Atlassian with Manual Provisioning
Goal
After completing this setup guide, you will have set up Atlassian with manual provisioning and your Atlassian product for the SAML SSO for Atlassian Server or Data Center app. Additionally, you will enable the SSO redirection and test SSO.
If you need help, please reach out to us at https://www.resolution.de/go/support. You can also book a free meeting via https://www.resolution.de/go/calendly.
Prerequisites
To use the SAML SSO app for Atlassian Server or Data Center with Azure AD, you need the following:
An Atlassian Developer Account
A (trial) subscription for the SAML SSO app
Admin access to your Atlassian product
Step-by-Step Setup Guide
Install the SAML SSO App
In your Atlassian product, open the in-product marketplace as described in the Atlassian documentation.
Search for "resolution saml" and click "Install" for SAML Single Sign On (SSO) by resolution Reichert Network Solutions GmbH.
After the installation is complete, click Manage Apps/Addons.
Configure SAML SSO
After you clicked "Configure", the Wizard will be triggered. If not, or if you want to add another Identity Prover (IdP) to your existing configuration, click on "+ Add IdP". This guide assumes, that there is no IdP configured.
The Wizard greets you with information, click on "Add new IdP" to proceed.
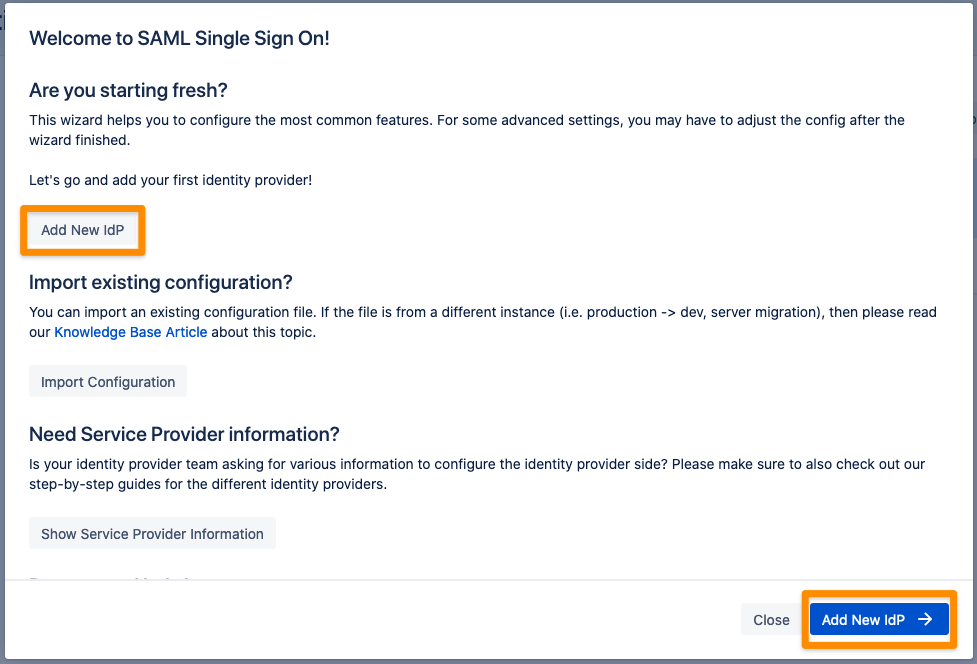
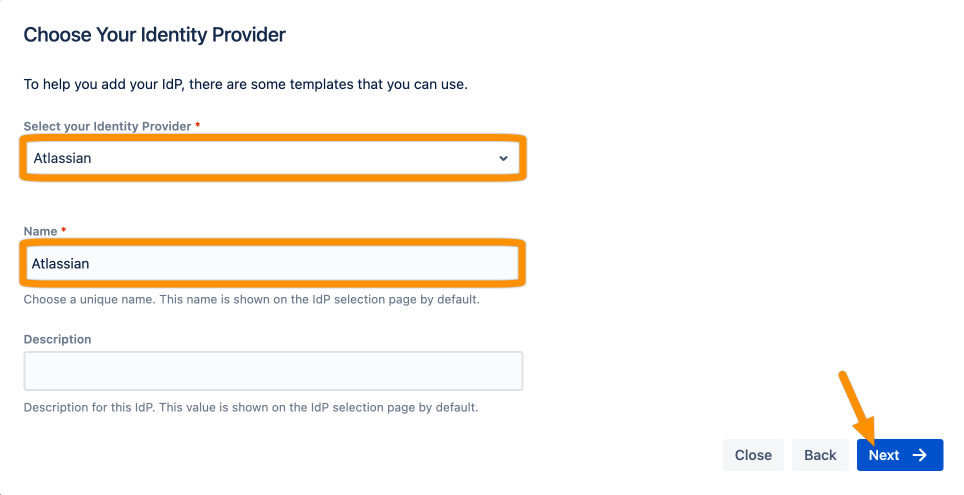
Choose Atlassian for the identity provider and click Next.
Copy the Callback URL and keep it ready for the next step. Click Next.
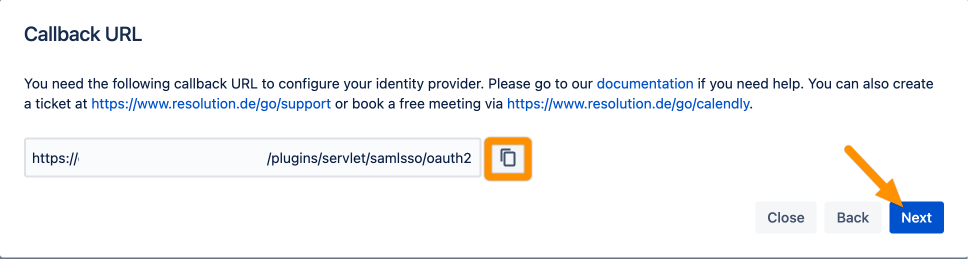
Go to https://developer.atlassian.com/console/myapps/ and log in with your Atlassian Developer Account.
Click Create and choose OAuth 2.0 integration from the list.
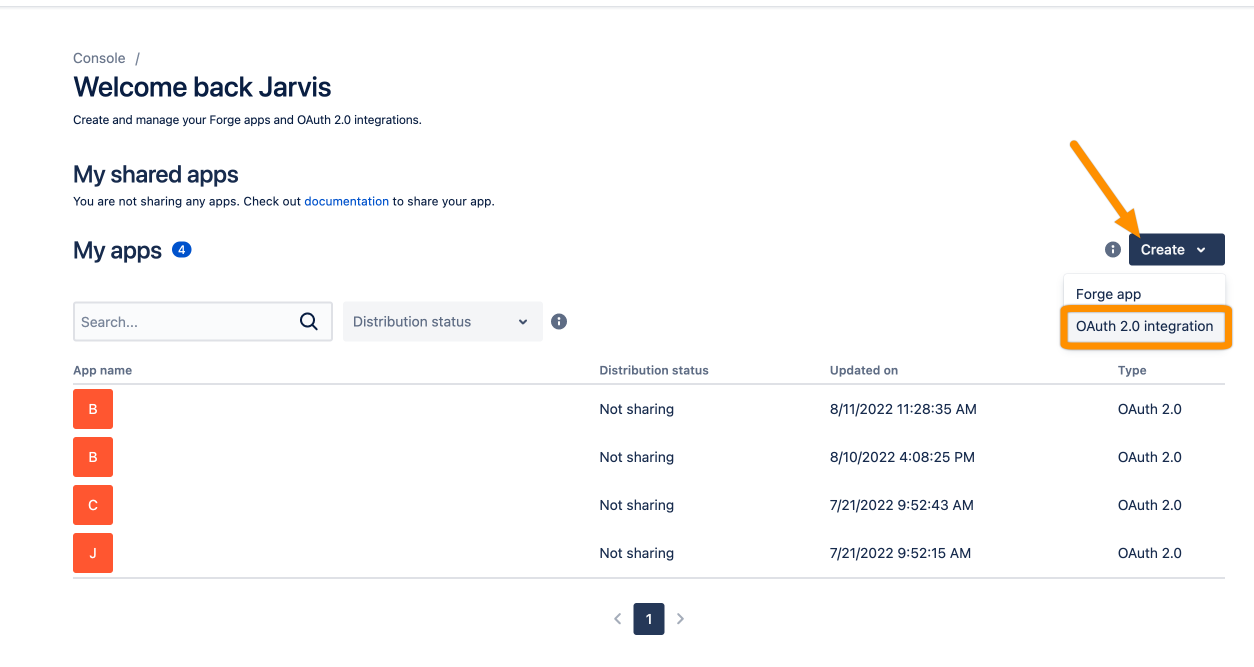
Provide a name for your app and agree to the terms. Click Create to continue.
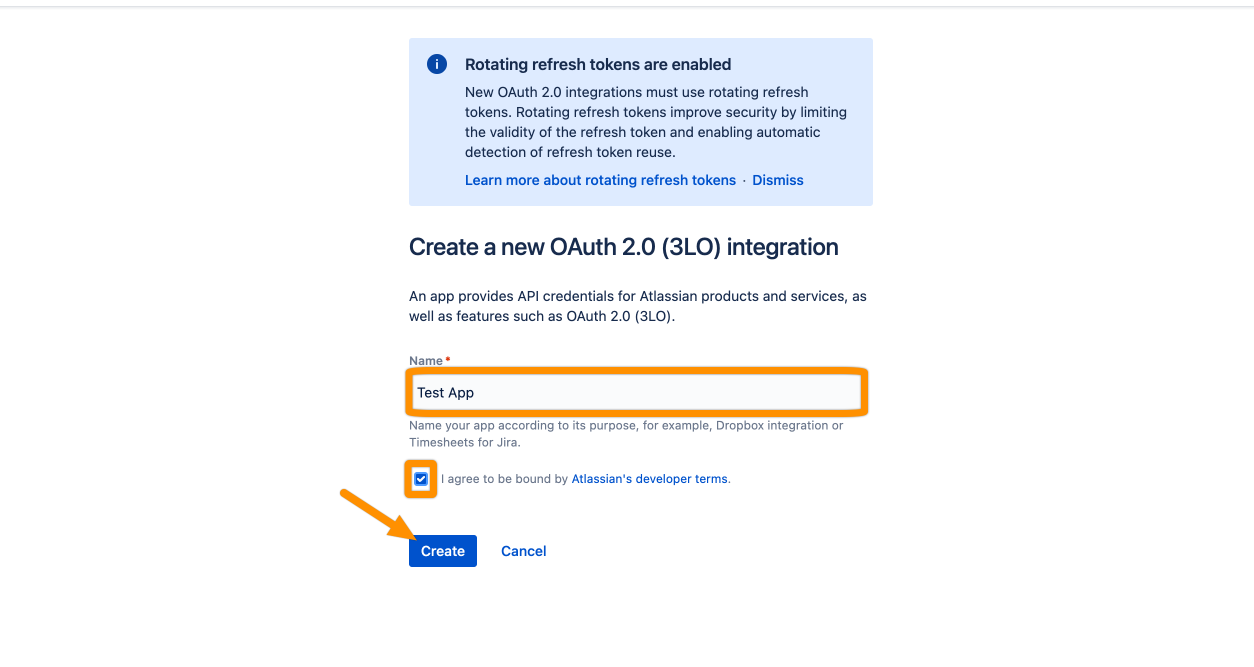
From the left sidebar, choose Permissions. Next, click Add for User identity API. This allows our app to get information like the email address of the user that tries to log in.
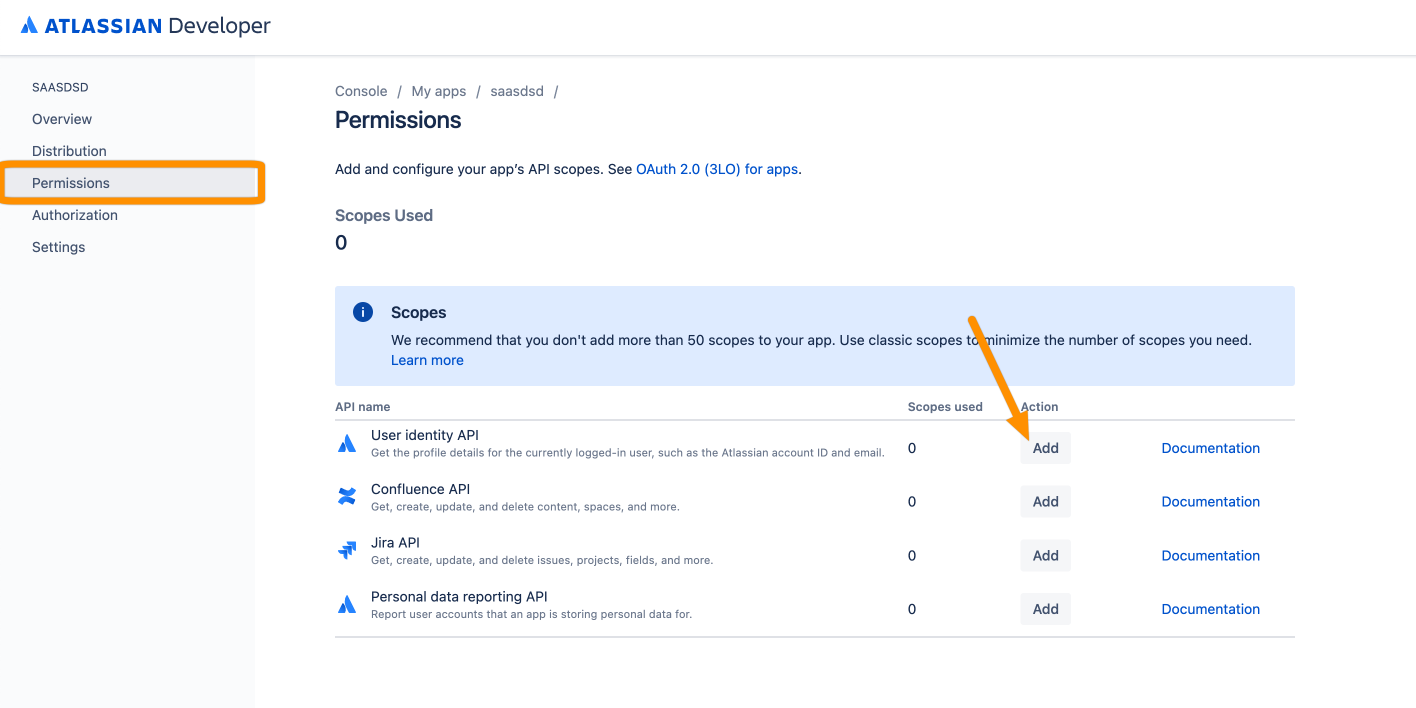
Now, go to Authorization from the left panel and click Add for the OAuth 2.0 (3LO) entry.
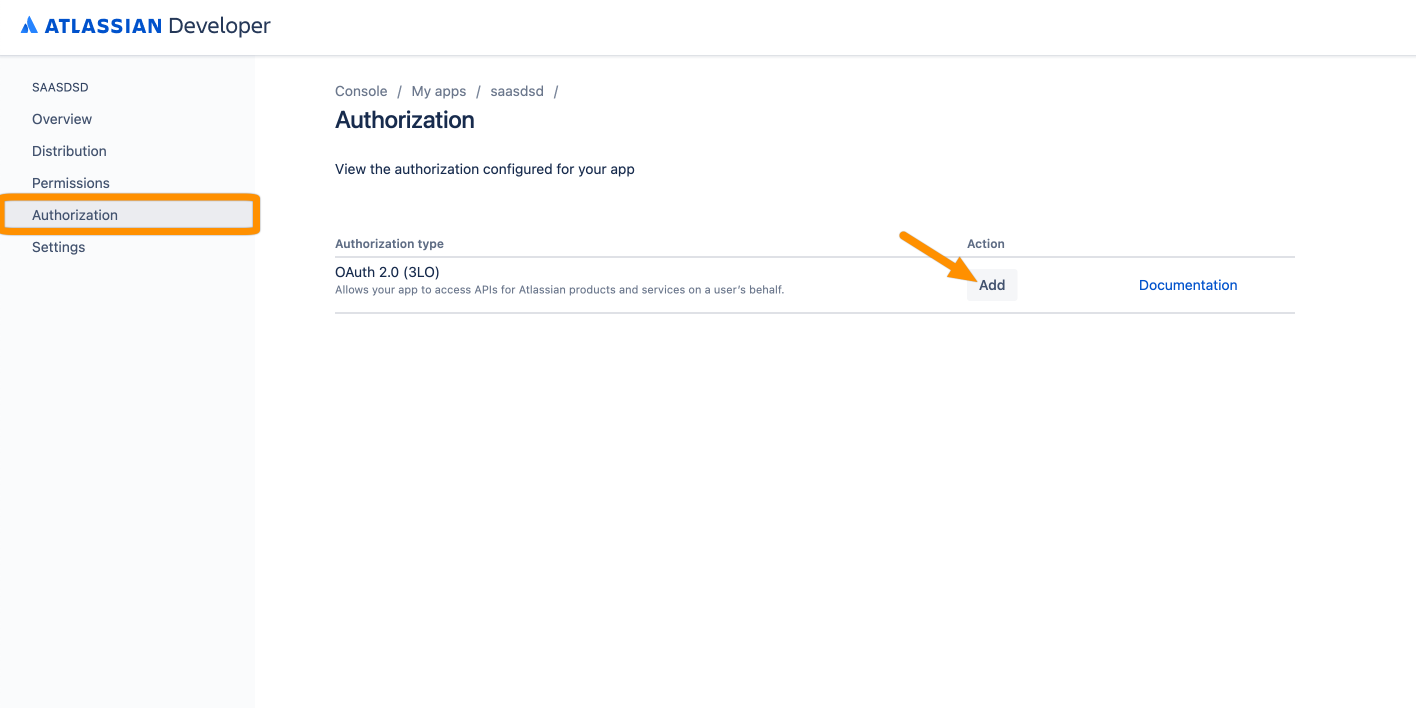
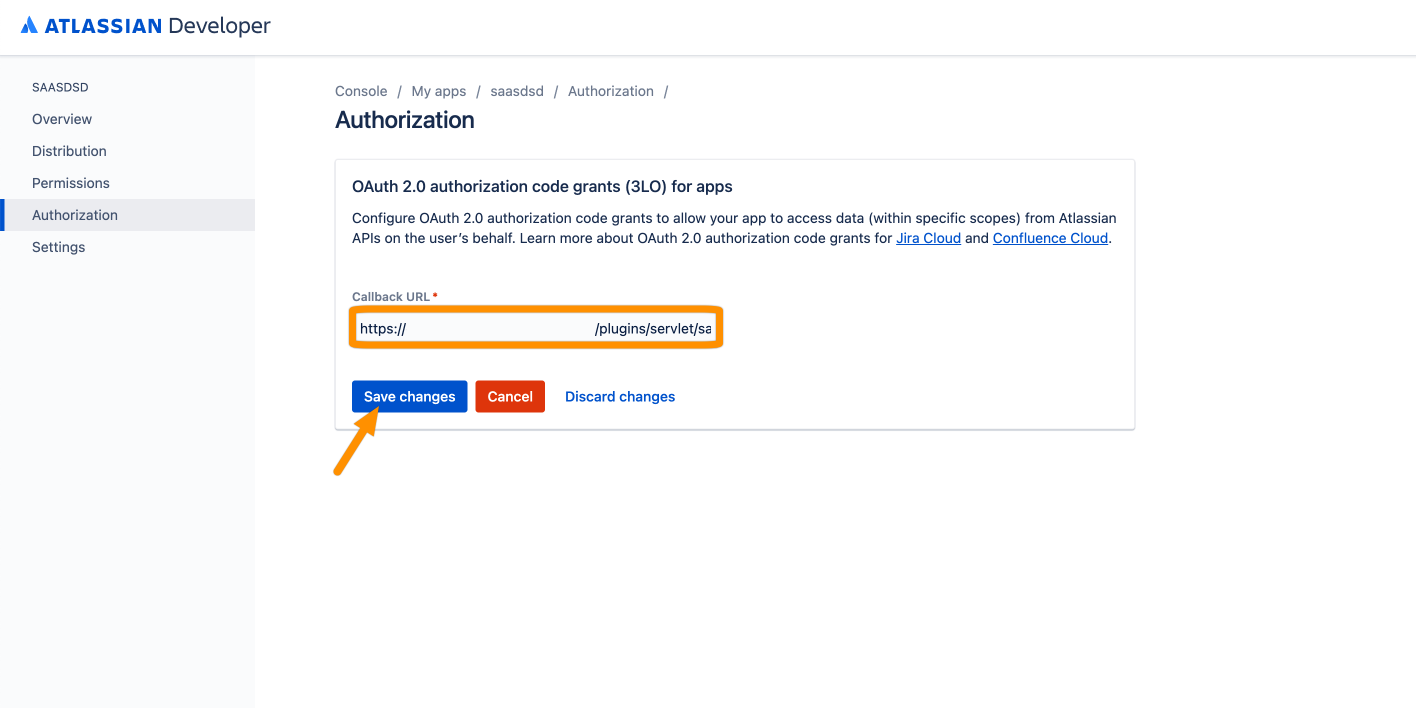
Now, enter the obtained Callback URL from the SAML SSO wizard. Click Save changes.
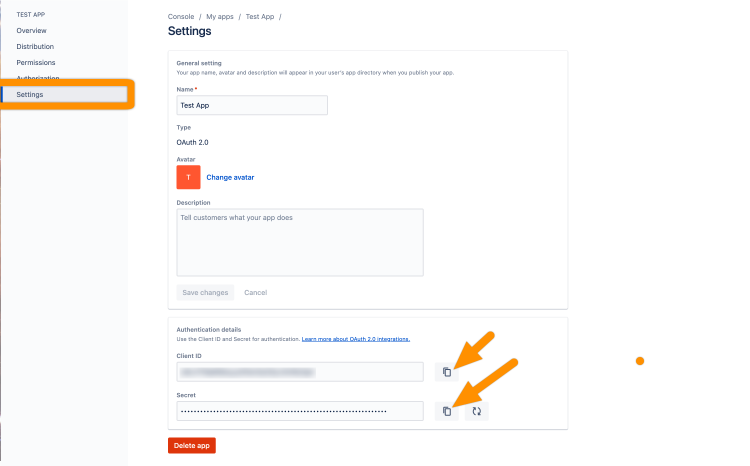
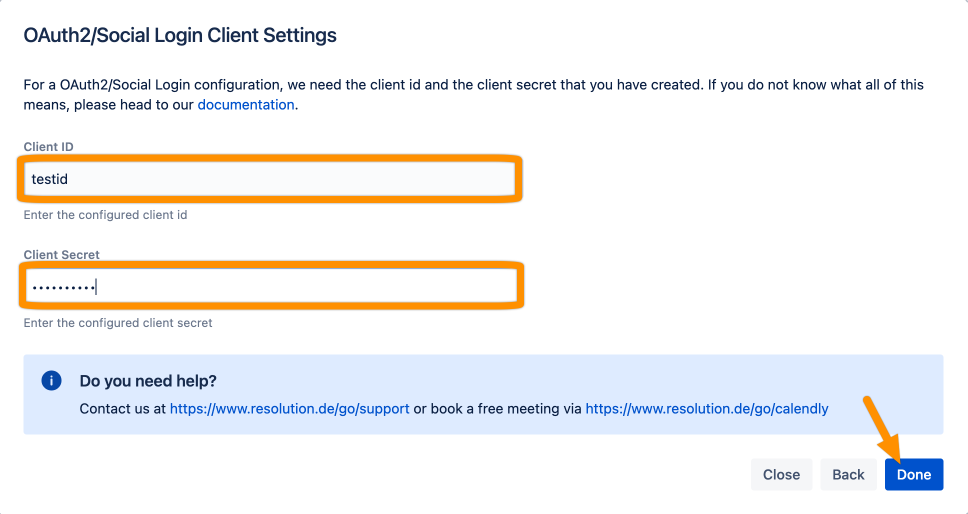
For the final step, go to Settings and copy the Client ID and Secret to your favorite text editor for later.
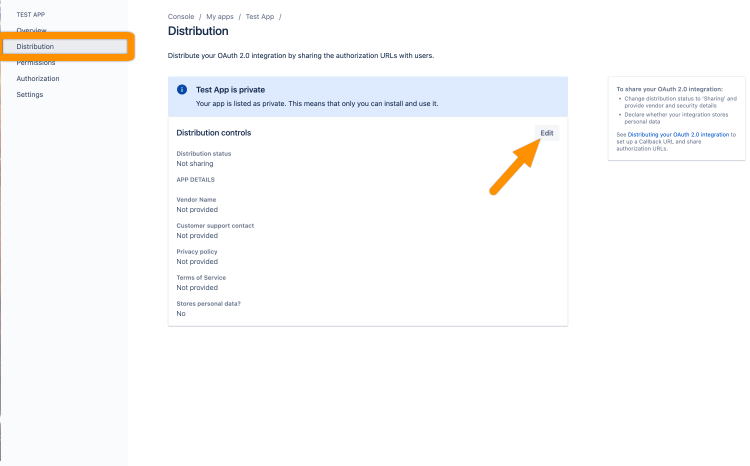
Right now, this app will only work for the user of the developer account. To make it accessible for all users, go to Distribution and click Edit. This means, that you will publish a public OAuth2 app, that anyone with an Atlassian account can use.
Thus, Atlassian will ask you for your vendor name and a privacy policy, see next step.
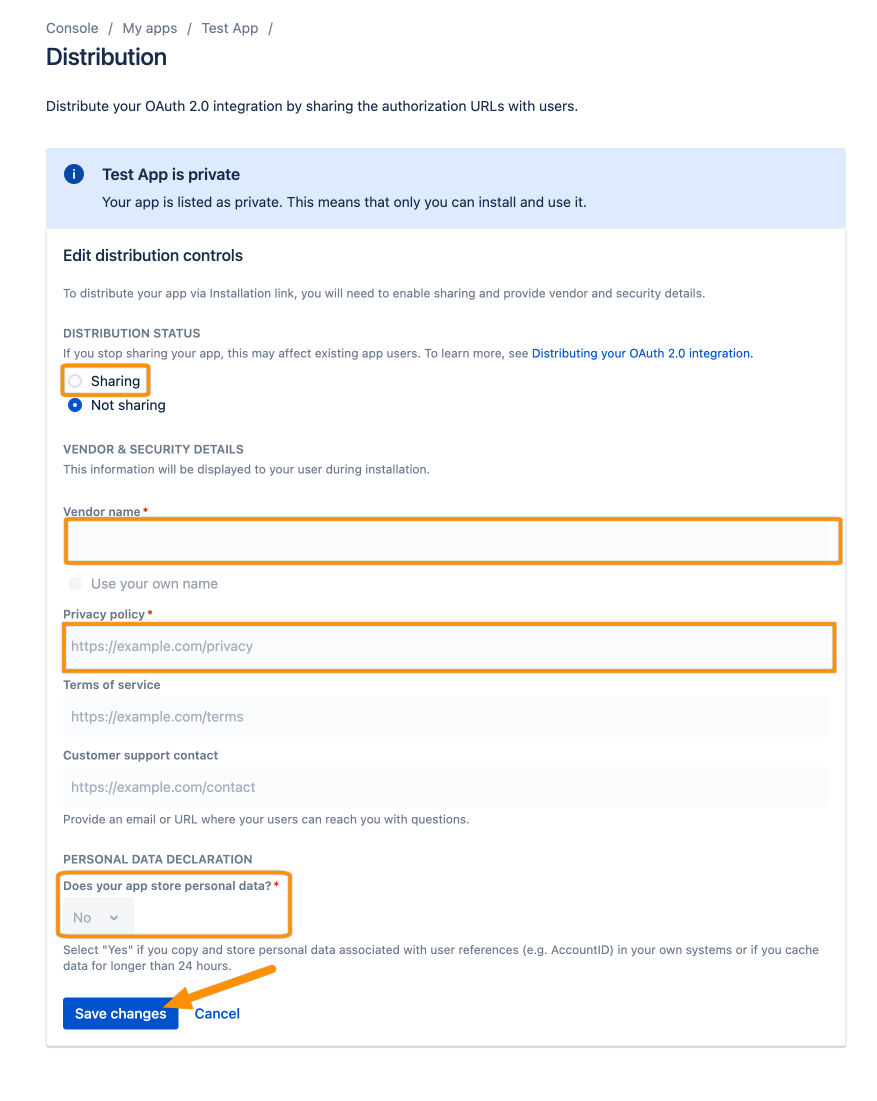
Change the Distribution Status to Sharing, add a Vendor name (or use your own name), and add your Privacy Policy. Regarding Does your app store personal data?, this depends on whether you do Just-In-Time provisioning or not, thus choose accordingly.
Click Save changes to make your app public.
Add the Client ID and Client Secret. Click Done.
Click Save to save the configuration.
That's it!
