Google Cloud Identity configuration
For the following setup, it's recommended to perform it in a browser where you're just logged into the Google account you are using for configuring GSuite.
Other Google sessions might make it hard for you to walk through the setup successfully, especially when authorizing the Gsuite app from inside the connector configuration.
This page contains information on how to set up User & Group Sync and G Suite. Note, that it is recommended to follow the video or the detailed User guide. If you are familiar with setting up G Suite projects, feel free to follow the Quick start guide.
Quick start guide
Log in to the Google API Console. Click on the currently active project.
Click on "NEW PROJECT".
Enter a "Project Name" and click on "CREATE". For this tutorial, it is called "Test Project". This can take a second.
In the next window, click on your newly created project.
After opening your project, click on "Library".
In the search bar, type "Admin SDK" and click on the "Admin SDK".
On the next page click on "ENABLE".
Now, click on "Credentials" in the left panel.
Click on the "Configure consent screen" button.
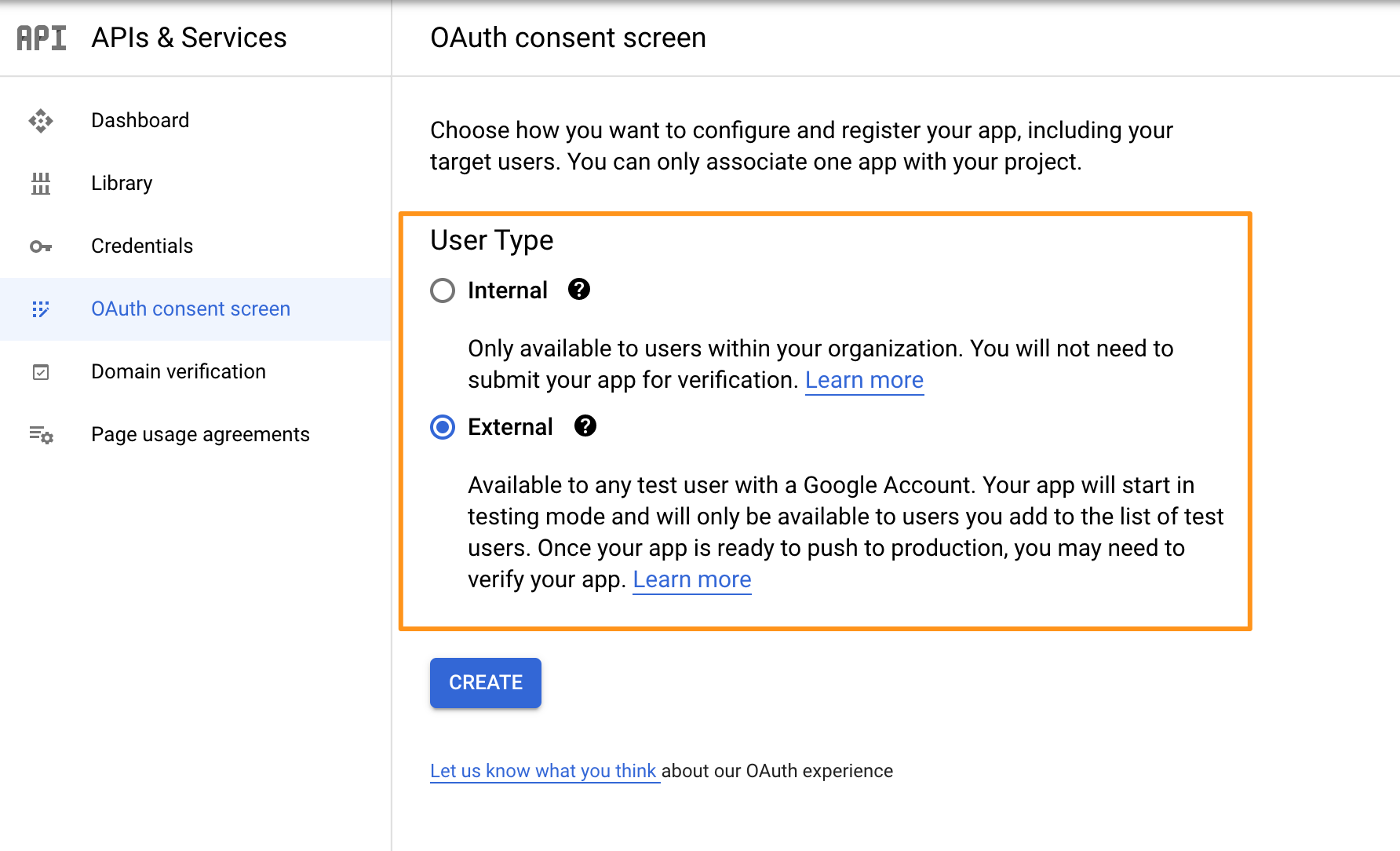
Choose a "User Type" (see https://developers.google.com/identity/protocols/googlescopes?hl=en_US) and click on "CREATE".
On the next screen, enter "App name" and "User support email".
Scroll down to "Authorized domains" and enter your domain, e.g. "mycompany.com". Press the ENTER key to add the domain.
Enter an email address in the "Developer contact information" section.
Click on "SAVE AND CONTINUE".
Go back to the Credentials tab on the left menu. On the next page, click on Create Credentials and click on OAuth client ID.
In the next window, choose "Web application".
Enter an "Authorized redirect URIs" https://<your-atlassian-product-base-url>/plugins/servlet/de.resolution.usersync/oauth2/authorize then click "CREATE".
In the next window, you can see your "client ID" and your "client secret". You will need both for setting up User & Group Sync, thus save them somewhere where you can find them for the next step.
Now User & Group Sync will be set up in your Atlassian application. Press "Create Connector" and choose "Google Cloud Identity".
Enter your "Client ID" and "Client Secret" that you have copied earlier (step 18). Click on "Start Authorization".
If you are a Google Cloud Identity Administrator, click on "Go to Google". Otherwise, copy the generated message and provide it to your administrator, and you can continue the configuration meanwhile by closing that window.
The plugin will show you if the authorization was successful.
Your configuration is now done, click on "Save and Return".
You are now ready for your first sync. Click on "Sync" in the Connector overview.
User guide
Log in to the Google API Console. Click on the currently active project.
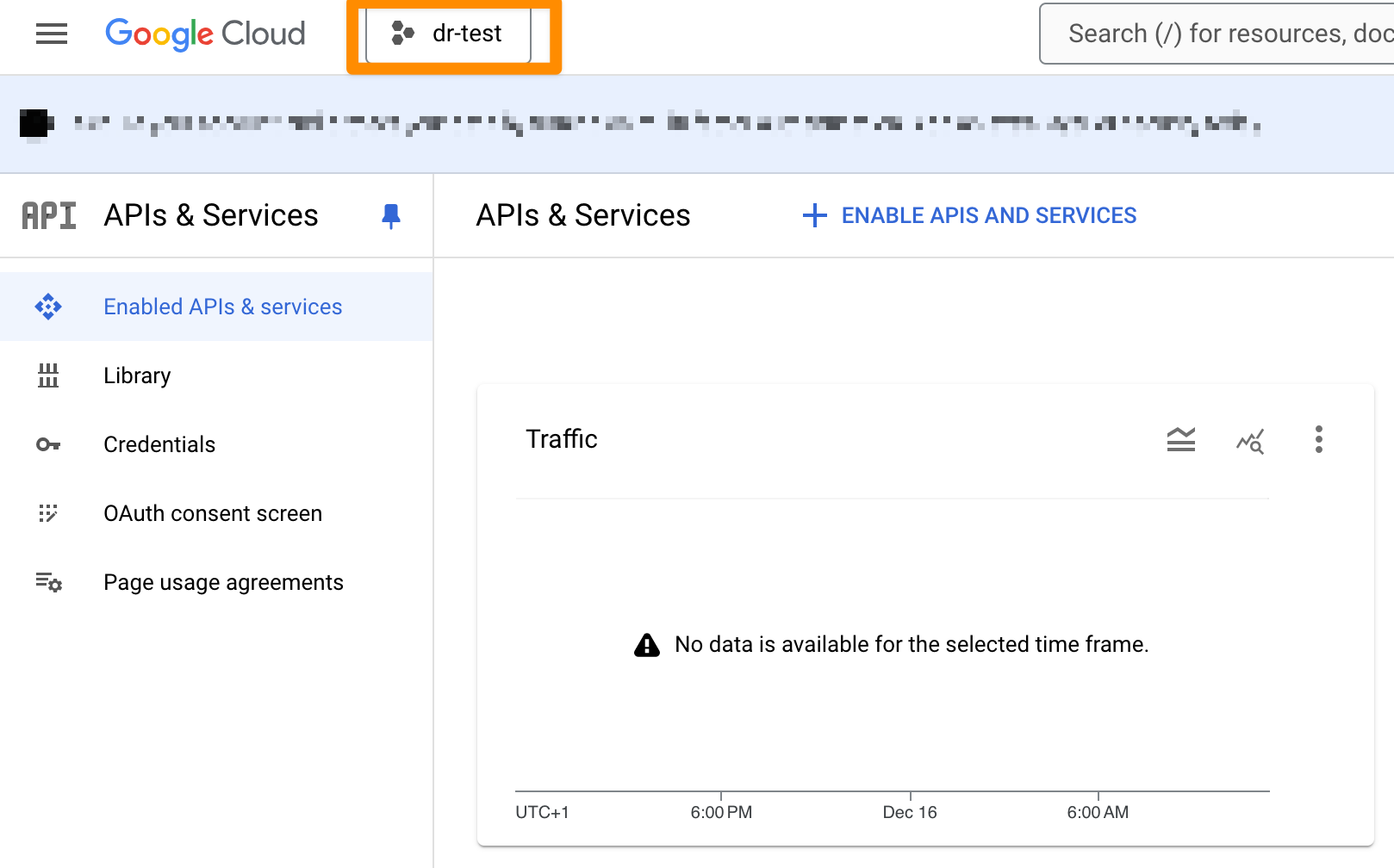
Click on "NEW PROJECT".
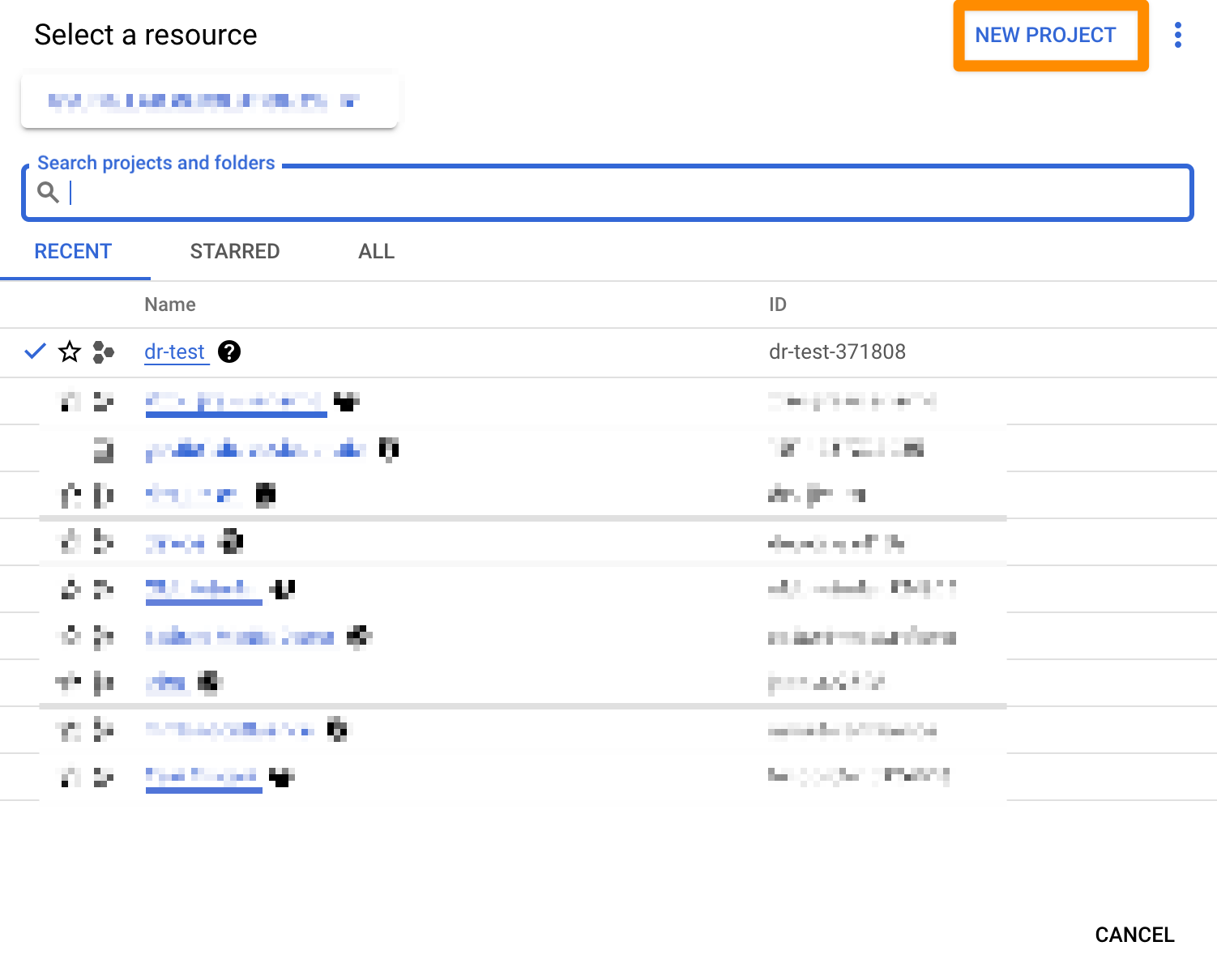
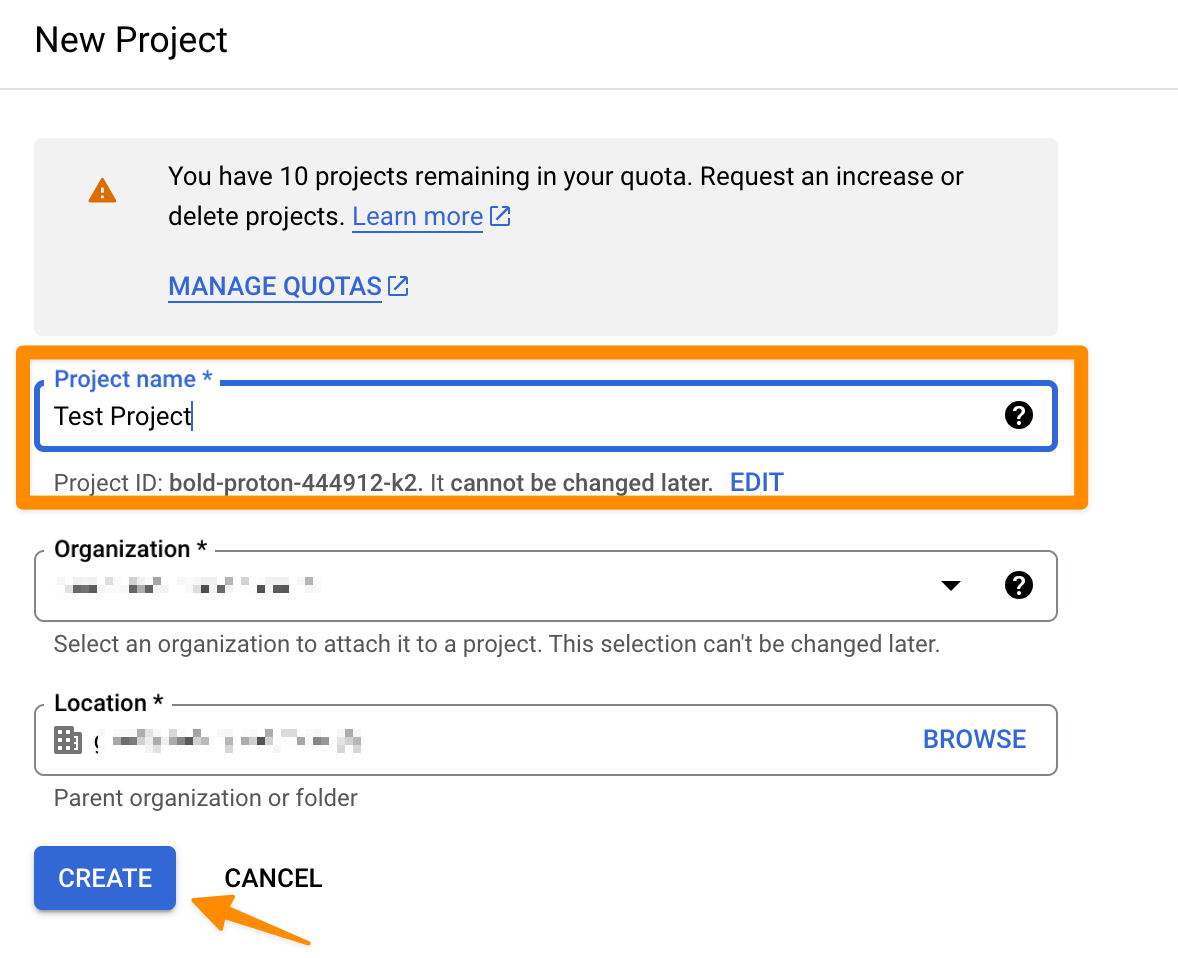
Enter a "Project Name" and click on "CREATE". For this tutorial, it is called "Test Project". This can take a second.
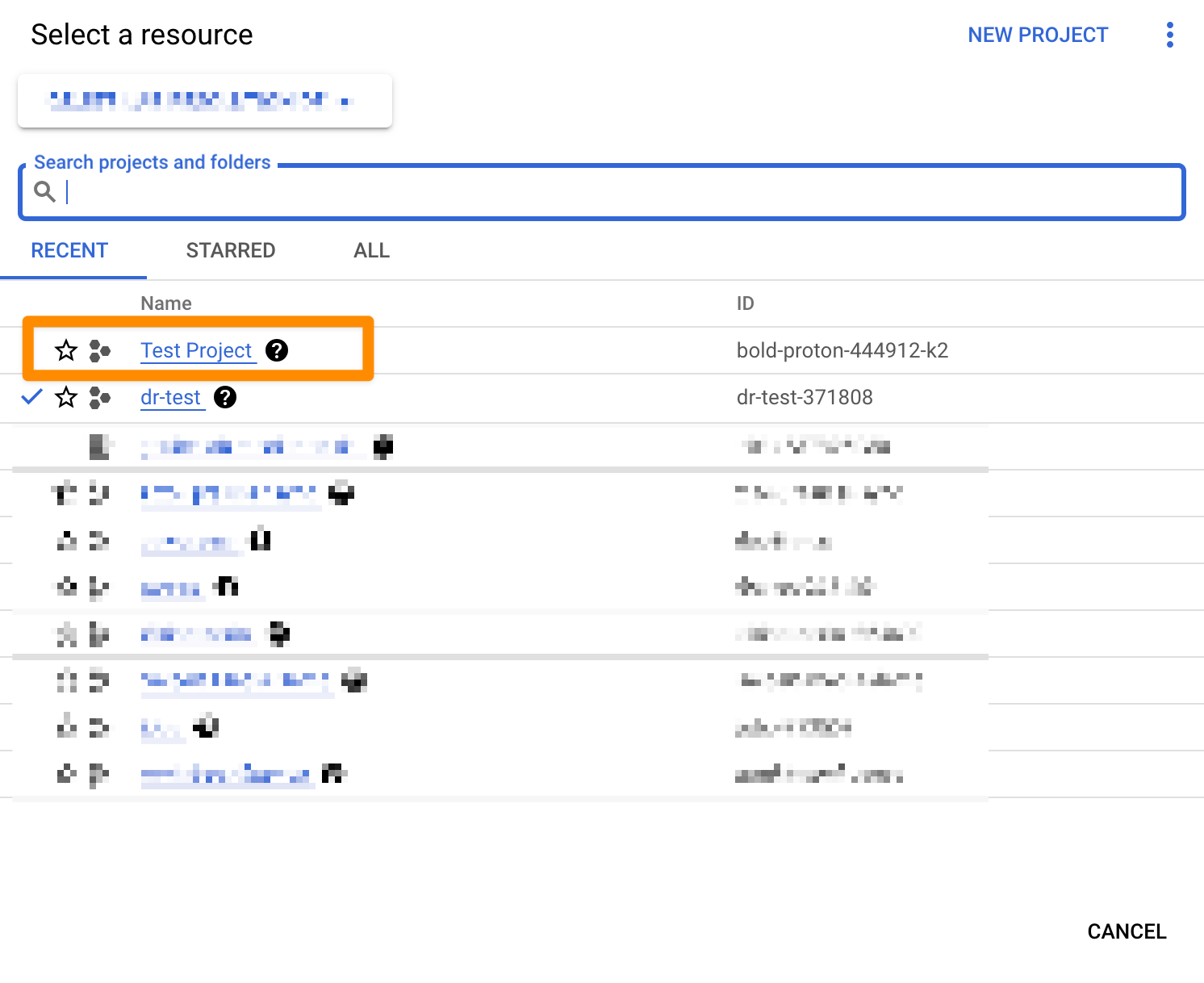
Open your project list again and click on your newly created project.
After opening your project, click on "Library".
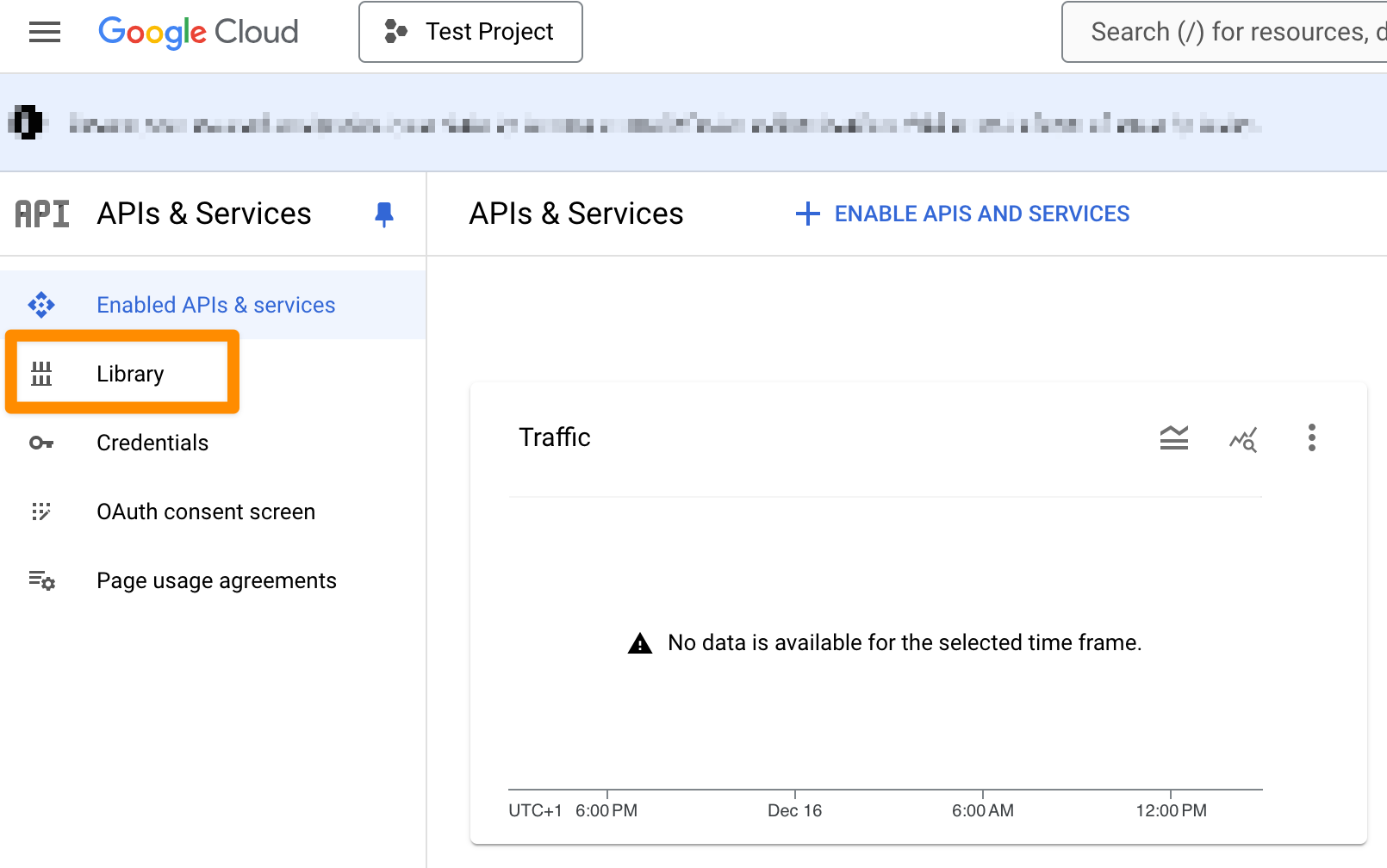
In the search bar, type "Admin SDK" and click on the "Admin SDK".
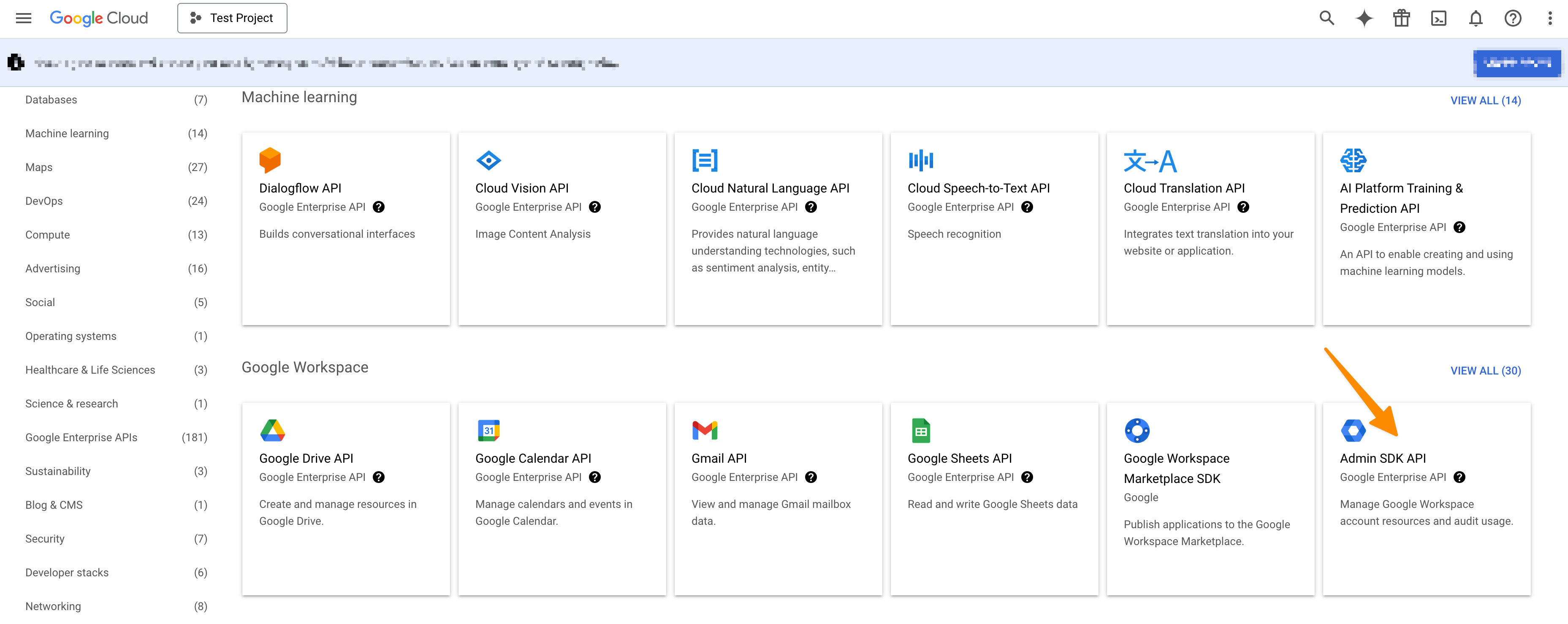
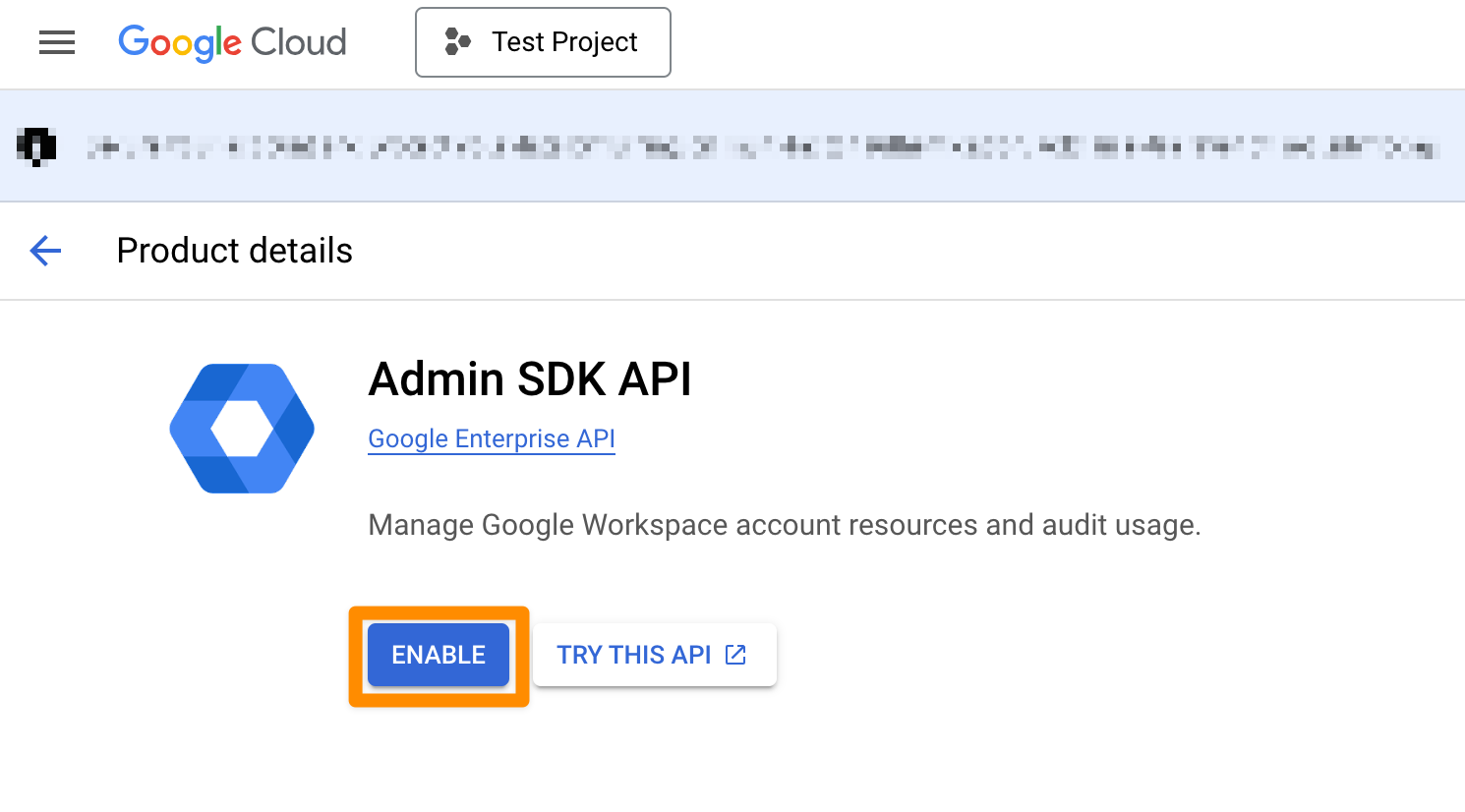
On the next page click on "ENABLE".
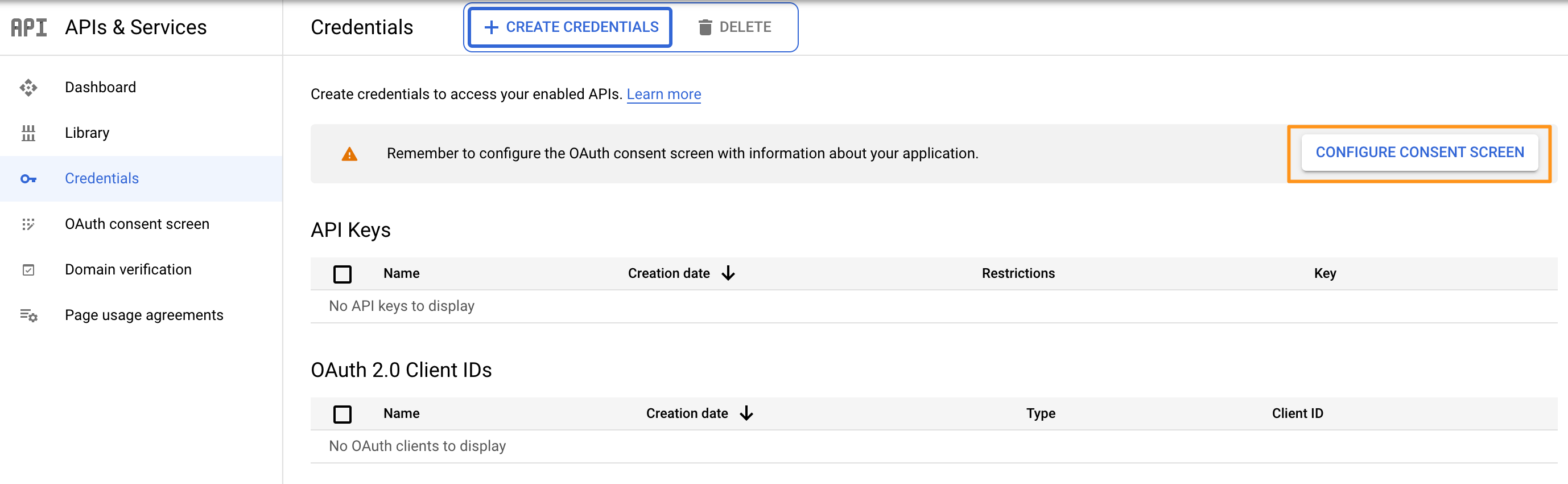
Now, click on "Credentials" in the left panel, and click on "Configure consent screen"
Choose a "User Type" (see https://developers.google.com/identity/protocols/googlescopes?hl=en_US) and click on "CREATE".
On the next screen, enter "App name" and "User support email".
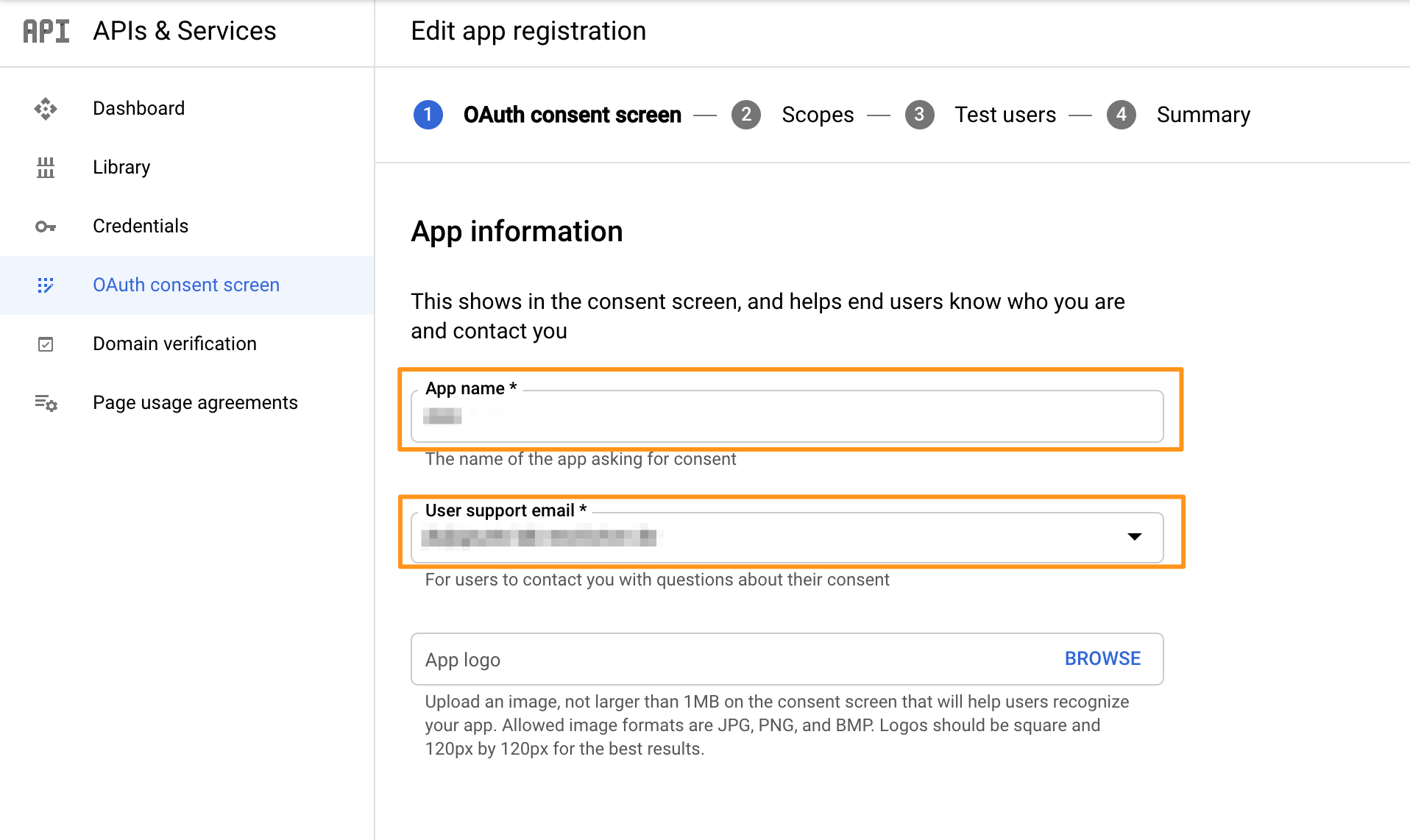
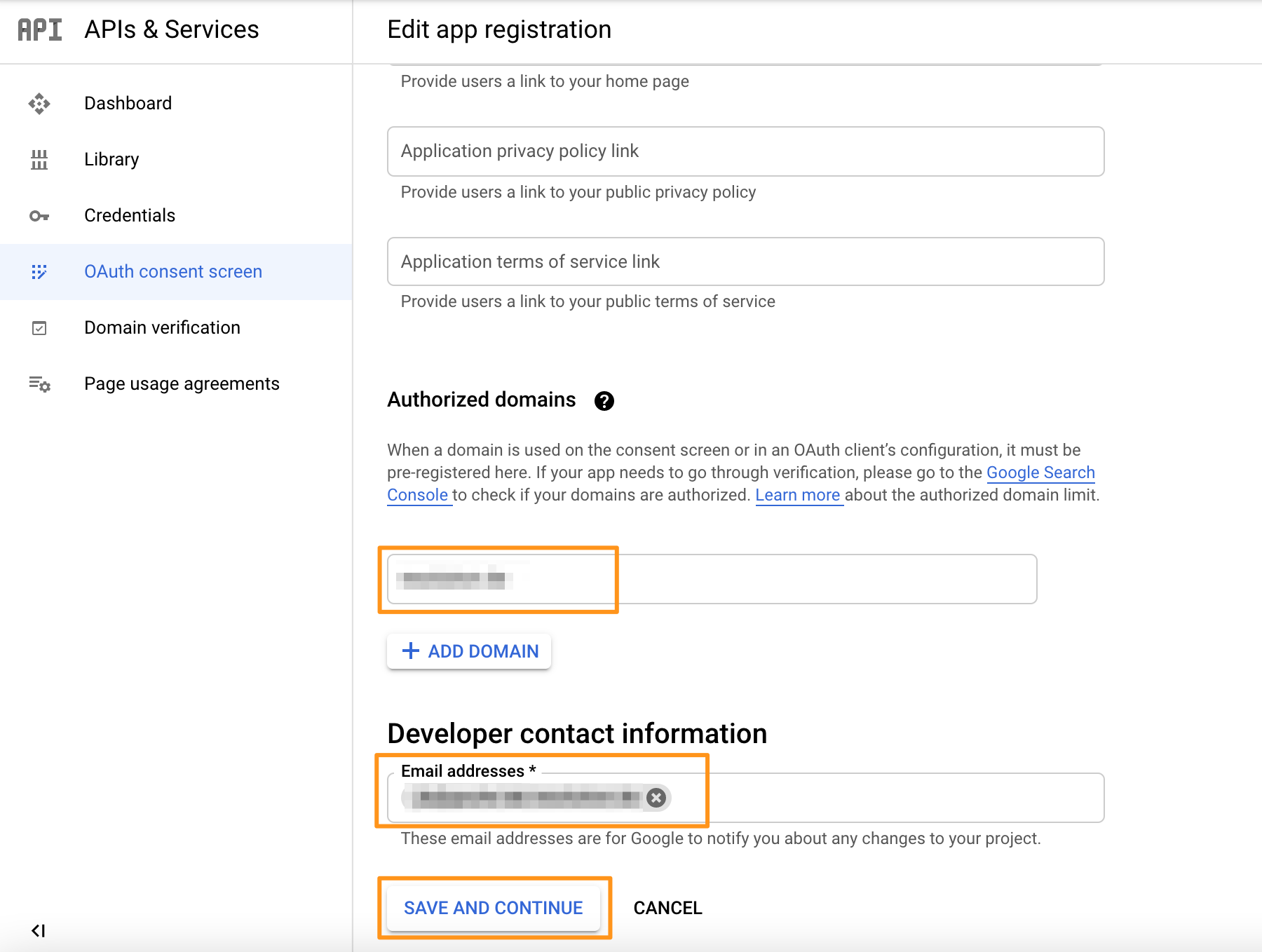
Scroll down to "Authorized domains" and enter your domain, e.g. "mycompany.com".
Enter an email address in the "Developer contact information" section.
Click on "SAVE AND CONTINUE".
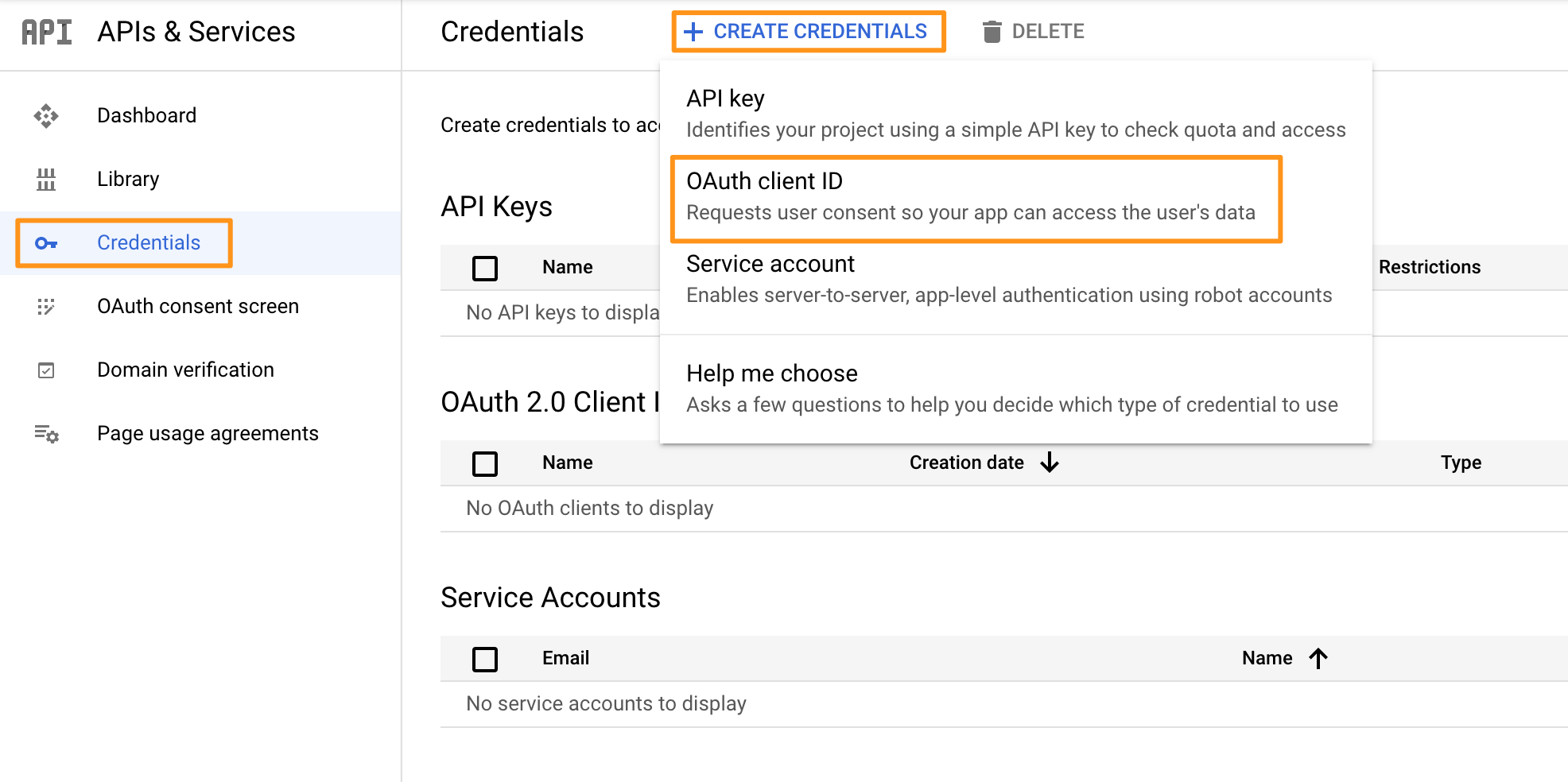
Go back to the Credentials tab on the left menu. On the next page, click on Create Credentials and click on OAuth client ID.
In the next window, choose "Web application".
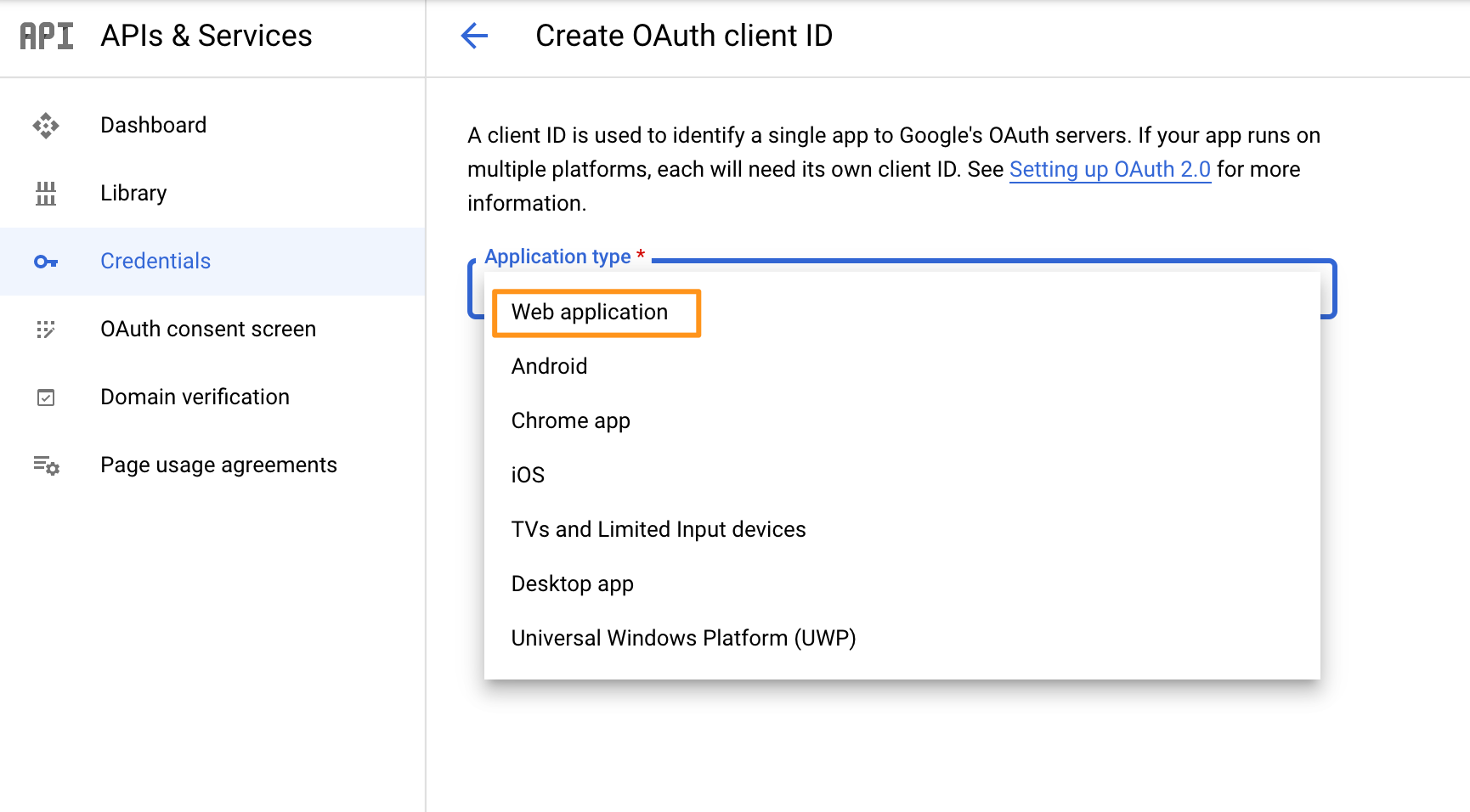
Choose ADD URI to enter an "Authorized redirect URIs".
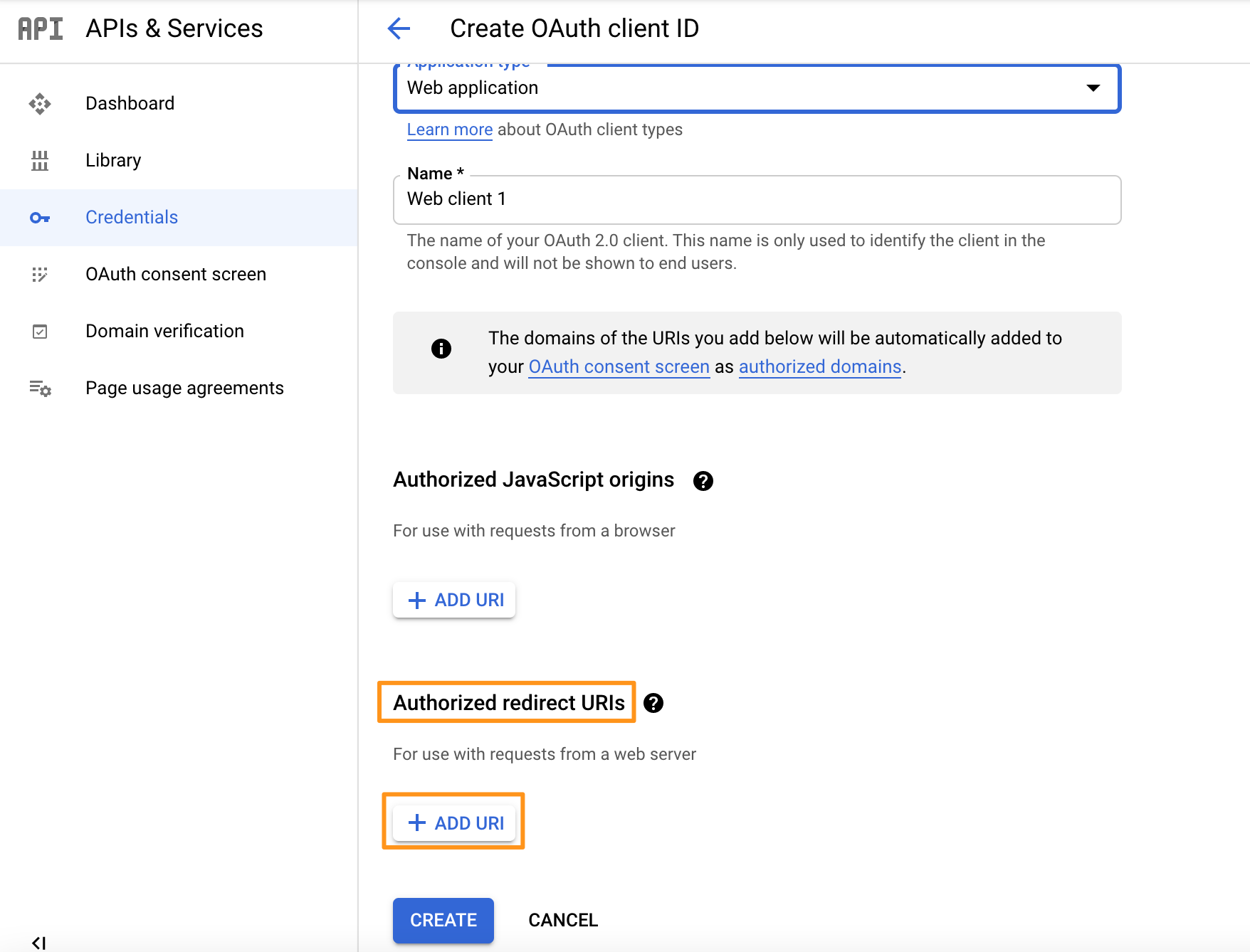
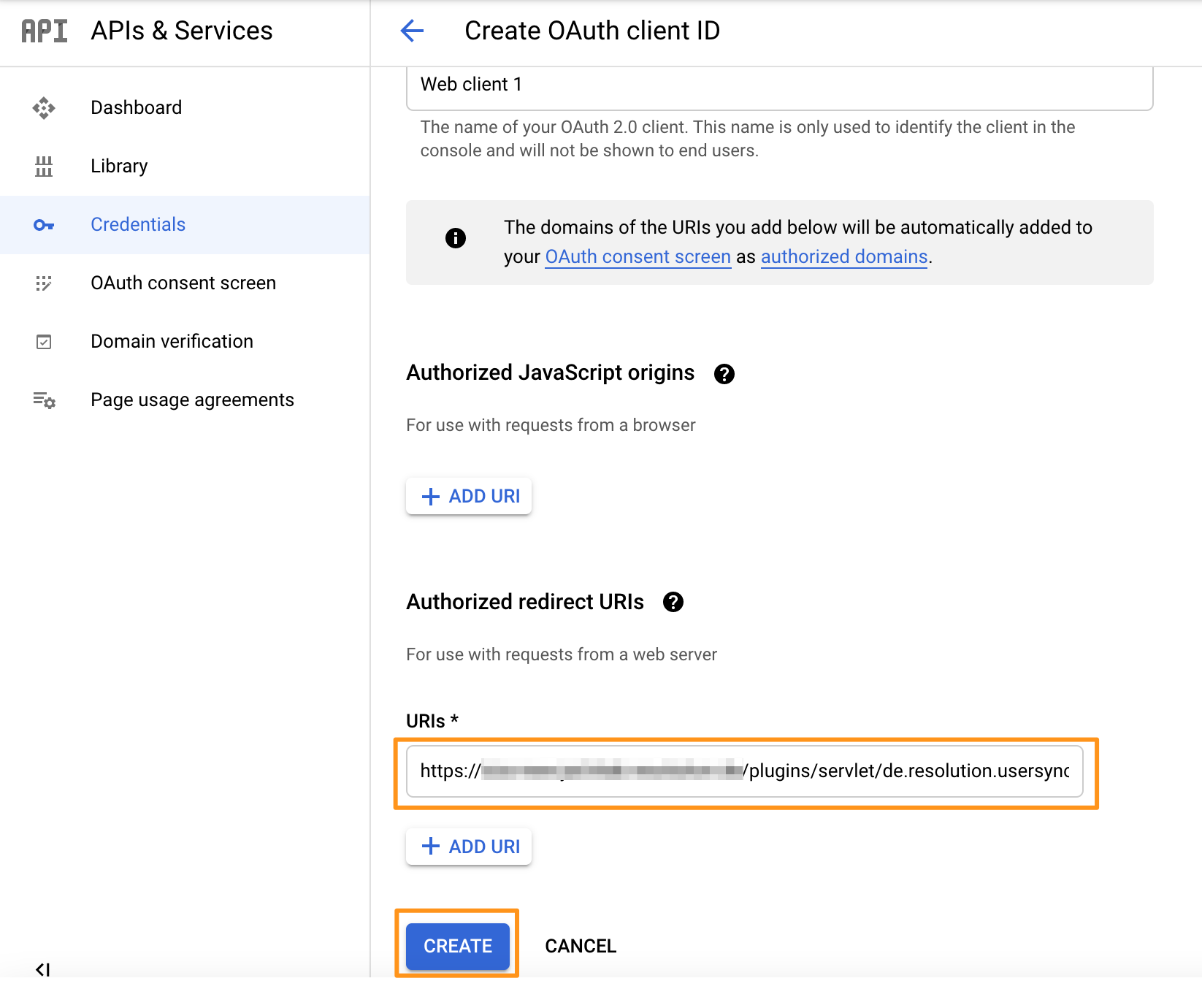
Enter the redirect URI as follows: https://<your-atlassian-product-base-url>/plugins/servlet/de.resolution.usersync/oauth2/authorize
You can now click "CREATE".
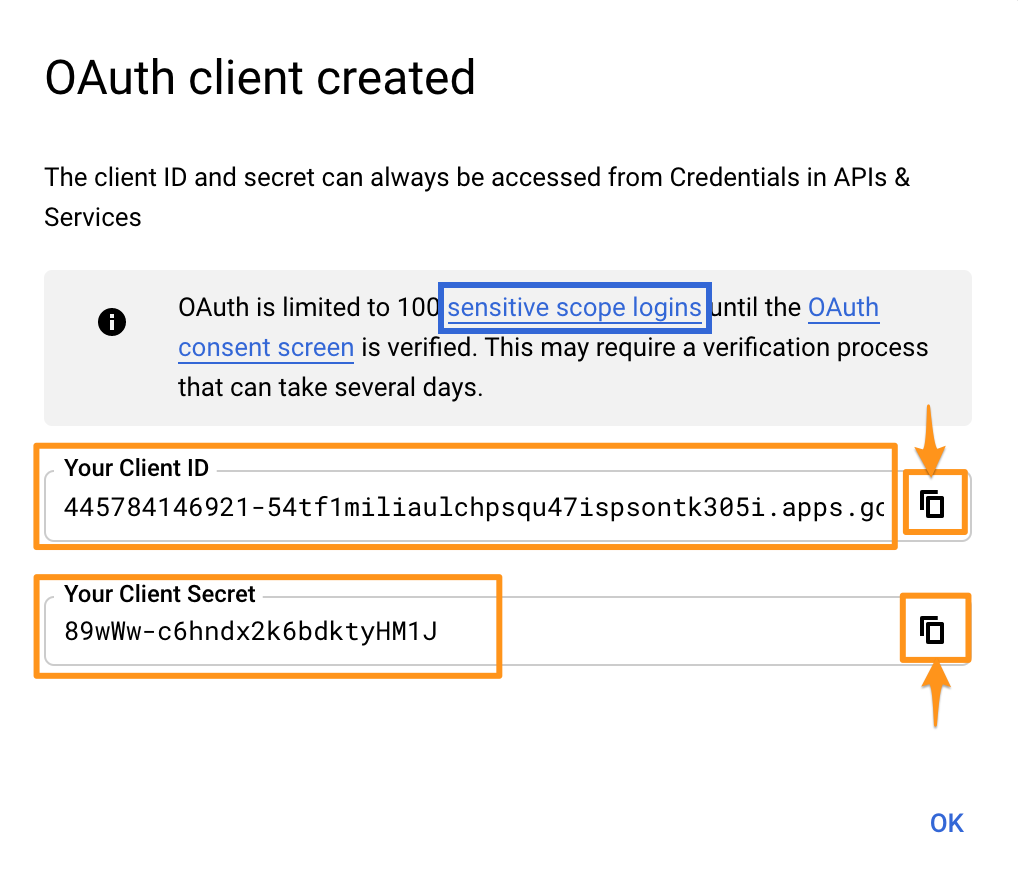
In the next window, you can see your "client ID" and your "client secret". You will need both for setting up User & Group Sync, thus save them somewhere where you can find them for the next step.
Now User & Group Sync can be set up in your Atlassian application. Press "Create Connector" and choose "Google Cloud Identity".
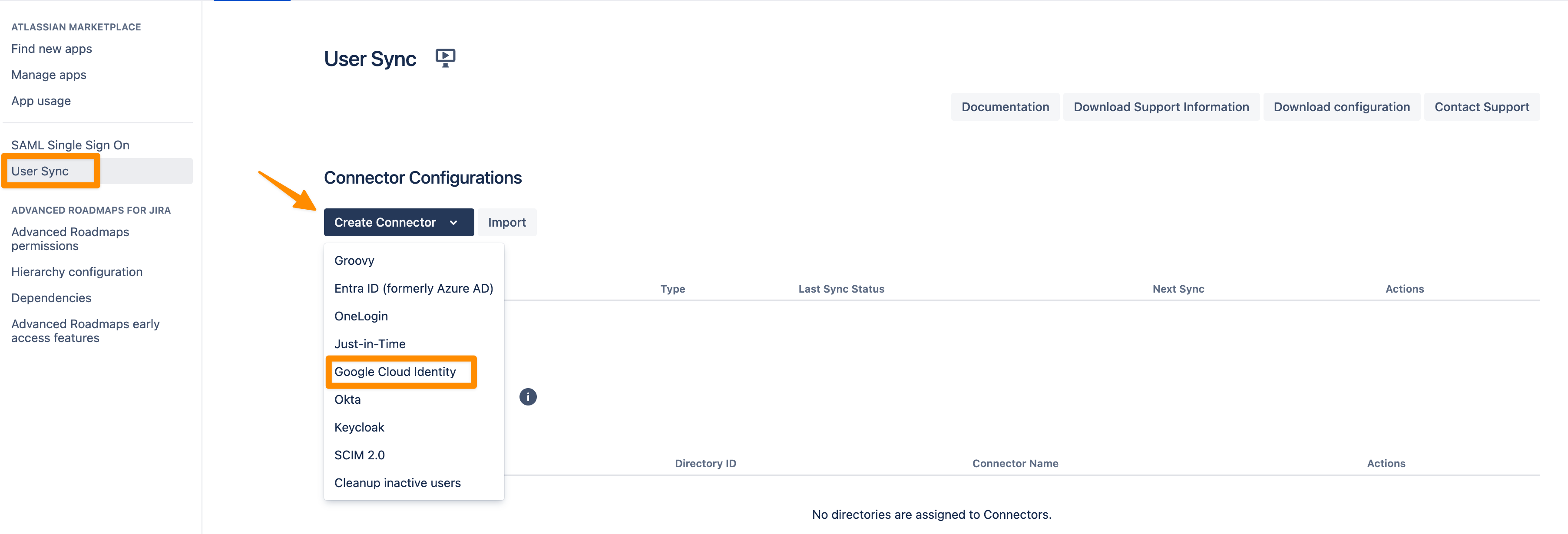
Enter your "Client ID" and "Client Secret" that you have copied earlier and click on "Start Authorization".
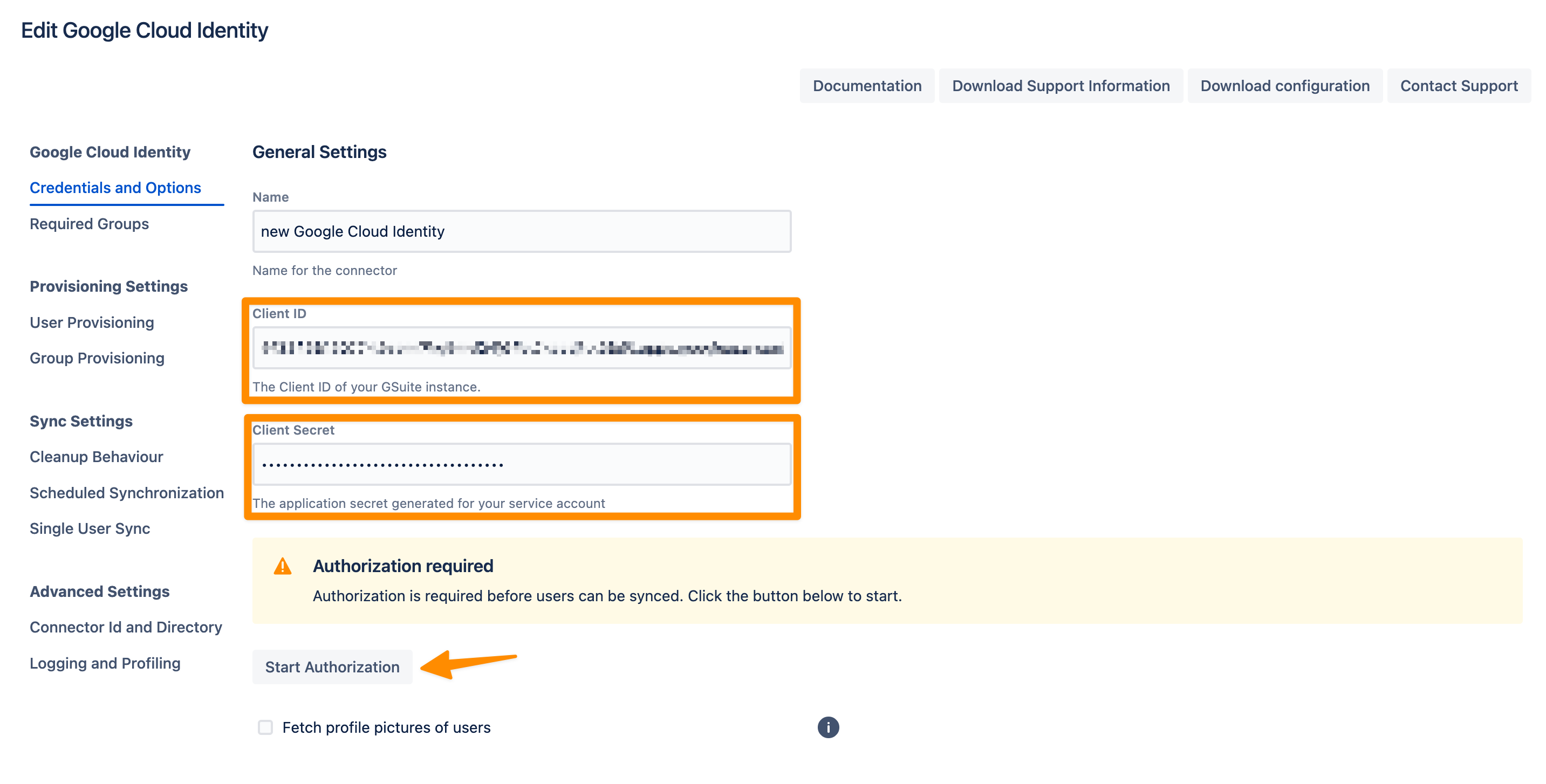
If you are a Google Cloud Identity Administrator, click on "Go to Google". Otherwise, copy the generated message and provide it to your administrator, and you can continue the configuration meanwhile by closing that window.
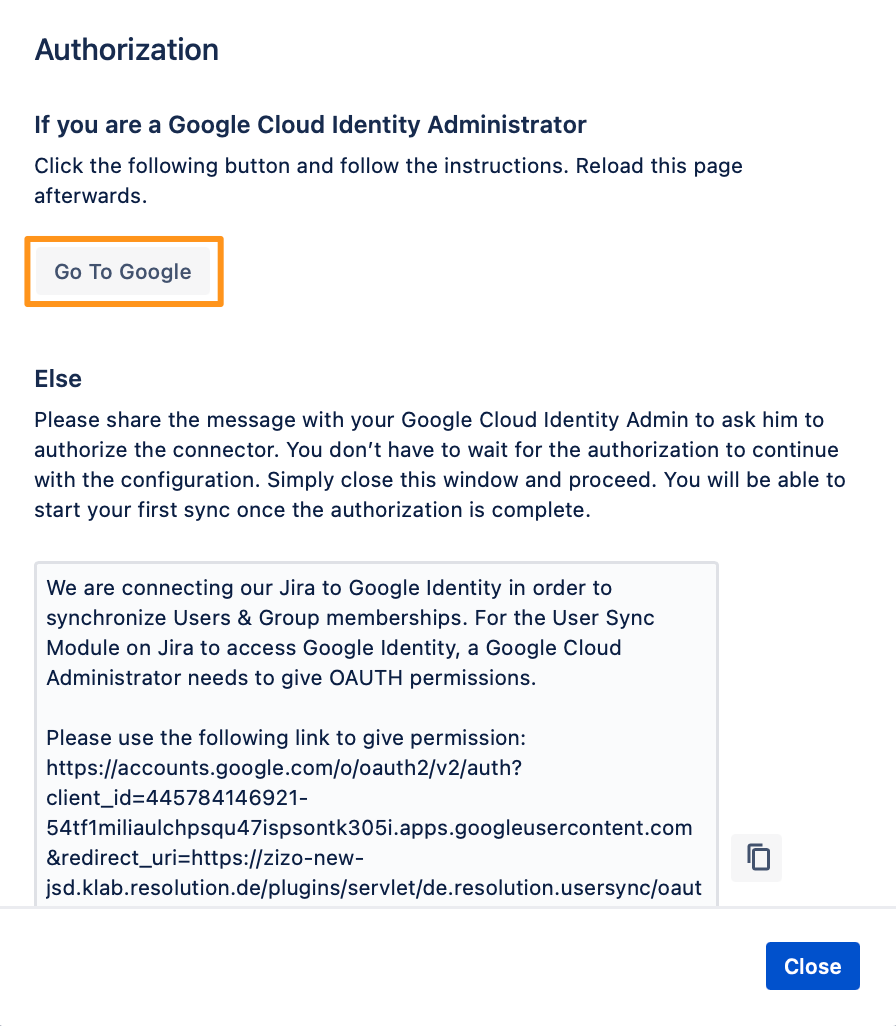
If the authorization was successful, you will see the following. Click Save and Test Connection to check whether User Sync can access all needed Google Cloud Identity API endpoints.
If you want to limit the number of users you sync from Google Cloud Identity you can set this up in the Required Groups tab. If you want to sync all users from your tenant you can skip this configuration step.
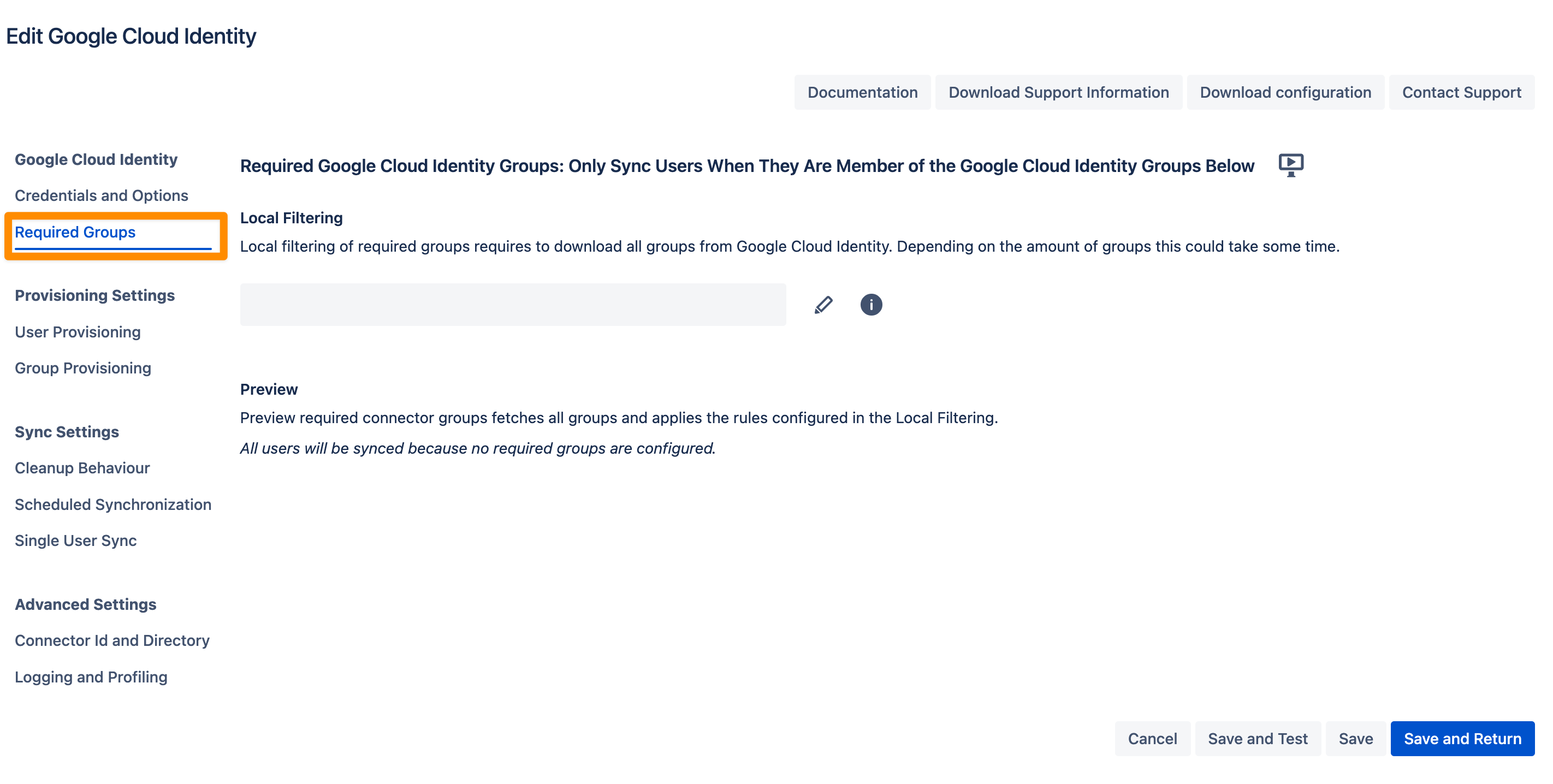
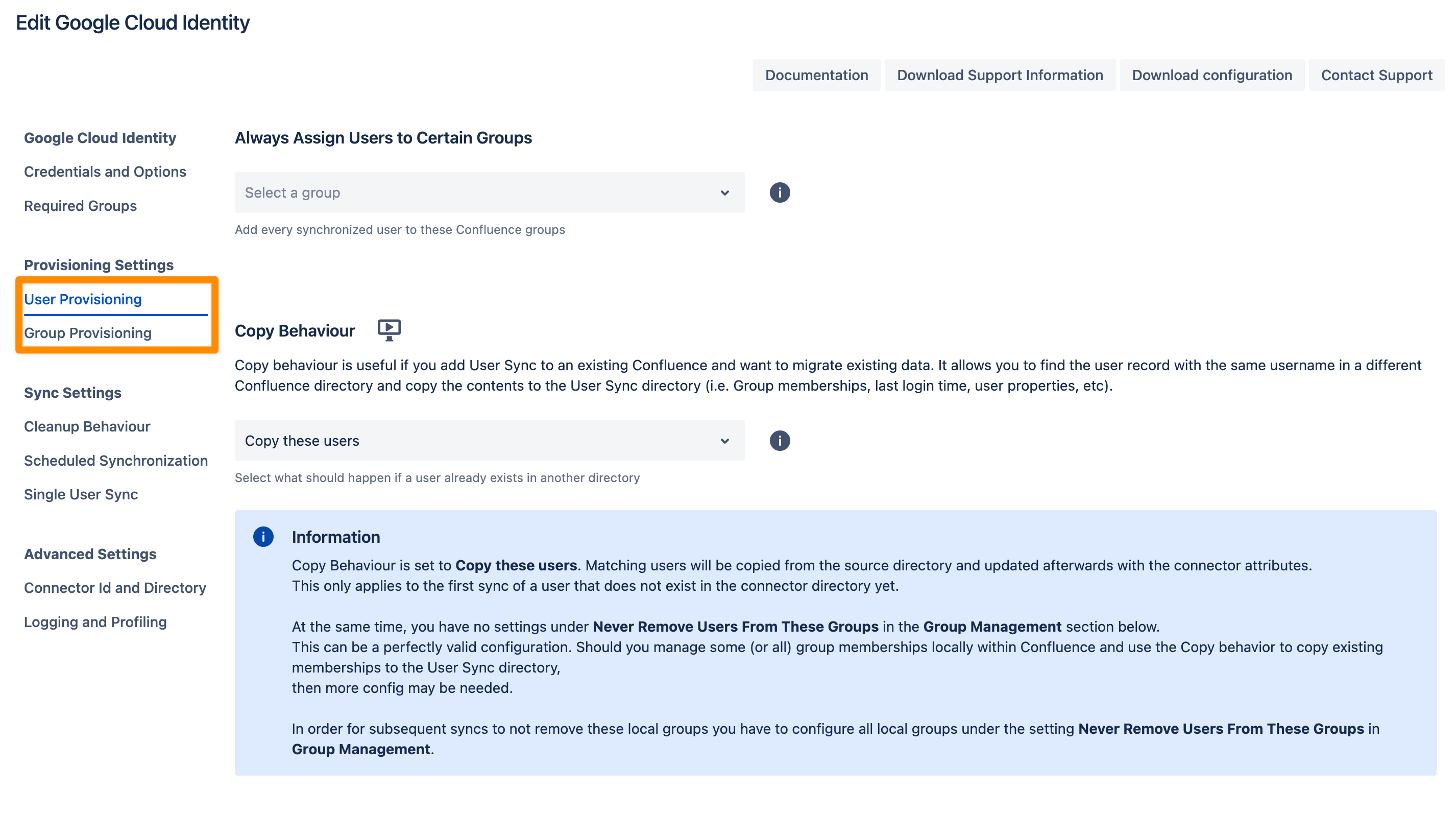
In the User Provisioning and Group Provisioning tab, you can change the attribute mapping for the user and define what groups should be assigned to users in case you don't need all groups from Google Cloud Identity. If you leave the settings unchanged the standard user attributes are synced together with all the groups that have been assigned to the user.
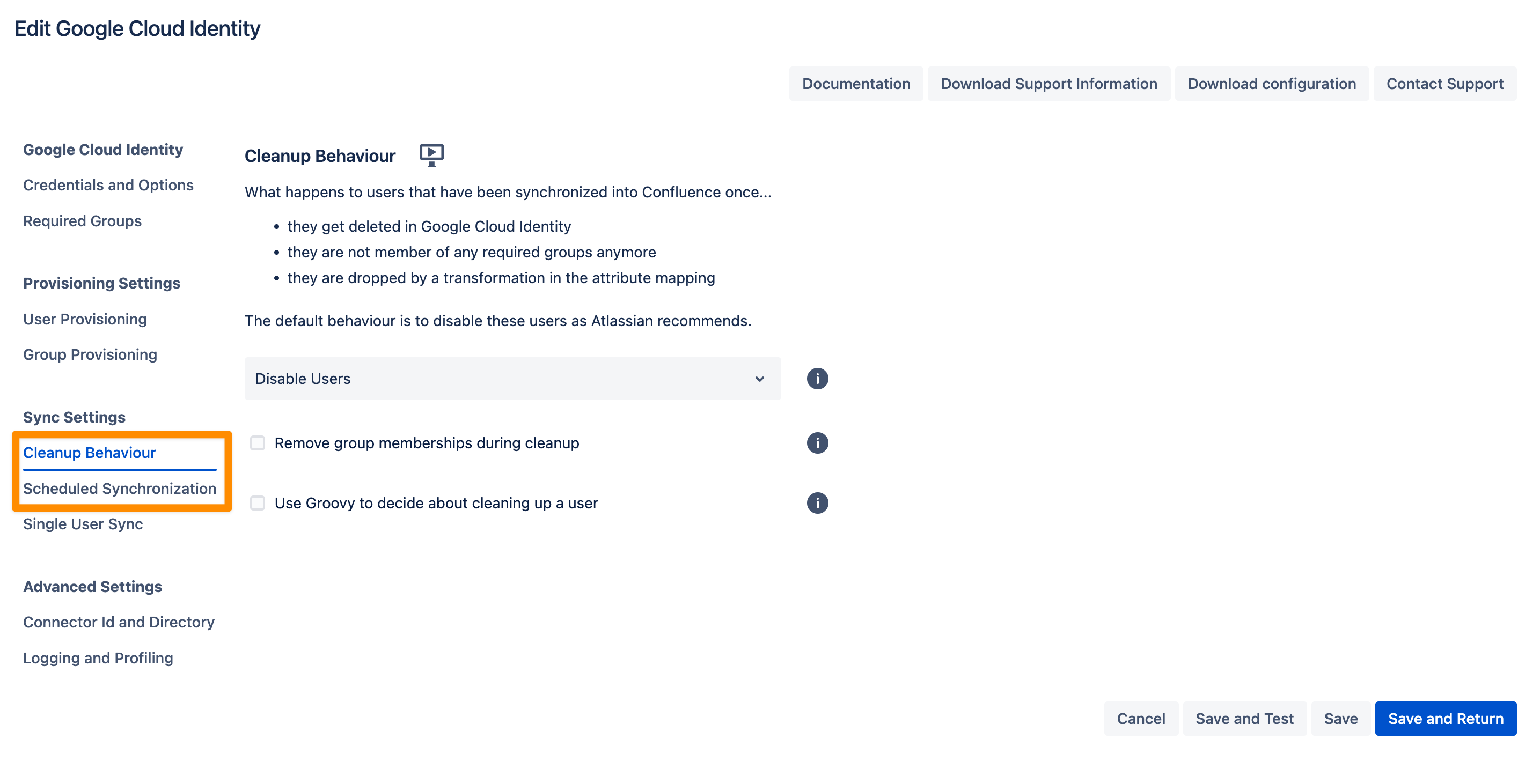
In the Sync Settings section, you can configure the Cleanup Behavior and the Scheduled Synchronization. The cleanup defines what should happen to the user when it is not returned by Google Cloud Identity anymore. The default is deactivating the user. By configuring the Scheduled Synchronization you can have the sync run periodically without manual interaction. When enabled the sync runs daily at 2 am but you can change this if you want.
Please ensure that you Save your configuration.
You are now ready to commence either a simulated or a full sync. By simulating the sync first you will be able to verify your configuration and see what changes User Sync would apply like what users will be added, modified, or not modified. With the full sync, User Sync will apply those changes. Both sync actions will run a full sync and will have the same sync duration. For more information on the sync simulation, please refer to Using the Simulated Sync Feature.
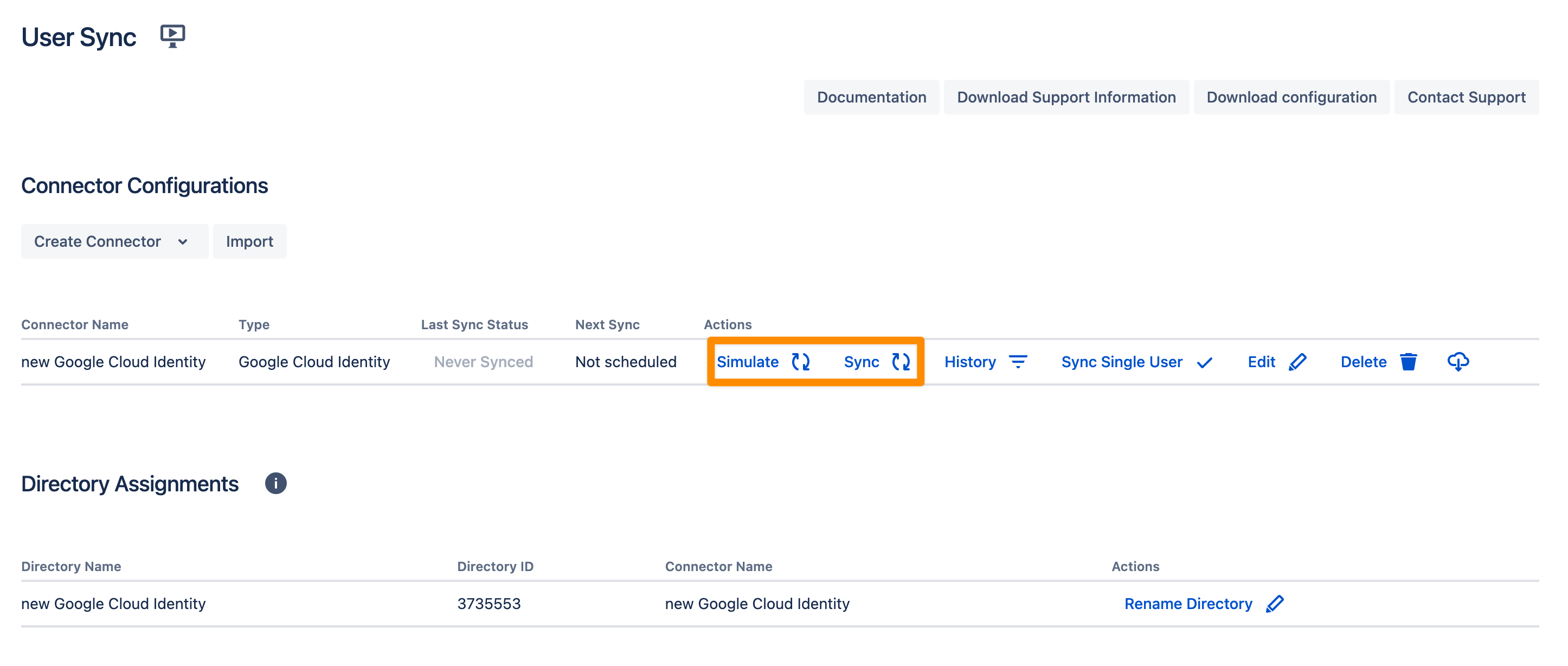
Please read here, if you already have users in your system which you want to migrate, without losing their history. Don't hesitate to reach out to https://www.resolution.de/go/support, if you need any help with achieving this.
