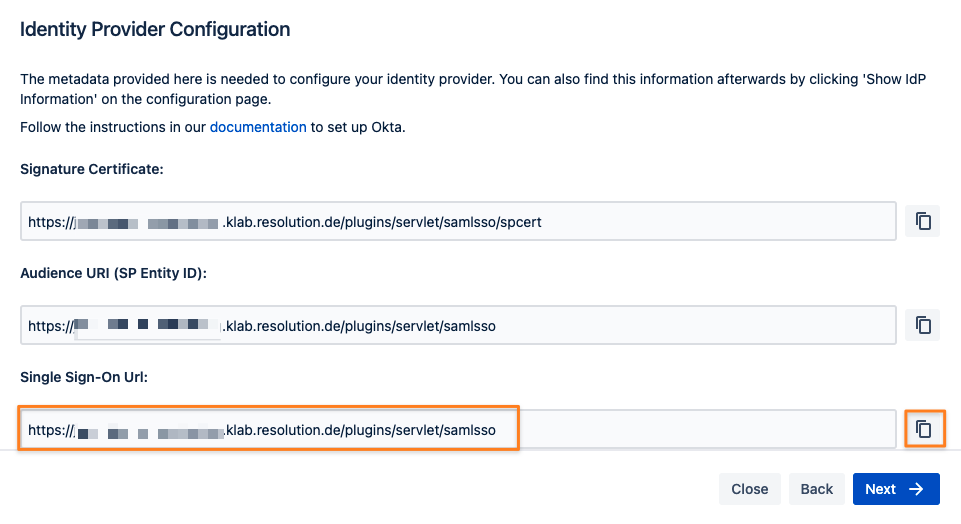
Retrieve SAML Metadata for Okta
Copy the Single sign-on URL from the screen, you'll need it in your Okta configuration web console.
Click on Next and leave that next screen as it is for now since we'll continue the setup in Okta.
Configure Okta
Now it's time to head over to Okta. Make sure you're logged in as Admin.
You need to switch to Developer Console/ Classic UI first, should you still see the black navigation bar:
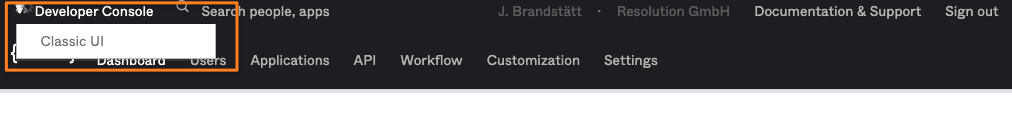
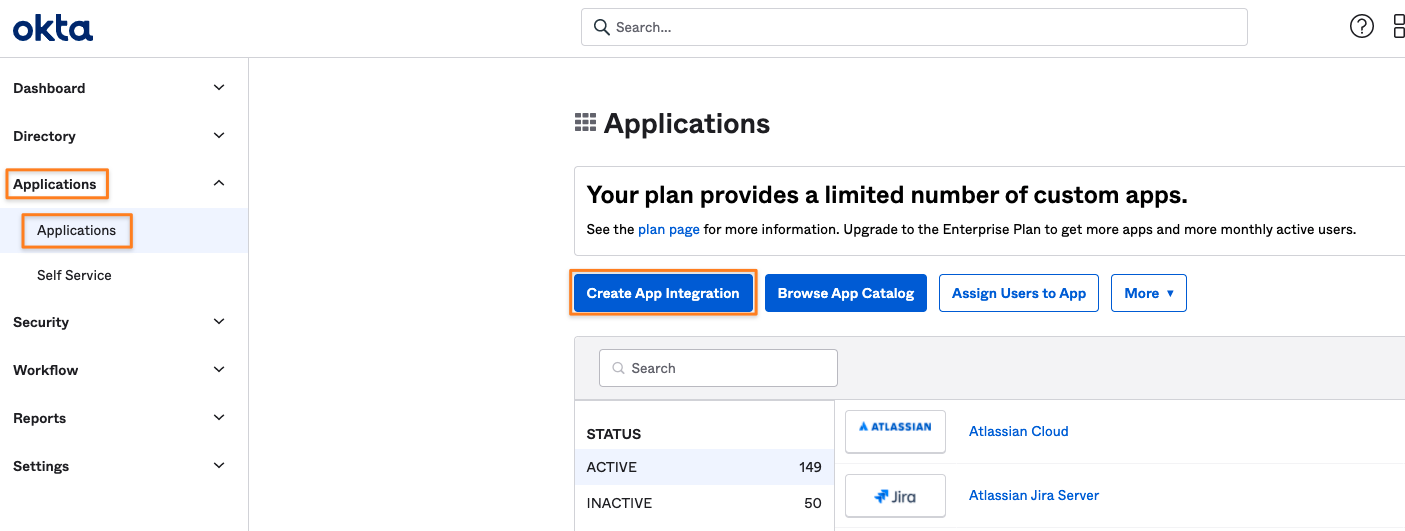
Once in classic mode, expand the Application menu on the left and click on Applications, and then the Create App Integration button:
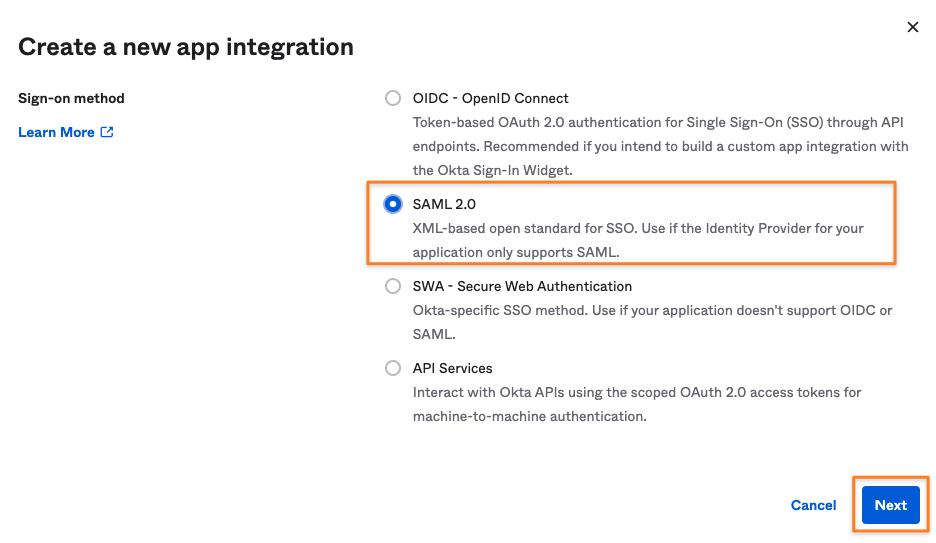
Select SAML 2.0 as the Sign-on method and click Next
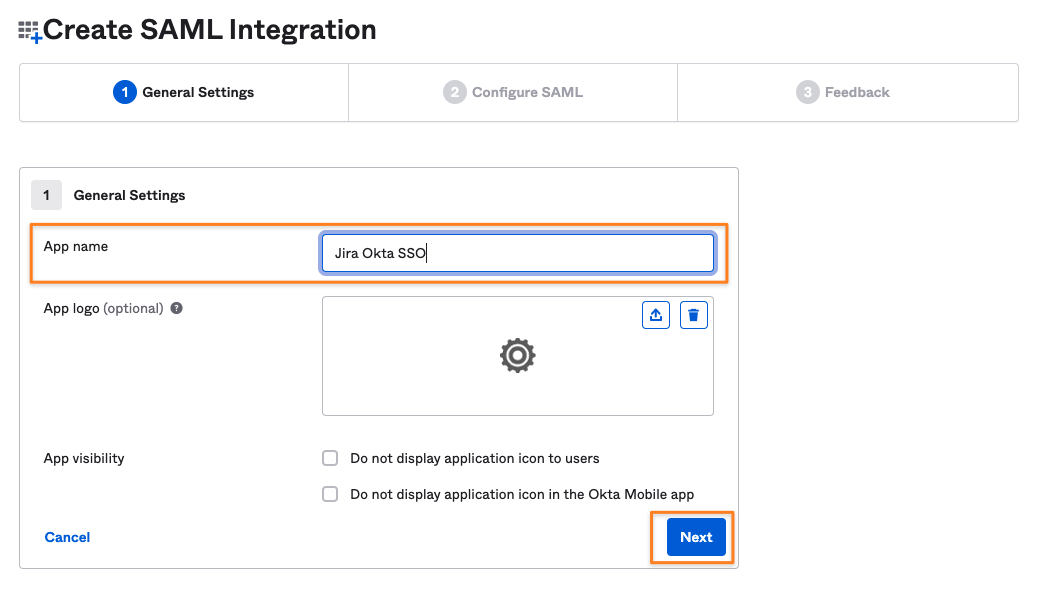
Provide an App name and click Next
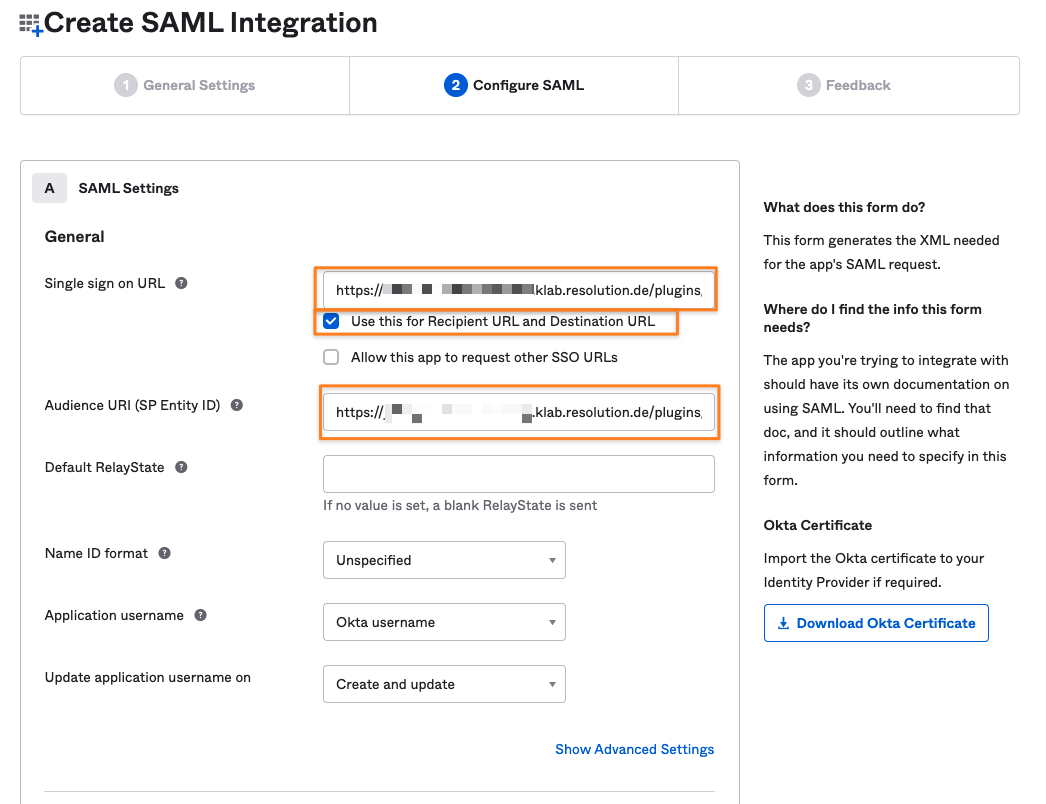
Paste the Single Sign-On URL to both the Single sign-on URL and the Audience URI (SP Entity ID) field.
Leave the Use this for Recipient URL and Destination URL checkbox enabled and click Next further down on the screen.
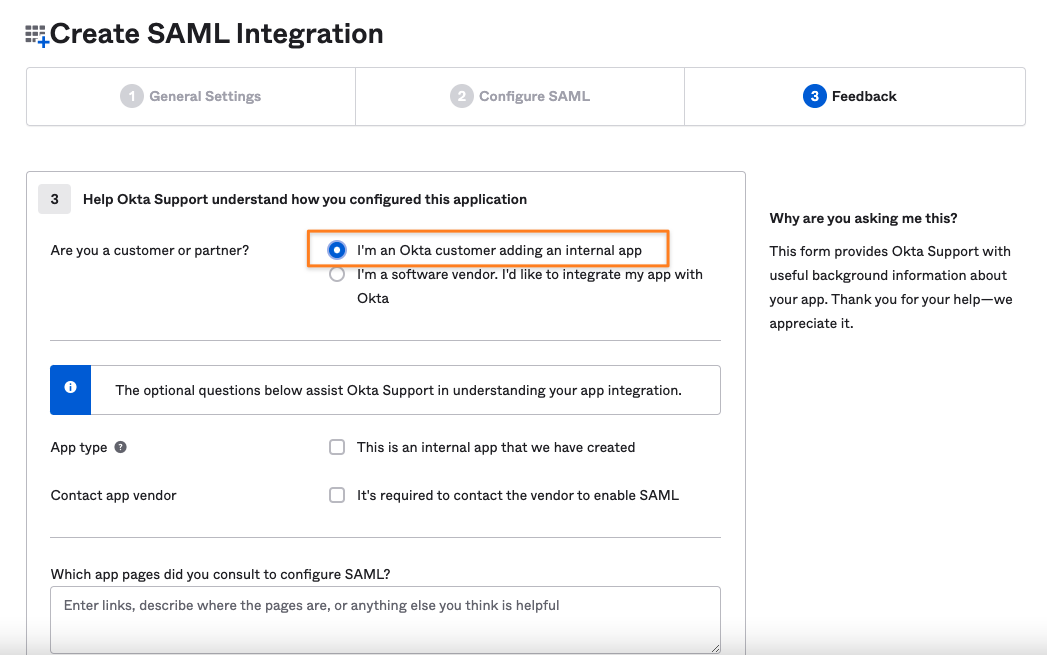
Step 3 is just for providing some feedback to Okta. Selecting I'm an Okta customer adding an internal app and clicking on Finish is all you need to do.
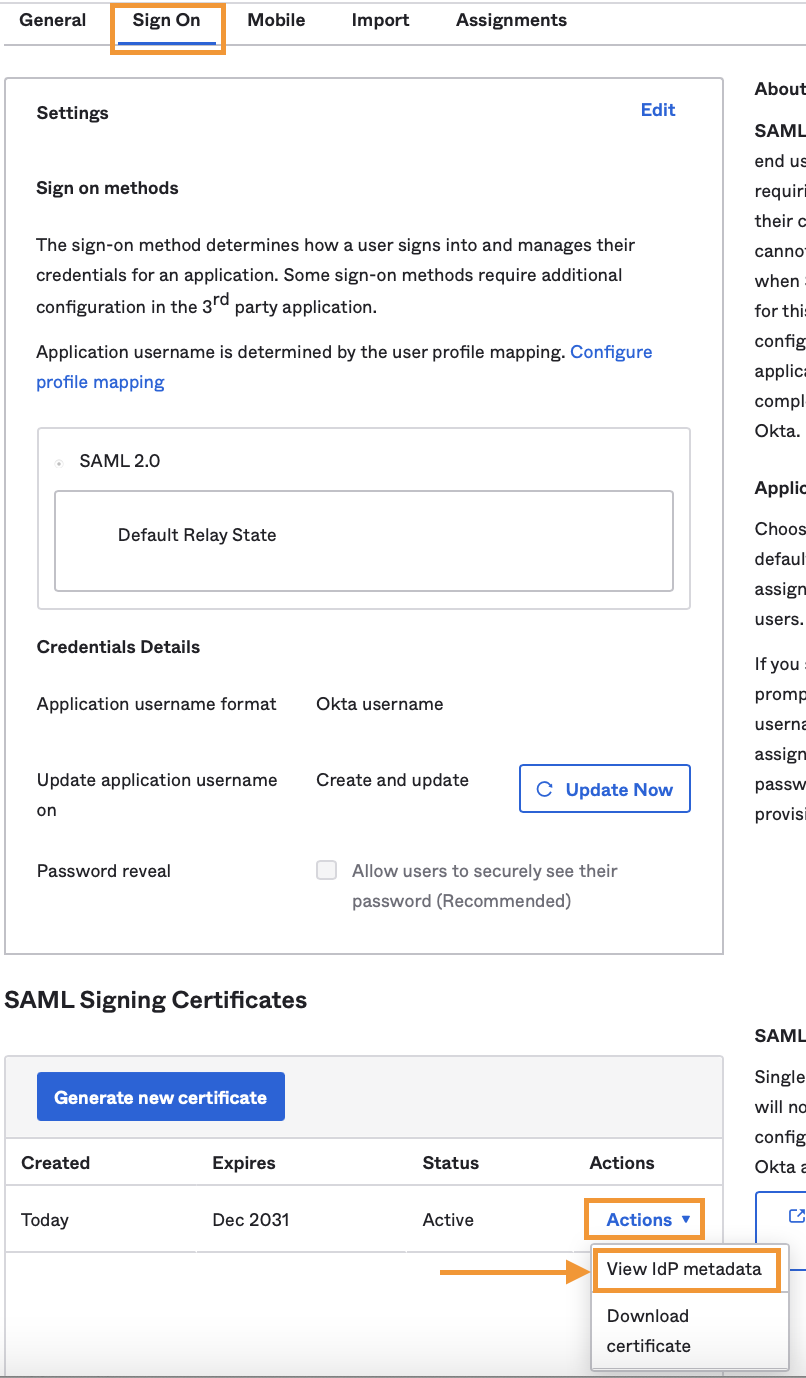
You'll be redirected to the Sign On tab from which you can get the Identity Provider metadata.
Under the SAML Signing Certificates section, click on Actions for the Active certificate, then choose View IdP metadata.
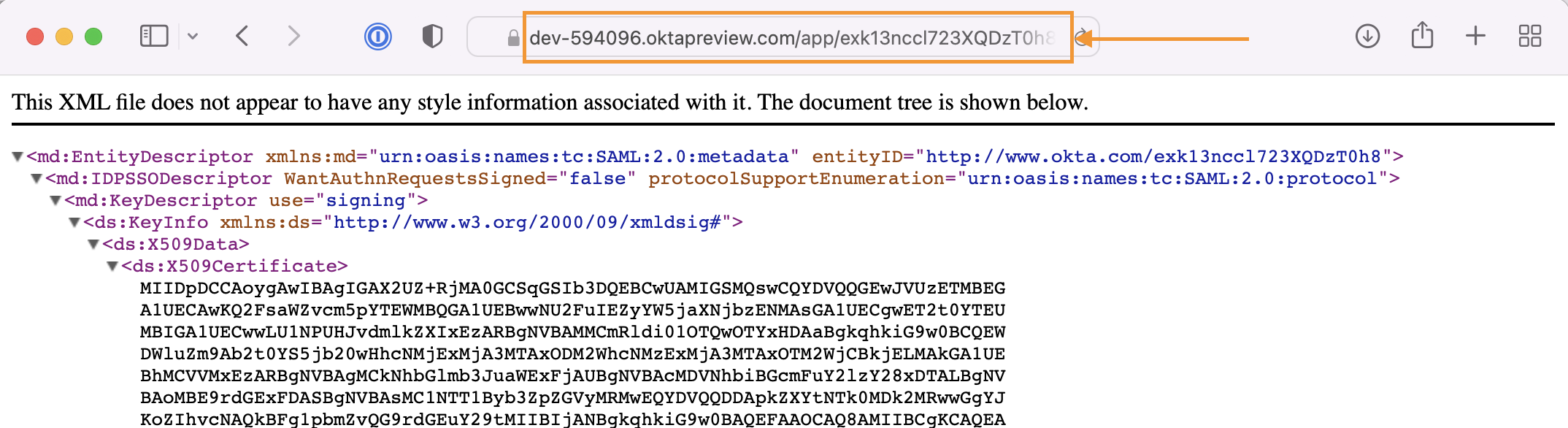
That would open a new page with the metadadata XML, where you need to copy its URL from the address bar.
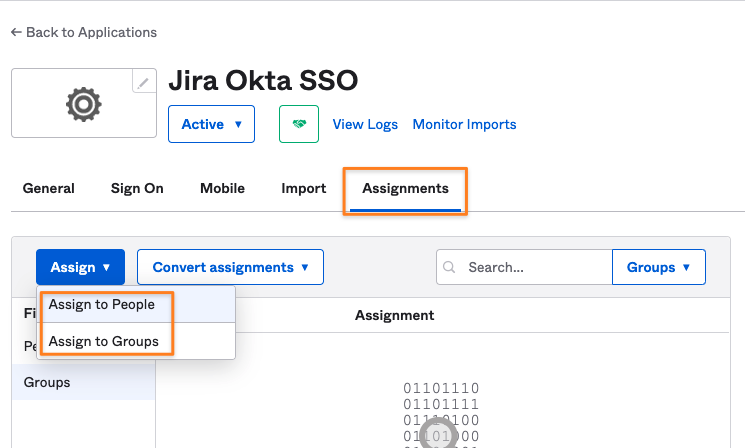
You also need to define which users and/ or groups should be allowed to sign in via SAML SSO in Okta via the app you've created.
Switch to the Assignment tab and use either the Assign to People or Assign to Groups button to define who should sign in with SSO.
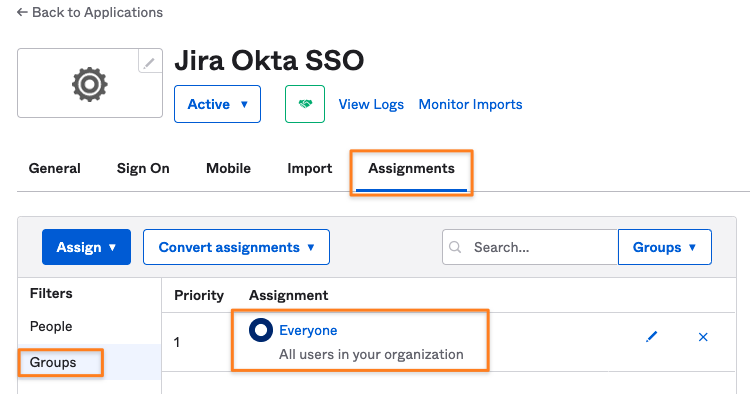
The simplest example, like below, would be to allow the group Everyone access to the app.
Import SAML IdP Metadata
It's time to resume configuration on the SAML SSO side. Take the Okta metadata link you've copied
and paste it to the Metadata URL field in the corresponding field of the Import SAML IdP Metadata wizard screen still open.
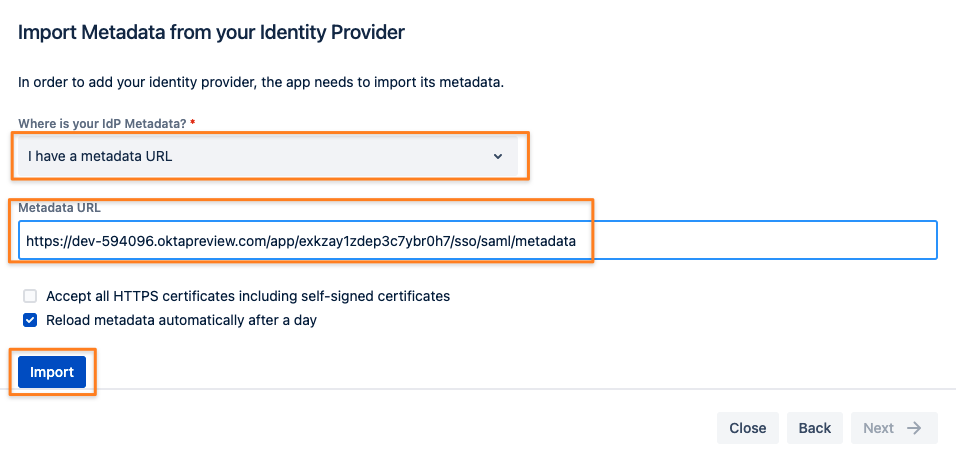
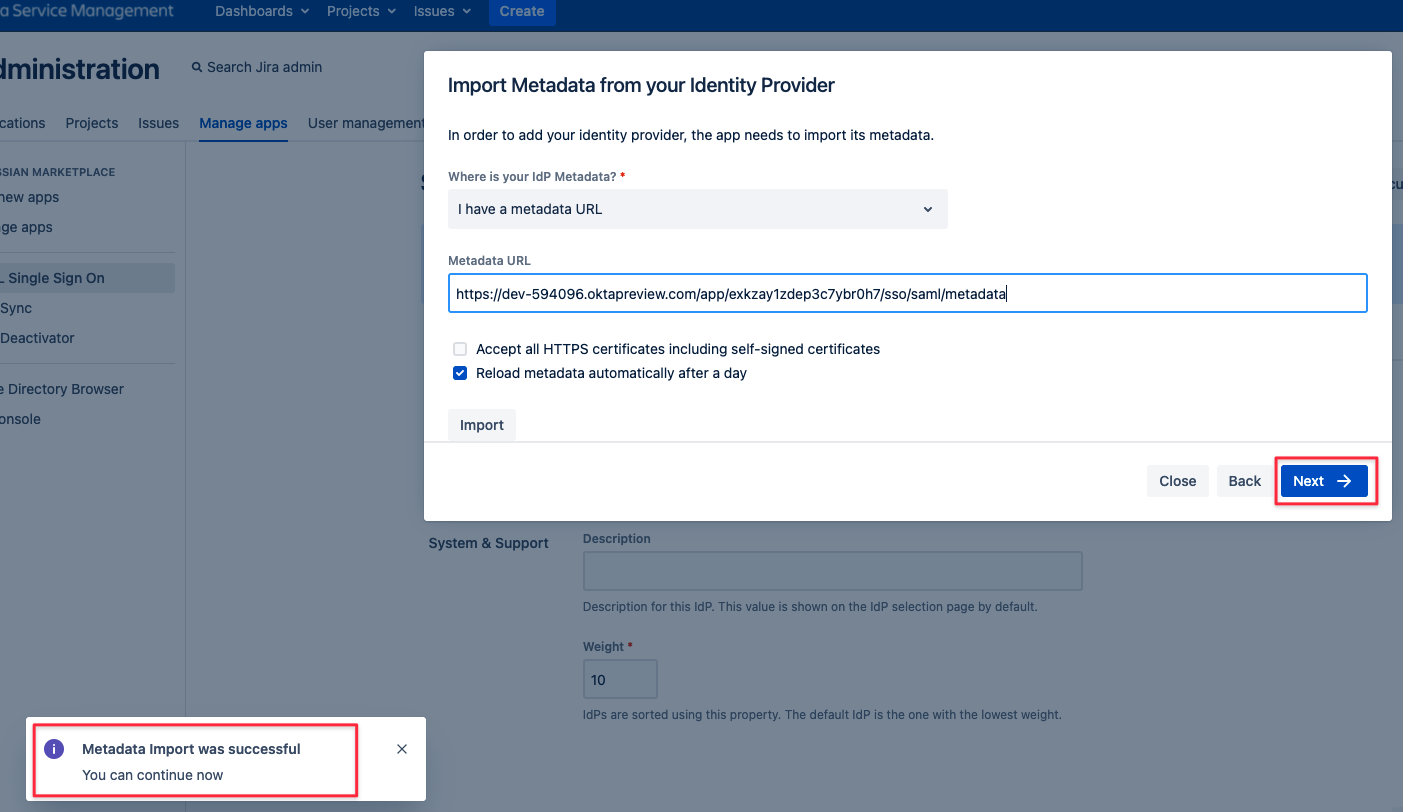
If loading the metadata from the URL worked, you can click Next
If it didn't work, your Atlassian instance can't talk directly to Okta (i.e. because traffic is blocked).
While you could also download the metadata first and import it manually by changing the Where is your IdP Metadata option,
we recommend making it work via URL. Our app supports automatic metadata refresh so that changes on the IdP will be reflected automatically after some time.
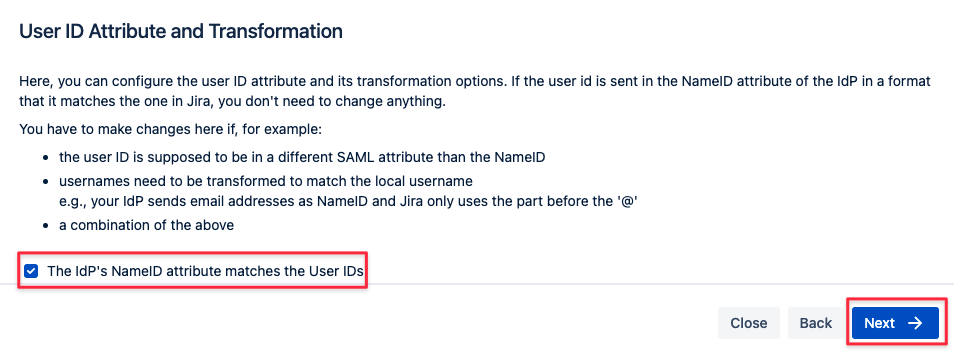
User ID attribute and transformation
It's recommended to leave this option checked. Click on Next.
As User Update Method choose Update with UserSync-Connector.
Select the User Sync connector name you've created before:
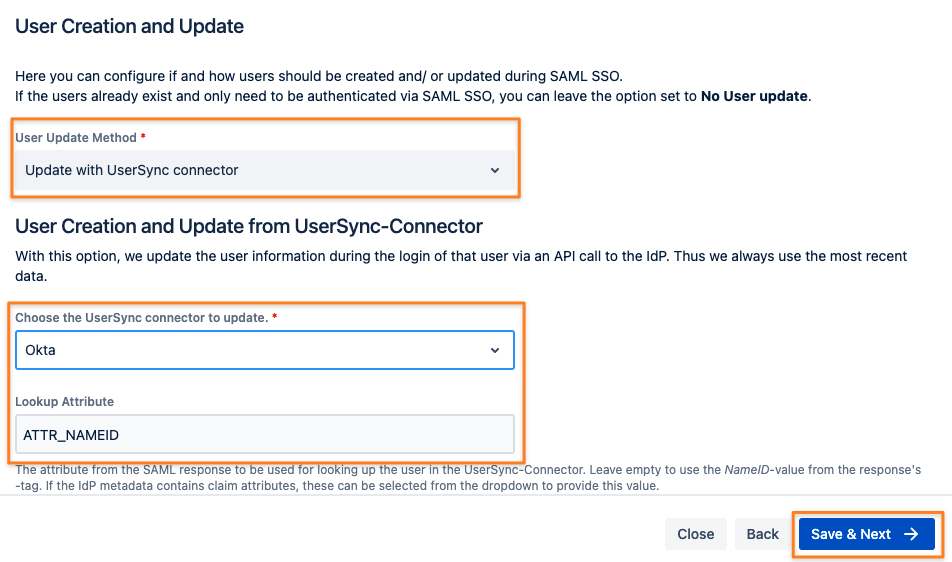
Click Save & Next to continue.
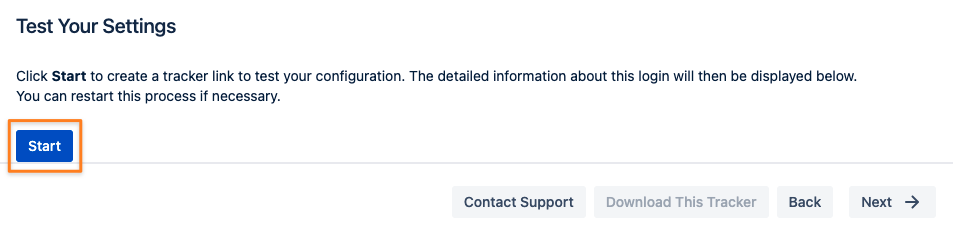
Test configuration of SAML SSO app
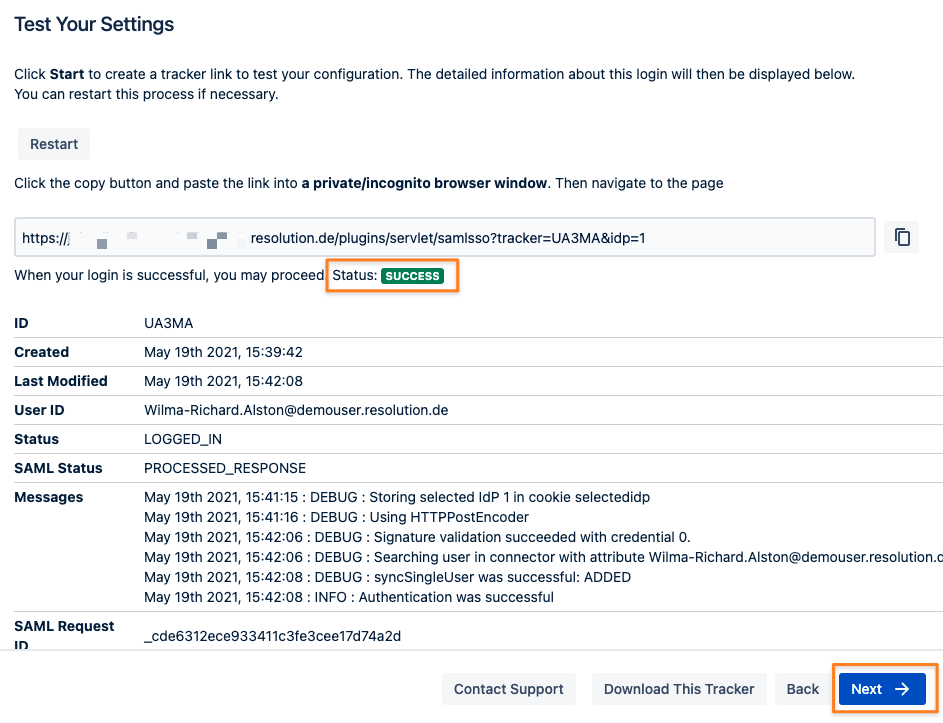
The last step of the configuration wizard is a test that can be executed with the Start button:
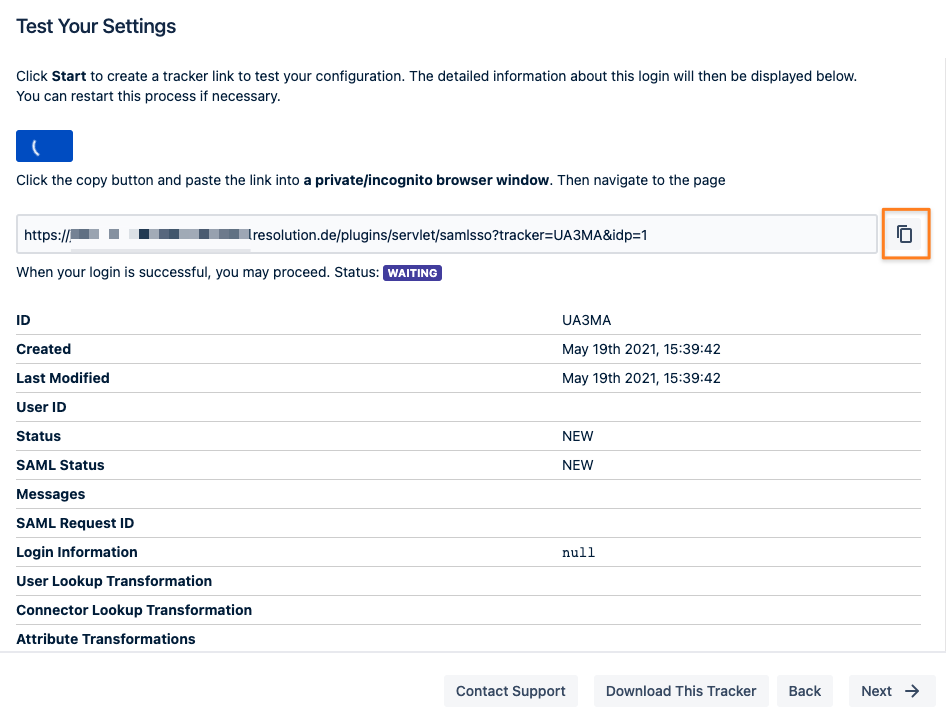
Copy the link displayed and paste it into a new incognito/ private browsing window, to execute a login with Okta.
Please remember that ...
the user you're logging in with needs to be assigned to the SSO app you've just created in Okta (we did that for Everyone in our example)
the groups providing application access to Jira, Confluence, etc. should be assigned to the user in Okta
if this is not possible, you can configure User Sync to automatically assign groups to all the users being synced
Edit the connector again and add the group at the top of the Provisioning settings tab and save the settings:
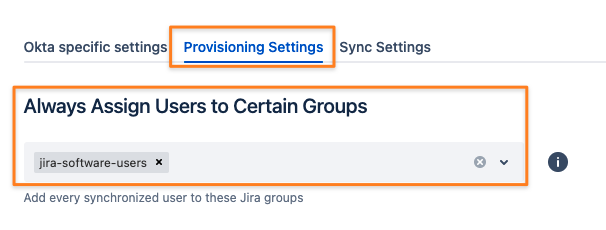
for more complex requirements we recommend looking at our User Sync group management tutorial
The status of the authentication process is permanently updated in the window.
If successful, you should click Next
Enable login redirection
The last step of adding Okta as your new IdP is to configure redirect options.
Selecting Enable SSO Redirect will ensure that users are getting redirected to be logged in via SAML, instead of via the login form as before the SSO setup.
The Custom Logged Out URL can be left empty.
It would redirect users after log out to a specific URL.
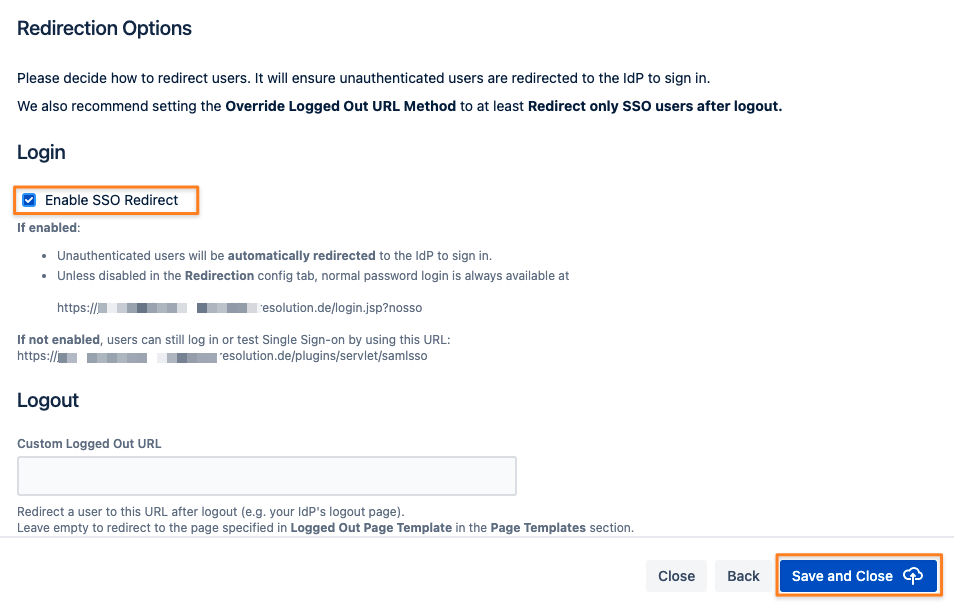
Complete the setup by clicking Save and Close
If Enable SSO Redirect is enabled, you can log in to your Atlassian application manually by browsing to the URL that matchs your Atlassian application as listed below.
Use this URL, if you need to log in as a local user unknown to Okta or if there are any issues with Single Sign On.
Jira: https://<baseurl>/login.jsp?nosso
Confluence: https://<baseurl>/login.action?nosso
Bitbucket: https://<baseurl>/login?nosso
Bamboo 5: https://<baseurl>/userlogin!default.action?nosso
Bamboo 6: https://<baseurl>/userlogin!doDefault.action?nosso
Read more about nosso here: https://wiki.resolution.de/doc/saml-sso/latest/jira/further-configuration/disable-password-login-with-nosso-parameter-v2-1-0
