Could not find user, but had a successful User Sync update.
Problem:
We found the following in our log or in trackers:
Could not find user, but had a successful User Sync update. Please note, with a future version of SAML SSO login will fail. Please see https://wiki.resolution.de/go/userNotFoundButUserSyncSuccess for more information.
This message indicates that your SAML SSO configuration or IdP configuration is wrong. In particular, this means that
The single user update with UserSync was successful during login.
But SAML SSO could not find the user with the information from the SAML response.
This can mean that either your SAML SSO configuration must be adjusted or you must change your IdP's configuration. If you feel unsure, please contact us at https://www.resolution.de/go/support.
Background
With SAML 3.x, users were logged in when there was at least a successful single user update during a SAML login. This also means, that SAML SSO does not search for the users again if there was a successful single user update during login.
As a consequence, if the information sent by the SAML response does not match your local user (e.g. because of a username transformation), users were still logged in even with a wrong SAML SSO configuration.
We intend to change this in near future such that after a successful single user update, SAML SSO will search for the user with the information from the SAML response. Thus, if you do not adjust your configuration,
the SSO will fail.
Possible causes and Solutions
One of main causes will be that you have configured a transformation in UserSync, which does not match the data from the SAML response.
In the following, we will examine an example. Please note that it is only an example, the case might different for you. If you feel unsure about what to do, please contact us at https://www.resolution.de/go/support!
Example:
One of the most common transformations in UserSync is to cut-off the domain from an email to match the local username. So, consider that the username of the local user is a.example, while the IdP sends a.example@domain.com for the username.
Thus, you configured a transformation in UserSync to adjust what is sent by the IdP, but did not do the same for the SAML SSO configuration.
This becomes a problem because when SAML SSO searches for the user, since it searches with what the IdP sends without transforming it:
In essence, you cannot find a.example when searching for a.example@domain.com.
To investigate this, please see the following:
Go to the SAML SSO configuration.
Scroll down User Creation and Update:
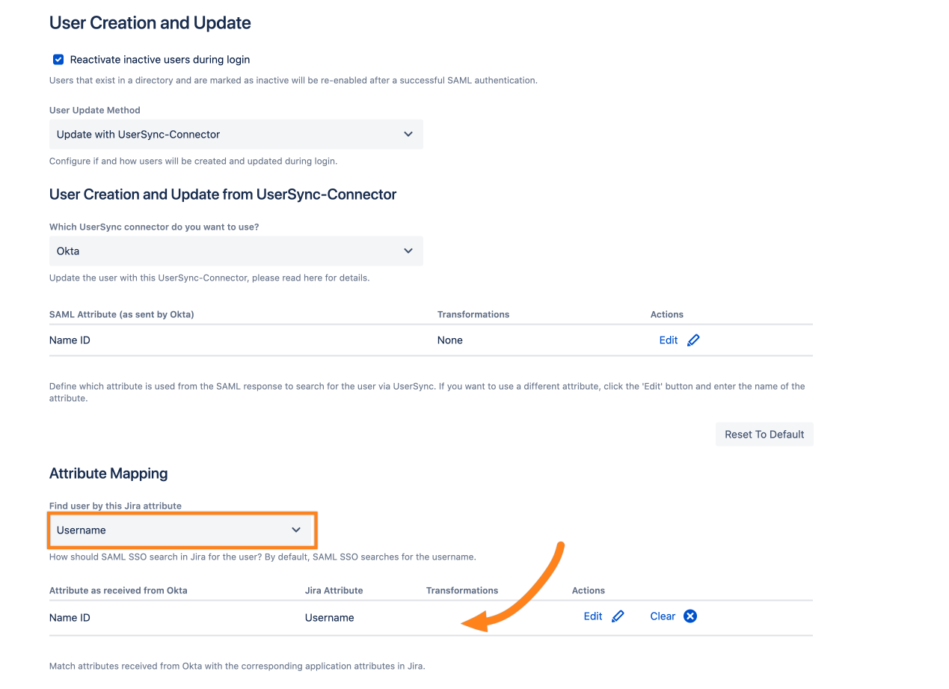
The Find user by attribute is set to Username (this can be different for you), meaning that SAML SSO searches users by their username to log them in. Below, you can see which attribute from the SAML response is used for the username. In this example, it is the Name ID.
Please note, that there is NO transformation for the username configured. Thus, SAML SSO takes the raw value from the SAML response and searches for this user for the username without altering the value.Now, go to the UserSync configuration of the connector and scroll down to the user mapping table. Search for the Username row (or whatever is configured for the Find user by attribute):
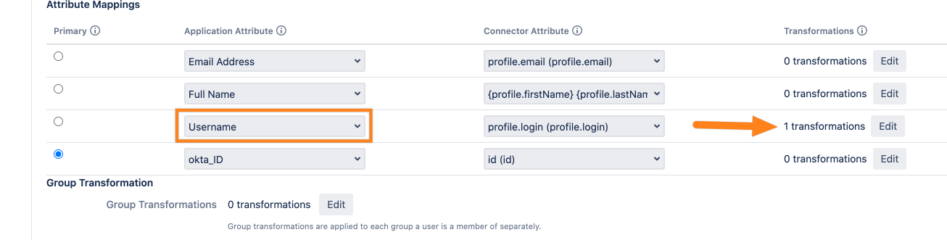
You can see, that there is a transformation for the username. If you consider the IdP sends the same for the SAML response as for the UserSync attribute, this means that the username as retrieved (and transformed) by UserSync will not match the username as retrieved from SAML SSO.
Thus, SAML SSO can not find the user because the attribute was transformed from UserSync, but not in SAML SSO configuration.
In this easy scenario, you can easily fix the problem by adding the same transformation to the SAML SSO configuration for the username attribute. Please note, that it is not always so easy to fix this and you may need to adjust your identity provider configuration.
Please do not change your UserSync configuration, this is a problem of the SAML SSO configuration.
If you feel unsure about this, please contact us at https://www.resolution.de/go/support or book a meeting via https://www.resolution.de/go/calendly.


