Dealing with JSM portal customers who are not part of the required groups of UserSync
Use Case
Scenario
You are using our SAML SSO with UserSync provisioning.
You are using the Required Groups in the UserSync connector, to limit the sync to only a subset of the users from the identity provider.
You are assigning the
jira-software-usersgroup (the group that gives application access) to everyone who is sync'd by default.
Requirements
You would like to enable the SSO redirection also for customers who are accessing JSM portals (check how to, here).
Those users (customers) are not members of the required group in the identity provider, but you still need them to be provisioned by UserSync.
You don't want to assign the
jira-software-usersgroup to them by default when they log in.The UserSync Cleanup Behaviour should be applied as normal to everyone in the UserSync directory when a full sync is executed.
Prerequisite
The following solution requires SAML SSO v6.3.0 or above.
Solution
The following settings need to be applied to your UserSync connector settings:
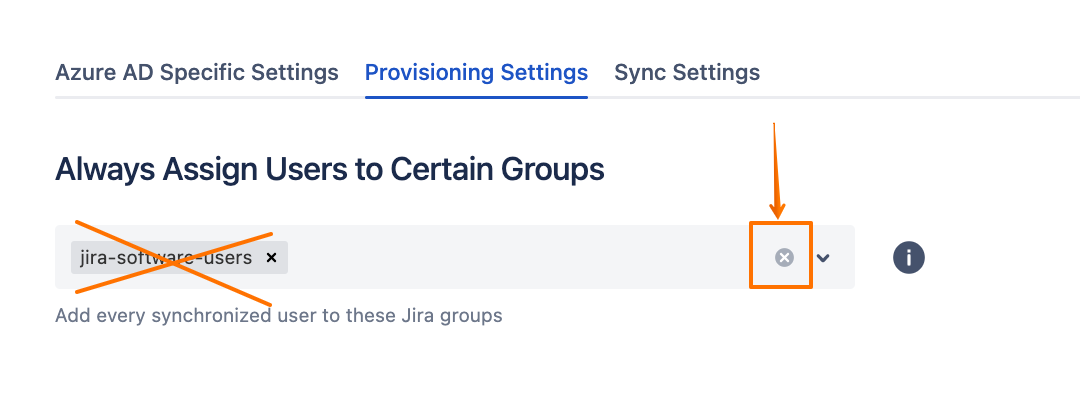
Under the Provisioning Settings tab, remove the default assignment of the
jira-software-usersgroup from the Always Assign Users to Certain Groups section: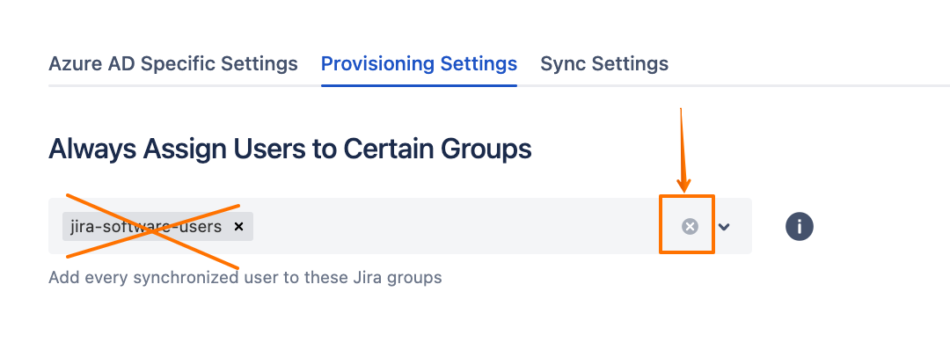
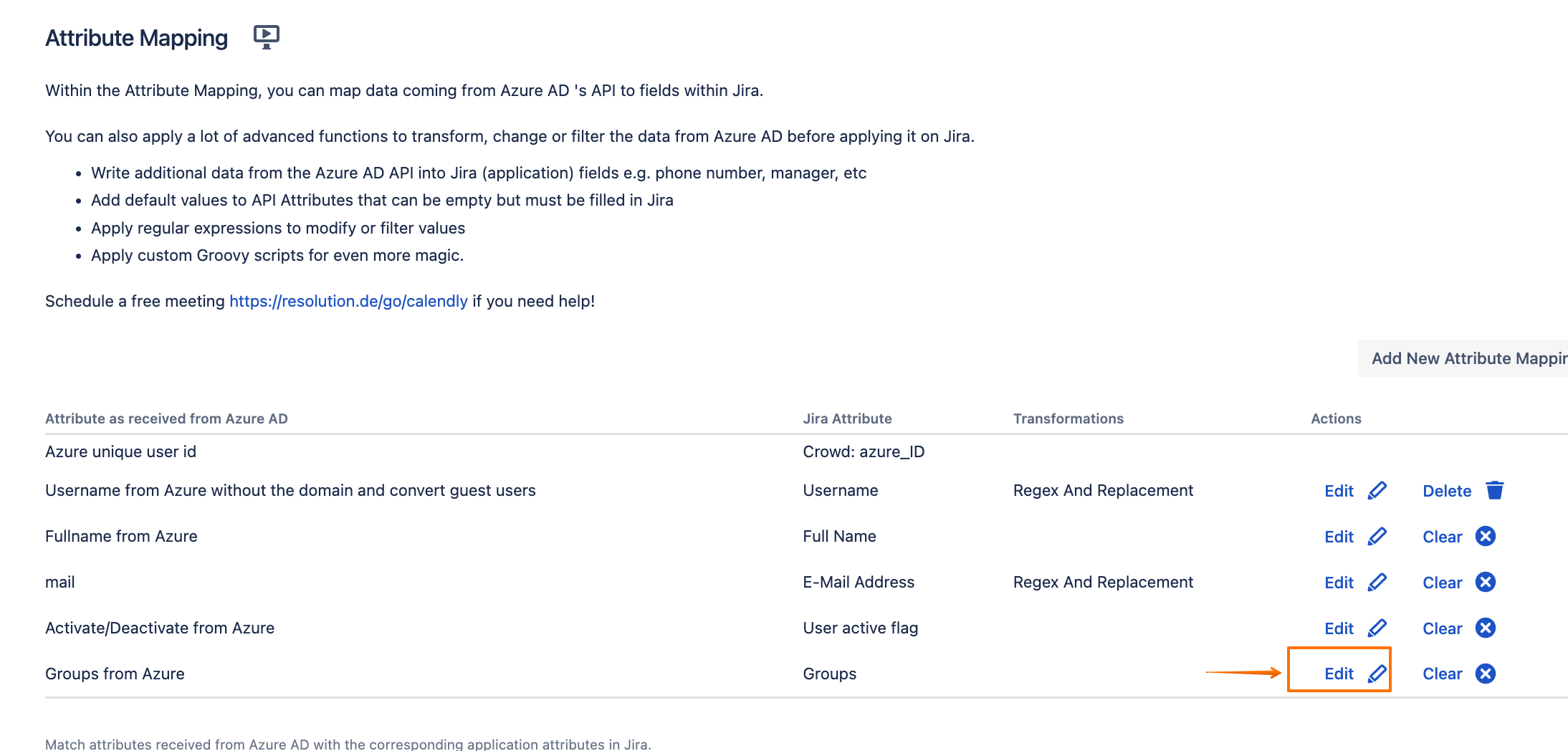
Scroll down to the Attribute Mapping section, and click on Edit beside the Groups attribute:
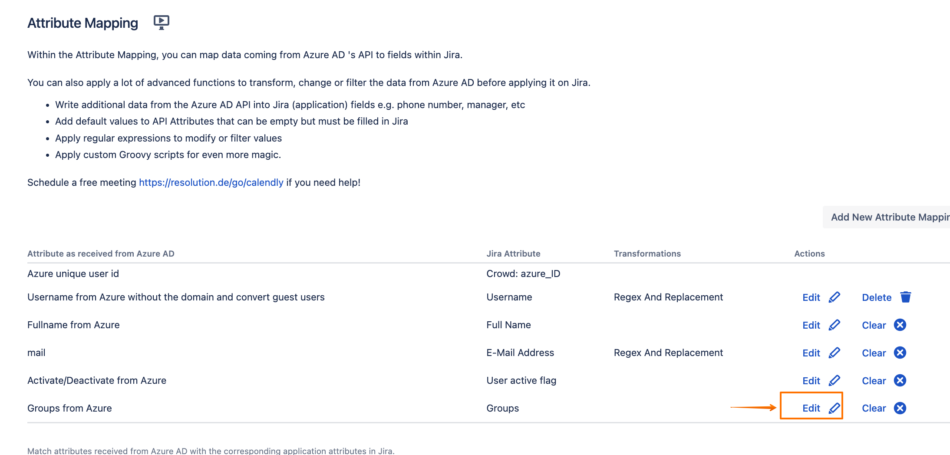
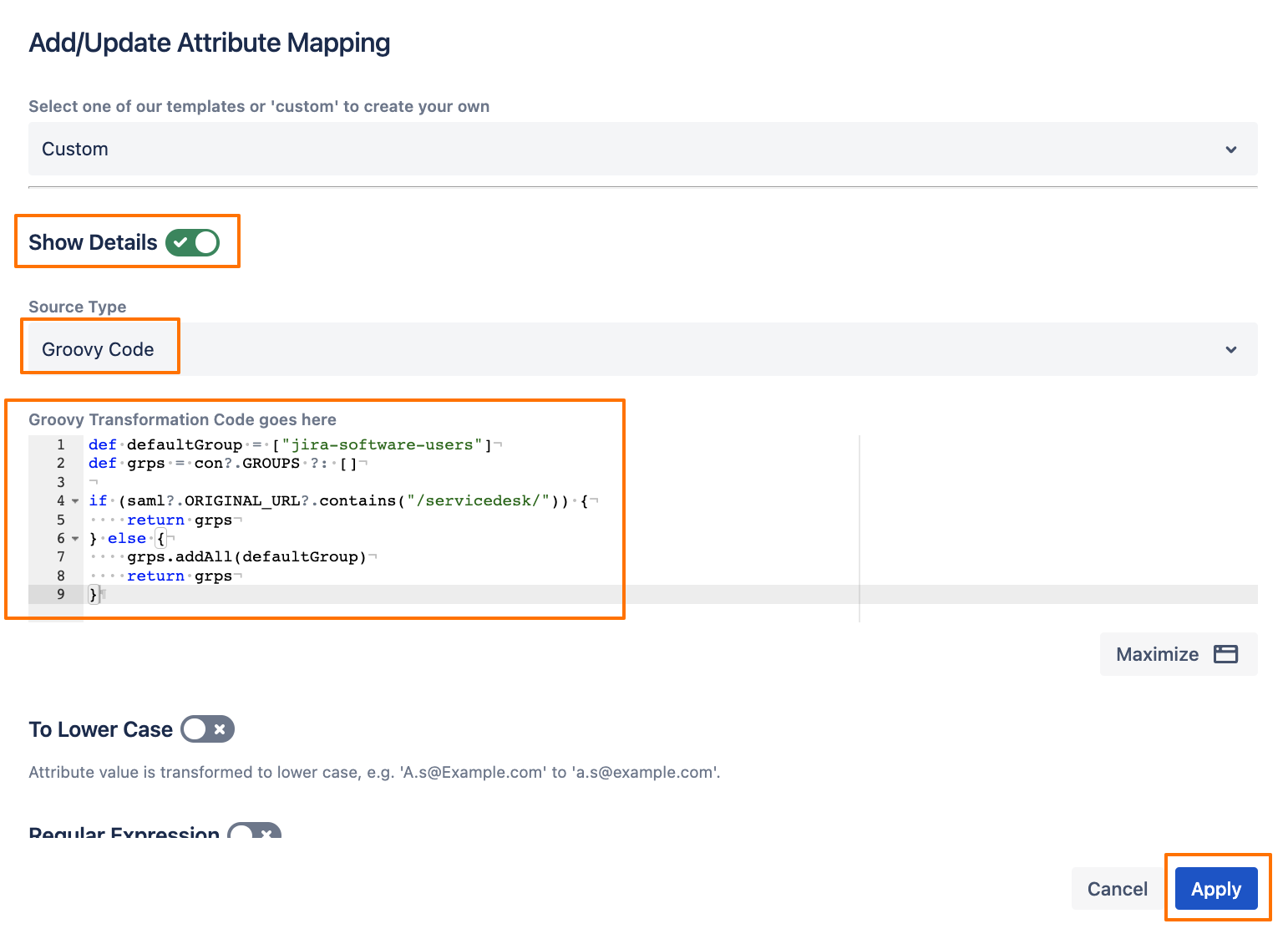
Click on Show Details, then choose Groovy Code for the Source Type, and enter the following Groovy code:
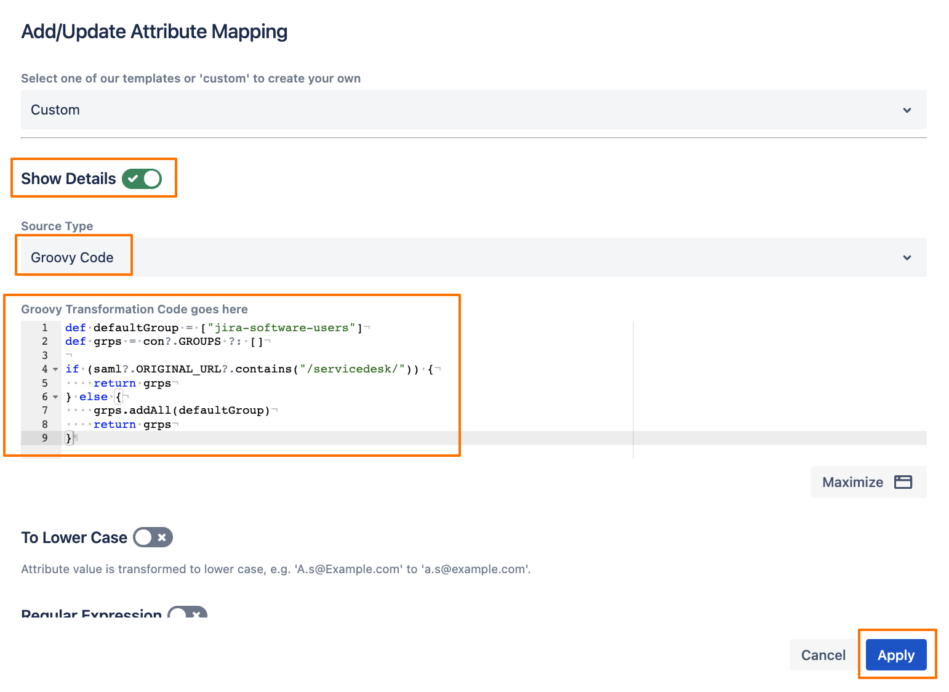
- def defaultGroup = ["jira-software-users"]
- def grps = con?.GROUPS ?: []
- if (saml?.ORIGINAL_URL?.contains("/servicedesk/")) {
- return grps
- } else {
- grps.addAll(defaultGroup)
- return grps
- }
Click on Apply, and Save the connector settings.
The above should only assign the jira-software-users group to users when they don't access the Service Management URL. If the customer accesses the JSM portal URL, the group would not be added.
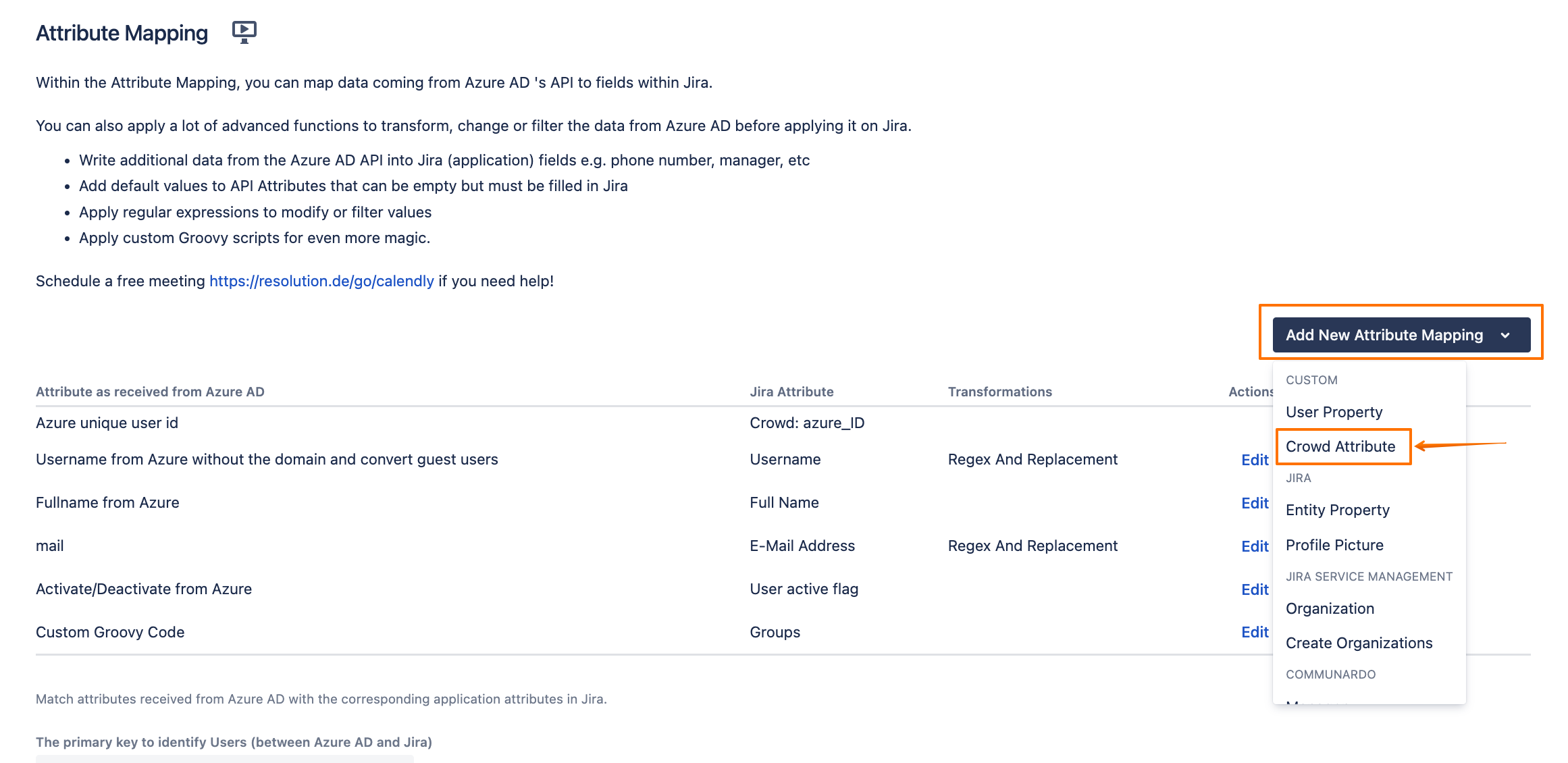
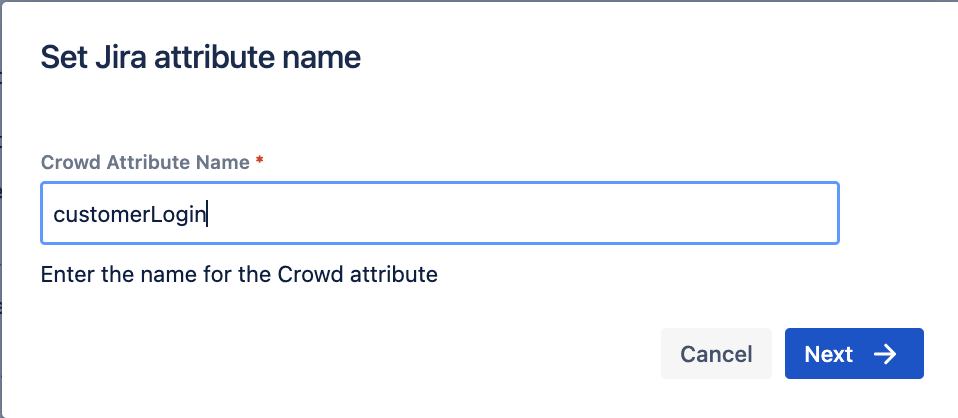
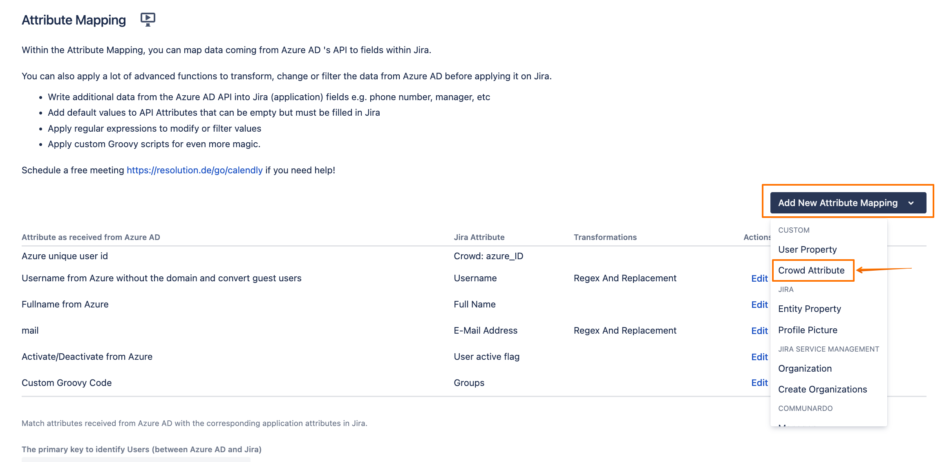
In the Attribute Mapping section, click on Add New Attribute Mapping, and choose Crowd Attribute:
Give it a name:
customerLogin, and click on Next: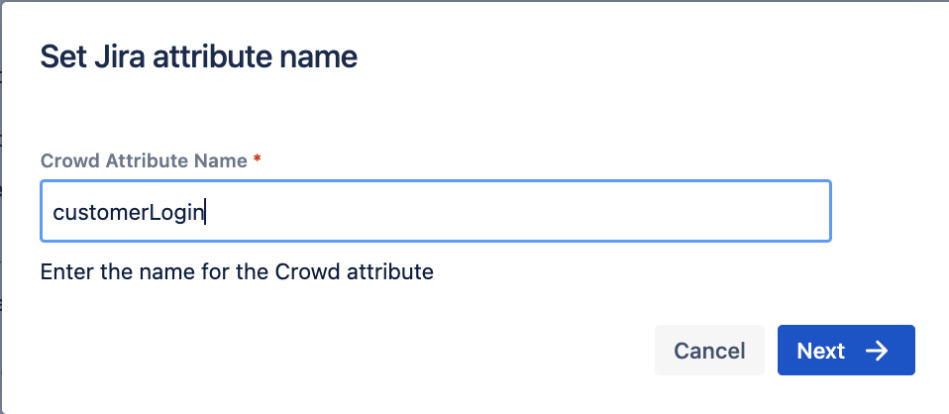
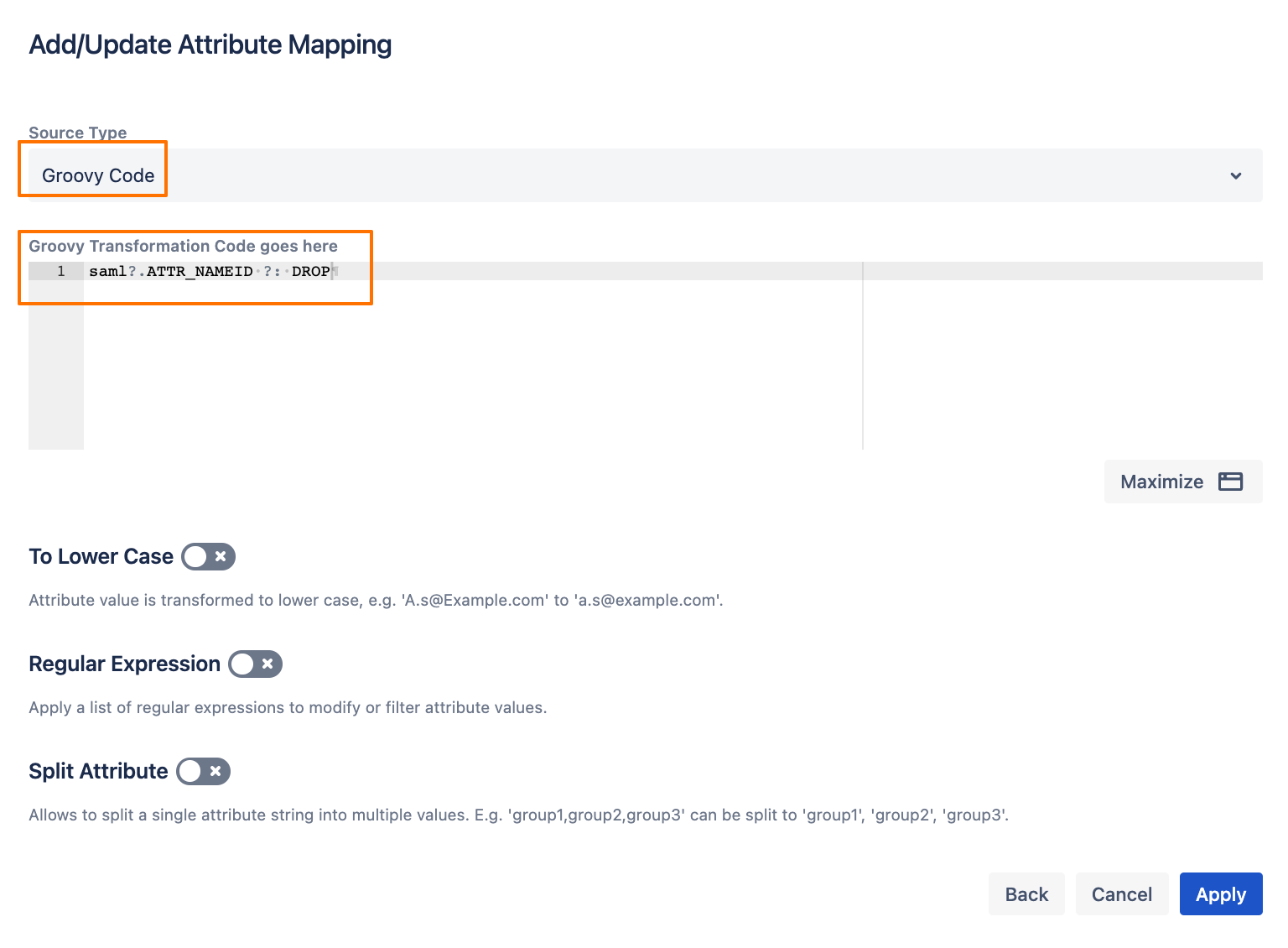
Choose Groovy Code, and enter the following code (this will add the value of the Name ID to the new attribute only when the user logs in via SAML, otherwise, that attribute would be empty):
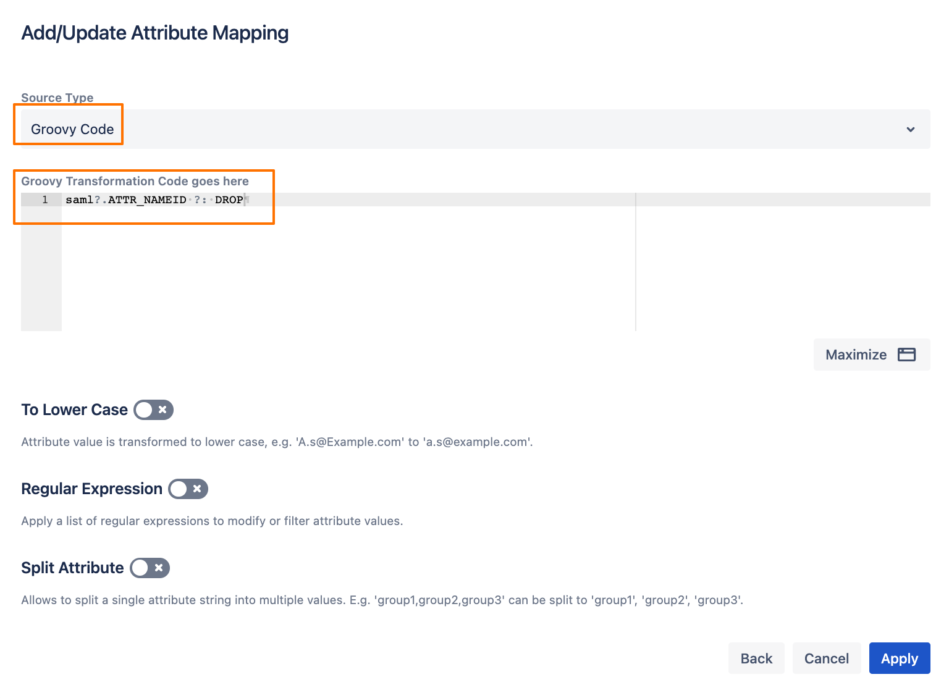
- saml?.ATTR_NAMEID ?: DROP
Then click on Apply.
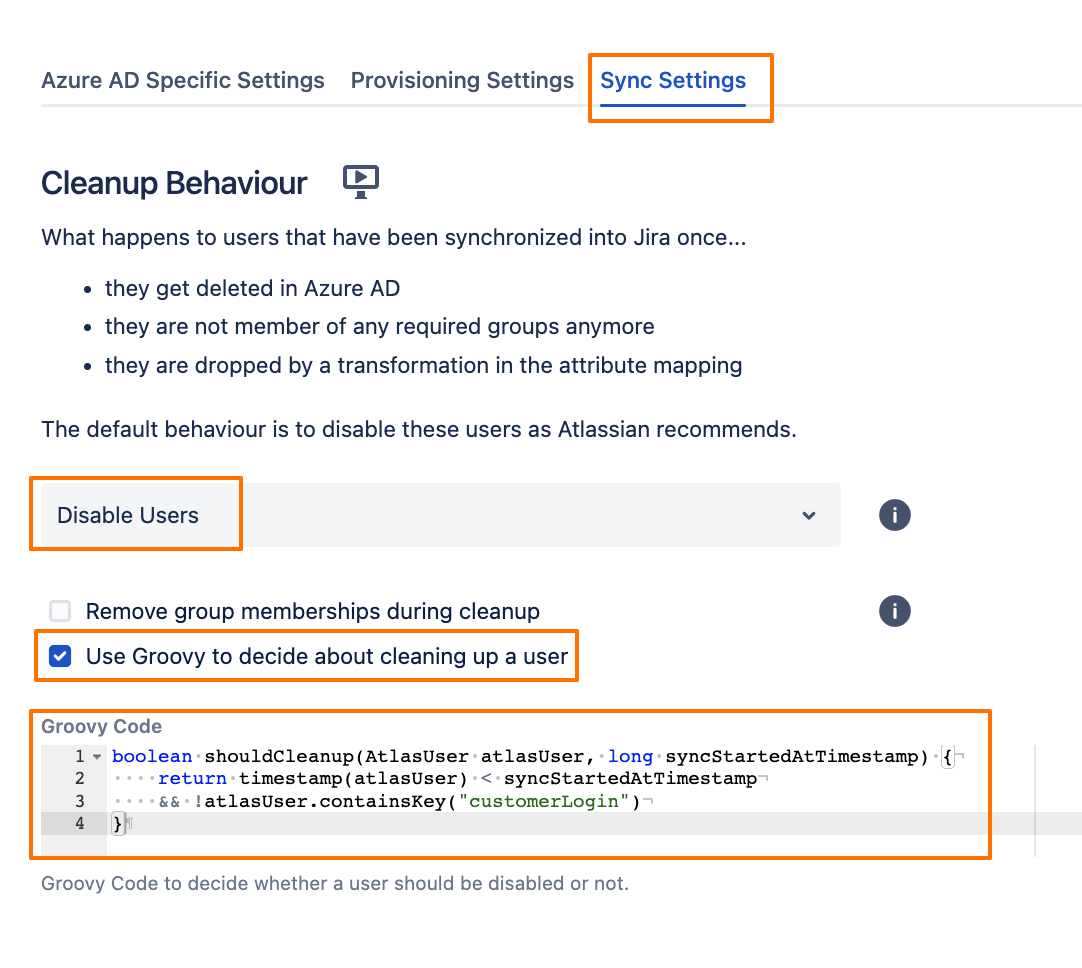
Go to the Sync Settings tab, change the Cleanup Behaviour to Disable Users, enable the “Use Groovy to decide about cleaning up a user“ option, and add the following code:
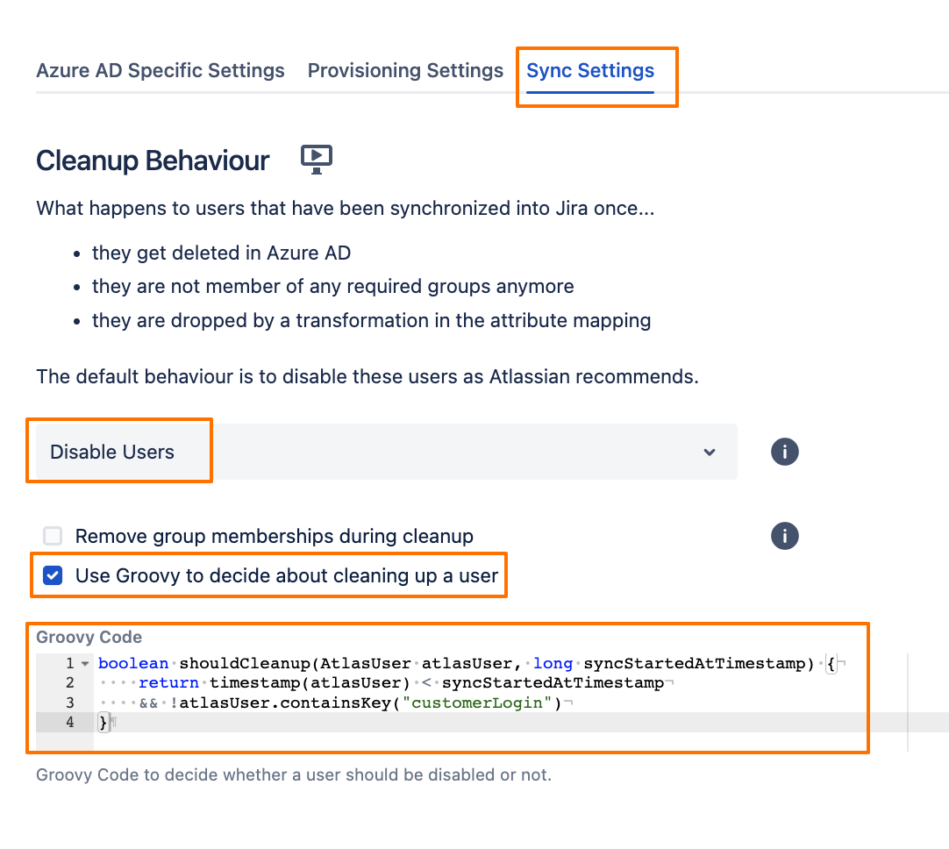
- boolean shouldCleanup(AtlasUser atlasUser, long syncStartedAtTimestamp) {
- return timestamp(atlasUser) < syncStartedAtTimestamp
- && !atlasUser.containsKey("customerLogin")
- }
Save the connector settings.
What the above would do is, when the customers log in to Jira via the portals URLs and SSO, they would have a new Crowd attribute with a value, and the cleanup behaviour (in addition to its normal function) would also not clean up the users who have a value in that new Crowd attribute.