Admin password prompt (WebSudo)
Starting with version 3.6.0, the SAML Single Sign-On app can delegate WebSudo authentication to the configured SAML Identity Provider (IdP).
As of version 6.6.0, WebSudo authentication is also supported for OpenID Connect configurations.
Limitations
WebSudo with SSO does not work with transient NameIDs.
This is because the SAML NameID from the additional authentication must be the same as the one from the initial login.WebSudo for Bitbucket was introduced in version 9.x, but does not support WebSudo functionality with SAML/SSO (refer to https://jira.atlassian.com/browse/BSERV-19537)
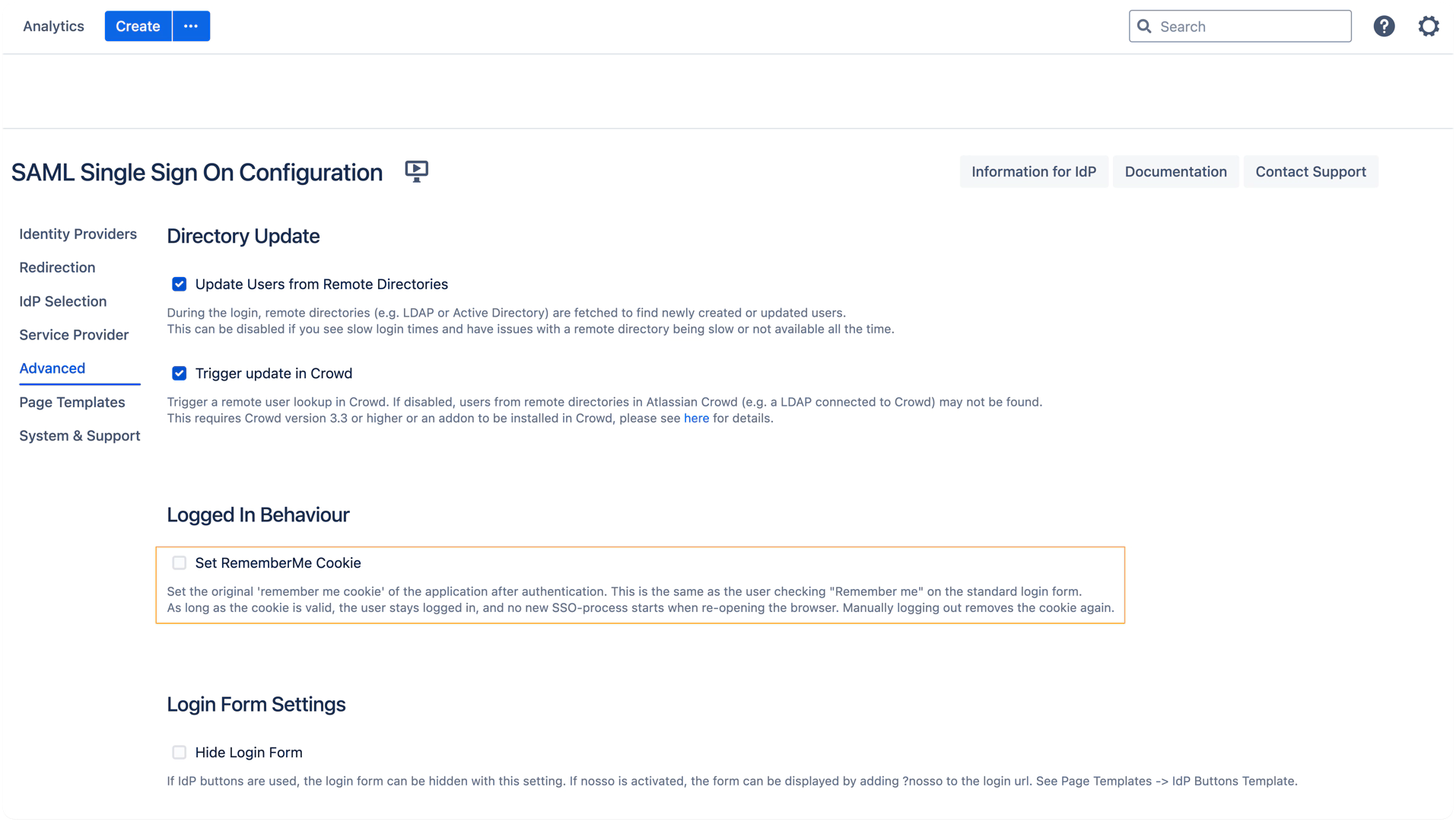
WebSudo with SSO does not work if the Set RememberMe Cookie option is enabled. Once the Remember Me cookie is used to re-establish a user session, it is no longer considered a SAML session. If the blue reauthenticate button does not appear as expected, the only current workaround is to log out and log in again using SAML SSO. To ensure WebSudo functions correctly, please disable the Set RememberMe Cookie option as shown below.
Configuration
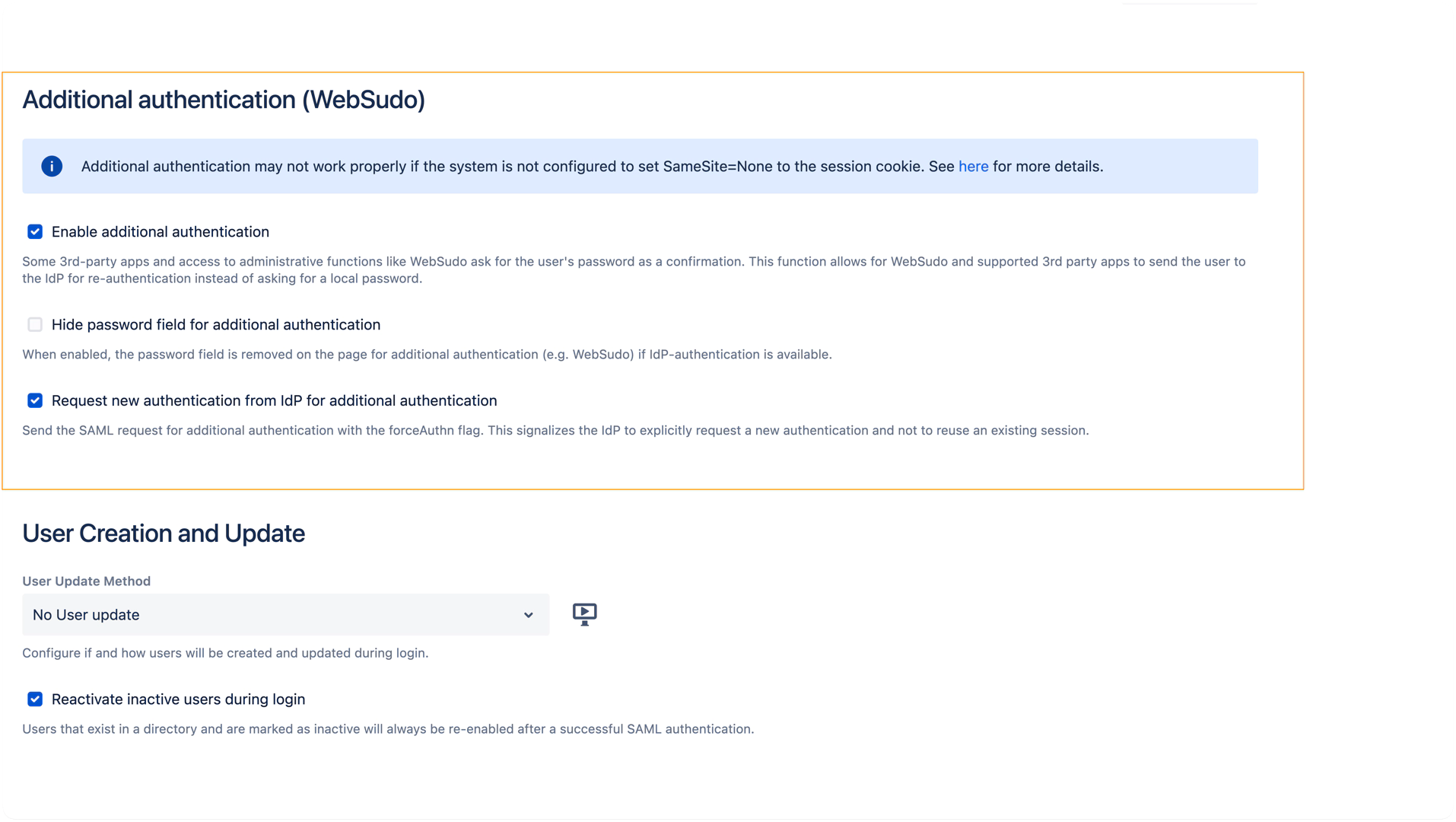
The Enable additional authentication setting is enabled by default. This feature allows WebSudo and supported third-party apps to request re-authentication from the Identity Provider (IdP) instead of asking for the user’s password again.
The following options are available in the Additional authentication (WebSudo) section:
Enable additional authentication (enabled by default)
Activates IdP-based re-authentication for admin actions and third-party apps that require additional confirmation (e.g. WebSudo).Request new authentication from IdP for additional authentication (enabled by default)
Sends a SAML request with theforceAuthnflag to explicitly trigger a fresh login at the IdP, rather than reusing an existing SSO session. This helps ensure the additional authentication is truly validated by the IdP. Since version 6.6.0, this option can be disabled, in which case the SAML request is sent without theforceAuthnflag.
Recommendation: Keep this option enabled to ensure a secure, fresh authentication at the IdP during WebSudo operations.
Hide password field for additional authentication (optional)
When enabled, the local password field is removed from the additional authentication page.
Additional authentication may not work correctly unless the session cookie is sent with SameSite=None.
In Confluence versions earlier than 9 and Jira versions earlier than 10, session cookies can be configured to use
SameSite=Noneusing the built-in setting “Set SameSite=None on the session cookie”, which has been available since version 4.0.7 of the SAML SSO app. This setting was made enabled by default in a later version, but earlier versions may require it to be enabled manually.For Confluence 9+ or Jira 10+, this built-in option is no longer sufficient due to changes in the underlying platform (Tomcat handling).
In these cases, customers must configureSameSite=Noneat the Tomcat level or via a reverse proxy.For detailed instructions on all of these configuration methods, see the documentation described here.
WebSudo Flow with Re-Authentication Button
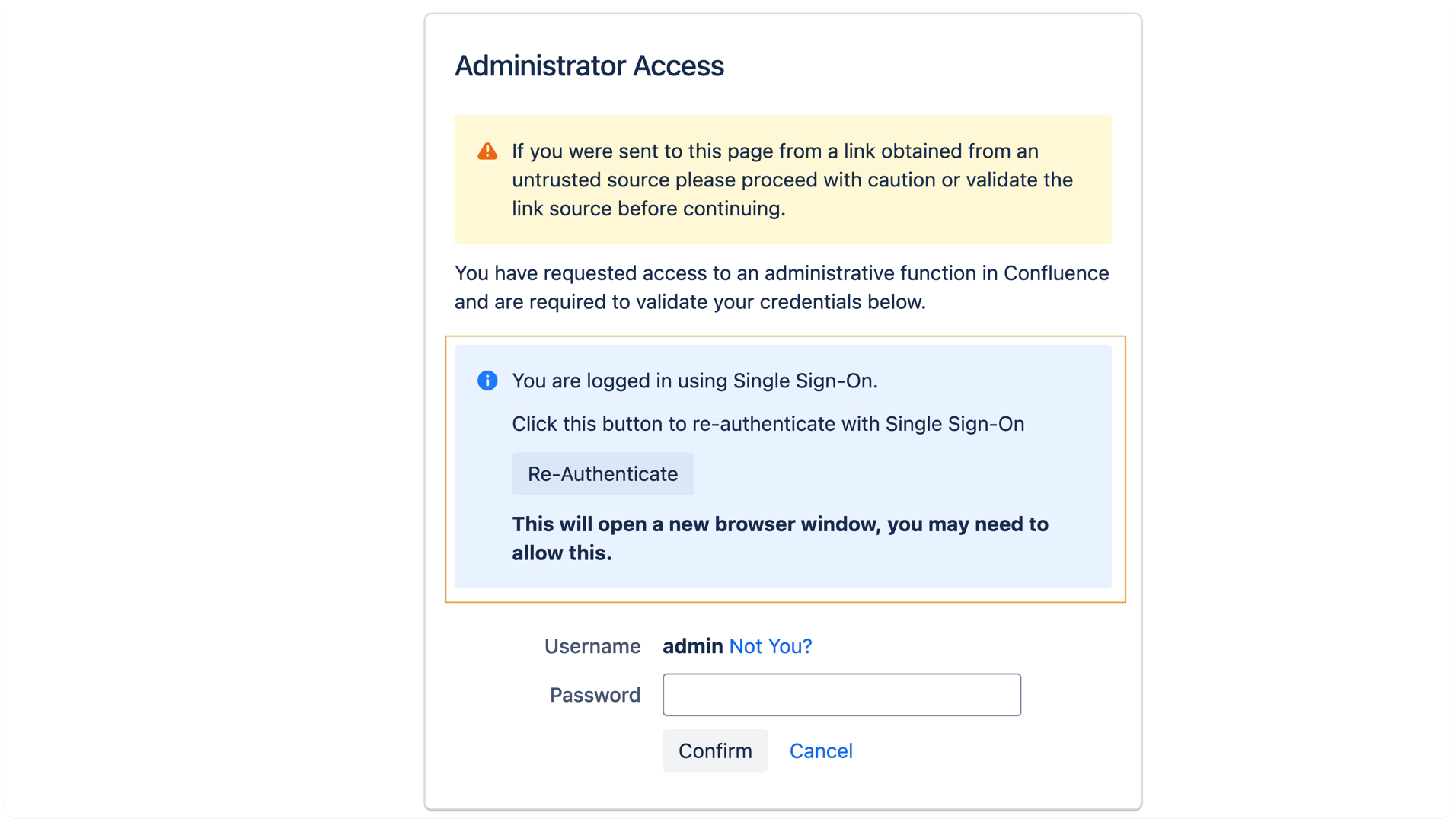
If the current admin user is logged in using SAML and additional authentication is enabled for the IdP the user authenticated with, the WebSudo page will show a Re-Authenticate button alongside the default local password prompt provided by Atlassian. To hide the password field and enforce SSO-only re-authentication, the admin must enable the optional "Hide password field for additional authentication" setting in the additional authentication configuration.
Clicking the Re-Authenticate button triggers a SAML authentication request, including the forceAuthn flag (depending on your configuration), to revalidate the user’s identity through the Identity Provider.
A new browser window with the IdP's authentication page will be opened, where the user needs to authenticate again.
After successful authentication, starting the WebSudo session must be confirmed before the window is closed automatically:
When the Re-Authenticate Button Does Not Appear
In some cases, the Re-Authenticate button is not displayed on the WebSudo page. This happens when:
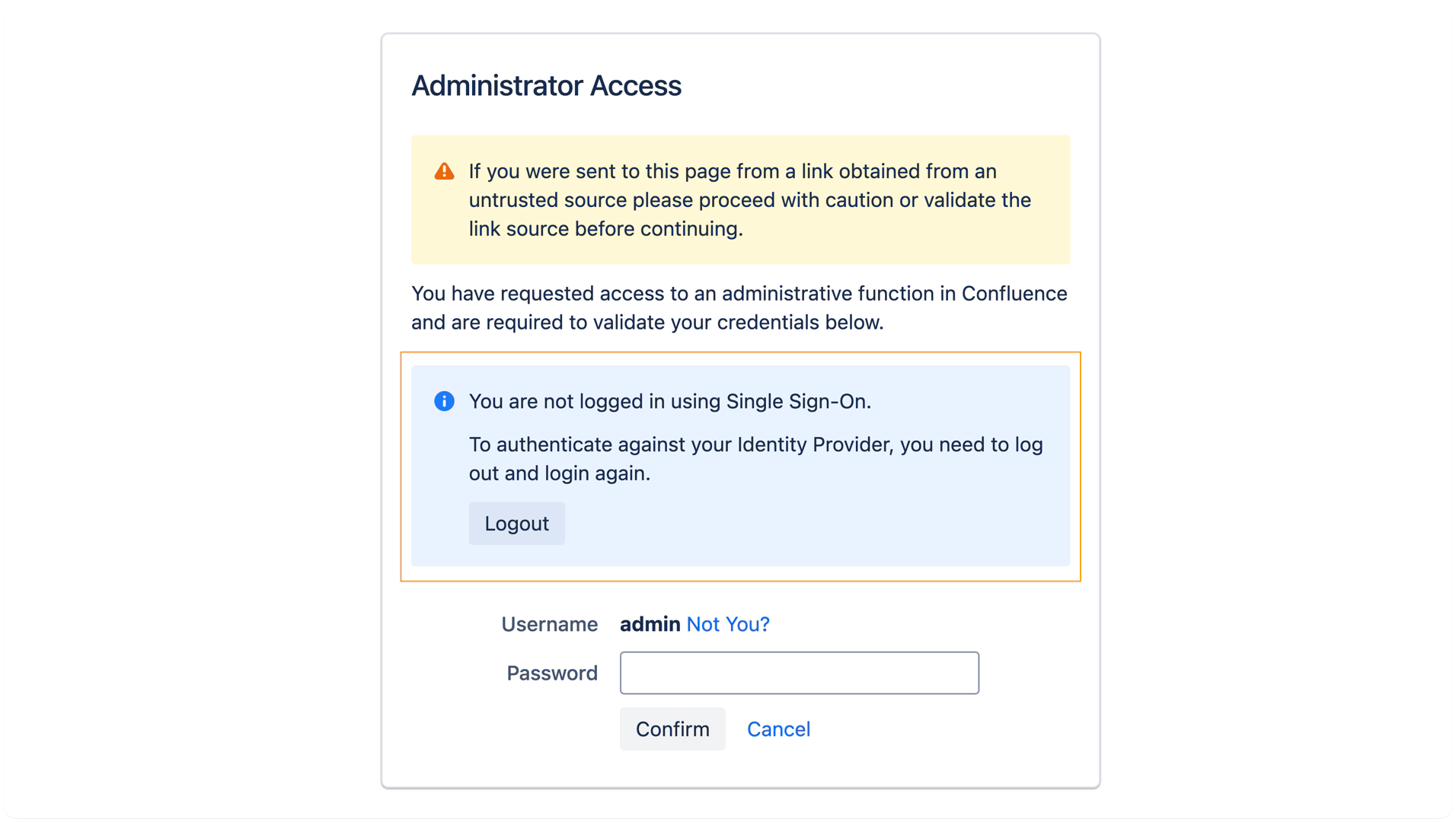
The session was restored using the Remember Me cookie rather than a fresh SAML login.
The admin user logged in with a local username and password instead of using SAML SSO.
In these situations, the WebSudo screen shows only the standard password prompt and a message indicating that you're not logged in via Single Sign-On.
To proceed with SSO-based re-authentication, you need to log out and log in again via your Identity Provider.